Atlassian Confluence is a collaboration tool that is used by organizations to create and share various documents related to marketing, design specifications, project planning, etc. It can be licensed both

Juniper Threat Labs is seeing a growing attack on Accept-Charset HTTP Header. This request header allows the client to indicate what character sets, i.e., ISO-8859-1 or utf-8, are available for

“Alexa, can you tell me which of my Internet of Things devices are vulnerable to an attack?” Echo: “Hmmm, I don’t know that one.” “Alexa, can anyone access my camera
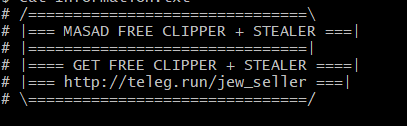
Juniper Threat Labs discovered a new Trojan-delivered spyware that uses Telegram to exfiltrate stolen information. Using Telegram as a Command and Control (C&C) channel allows the malware some anonymity, as

On August 7, 2019, Juniper Threat Labs started seeing attacks on PHP-FPM (FastCGI Process Manager) on port 9000. This attack works by passing PHP configuration options that allows injection of

I recently had the pleasure of participating in a panel discussion at the Cyber Security Summit USA in Denver, CO, on the topic of cloud INsecurity. The panel needed to
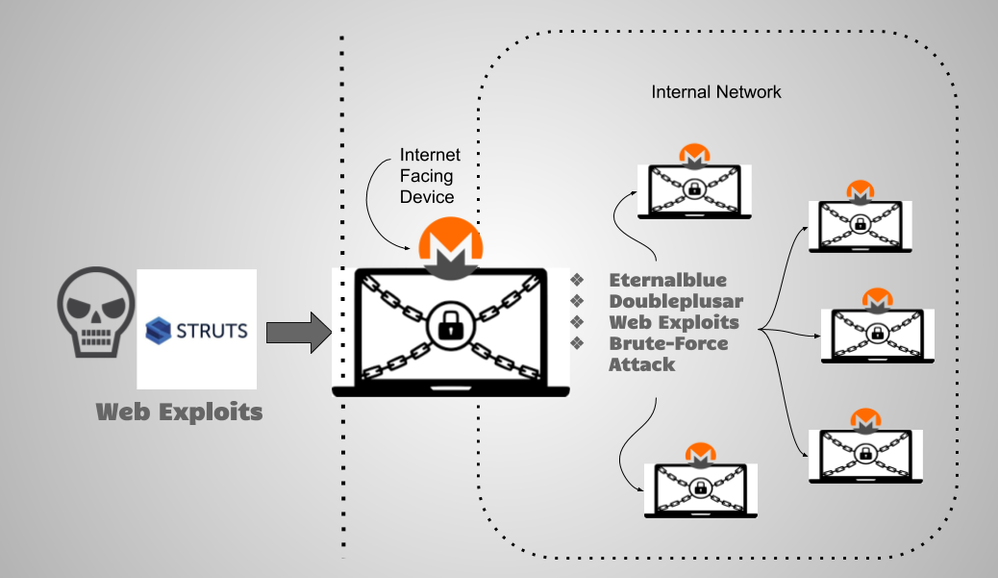
Juniper Threat Labs has been monitoring a campaign that delivered multiple stages of malware to install a cryptocurrency miner and ransomware. On March 16, 2019, we identified a surge in
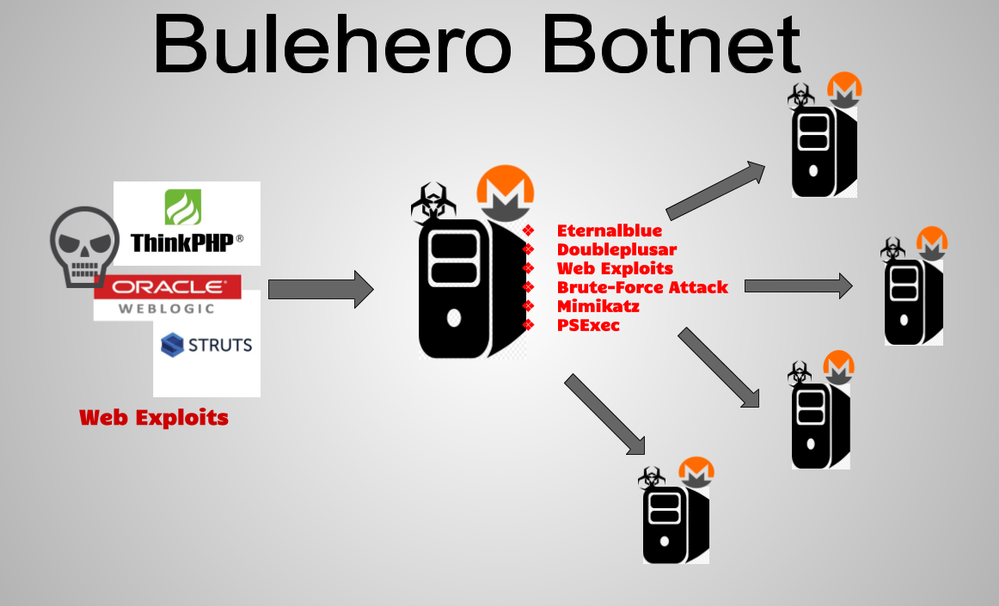
Juniper Threat Labs recently discovered an attack campaign that installs a cryptominer and spreads throughout the network. This campaign is interesting as one of its techniques is to use the infamous
Deploying detection solutions on an endpoint host comes with constraints – limited availability of CPU, memory, disk and other resources, stability constraints, policy adherence and restrictions, the need to be

Juniper Threat Labs has been monitoring the activity of a botnet, which is now being referred to as ViroBot by TrendMicro in their blog, and would like to share additional























