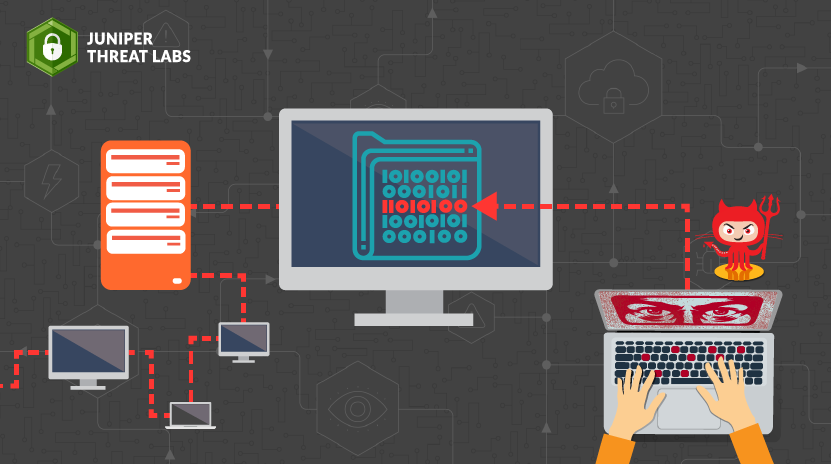
On February 1st, Juniper Threat Labs observed an attack that attempted to inject malicious code into Secure Shell (SSH) servers on Linux. The attack begins with an exploit against the
VMware vCenter Server is the centralized server management software for VMware, and is used to manage virtual machines, multiple ESXi hosts, and all dependent components from a single centralized location.
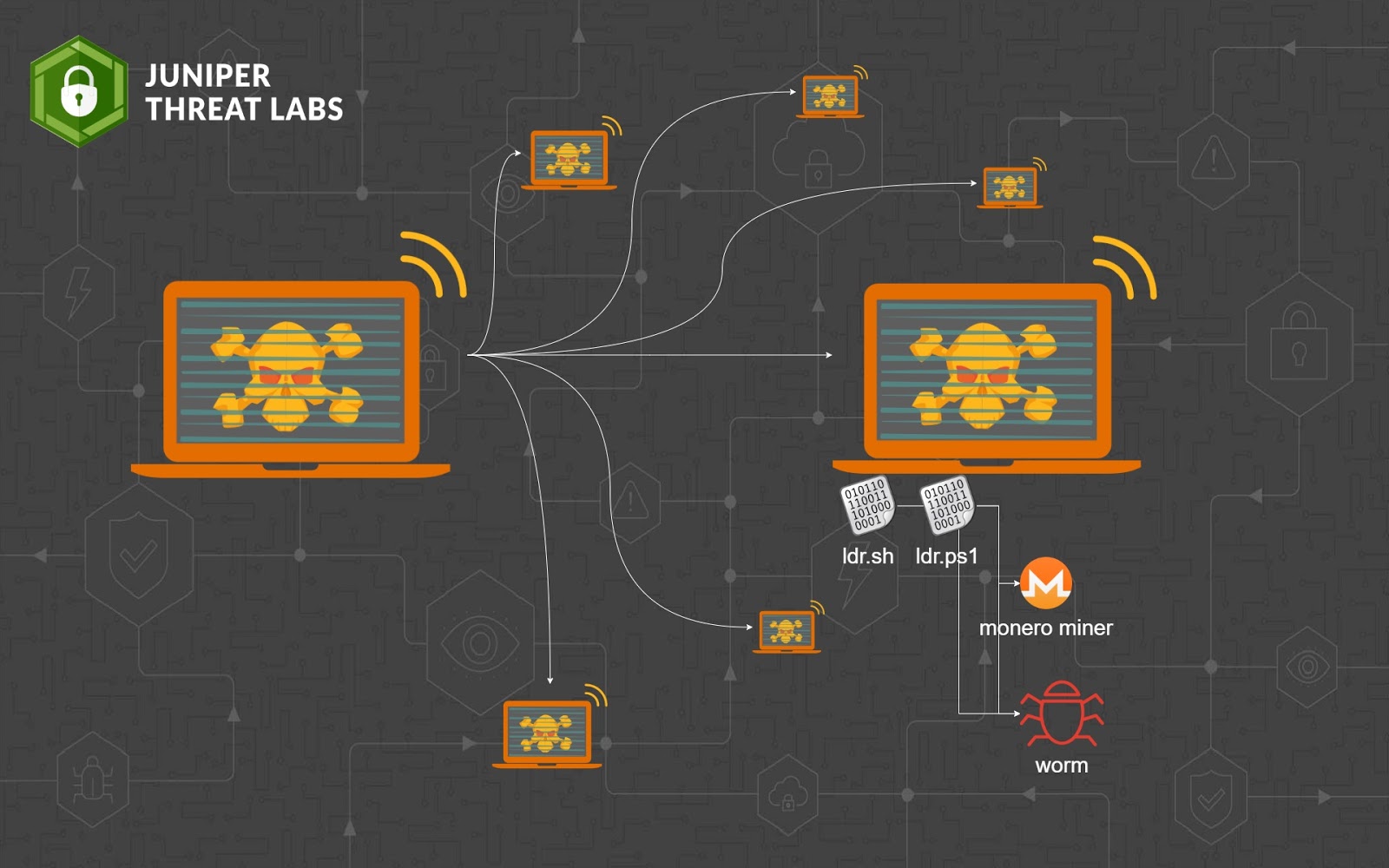
On March 4, 2021, Juniper Threat Labs identified a surge of activity of the Sysrv botnet. The botnet spread itself into Windows and Linux systems by exploiting multiple vulnerabilities, which
Apache Druid is an open source, distributed data store that is designed for ingesting high volumes of data to provide instant data visibility, ad-hoc analytics and queries with low latency and
In November, Juniper Threat Labs documented a new wormable cryptomining campaign dubbed Gitpaste-12. The initial wave of Gitpaste-12 attacks was last seen on October 27, when the GitHub repository hosting

Juniper Threat Labs is seeing active attacks on Oracle WebLogic software using CVE-2020-14882. This vulnerability, if successfully exploited, allows unauthenticated remote code execution. As of this writing, we found
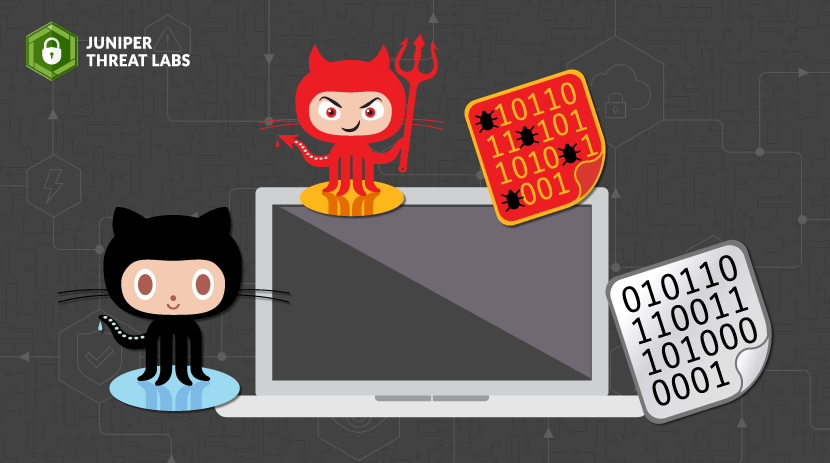
Gitpaste-12 is a new worm recently discovered by Juniper Threat Labs, which uses GitHub and Pastebin for housing component code and has at least 12 different attack modules available. There
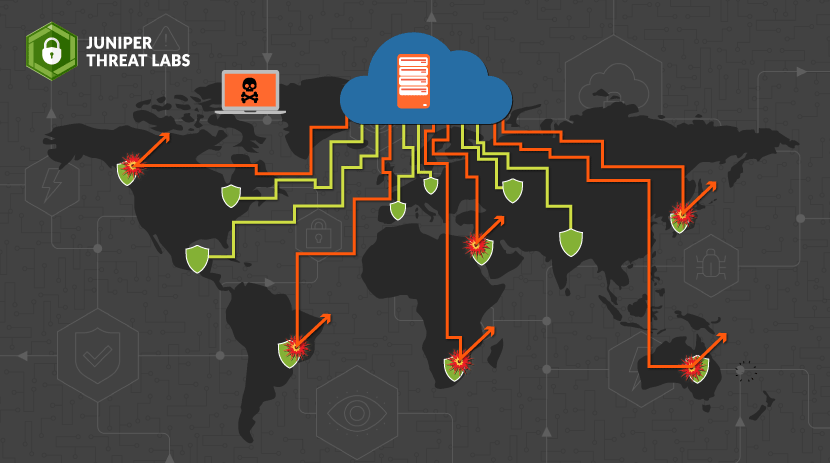
Juniper Threat Labs (JTL) has a network of sensors throughout the world that we use to monitor cyber security threats. These threats can range from Brute Force attacks against logins,
Juniper Threat Labs identified several malware campaigns that rely on a pastebin-like service for its infection chain. The domain in question is paste.nrecom.net. The attacks usually start as a phishing
Mirai has become such a common discovery in the wild that it is beginning to be disregarded as white noise, played off as a simple attack that should be readily