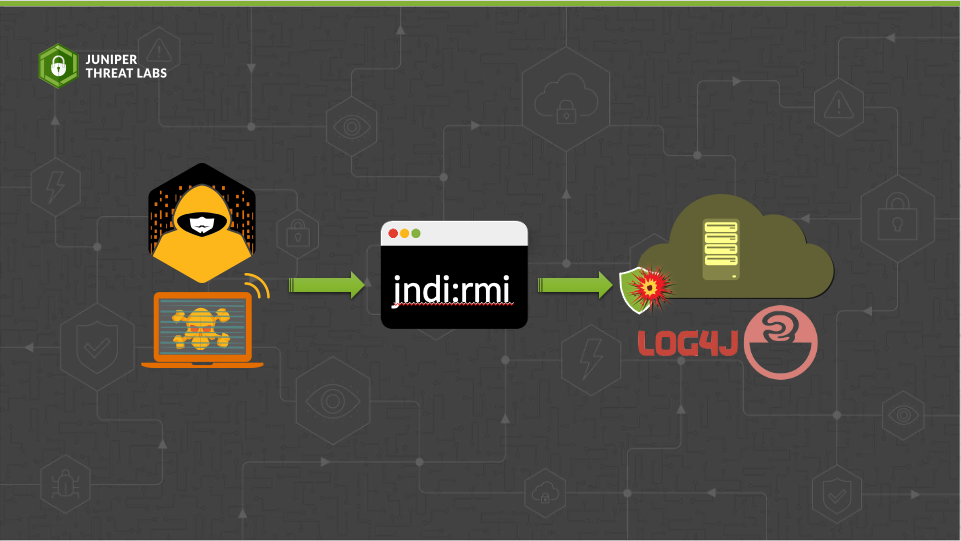
In a previous post, we discussed the Log4j vulnerability CVE-2021-44228 and how the exploit works when the attacker uses a Lightweight Directory Access Protocol (LDAP) service to exploit the vulnerability.
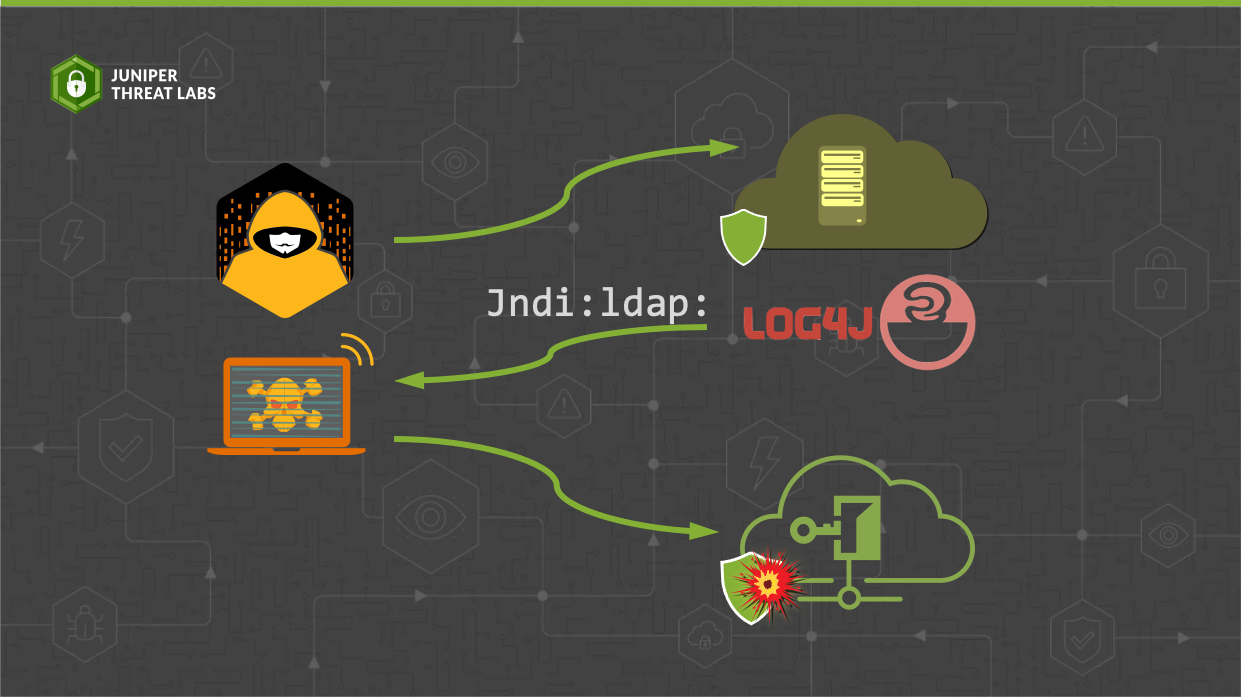
Log4j is a popular logging library used in Java by a large number of applications online. To enhance its functionality from basic log formatting, Log4j added the ability to perform
Juniper Threat Labs has been seeing on-going attacks targeting Apache http servers. On October 4, the Apache Software Foundation disclosed CVE-2021-41773, a path traversal 0- day vulnerability with reports of
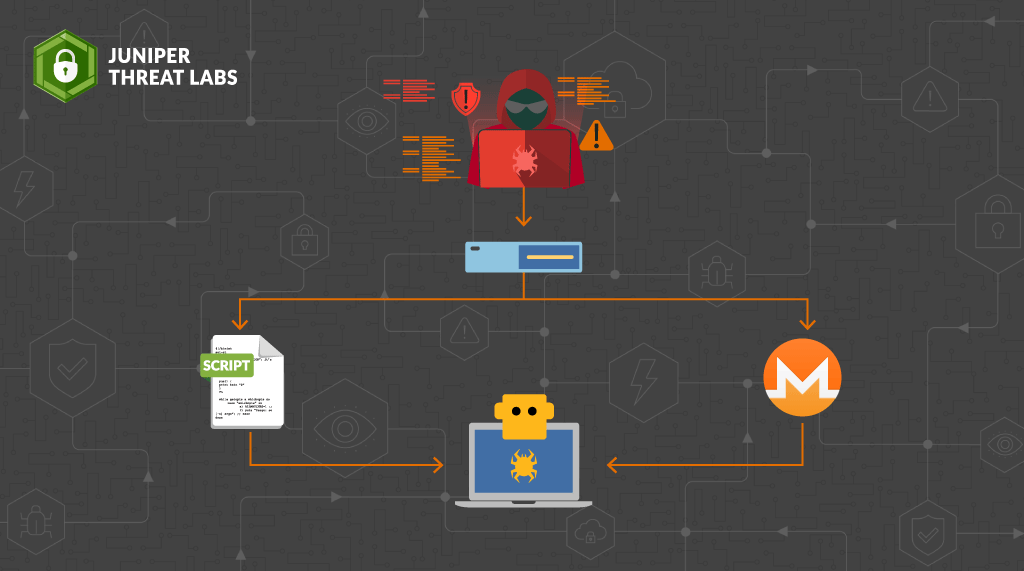
In the last week of September 2021, Juniper Threat Labs detected a new activity from Necro Python (a.k.a N3Cr0m0rPh , Freakout, Python.IRCBot) that is actively exploiting some services, including a
VMware vCenter server is a centralised management utility used for managing multiple ESXi hosts, virtual machines and all their dependent components. An arbitrary file upload vulnerability has recently been discovered in the Analytics
Juniper Threat Labs is seeing an on-going attack targeting Confluence servers. On August 25, Atlassian, the company behind Confluence, disclosed the vulnerability CVE-2021-26084. A few days after that, several
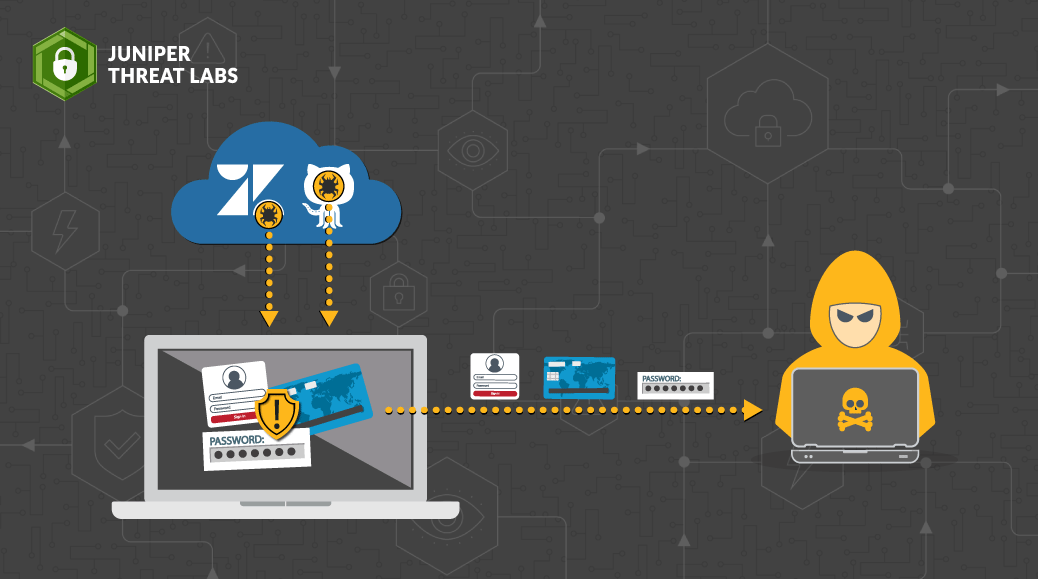
Juniper Threat Labs has detected a new development in the Aggah malware campaign. Previously, Aggah was known to be using legitimate infrastructures like BlogSpot, WordPress and Pastebin to host its
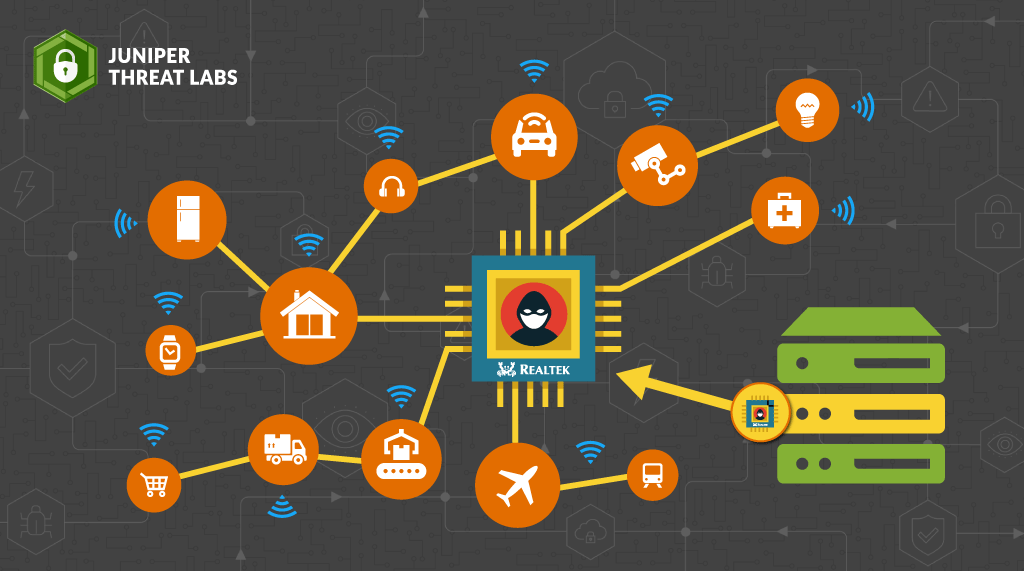
As we predicted in last week’s post, threat actors continue to utilize new Realtek vulnerabilities disclosed by IoT Inspector Research Lab to distribute malware. Starting on August 19th, Juniper Threat
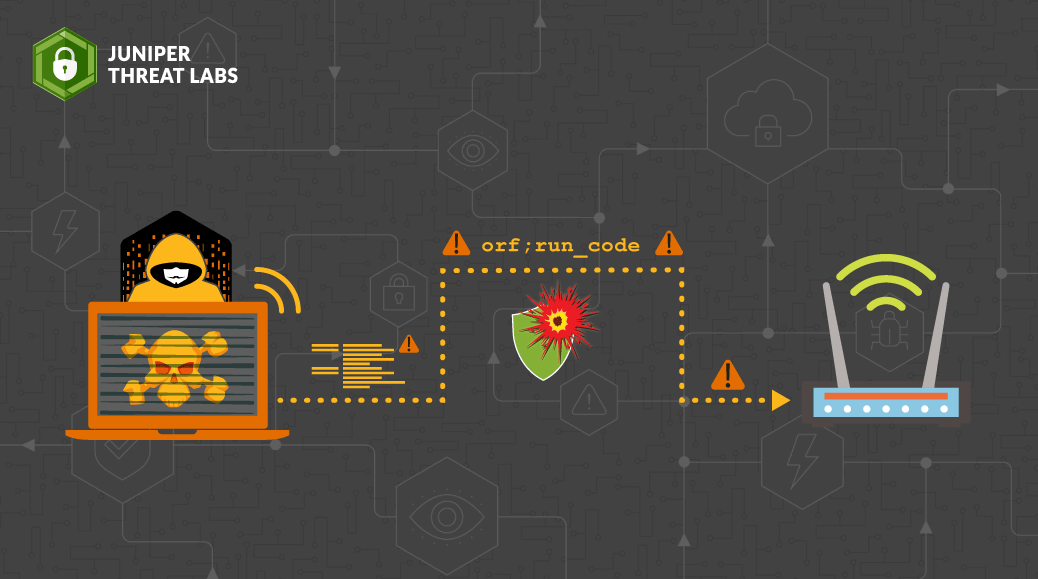
Juniper Threat Labs has detected that the threat actors that we recently observed exploiting CVE-2021-20090 are now actively exploiting CVE-2021-35394, a vulnerability disclosed last week by IoT Inspector Research Lab.
Juniper Threat Labs continuously monitors in-the-wild network traffic for malicious activity. Today, we have discovered an active exploitation of a vulnerability that was disclosed just 2 days ago. CVE-2021-20090 is a vulnerability that was discovered by