 Understanding how attackers establish and maintain their attack infrastructure is important for building robust defenses. Attackers employ various tactics to keep their operations resilient and undetected. In this blog post, we dive into the methods attackers use to set up their infrastructure, focusing on techniques like IP churn and changing hosting providers. We will also highlight how our Juniper Threat Labs leverages passive DNS to proactively discover malicious infrastructure before it is used.
Understanding how attackers establish and maintain their attack infrastructure is important for building robust defenses. Attackers employ various tactics to keep their operations resilient and undetected. In this blog post, we dive into the methods attackers use to set up their infrastructure, focusing on techniques like IP churn and changing hosting providers. We will also highlight how our Juniper Threat Labs leverages passive DNS to proactively discover malicious infrastructure before it is used.
Understanding Attack Infrastructure
The attack infrastructure comprises the servers, domains, and other resources that attackers use to launch and sustain their operations. Setting up this infrastructure involves configuring servers, registering domains, and compromising victim infrastructure, such as vulnerable unpatched home routers and IoT devices. A common strategy used by attackers is to leverage multiple servers with different domains and IP addresses and churn through them. As one gets discovered and blocked, the attackers move on to the next server(s).
Infrastructure churn involves frequently changing the domains and IP addresses associated with the attacker servers, such as DNS fast flux. However, there are key differences between DNS fast flux and infrastructure churn. Specifically, they differ in mechanism of operation, automation, and frequency. Infrastructure churn maintains a pool of pre-registered domains and IP addresses and switches between these backup resources as they are blocked or taken down. DNS fast flux associates a single domain with multiple IP addresses that change rapidly (within minutes) to make it difficult to block or takedown the malicious server. Infrastructure churn occurs when a domain is blocked or taken down, which makes the change frequency relatively low and reactive. DNS fast flux rotates IP addresses proactively in an automated way with high frequency.
Case Study: CatDDoS Botnet – Cecilio.network
To illustrate these tactics, we present a CatDDoS Botnet case with six months of activity. CatDDoS is a new-generation botnet that evolved from the Mirai codebase, featuring modified payload structures, and usingOpenNIC domains for command and control (C&C) servers. OpenNIC domains are alternative top-level domains (TLDs) managed by user-controlled, non-profit DNS network that operates outside the ICANN regulation. The botnet uses a combination of plaintext and encrypted requests for initial communication with C2 servers. Encryption is based on the ChaCha20 algorithm. The botnet modifies the original Mirai payload structure by changing the order of the data structure fields. Additionally, the botnet relies on N-day vulnerabilities in devices for propagation.
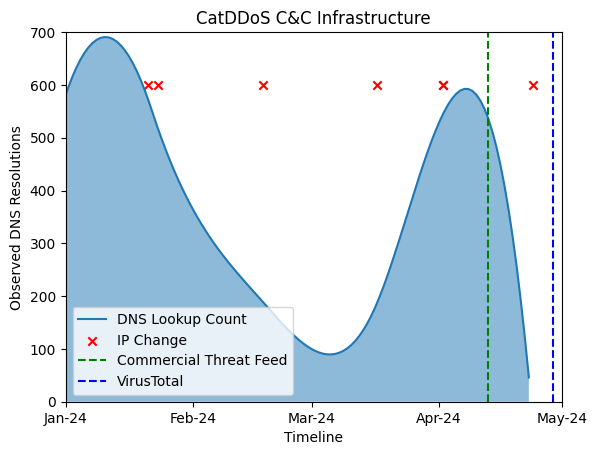
Figure 1: A plot showing the change in the server C&C IP address as red Xs
Let us take a look at a six-month window of the CatDDoS attack activities. During this six-month window, the attacker frequently changed servers and hosting providers to avoid detection. Figure 1 is a plot showing the change in the C&C server’s IP address as red Xs. This constant change makes it challenging to track and block their infrastructure using traditional methods. Figure 1, also plots the number of queries observed resolving the C&C domain during the six months (the blue area). These observed query counts can be correlated with the activity of the botnet, including the number of infected devices or DDoS activities. The green vertical line indicates when the domain was first observed in commercial threat feed. The vertical blue line indicates when the domain appeared in VirusTotal (30 days later).
What is passive DNS?
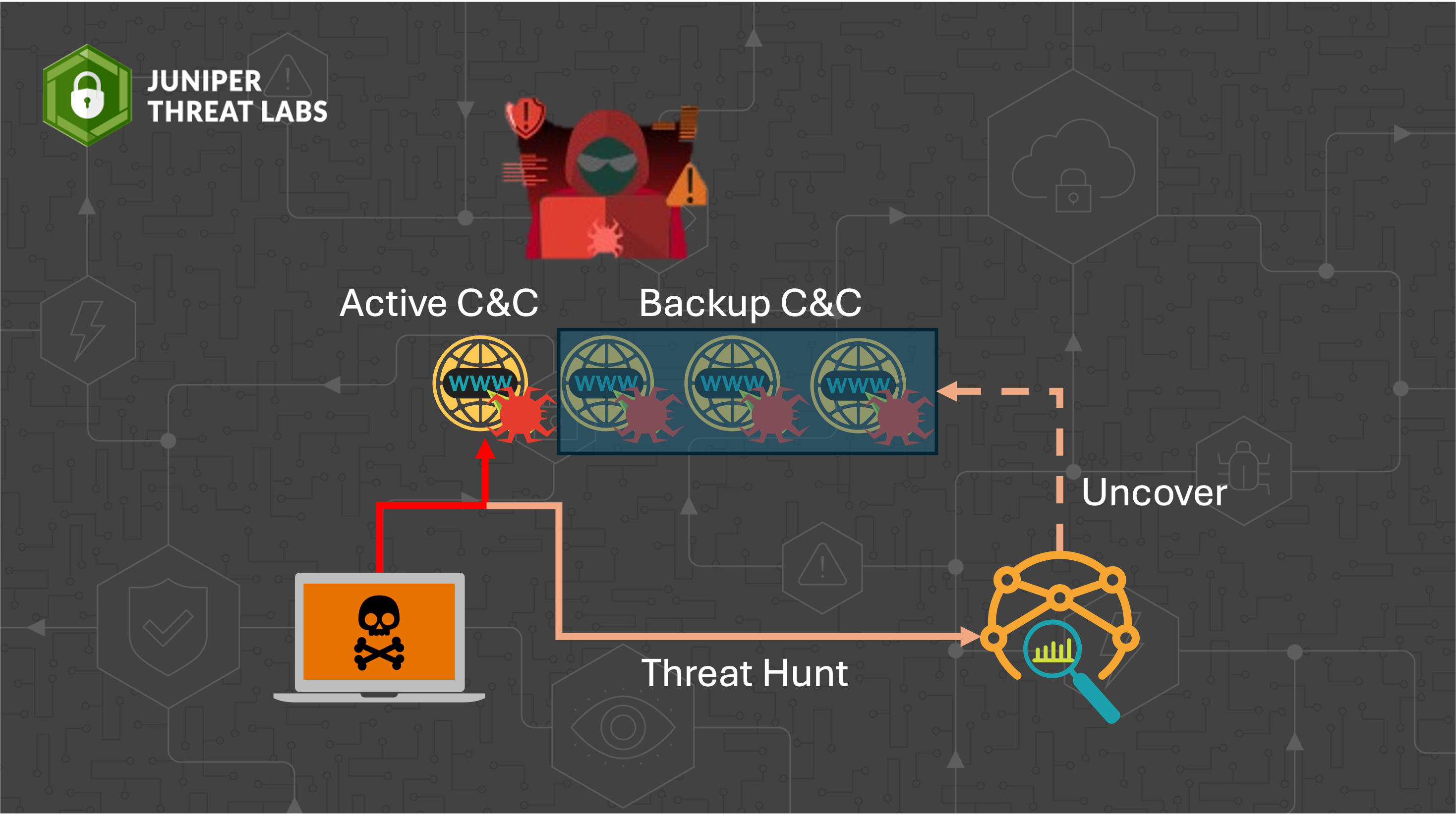
Using passive DNS, Juniper Threat Labs can uncover additional infrastructure used by CatDDoS. So what is passive DNS? Passive DNS are DNS logs that are typically collected on network transit paths using distributed network sensors. In traditional enterprise networks, firewalls, security appliances, and network collectors sit on the edge of the network and can log DNS queries from clients. However, many networks may not have configured traffic logging due to the cost associated with collecting and storing historical data. Furthermore,DNS traffic analysis can violate user privacy on sensitive networks. Passive DNS sensors address these challenges by logging DNS queries on different network paths and recording domain, IP address, timestamp, and record type. In addition, some passive DNS data providers would calculate additional fields that track query count (how many times a domain is resolved) and first and last seen timestamps.
Figure 2 illustrates an example of how DNS traffic might transit different paths on the Internet. Passive DNS sensors can be deployed anywhere on the path to observe DNS traffic. The closer the sensors are to the DNS authority, the more representative the data they collect. For example, Sensor 1 in Figure 2, will only observe DNS traffic from Enterprise 1. On the other hand, Sensor 3 in Figure 2 will observe DNS from Government, Residential, School, and Enterprise 2 and 3. The collected data must also be processed to remove duplicate records collected by different sensors. For example, a government DNS query in Figure 2 will be observed by Sensor 2 and Sensor 3 as it traverses the DNS Authority. Duplicate records require deduplication to ensure that the observed query counts are correctly recorded.
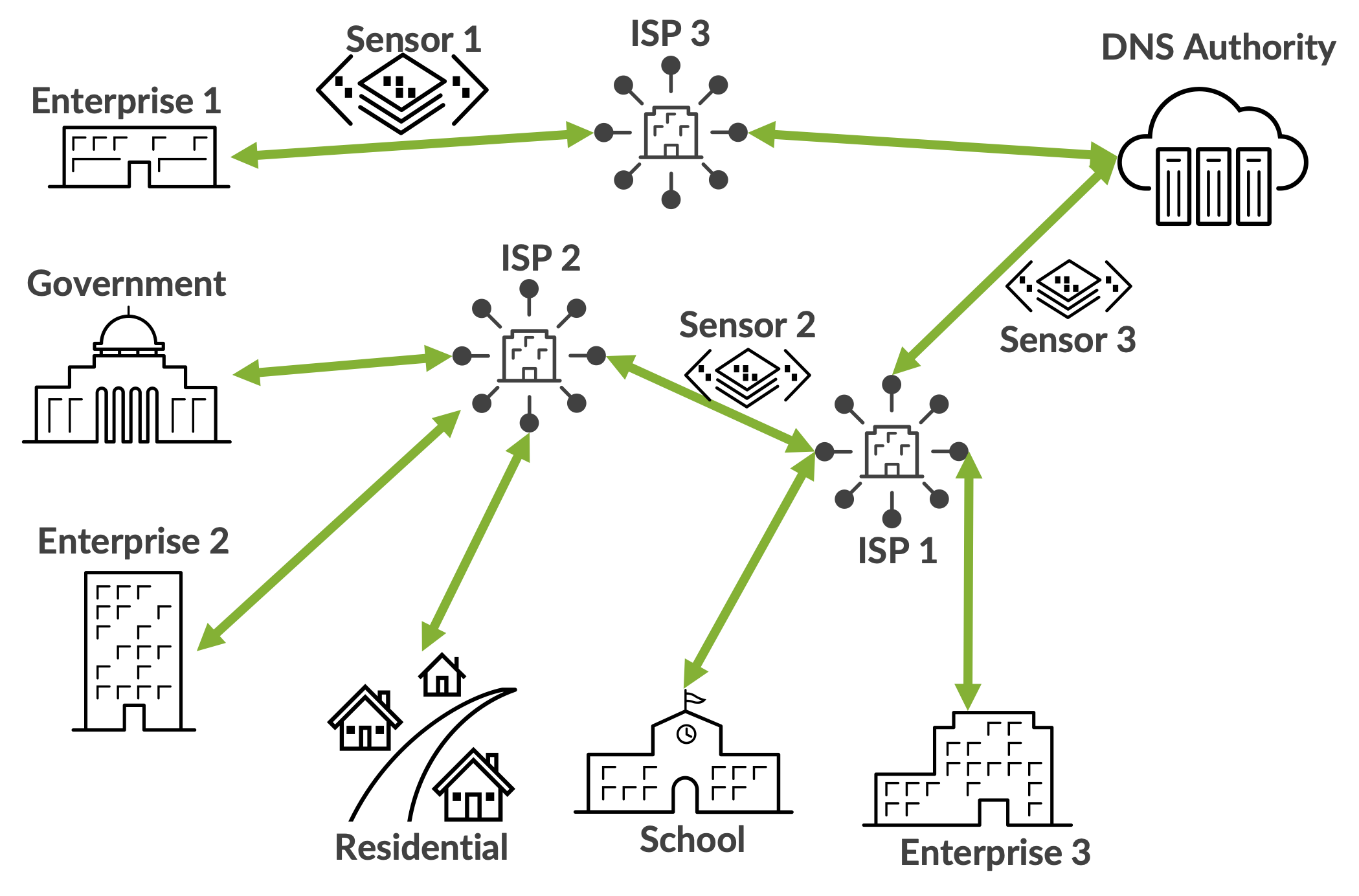
Figure 2: An example of how different paths on the Internet that DNS traffic might traverse.
Using Passive DNS for Threat Hunting
The passive DNS data are historical, which means that it will track domain and IP relationships from past observation. Juniper Threat Labs uses this data set to identify infrastructure relationships to map the attacker infrastructure. We assume that an attacker may test their domains and IP addresses before using them, which can potentially be observed by passive DNS sensors before the attack starts. Our processes are illustrated in Figure 3. We start by taking a list of known malicious domains and IP addresses that we call seed infrastructure from threat intelligence feeds. We remove duplicate entries from the various threat intelligence feeds and filter for only C&C servers. We exclude servers such as downloader site, phishing website, and various other categories. Next, we query our passive DNS data to identify historical relationships for the seed C&C servers. The discovered records usually contain noise that we must remove. This noise includes domains and IPs that are related to the top websites, such as search engines, social networks, and content delivery networks.
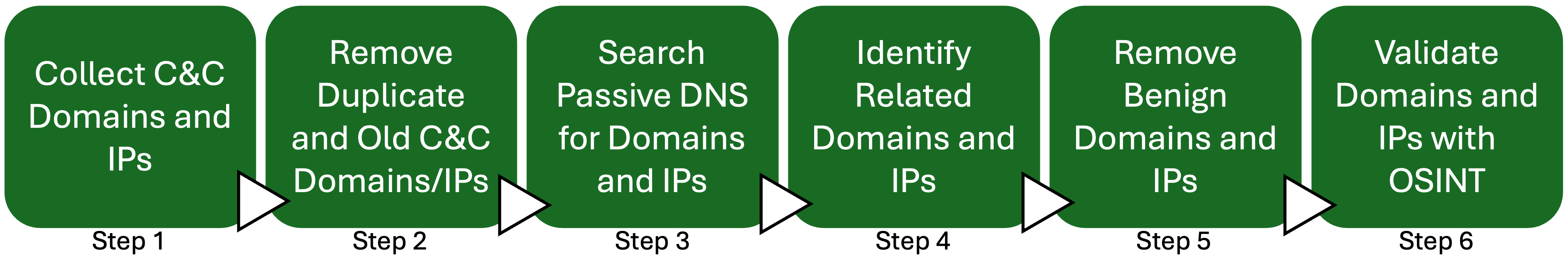
Figure 3: JTL’s threat hunting process using passive DNS.
We use various techniques to clean up the results. Some of these techniques include using top site lists such as Alexa Top 100K. Additionally, we can estimate domain or IP popularity using passive DNS data by inspecting the query counts, duration of domain-to-IP association, and the number of related domains and IPs to the discovered artifacts. Using these heuristics, we remove irrelevant domains and IPs. The last step validates our findings by searching open-source intelligence for the discovered domains and IPs for detections. Once we have a final list of suspected domains and IPs, we rank them according to time and third-party detection.
We have used this technique for the past 13 months and have managed to identify emerging threats before they were publicly disclosed. Next, we will present one case where our threat hunting approach using passive DNS has helped our customers stay protected from emerging threats.
Case Study: Remote access Trojans and Cloudflare Abuse
On August 1, 2024, proofpoint published a blog on threat actors abusing Cloudflare tunnels to deliver remote access trojans (RATs). Figure 4 illustrates the attack stages. The infection vector utilizes phishing emails with links to a downloader site using the WebDAV protocol. Once a user clicks on the link, a CMD/BAT file downloads Python installer, which downloads the RAT/Trojan component. The researchers observed the attack delivering different RAT families such as XWorm, AsyncRAT, VenomRAT, and PureLogs Stealer. Once the RAT component infects a target system, it will typically connect to a C&C server to exfiltrate sensitive information. The researchers at eSentire observed the same attacks against their government customers.
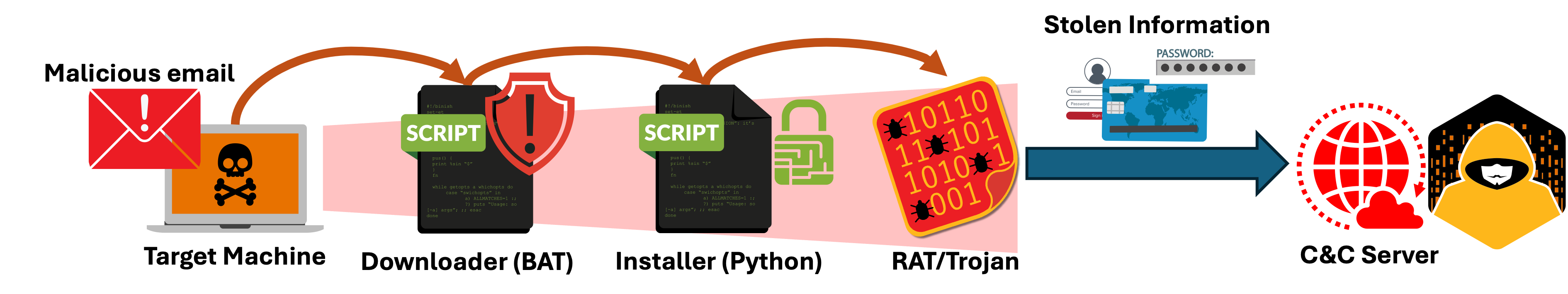
Figure 4: Phishing attack leading to Malware infection
Attack Timeline
Proofpoint researchers observed the initial activities of threat actors in February 2024. These activities appear to be associated with phishing activities using the Cloudflare tunneling service (trycloudflare). On the other hand, eSentire researchers detected an infection that affected their customers in July. Juniper Threat Labs became aware of one C&C server on the 8th of July from a threat intelligence feed. We leveraged our threat-hunting passive DNS data to identify additional C&C infrastructure and pushed it to our customers. The following table highlights the discoveries made by our threat hunting:
Four of the highlighted indicators overlap with the Proofpoint and eSentire indicators in their reports. Our research identified seven additional domains and two additional IP addresses. These indicators were included in our SecIntel feed to customers. We continue to track the infrastructure of the threat actor using passive DNS. The most recent C&C domains were last observed from July 31st to August 13, 2024. Here are the latest indicators:
- nanarchym[.]duckdns[.]org
- xwrmmone[.]duckdns[.]org
- nhvncpure[.]duckdns[.]org
- modsamsync[.]duckdns[.]org
- nanarchymomey[.]duckdns[.]org
- momekxwrm[.]duckdns[.]org
- hvncmomentpure[.]duckdns[.]org
We can see that threat actors are constantly changing the C&C domains to circumvent network defenses. We calculate that this attack campaign creates on average three new domains every 10 days. Furthermore, we found that certain domains have much higher counts (distinct DNS resolutions) that potentially correlate with higher numbers of infected machines. For example, the domain ‘ncmomenthv [.] duckdns [.]org’ has the highest count, which we rank as the top active C&C domain in this campaign. The domain was first observed by passive DNS sensors on July 4th and last observed in August.
Keep in mind that the underlying passive DNS data source is not perfect, and the placement of the sensors along with where the infected machines exist can skew the overall observations. However, our approach is to identify associations between the C&C domains and IPs to uncover the zero-day attacker infrastructure. This active discovery approach increases the cost for the attacker because once their domains or IP addresses are identified by defense systems such as firewalls, the attack efficacy drops. Therefore, the attacker must allocate new resources to support their campaign, which increases their operational cost and reduces their overall profit.
Conclusion
In this blog, we show how Juniper Threat Labs utilizes historical DNS data to investigate and discover yet-to-be-used attack infrastructure. This approach provides a unique perspective on the evolution of attacker tactics and helps defenders increase their visibility of potentially harmful domains and IP addresses. Customers with an active Advanced or Premium license automatically get the latest SecIntel feed and are protected from this threat. We continue to track this campaign and other attack campaigns using the proactive threat-hunting approach to stay ahead of attackers.