Juniper Threat Labs has uncovered an attack that targets Redis Servers using a recently disclosed vulnerability, namely CVE-2022-0543. This vulnerability exists in some Redis Debian packages. The attack started on

As more companies embrace a Work-From-Anywhere (WFA) workforce, new cloud-based architectures are required to secure the network edge. However, many organizations are hesitant to walk toward SASE for fear of
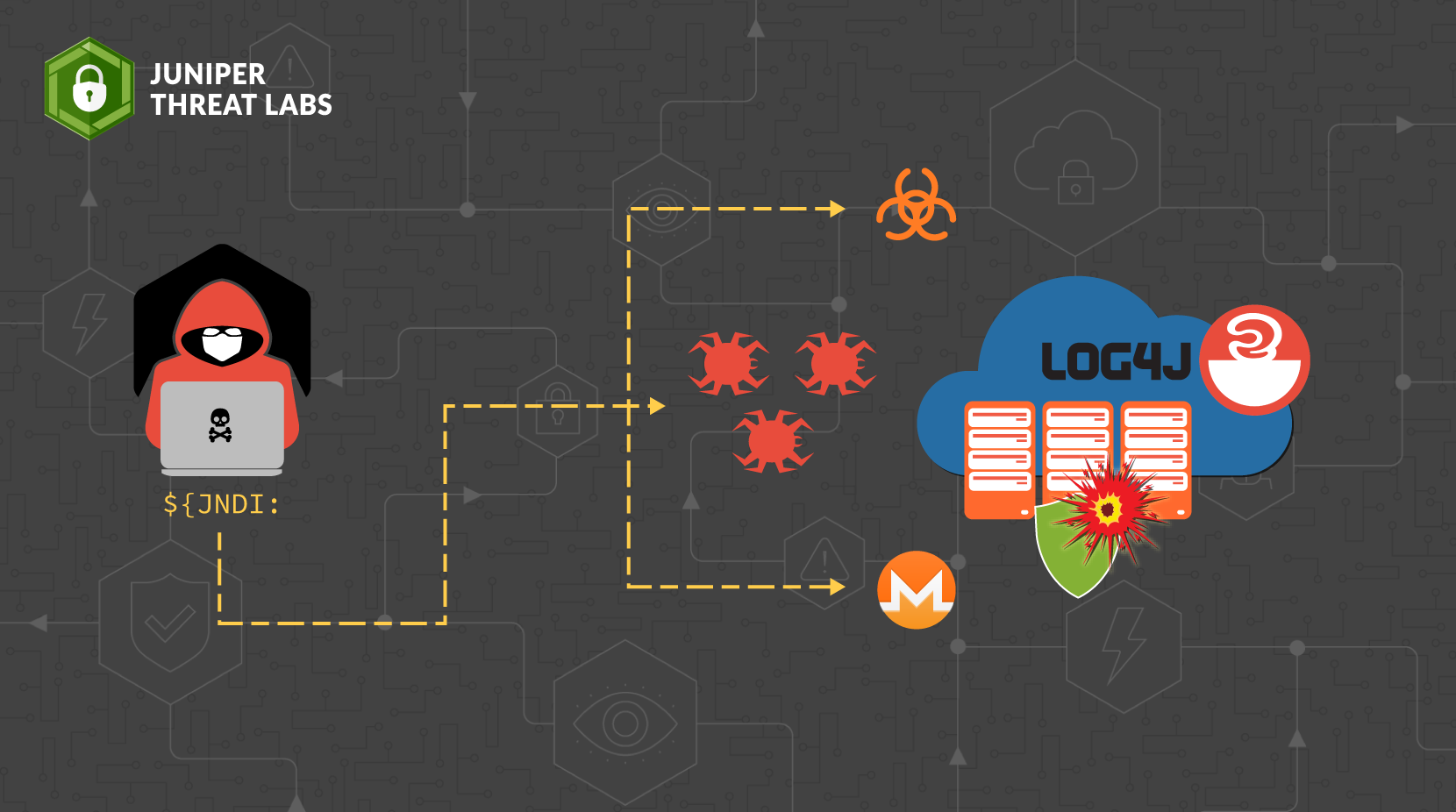
Juniper Threat Labs compiled a list of the payloads from log4j attacks we have seen as of 12/16. Most of the payloads install malware such as Muhstik, Kinsing, Mirai and
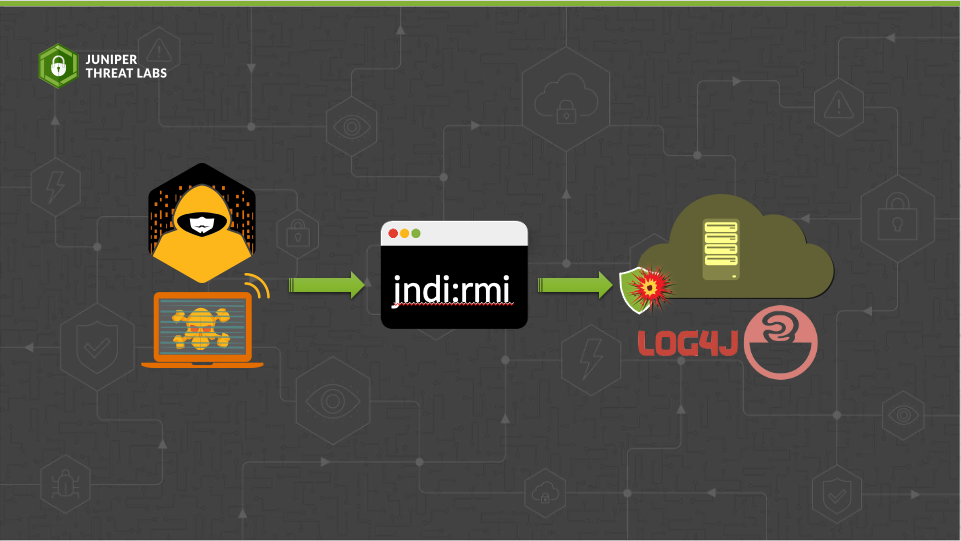
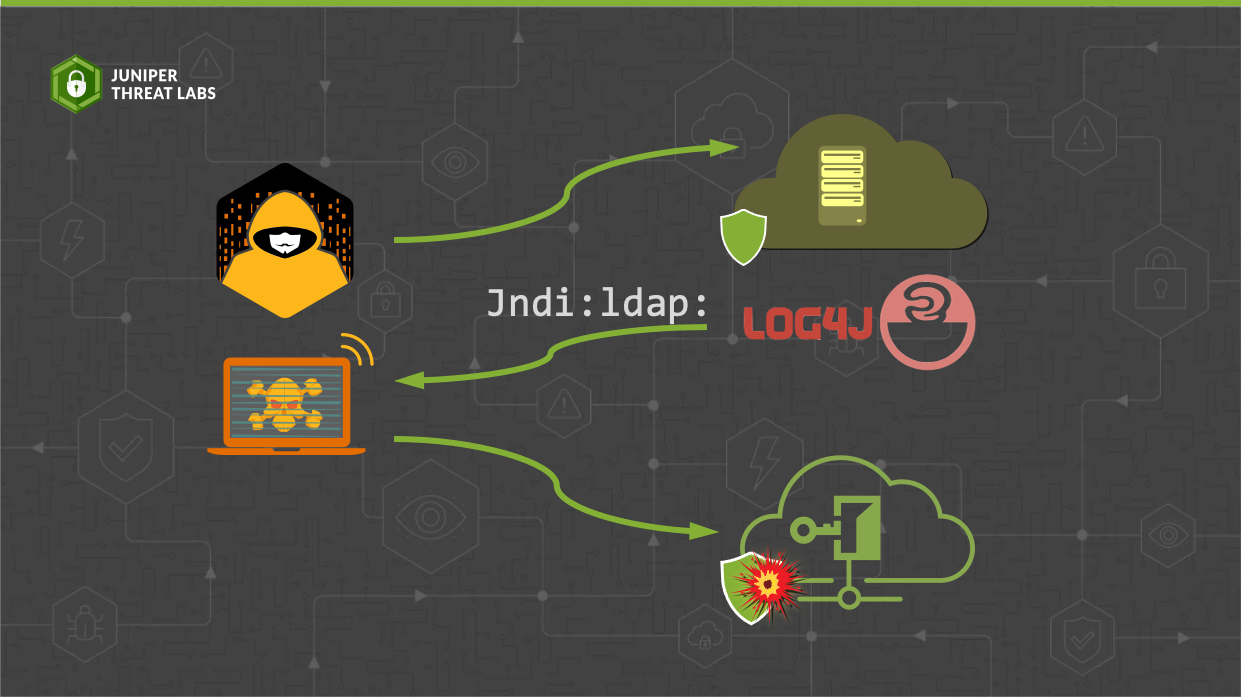
In a previous post, we discussed the Log4j vulnerability CVE-2021-44228 and how the exploit works when the attacker uses a Lightweight Directory Access Protocol (LDAP) service to exploit the vulnerability.
Log4j is a popular logging library used in Java by a large number of applications online. To enhance its functionality from basic log formatting, Log4j added the ability to perform
At Juniper Networks, we have always been focused on delivering great end-user experiences for our customers. We do this by providing not just uptime, but reliable connectivity from anywhere in
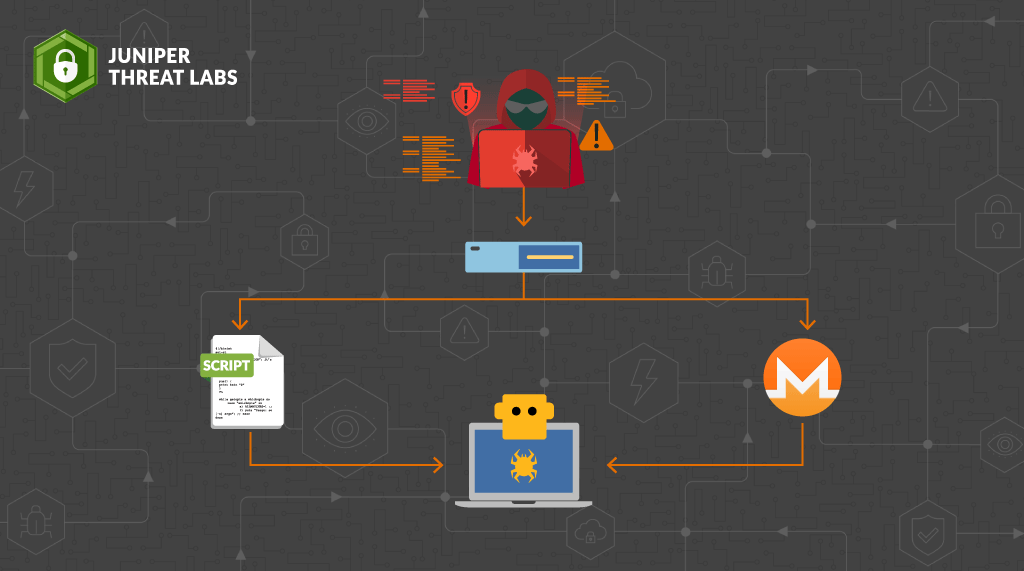
In the last week of September 2021, Juniper Threat Labs detected a new activity from Necro Python (a.k.a N3Cr0m0rPh , Freakout, Python.IRCBot) that is actively exploiting some services, including a
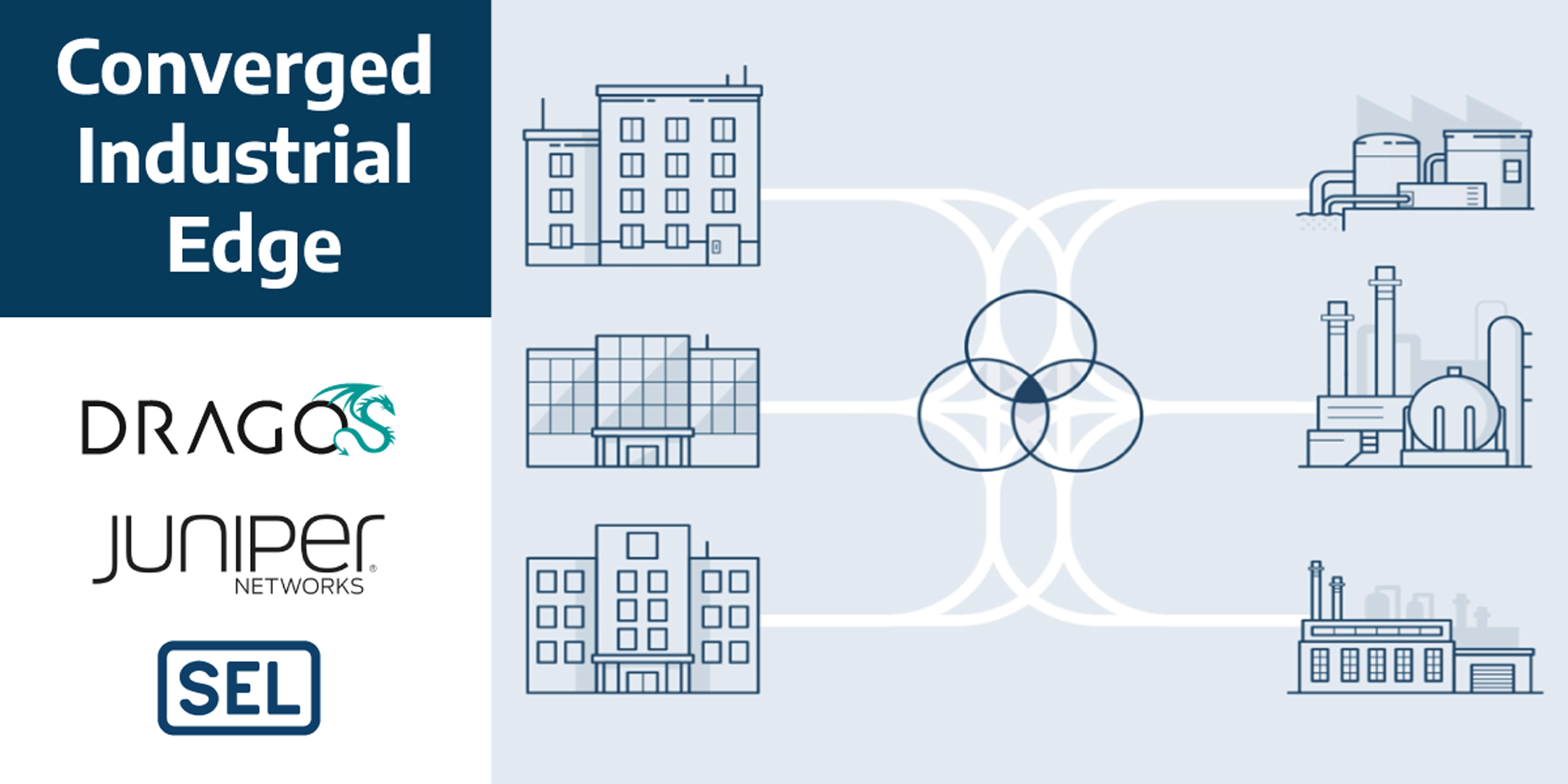
Juniper Networks is pleased to announce the completion of Project Ambassador, a Department of Energy (DOE) funded initiative, and with it, the general availability of Juniper Networks’ Converged Industrial Edge
Juniper Threat Labs is seeing an on-going attack targeting Confluence servers. On August 25, Atlassian, the company behind Confluence, disclosed the vulnerability CVE-2021-26084. A few days after that, several
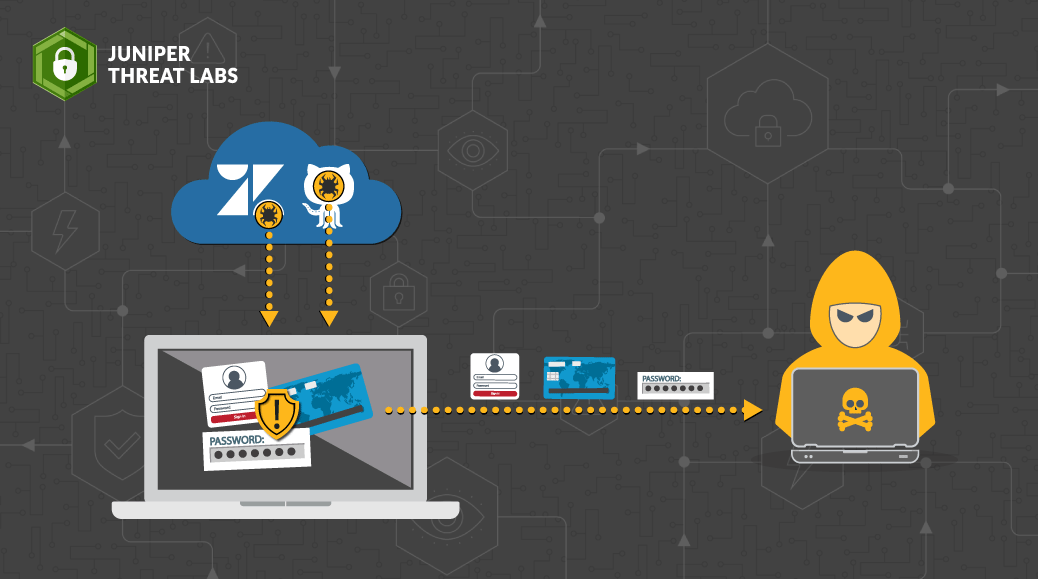
Juniper Threat Labs has detected a new development in the Aggah malware campaign. Previously, Aggah was known to be using legitimate infrastructures like BlogSpot, WordPress and Pastebin to host its























