This blog post is a follow up to the introductory blog, “Solving the Quantum Computing Security Problem,” by Gert Grammel. Quantum computers capture the imagination of futurists, physicists, engineers and
When it comes to information security, most would agree that guessing is no substitute for knowing. While hope is not a strategy, many organizations employ this approach and don’t run

Encrypting files is and has always been an effective way to protect sensitive or confidential data. The earliest known use of encryption was found in hieroglyphs carved into the wall
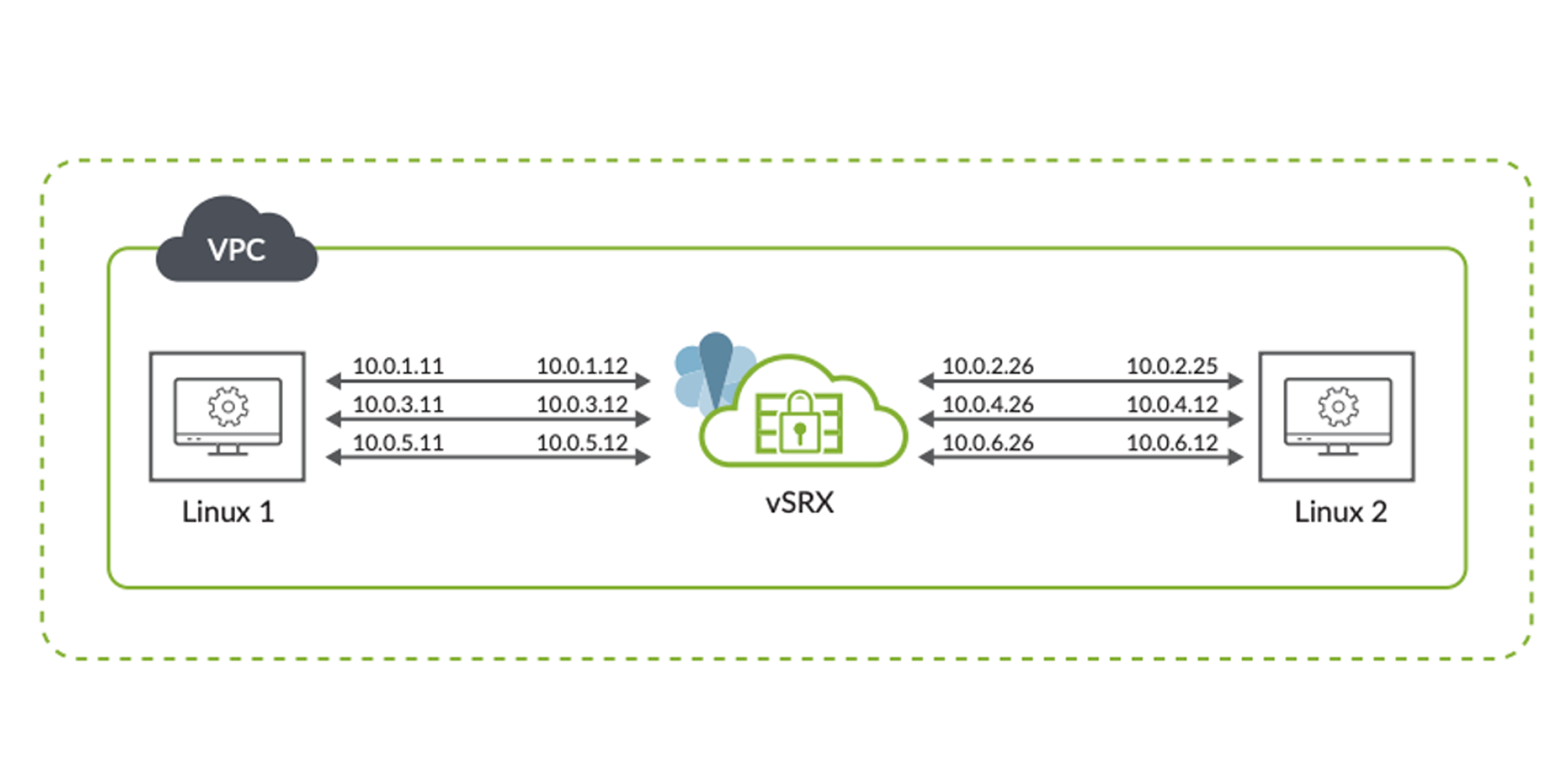
Enterprises are moving workloads to the public cloud to gain operational efficiencies and potential cost benefits. Throughout this transition, the network design must ensure that the end-user experience is not

In the final installment of our three-part series on the journey to Secure Access Service Edge (SASE), we’ll discuss the architecture. See part two in our SASE series here. An
In this second installment of our three-part series on the journey to Secure Access Service Edge (SASE), the focus will be identifying team members and developing a plan that will

Juniper Threat Labs is seeing active attacks on Oracle WebLogic software using CVE-2020-14882. This vulnerability, if successfully exploited, allows unauthenticated remote code execution. As of this writing, we found
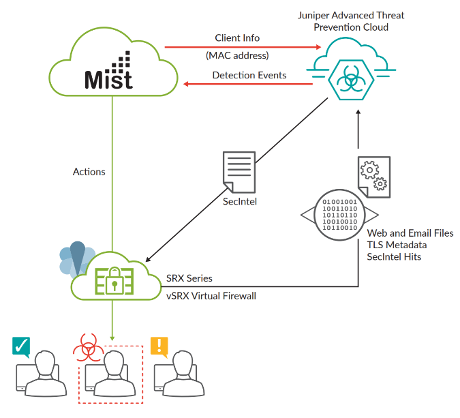
With the rise in remote work, employee devices often share networks with personal and new devices are regularly added to networks – and often, unbeknownst to IT. Incomplete network visibility

When it comes to securing an organization, there are so many questions to answer. Where are the organization’s users predominantly located – onsite or remote? Are there any predicted shifts
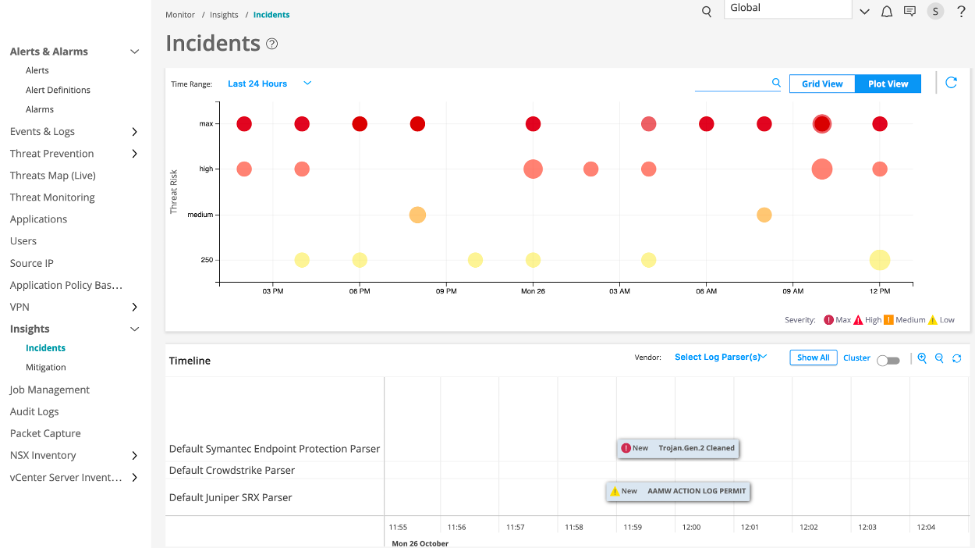
In the technology industry, there is no shortage of marketing buzzwords, oftentimes applied to product capabilities that aren’t truly able to live up to their hype. Take “single pane of























