There are many “cyber gangs” out there wreaking havoc wherever there’s an opportunity to do so, especially with the current geopolitical climate. As the past year has clearly shown us,

No two organizations are the same, yet all face a common challenge: increasing cybersecurity threats. According to one recent study, the global cost of cybercrime will top $8 trillion in
Juniper Networks has been on a journey over the past four years to transform the way teams secure their networks, and we’re proud that Gartner recognized both this journey, as
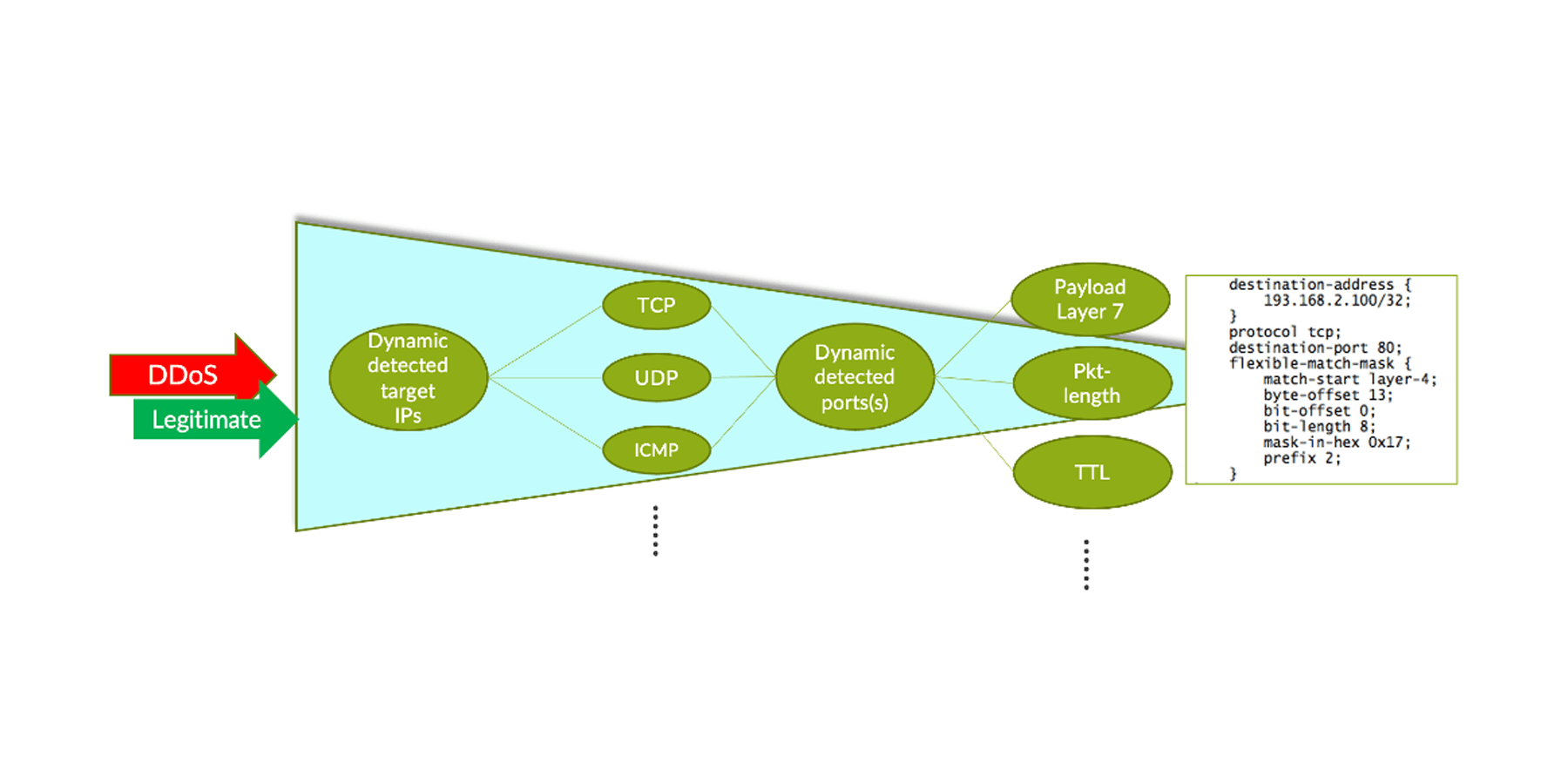
The joint Corero-Juniper Threat Defense Director (TDD) anti-DDoS solution protects network infrastructure from volumetric DDoS attacks that continue to grow in magnitude, frequency and sophistication. Today, the solution has already
Did you know that Distributed Denial-of-Service (DDoS) attacks are one of the fastest ways for cybercriminals to bring down a digital business? Scan the news for “DDoS attack,” and you’ll
Introduction Juniper Threat Labs is currently monitoring an emerging Chinese Remote Desktop Trojan called Asbit. It’s a remote access Trojan being advertised on its developer’s website as a “Fast

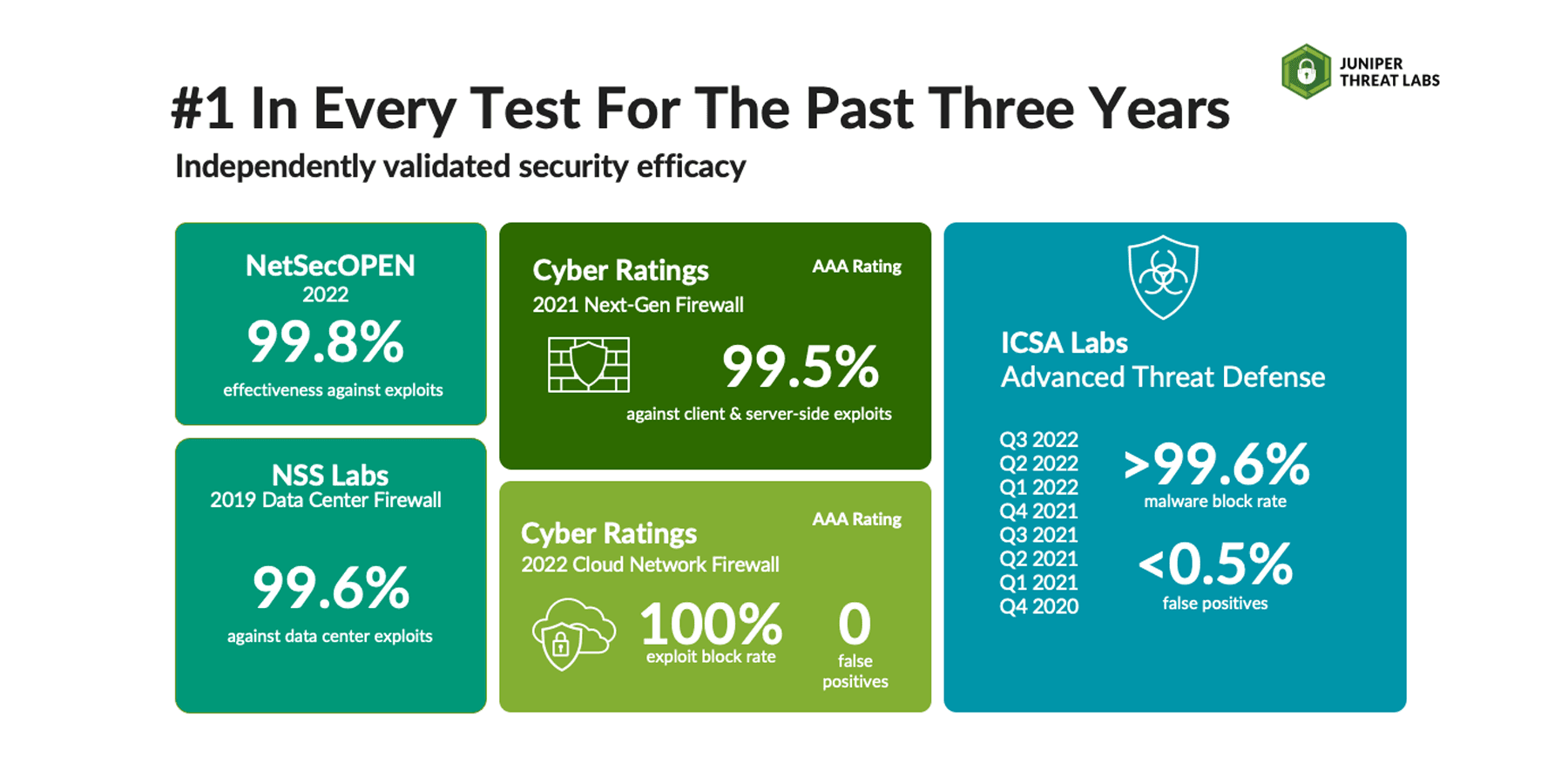
Whether at work or our personal lives, we want to purchase a product that performs as advertised and gets the job done. Fortunately for consumers, there are excellent resources that
A zero-day vulnerability was discovered on Microsoft Windows Support Diagnostic Tool (MSDT). On May 27, a researcher who goes by the twitter handle nao_sec discovered an interesting Microsoft Word document

With networks becoming more distributed and complex, and IT resourcing either remaining flat or declining, networking and security teams have to do more without actually having more. Secure Access Service

On May 12, 2021, United States President, Joe Biden, signed Executive Order 14028 to address the increasing nature of cybersecurity attacks and the effect that they have on businesses, the























