Juniper Networks has been on a journey over the past four years to transform the way teams secure their networks, and we’re proud that Gartner recognized both this journey, as well as our strength in security technology and an effective overall solution, in its 2022 Magic Quadrant™ for Network Firewalls.
We started our journey by making sure that our security technology is effective against threats. After all, this is the reason security technology exists, but efficacy must be ubiquitous across all environments.
Juniper Networks has consistently ranked #1 in security efficacy in objective, third-party security tests, such as Cyberratings, NetSecOPEN and ICSA Labs, for the past three years, which cover firewall use cases across the network from edge to data center, including public cloud. We can prove that Juniper firewalls, regardless of form factor or use case, effectively prevent threats.
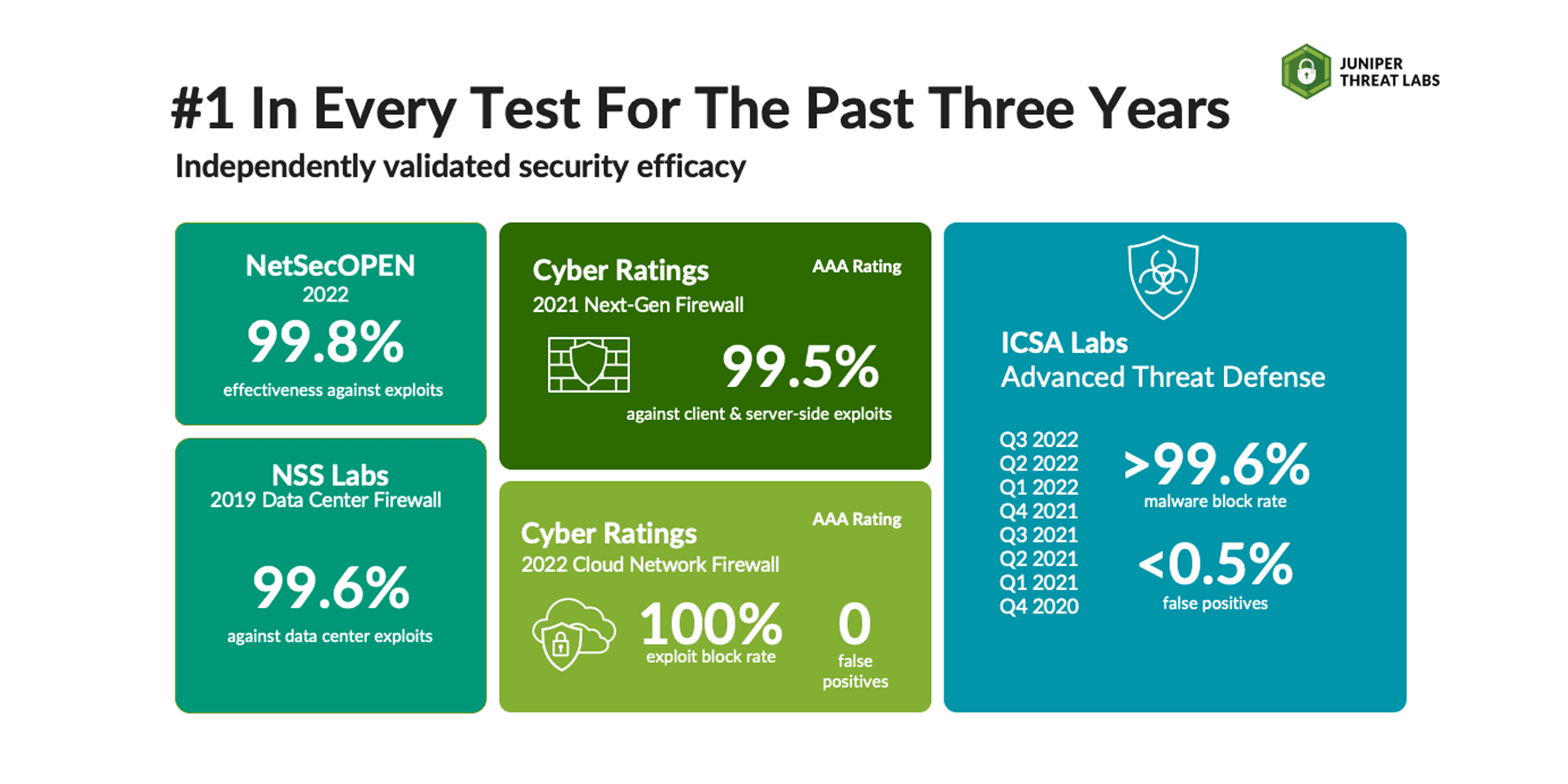
We also recognized that the impossible choice of network security — choosing between effective threat protection or network throughput performance — was a choice that left organizations at a constant disadvantage. We felt that our customers shouldn’t have to choose and that they should demand more from security vendors. So, we made sure that our firewalls could sustain high volumes of traffic with all security features turned on.
Juniper’s Strengths
Effective threat protection without performance tradeoffs across all firewall deployment scenarios is not enough without a means to operationalize it across the network.
This is why we launched our unified management experience, Security Director Cloud, nearly two years ago. In addition to managing all SRX firewall form factors — physical, virtual and containerized — it also manages Juniper Secure Edge, our cloud-delivered Secure Services Edge (SSE) service.
But what allows Security Director Cloud to truly operationalize security across the network is that the policy framework is exactly the same, no matter what the form factor or deployment use case is, so policies can easily follow users, applications and devices wherever they go.
Security Director Cloud, with its single UI and policy framework across all firewall deployment use cases, takes much of the operational overhead and risk associated with network transformation out of the equation.
As teams move applications to public cloud environments, they don’t need to recreate or copy over security policies. As teams move to better accommodate remote and in-office users alike, they can use existing Zero Trust access policies and enable them to follow those users wherever they go. And most importantly, they have security visibility across the network, from their edge to their many centers of data.
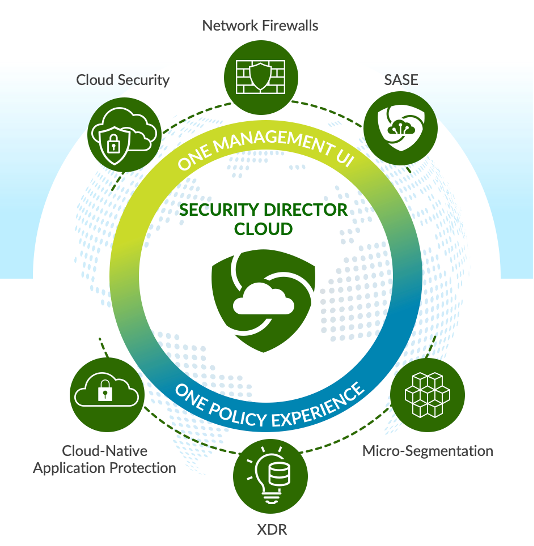
-
- Cloud-delivered security (SSE)
- On-prem campus and branch NGFW
- Public cloud security
- Data center gateway
- Data center interconnect
- East-west traffic via micro-segmentation
- Securing IoT devices
- OT security within ICS/SCADA environments
- Extended detection & response (XDR)
Our ability to do this has landed us first-to-market in accommodating an overarching use case that Gartner is calling “hybrid mesh firewall,” which is an architecture that bridges on-premises and cloud- native security through a single control point. With Juniper, that control point is Security Director Cloud.
Juniper’s “Weaknesses”
We’ve put the bulk of our investments into making sure our technology is top-notch; that it’s built to protect, built to last and most importantly, built so that security teams can accomplish herculean feats without breaking them or their budgets. We’ve done this instead of putting those investments into marketing, unlike other vendors, and we fully believe this is the right decision — would you rather your security solution be popular or actually work?
It has been noted Juniper has a lack of visibility in the market and lacks pace compared to competitors. However, instead of focusing on sitting with the popular clique, we’ve focused on the substance of our technology – at the end of the day, that’s what gets the job done.
Juniper has made security acquisitions — most recently, Witesand, a cloud-based NAC company, in early 2022 — and we have what other vendors haven’t accomplished.
In the 12 months between September 2021 and August 2022, Juniper filed more than 245 cybersecurity patents and is ranked 2nd in cybersecurity innovation only to Microsoft. In addition, our innovations in security — such as enabling networking equipment for threat detection and response, encrypted traffic insights using AI-based machine learning to detect malicious traffic to detect threats while keeping privacy intact and IoT fingerprinting — are natively built within our JunOS operating system.
This means new capabilities that address emerging use cases don’t take 2-3 years to integrate into our existing portfolio. Our customers can leverage their existing Juniper deployments to use those new features immediately.
Recognized as a Challenger, and Leading Where it Matters
We believe Gartner’s recognition of Juniper Networks in the 2022 Magic Quadrant™ for Network Firewalls is a testament to both the journey Juniper has been on over the past four years and how much we accomplish for our customers today: unbroken visibility, extensible Zero Trust policies and operationalized security for the entire network.
Read a free copy (no form-fill necessary) of Gartner’s 2022 Magic Quadrant for Network Firewalls.
Gartner Disclaimers
Gartner Magic Quadrant for Network Firewalls, by Rajpreet Kaur, Adam Hils, Thomas Lintemuth, 19, December, 2022.
Gartner Critical Capabilities for Network Firewalls, by Rajpreet Kaur, Adam Hils, 17 January 2022.
Gartner and Magic Quadrant are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner®, Magic Quadrant and Peer InsightsTM are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.

























