Validation is always reassuring, especially when you’ve been told it can’t be done. Stepping off of the beaten path, going against the status quo and doing something different isn’t easy.
Gitpaste-12 is a new worm recently discovered by Juniper Threat Labs, which uses GitHub and Pastebin for housing component code and has at least 12 different attack modules available. There
Juniper Threat Labs (JTL) has a network of sensors throughout the world that we use to monitor cyber security threats. These threats can range from Brute Force attacks against logins,
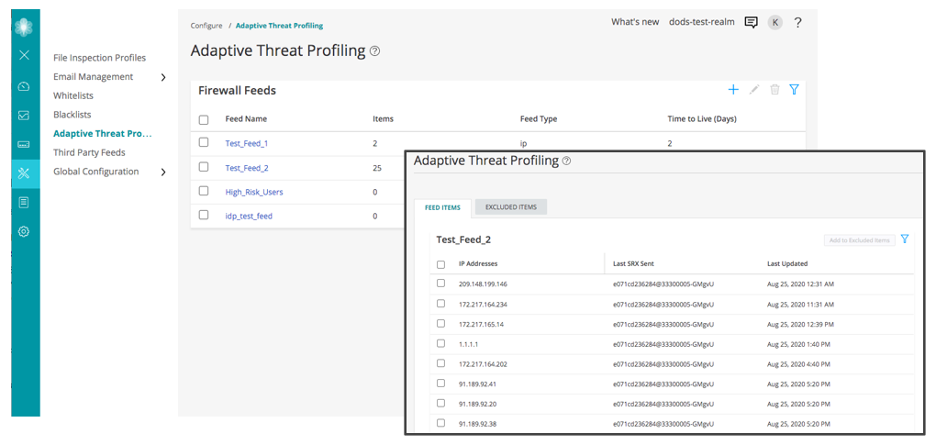
Do you know who and what is on your network? Throughout my career, whenever I’ve asked this question to IT security leaders, it has almost always been met with an
Juniper Threat Labs identified several malware campaigns that rely on a pastebin-like service for its infection chain. The domain in question is paste.nrecom.net. The attacks usually start as a phishing
Mirai has become such a common discovery in the wild that it is beginning to be disregarded as white noise, played off as a simple attack that should be readily
IT and healthcare providers were targeted in late 2019 by a new ransomware campaign calling itself Zeppelin, a variant of the Buran ransomware-as-a-service family. According to researcher Vitali Kremez, Zeppelin

Today, Juniper Networks, in collaboration with Schweitzer Engineering Laboratories (SEL Inc.) and Dragos Inc., announced the Converged Industrial Edge; a communications architecture designed to reduce cybersecurity risk, lower operational expense
In our previous blog about IcedID, we explored some of the changes in the malware and how it tries to evade detection. We also detailed how threat actors took advantage
In cybersecurity, the difference between a small event that requires minor investigation and a massive data breach can simply boil down to how strong the integration is between two of























