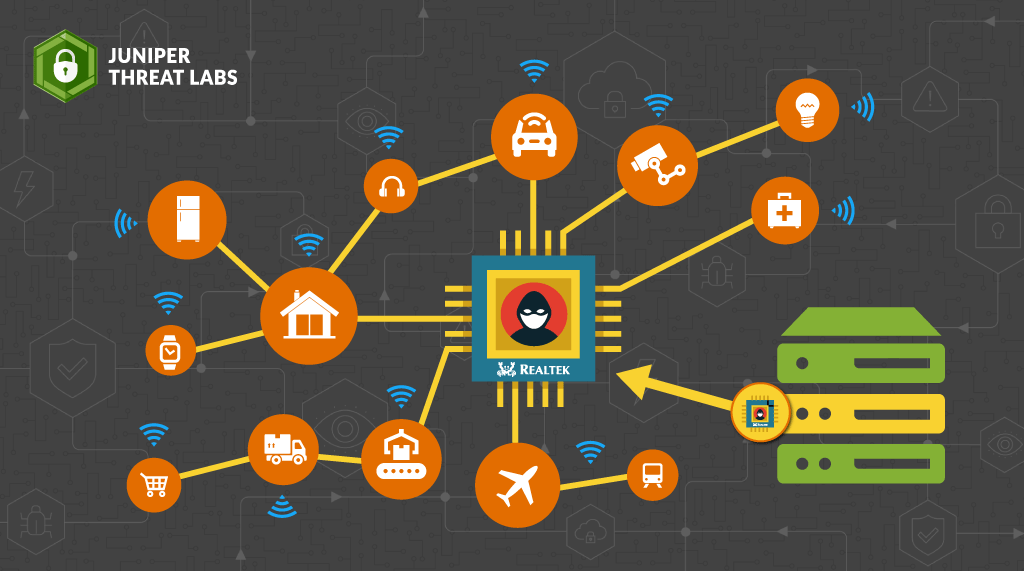
As we predicted in last week’s post, threat actors continue to utilize new Realtek vulnerabilities disclosed by IoT Inspector Research Lab to distribute malware. Starting on August 19th, Juniper Threat
Juniper Threat Labs continuously monitors in-the-wild network traffic for malicious activity. Today, we have discovered an active exploitation of a vulnerability that was disclosed just 2 days ago. CVE-2021-20090 is a vulnerability that was discovered by

Nearly everything we do on the network involves applications, from web browsing and chat to mobile games and services that allow us to get work done. Applications store, process and

From the very beginning, our destiny at Juniper Networks has been tied to our expertise with silicon. While the storied history and evolution of our application-specific integrated-circuits (ASICs) are quite

2020 was a busy year for cybercriminals. As COVID-19 drove a dramatic acceleration of digital transformation, almost everything moved online. Today, cybercriminals have more potential attack targets than ever before.

When I was in the eighth grade, I wrote an essay on my hopes and dreams which centered on being elected the first woman President of the United States. At

Quantum key distribution (QKD) is a technology that relies on quantum mechanics to share secret information between two distant locations. To many of us, quantum mechanics are incomprehensible – even
The COVID-19 pandemic and the rise of remote work have accelerated digital transformation and the shift to the cloud. It’s an industry turning point. Gartner predicts that by 2022, more

SASE is everywhere. Recently, Secure Access Service Edge (SASE) has taken off, seemingly overnight. This term, coined by Gartner, describes the convergence of networking and security into an architecture that
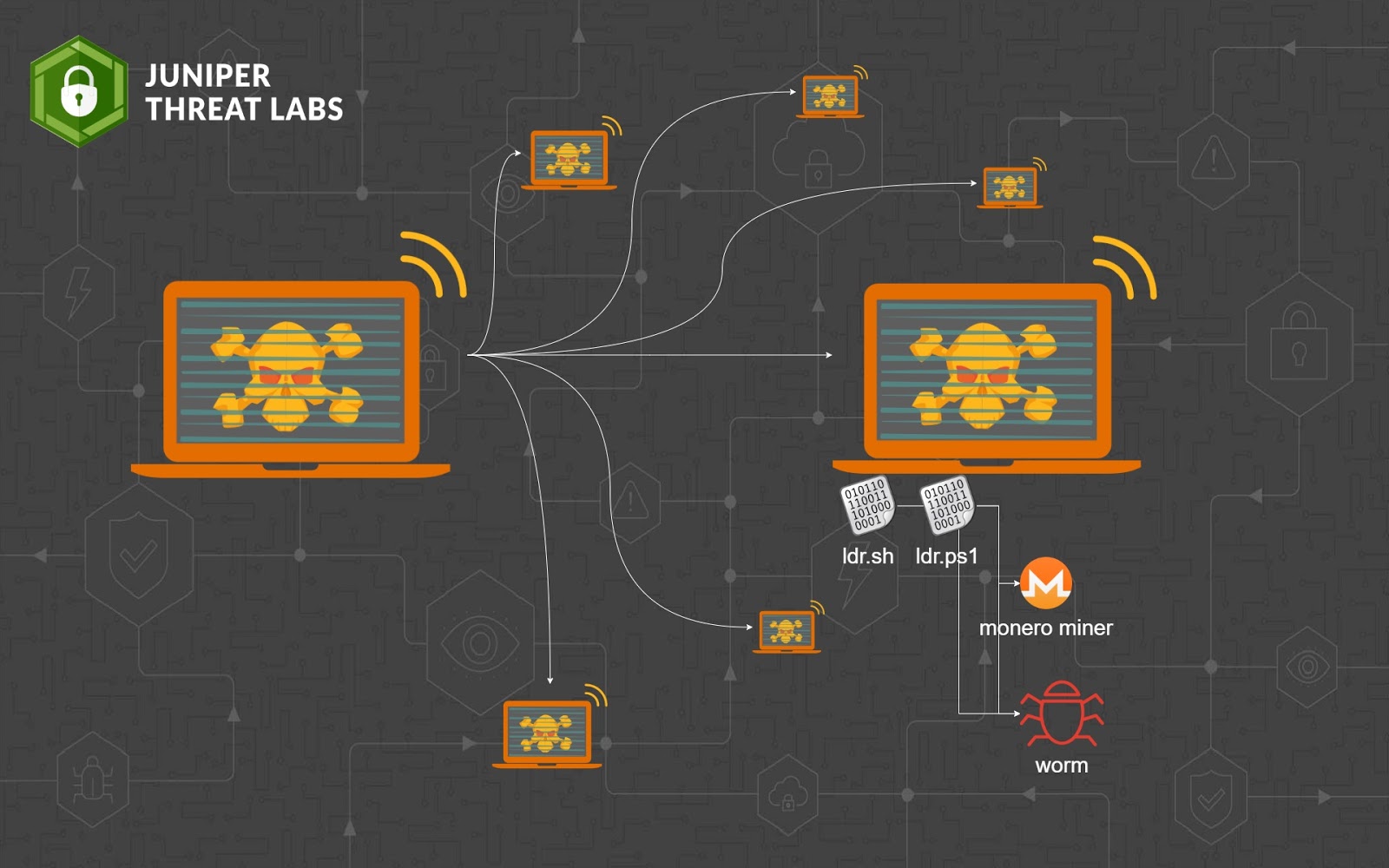
On March 4, 2021, Juniper Threat Labs identified a surge of activity of the Sysrv botnet. The botnet spread itself into Windows and Linux systems by exploiting multiple vulnerabilities, which