Juniper Networks and AWS are pleased to announce the integration with AWS’ Cloud WAN Tunnel-less solution powered by Juniper Session Smart™ Routing. The AWS Cloud WAN Tunnel-less solution is a
Unless you were catching up on some much-needed sleep, you know by now that Apple unveiled its new iPhone on September 12, 2023. The iPhone 15 Pro and Pro Max

When it comes to data center networks, new solutions are released every year, but the biggest challenges remain unsolved: nonstop complexity as new technologies get layered on top of the
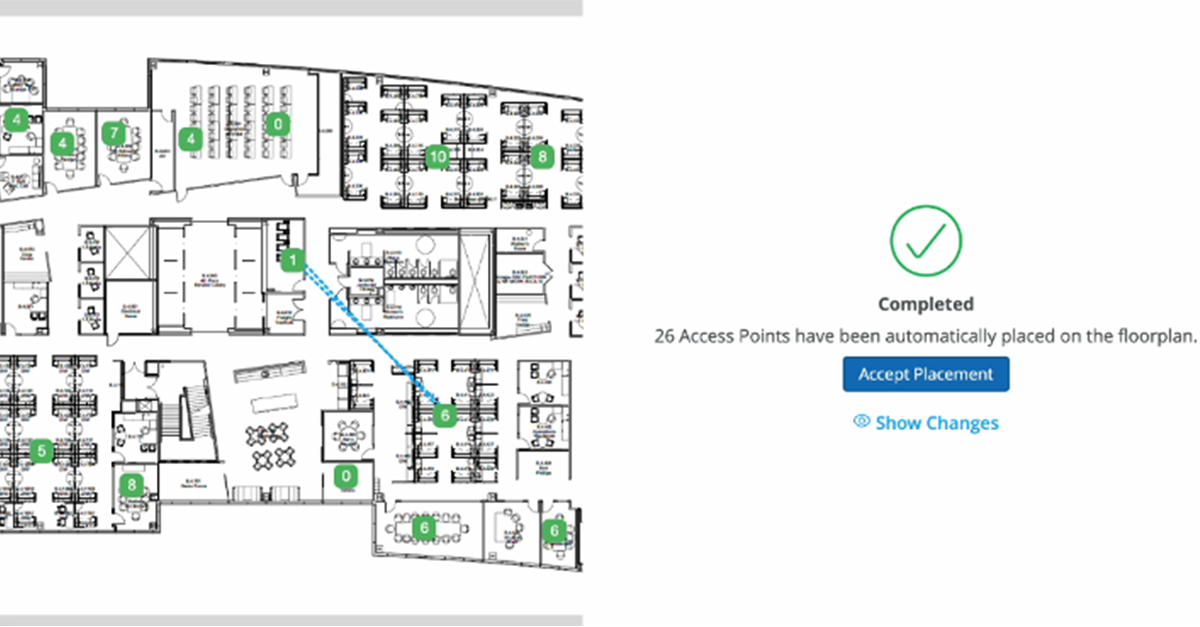
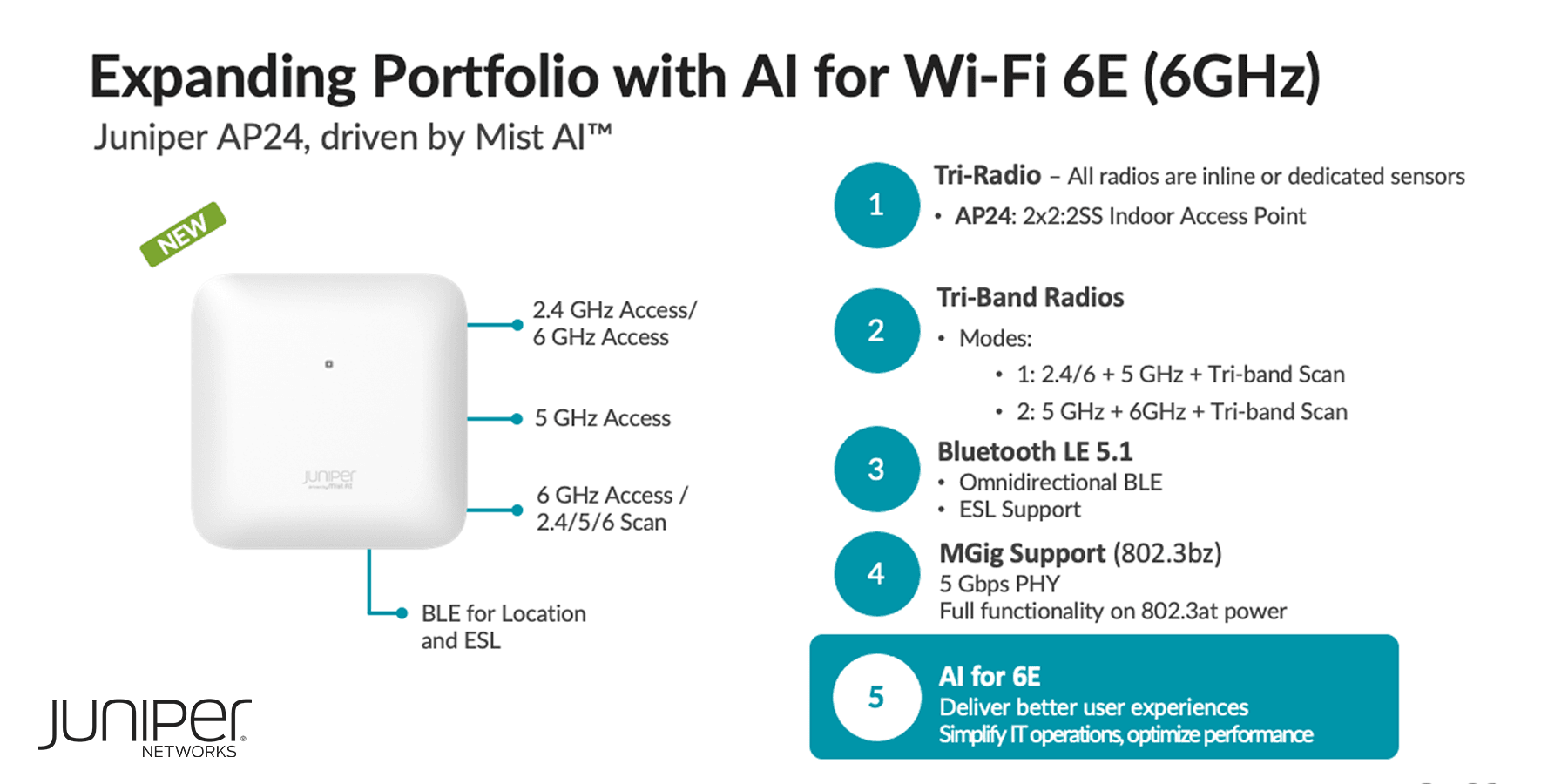
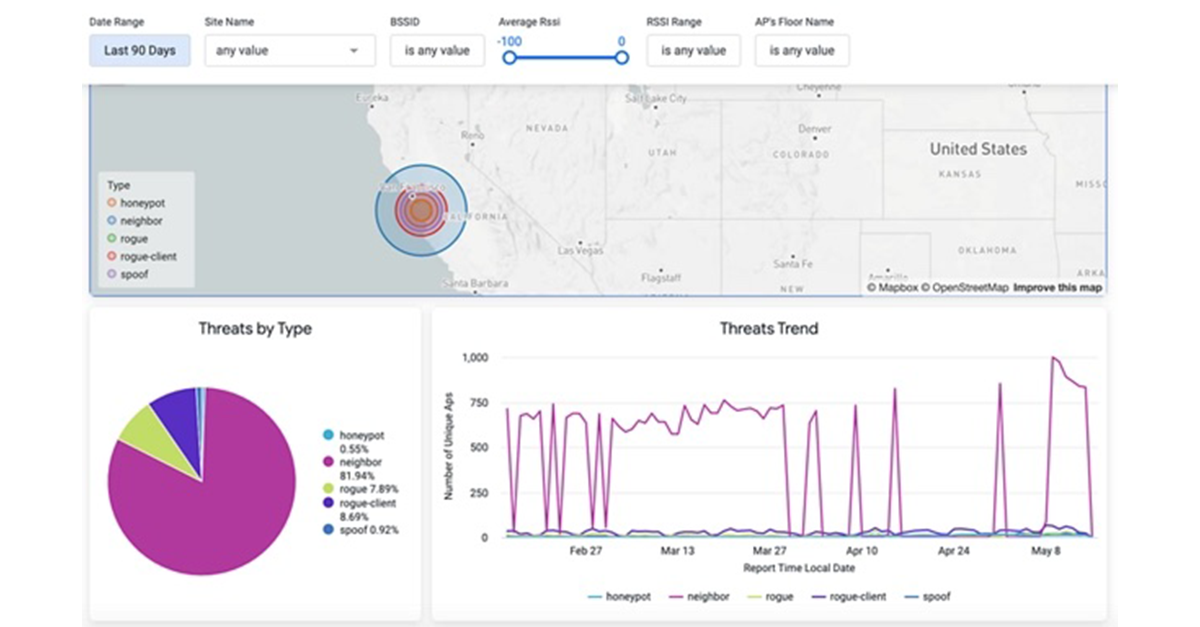
As part of Juniper Networks’ ongoing commitment to Experience-First Networking, we’re excited to announce a significant advancement to our AI-driven Juniper Mist Wi-Fi Assurance capabilities. Our latest AIOps additions –
In the realm of digital transformation, the IT networking team plays a crucial role in orchestrating the connectivity foundation that drives the transformation process. By architecting and managing networks that
At Juniper Networks, we’re sometimes asked why we talk about session awareness while our competitors talk about application awareness. After all, aren’t applications the most important topic in networking? As
Artificial Intelligence (AI) has been around for a while, having first been turned into a field of study in 1959 at Dartmouth College (a Juniper Mist Customer!). Yet in the past
Juniper Networks announced another groundbreaking capability within its Virtual Network Assistant (VNA), Marvis, designed to address a widespread problem in many enterprise networks – bad video conferencing experiences. All too
In today’s fast-paced and interconnected world, businesses and organizations rely heavily on robust network infrastructures to enable seamless communication, collaboration and data access. As the demand for efficient networking solutions
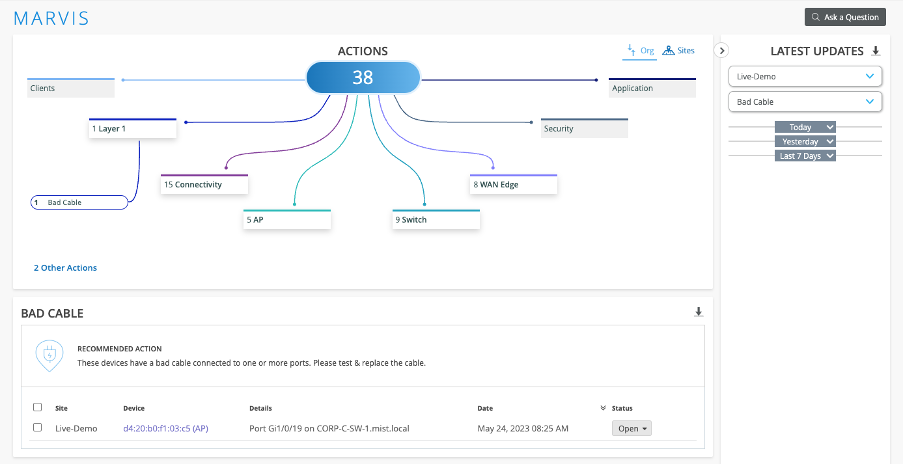
The Problem of Traditional Troubleshooting Sometimes problems occur unexpectedly. Other times problems grow in the shadows, lurking for months or years unnoticed. They slowly chip away at users’ service expectations























