At Juniper Networks, we’re sometimes asked why we talk about session awareness while our competitors talk about application awareness. After all, aren’t applications the most important topic in networking?
As Abilash Menon—the Chief Architect of our Session Smart Networking technology—explains it, “With session awareness, you automatically get application awareness.” (And, we’ll argue, you get a whole lot more.)
Let’s examine how we got here, and then take a look under the hood to see why this is so and why it matters.
Application Awareness
It’s a familiar cliché to say that networks exist to support applications. After all, what else would they be doing? The term “application awareness” has been used liberally for decades.
By the turn of the century, nearly all networking equipment suppliers claimed application awareness as a core strength. Every vendor’s content was filled with assertions that their routers, switches and firewalls could identify, understand—and ultimately optimize—specific applications running over enterprise networks.
Mostly, these declarations contained at least a kernel of truth. Networking equipment software can certainly distinguish between various applications, such as enterprise planning or customer management software, VoIP or video calls, file transfers and more. And networks can indeed adjust how to handle different traffic types, prioritizing mission-critical applications and applying specific quality of service (QoS) settings tuned to the needs of each application.
However, policies that maximize bandwidth or reduce latency for real time applications, such as video conferencing, may starve the needs of other applications, such as file transfers or web browsing. And the users served by these applications are themselves in different locations with unique performance requirements.
SD-WANs (Sort of) to the Rescue
Since Marc Andreeson’s Why Software is Eating the World first appeared in 2011, wide area networking has provided many examples of software’s ability to transform industries. By 2015, SD-WANs were on the scene and these useful overlays provided some ability to map applications to users in a broad and aggregated sense.
A key reason why the mappings weren’t exact was that these SD-WANs were built using tunnel encapsulation. Most notably, IPsec was developed to authenticate and encrypt packets for secure transmission across an IP network.
IPsec proved to be a cost-effective way to securely handle traffic in dynamic multipath environments for organizations, user groups and applications—both asynchronous (such as database access) and real-time (such as telephony).
However, as ACG Research Analyst Ray Mota has pointed out, the proliferation of these tunnels hogged bandwidth while causing numerous problems in operational complexity.
Limited Visibility Inside Tunnels
Depending on how they’re constructed, tunnels can enforce application policies, but it’s impractical to implement separate tunnels for every application. So tunnels typically contain multiple applications as well as multiple groups of users, and thus cannot reveal very much about what’s working well and what isn’t.
Some users are happy, and others are not, and administrators only have a crude sense of why this is so. This opacity and complexity is shown in the “bowl of spaghetti” depicted in Figure 1.
Figure 1: The User Experience is Hidden in Tunnels
In tunnel-based architectures, the quality of service (or experience) is only gauged—and can only be acted upon—at the tunnel level. But different applications within the tunnels have different requirements and may be performing poorly (or well) for reasons that can’t be fully discerned.
Furthermore, the user experience can only be measured—or adjusted—in the aggregate, which often doesn’t help individual users.
How Sessions Add User Context to Applications
To see how Session Smart Networking overcomes these limitations, it’s useful to take a peek into how a session is actually created. To initiate a session, a Juniper® Session Smart™ Router (SSR) embeds a small metadata cookie into the first packet of a symmetric bidirectional connection. The information in this cookie includes:
- Source and Destination Addresses and Ports: These fields, along with the TCP or UDP protocol, form what is called the 7-tuple and identify the specific user and server for the session.
- Source Tenant: Identifies a group that the user belongs to—perhaps a department such as finance or engineering.
- Service Name: Identifies the application being accessed by the user.
There are other fields[1] for authentication, encryption and managing the session’s state, which tells us what is going on with the application at a specific point in time. This seemingly simple mechanism is how operating at a session-awareness level adds critical user context to enhance application awareness.
An example of a session’s metadata is shown in Figure 2, which establishes a session for a user in the finance department accessing an inventory application.
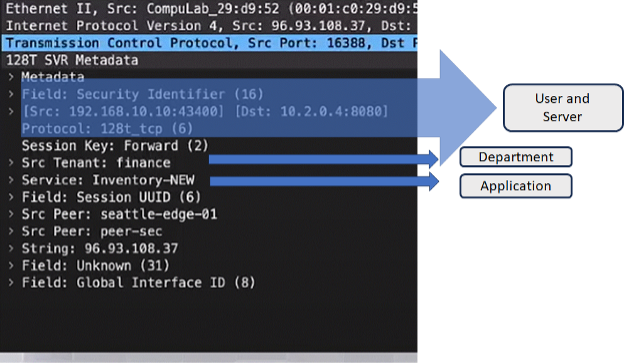
Figure 2: Metadata for a Session (Wireshark Capture)
In addition to being simple to envision and configure, the fact that this is done without the use of tunnels—where multiple sessions would have to be maintained simultaneously—makes this technique much more scalable than tunneled environments.
Top 3 Advantages of Session vs. Application-Awareness
Although it can oversimplify things to talk about a technology’s “top 3” (or however many) characteristics, this shorthand provides a useful way to express the advantages of a Session Smart network over an application-aware network.
Here are the top three reasons that tunnel-free, session-intelligent networks improve upon application awareness:
- Session intelligence provides user experience guarantees along with application performance assurances. Traffic isolation and treatment are far more reliably applied to each application per user. Teams can guarantee that policies do exactly what they are supposed to, unaffected by policies for other applications. Tunneled implementations can give no such assurances because the fates of some applications are shared with others.
- This simple design enables huge scale. Sessions for tunnels can quickly be exhausted when employees have many applications open, and they are bundled in awkward and unpredictable ways with tunnels. With session intelligence, sessions tying an application to a user are addressed individually for as long as the session is open. This removes the complexity of tracking large numbers of tunnels.
- Session-intelligent networks are inherently secure with a Zero Trust, “deny-by-default” approach to all new traffic accessing the network. SSR routers fully encrypt and route traffic securely without the excess encapsulation overhead and other problems caused by tunnels.
A Session Smart (and tunnel-free) SD-WAN can act on a per-application, per-user basis and thus can prevent spurious traffic from interfering with an application’s performance. The user thus enjoys a superior experience. Application visibility and control are far more adjustable in this environment, ensuring the highest possible performance for all applications (Figure 3).
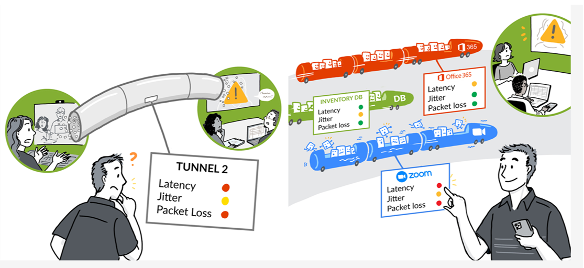
Figure 3: Optimizing Every Session for Each User
Characteristics such as latency, jitter and packet loss can be monitored for individual sessions, each serving only one user and one application. In the example shown here, three different applications—Office 365, a local inventory management system, and Zoom—can be optimized individually based on their current state, without impacting other users and applications. This is not possible with tunnel-based SD-WANs.
As this level of granularity is completely unique in the industry, it raises the consideration of scale. The Juniper Session Smart Networking environment scales to millions of sessions, far beyond the levels of tunneled architectures and the requirements of large, distributed enterprises with thousands of users.
Session Smart’s deny-by-default approach to session access provides full Zero Trust security. Whenever any SSR router cannot tell if it has already seen the session, the router immediately determines whether the client is allowed to access the server. If not, the session is not started.
And finally, all of the Session Smart technology discussed here is integrated into Juniper AI-Driven SD-WAN. With Juniper Mist WAN Assurance, this rich telemetry is fed to the Mist AI engine, which provides actionable insights into network health.
Resources
The following resources are available for more detailed information on how Session Smart Routing works, and how it brings application assurance for the best quality user experience in wide-area enterprise networking.
Feature Briefs on Secure Vector Routing
White Papers
For a more complete treatment on the importance of sessions and the limitations of tunnel-based networking, download the new white paper, Session Intelligence in a Tunnel-Free SD-WAN.
[1] These are described in Justin Melloni’s feature brief on Secure Vector Routing, Part 2: Packet Walkthrough.
For a comprehensive description of all metadata fields, see the Internet Draft for Secure Vector Routing.
























