In a previous blog on Getting Started with Modern Data Center Fabrics, we discussed the common modern DC architecture of an IP fabric to provide base connectivity, overlaid with EVPN-VXLAN to provide end-to-end networking. We have also discussed various overlay design options, including Bridged Overlay, Centrally-routed Bridging (CRB), Edge-routed Bridging (ERB) and Collapsed Spine/Core. In this blog, we discuss the connection point into and out of the fabric: border devices.
What is a Border Device?
Just as the name suggests, border devices are located at the edge, or border, of a data center fabric. In EVPN-VXLAN terms, these devices also act as the virtual tunnel end point (VTEP) for north-south traffic entering and exiting the fabric.
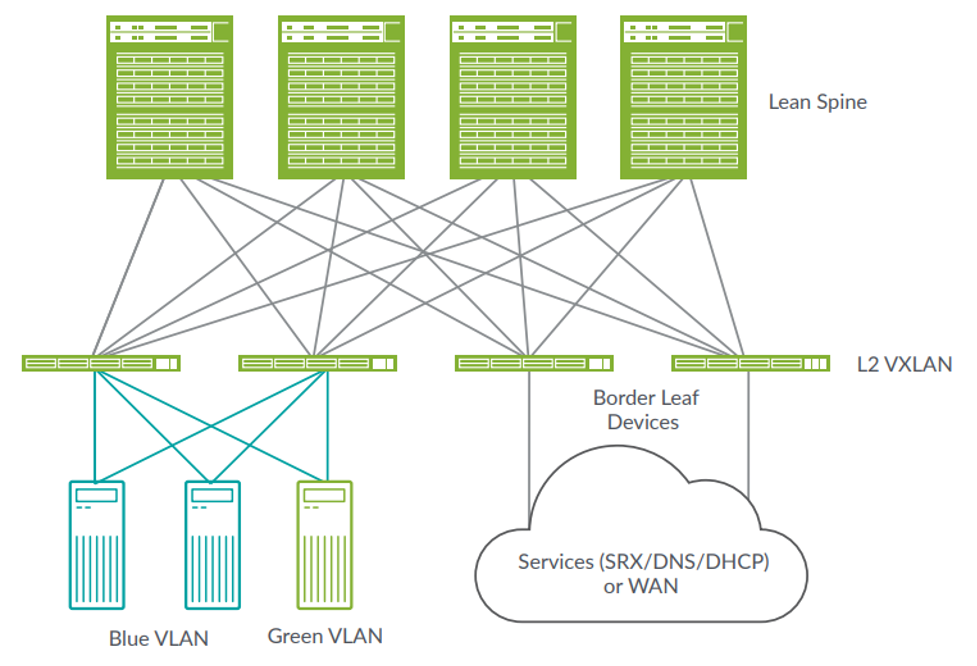
One approach to implementing the border function is at the leaf layer of the fabric. As shown below, these ‘border leaf’ devices typically have the sole purpose of providing connectivity and handing off traffic to one or more external devices that provide additional functionality for the fabric.
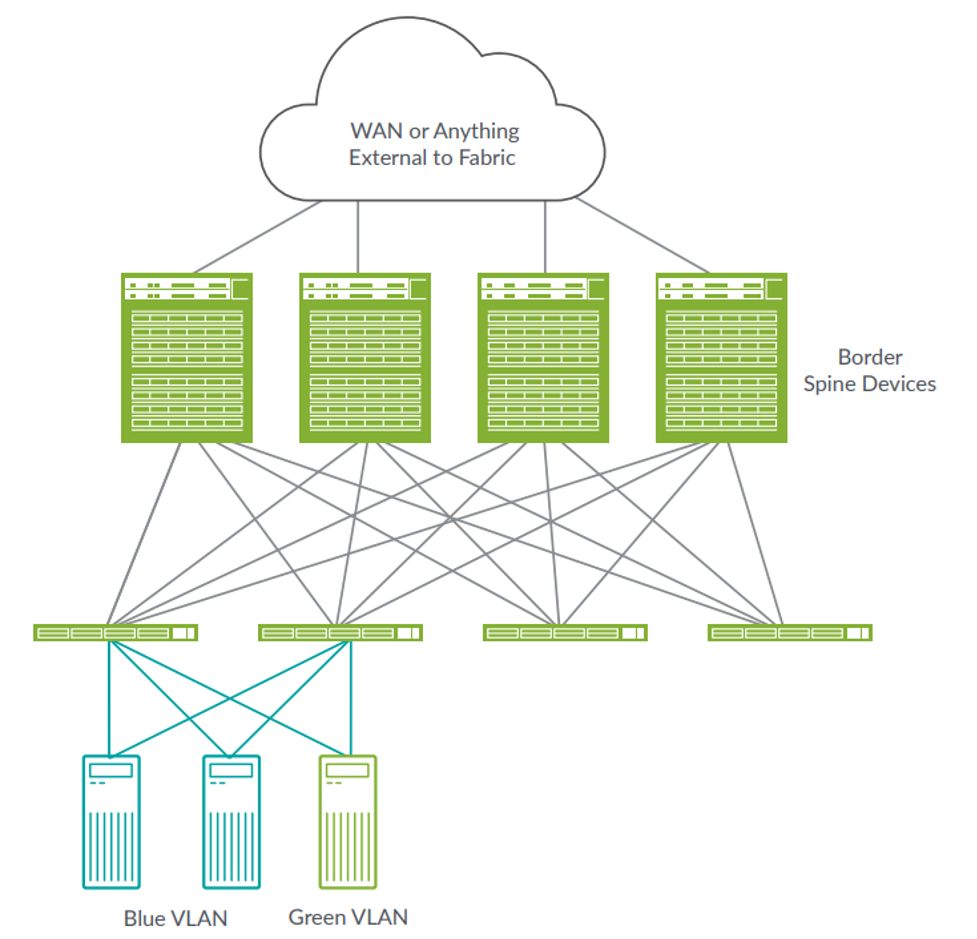
Another approach to implementing the border function is at the spine layer of the fabric. As shown below, these ‘border spine’ devices are positioned such that they typically handle both the spine and border role.
Why use Border Devices?
Border devices connect in-fabric traffic to services, which is a leading reason for their use. Architecturally referred to as physical network functions (PNFs), these are typically security devices that can provide traffic filtering, NAT and IDP, or other appliances and servers that can provide load balancing, DNS, DHCP and so on.
Border devices also interconnect the fabric with other networks, such as the WAN or another data center.
Border Devices and DC Gateway
We have two design options when using border devices to support traffic flow between the fabric and other networks.
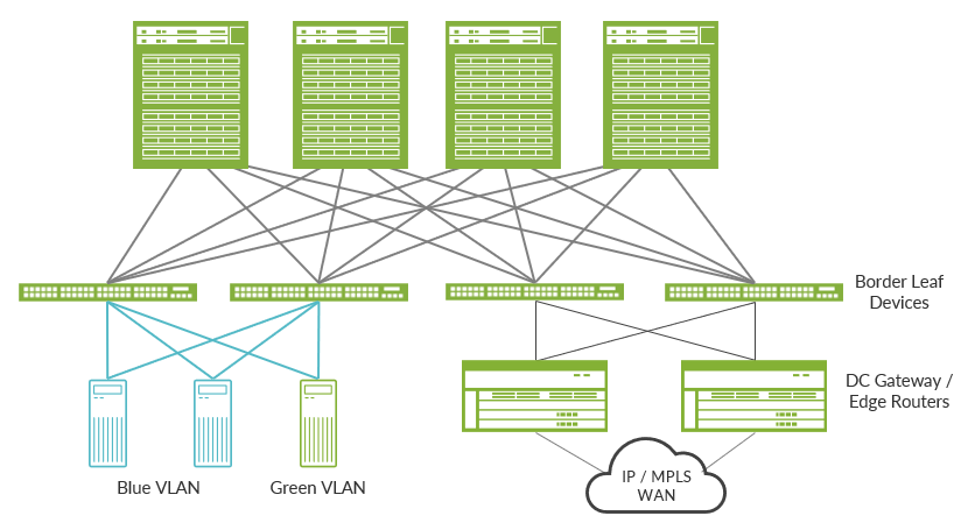
One option is to use dedicated edge routers to handle the DC gateway function, as shown below and have the border devices hand off traffic to these routers.
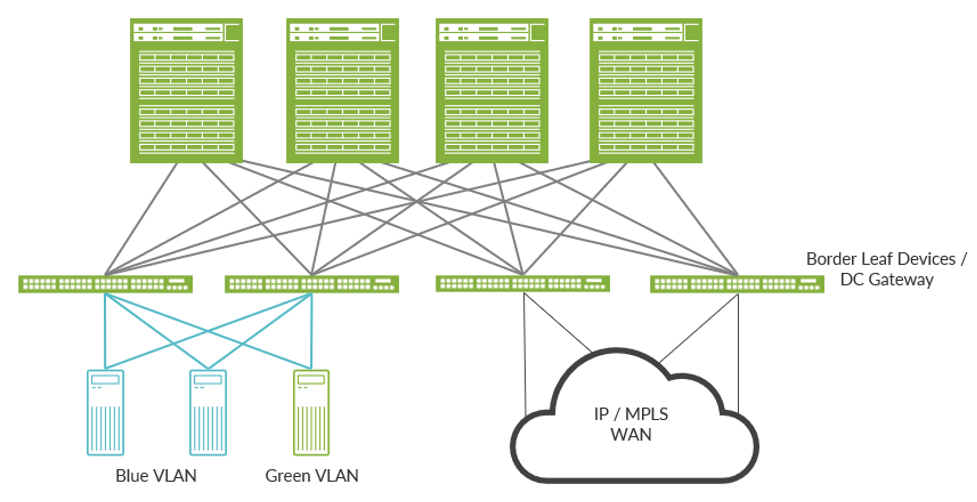
The other option is to ‘collapse’ the DC gateway function onto the border devices, as shown below.
So, which option is best for you? Here are some considerations:
- Traffic burstiness – consider deep buffer platforms to handle DC gateway functionality as north-south traffic is bursty and oversubscription is typically high at the WAN edge (since WAN links are expensive).
- Multicast – if needed, be sure the DC gateway platform can handle multicast traffic in and out of fabric.
- Host scale – border devices typically maintain reachability to every host in the fabric, so ensure they can scale to meet your requirements.
Implementing Border Functionality
Your border design does not directly affect how you build the main DC architecture. As described in Getting Started with Modern Data Center Fabrics, the EVPN-VXLAN fabric configuration elements still include:
- BGP-based IP fabric as the underlay
- EVPN as the overlay control plane
- VXLAN as the overlay data plane
With these elements in place, the additional configuration to add border functionality is relatively straightforward: Simply add a routing instance and related elements on the border devices to enable the handoff of traffic in and out of the fabric.
With that, we’ve covered the basics for adding border devices and functionality to your EVPN-VXLAN architecture. There are plenty of other details to consider but this will get you started. We’ll discuss other architecture elements in a future blog. In the meantime…
Keep Going
To learn more, we have a range of resources available.
Read it – Whitepapers and Tech Docs:
Learn it – Take a training class:
- Juniper Networks Design – Data Center (JND-DC)
- Data Center Fabric with EVPN and VXLAN (ADCX)
- All-access Training Pass
Try it – Get Hands-on with Juniper vLabs, a (free!) web-based lab environment that you can access any time to try Juniper products and features in a sandbox type environment, including an IP Fabric with EVPN-VXLAN topology.
























