In last week’s blog, we explained that a Segment Routing (SR) path is an ordered list of segments. We also explained that a segment is an instruction that causes a packet to traverse one or more links.
This week, we will discuss a class of SR implementations that leverage MPLS. We refer to these implementations as SR-MPLS. A thorough understanding of SR-MPLS will help you understand next week’s blog, in which we explain how SR supports traffic engineering applications.
Overview
In SR-MPLS, SR paths are encoded as MPLS label stacks. Each label stack entry represents a segment in the SR path. In this week’s blog, we will explain how MPLS labels are used to encode adjacency and prefix segments.
Adjacency Segments
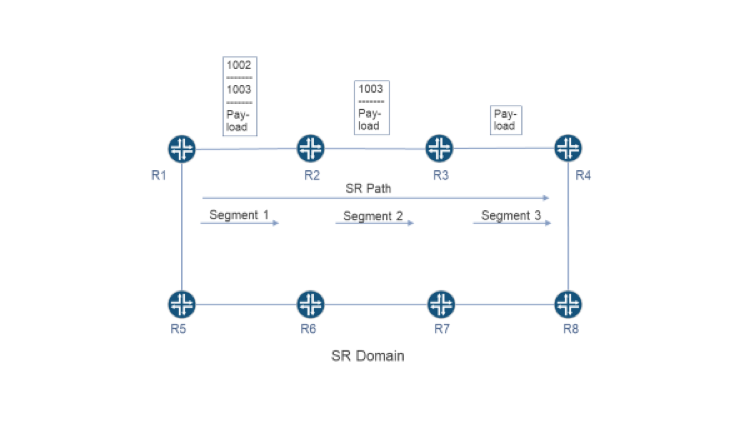
In Figure 1, an SR path connects R1 to R4. The SR path contains three adjacency segments. Segment 1 causes packets to traverse Link R1->R2, while Segment 2 causes packets to traverse Link R2->R3. Segment 3 causes packets to traverse Link R3->R4.
When R1 receives a packet from outside of the SR domain, it subjects the packet to policy. Policy may cause R1 to forward the packet through the SR path shown in the figure. When this occurs, R1 imposes an MPLS label stack containing two entries. The entry at the top of the stack represents Segment 2 and carries MPLS label 1002. The entry at the bottom of the stack represents Segment 3 and carries MPLS label 1003.
Having imposed an MPLS label stack, R1 forwards the packet through Segment 1 (i.e., Link R1->R2). When the packet arrives at R2, R2 examines the topmost label (i.e., 1002) and searches for a corresponding entry in its Forwarding Information Base (FIB). The corresponding FIB entry includes an instruction (i.e., POP) and a next-hop (i.e., R3). Therefore, R2 pops the topmost entry from the label stack and forwards the packet through Segment 2 (i.e., Link R2->R3).
When the packet arrives at R3, R3 examines the remaining label (i.e., 1003) and searches for a corresponding entry in its FIB. The corresponding FIB entry includes an instruction (i.e., POP) and a next-hop (i.e., R4). Therefore, R3 pops the remaining entry from the label stack and forwards the packet through Segment 3 (i.e., Link R3->R4). The packet arrives at R4 without MPLS encapsulation.
Prefix Segments
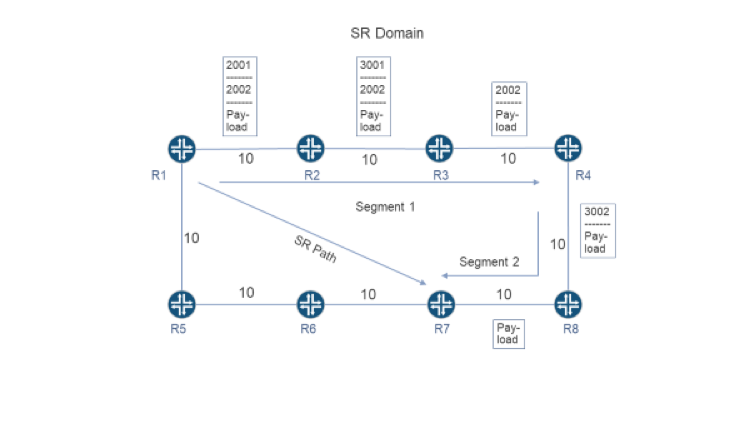
In Figure 2, an SR path connects R1 to R7 via R4. The SR path contains two prefix segments. Segment 1 is a prefix segment that causes packets to traverse the least cost path from R1 to R4. Segment 2 is also a prefix segment and it causes packets to traverse the least cost path from R4 to R7. In this network, all links are configured with the same IGP metric (i.e. 10). Therefore, the least cost path from R1 to R4 traverses links R1->R2, R2->R3 and R3->R4, while the least cost path from R4 to R7 traverses links R4- >R8 and R8->R7.
When R1 receives a packet from outside of the SR domain, it subjects the packet to policy. Policy may cause R1 to forward the packet through the SR path shown in the figure. When this occurs, R1 imposes an MPLS label stack containing two entries. The entry at the top of the label stack represents Segment 1 and carries the label 2001. The entry at the bottom of the label stack represents Segment 2 and carries the label 2002.
Having imposed an MPLS label stack, R1 forwards the packet into Segment 1 via Link R1->R2. When the packet arrives at R2, R2 examines the topmost label (i.e., 2001) and searches for a corresponding entry in its FIB. The corresponding FIB entry includes an instruction (i.e., SWAP – 3001) and a next-hop (i.e., R3). Therefore, R2 overwrites the topmost label with a new value (i.e., 3001) and forwards the packet to R3.
When the packet arrives at R3, R3 examines the topmost label (i.e., 3001) and searches for a corresponding entry in its FIB. The corresponding FIB entry includes an instruction (i.e., POP) and a next-hop (i.e., R4). Therefore, R3 pops the topmost entry from the label stack and forwards the packet into Segment 2 via Link R3–>R4.
When the packet arrives at R4, R4 examines the remaining label (i.e., 2002) and searches for a corresponding entry in its FIB. The corresponding FIB entry includes an instruction (i.e., SWAP – 3002) and a next-hop (i.e., R8). Therefore, R4 overwrites the remaining label with a new value (i.e., 3002) and forwards the packet to R8.
When the packet arrives at R8, R8 examines the remaining label (i.e., 3002) and searches for a corresponding entry in its FIB. The corresponding FIB entry includes an instruction (i.e., POP) and a next-hop (i.e., R7). Therefore, R8 pops the remaining entry from the label stack and forwards the packet to R7 without MPLS encapsulation.
Penultimate Hop Popping (PHP) and the Explicit Null Label
In the examples above, each segment executes PHP procedures. When a packet traverses a segment, the segment’s penultimate node pops the label associated with the segment.
If the SR path contains another segment, yet to be traversed, the current segment’s egress node is also the ingress node of the next segment. In this case, the packet arrives at that node with the next segment’s label exposed on the top of the stack. If the SR path does not contain another segment, yet to be traversed, the segment egress node is also the path egress node. In that case, the packet arrives at the path egress node without MPLS encapsulation.
In some cases, the final link in the SR path may not be able to carry the packet without MPLS encapsulation. For example, the packet may be IPv6, while the link supports IPv4 only. In order to prevent this problem, the SR ingress node can add an MPLS Explicit Null label to the the MPLS label stack.
When the penultimate node in the final segment pops the label associated with the final segment, it exposes the Explicit Null label. It then forwards the packet to the path egress node. The path egress node pops the Explicit Null label and continues to process the packet.
Conclusion
This week, we learned how SR-MPLS encodes SR paths as MPLS label stacks. We also learned how SR- MPLS uses its FIB to process packets.
Next week, we will learn how SR can be applied to traffic engineering applications.
Join us on June 10 (US/EMEA) and June 11 (APAC) to discover how network architectural shifts create business value at our Juniper Virtual Summit for Cloud & Service Providers. Register here.