Crypto ransomware seems to be a never-ending threat in today’s cyber world. It’s comparable to the “Kaiju” in the 2013 Hollywood blockbuster, Pacific Rim. One crypto ransomware dies and another is born that has more evolved features. The second half of 2017 witnessed back-to-back outbreaks of Wannacry, Petya, NotPetya and BadRadbbit ransomware.

ransomware
But, we do not have to rely exclusively on security software to defend ourselves. Sometimes, the software already installed on our systems and proper configuration of our operating system can save the day.
Let’s go through some of the simplest things anyone can do on their Windows PC to prevent or limit the damage of a crypto ransomware attack.
Software Updates
Operating systems and all installed software should be updated on a regular basis. WannaCry and Petya exploited a vulnerability in SMB2 on Windows OS to spread across the network, even though a patch to close that vulnerability was available for months. Many of the ransomware and other malware are downloaded after being successfully exploited using exploit kits. The latest exploit kits like Angler and Neutrino contain exploits for various Adobe flash versions, Sun Java and Internet Explorer. Unpatched software may lead to your computer being compromised.
Most applications have an auto update capability – make sure this is enabled. Alternatively, you can update your applications manually by typing “update” in the Windows search bar and selecting “software update”.
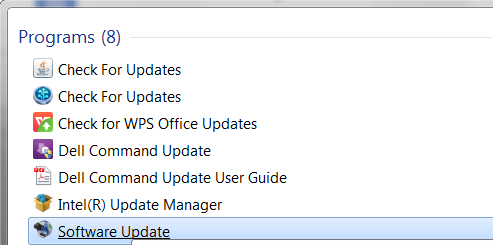
software update
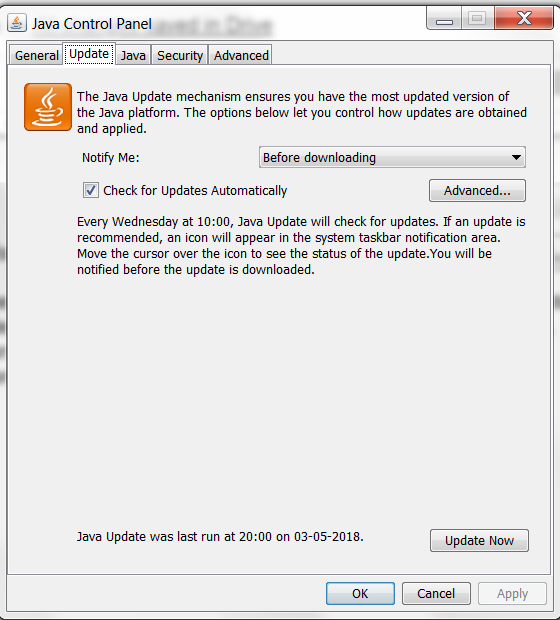
java update
System Configuration
Windows has lot of features. Many of these features are have default settings for a better user interaction . Changing these default settings can sometimes help to elevate security
View File Extension
Ransomware like Locky is distributed through spam emails. To hide the executable, the attachment often has a name similar to “invoice.pdf.exe”. By default, Windows hides the extension of some common file types, so when the victim downloads the executable from the email, it shows as “invoice.pdf” without the .exe extension. You can change this default behavior of folder options to always display file extensions. On Windows 7, you can type “folder options” into the window search option to get the folder option menu and make sure “hide extensions…” is not checked.
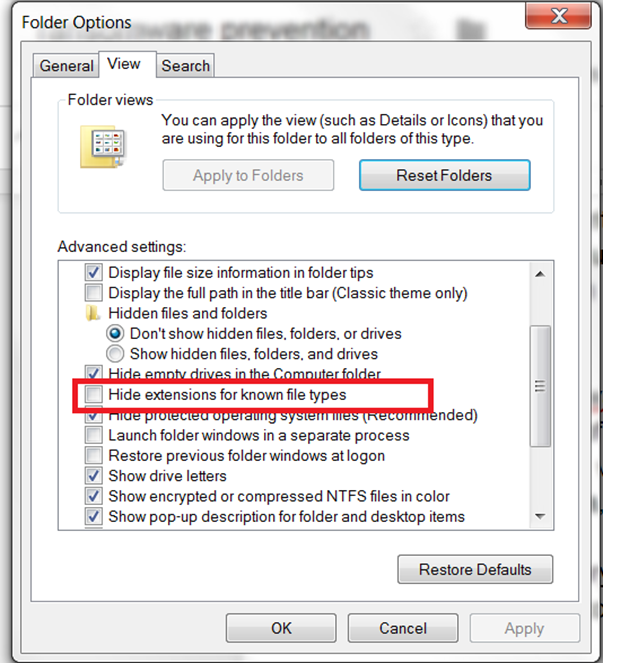
folder option
Additionally, you should only download attachments or click on URLs after carefully inspecting emails. Sometimes, emails can have javascript attachments, which can download other malware or ransomware.
Account Privilege
All programs run within a certain privilege level, typically the privilege level of the user who started the program. In general, user accounts on a Windows system should not have administrator privileges unless absolutely necessary. This will prevent programs for having access to the entire system should your computer be compromised by malware. You can check and change this setting in the user account type settings page.
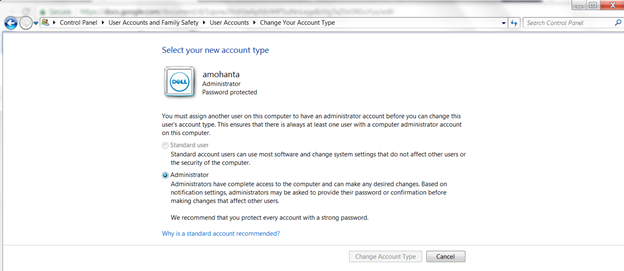
user account setting
User Account Control
User Account Control (UAC) is a Windows feature that prevents unauthorized changes to the operating system. It displays a pop-up window asking for permission whenever a new program tries to make changes. You can find the setting for UAC on Windows 7 by going to control panel->system and security->action center->change user control setting.
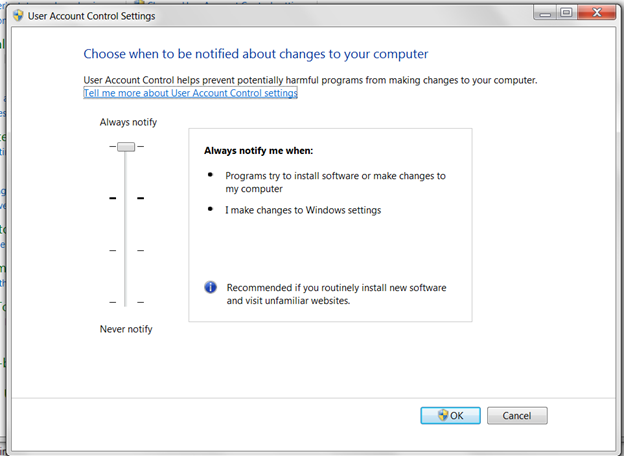
UAC setting
When the UAC setting is set to “always notify”, you will always get a pop-up similar to the one shown in below image whenever a program tries to modify the system settings.Although this may be a bit irritating, it is a useful and preventive feature.
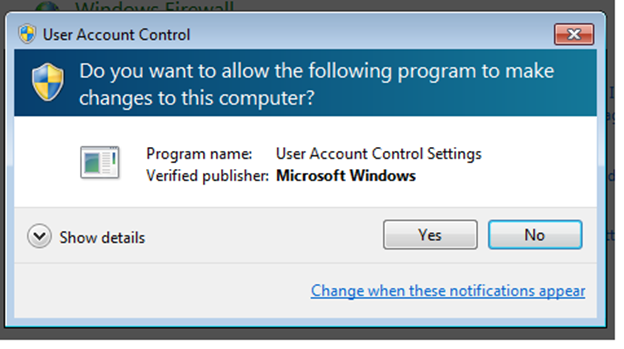
UAC pop up
Disable Autoplay:
The Windows Autoplay feature is meant to facilitate the use of removable media by automatically launching the content upon insertion. When the user inserts a detachable drive into the system, Autoplay executes the script called “autorun.inf” present in that drive. A lot of malware and some ransomware are known to misuse this feature to spread from one machine to another.
As a preventive measure, we recommend disabling this feature. To disable, type in “gpedit.msc” and you will see a window for group policy editor. You can browse through Administrative Templates >Windows Components > Autoplay Policies and turn off Autoplay.
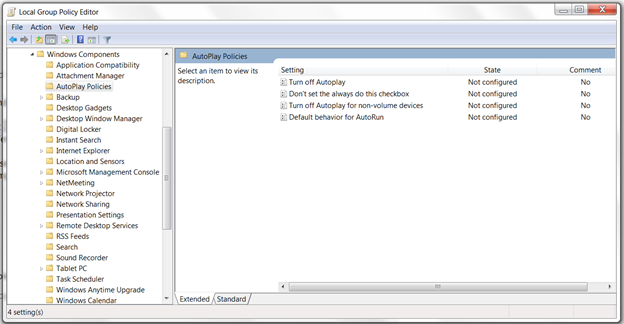
autoplay settings
Security Software Configuration
Many computers have pre-installed anti-virus software, as well as firewalls. These and other security related features need to be configured properly in order to boost the security posture of the device.
Windows Defender:
Windows Defender is an antivirus from Microsoft. All versions of Windows since Windows 7 include Windows Defender. Windows Defender should have real-time protection enabled. This feature scans each new file before it is written to the hard drive and hence can prevent infection. Signatures for all antivirus software, including Windows Defender, should be updated regularly and automatically.
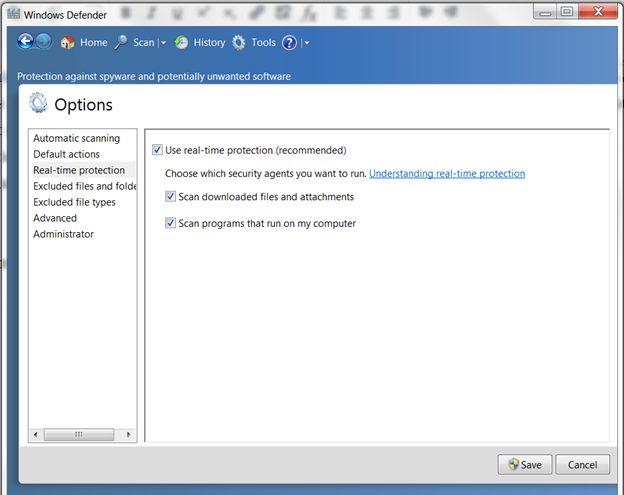
windows defender real time protection
Additionally, the entire system should be scanned on a regular basis. The latest version of Windows Defender has an anti-exploitation feature too. Up until the end of 2017, a lot of ransomware was delivered via exploit kits. Microsoft Enhanced Mitigation Experience Toolkit (EMET) is another tool from Microsoft meant to protect against exploitation. It has the Data Execution Prevention (DEP) capability, Address Space Layout Randomization (ASLR), Structured Exception Handler (SEH Protection) and the Anti-Return Oriented Programming (Anti-ROP) feature. Some older versions of Windows lack many of the anti-exploitation features listed above. For those systems, installing EMET can act as an exploit-prevention shield in that case. In 2017, Windows introduced anti-exploitation features in Windows Defender known as Windows Defender Exploit Guard (WDEG). This blog [https://blogs.technet.microsoft.com/srd/2017/08/09/moving-beyond-emet-ii-windows-defender-exploit-gu…] talks about the introduction of Windows Defender Exploit Guard (WDEG). Other than EMET, WDEG had inducted a few more features into it. Controlled folder access is one such feature that is meant to protect data from ransomware.
By implementing this recommended configuration, you can significantly reduce the possibility of getting infected by ransomware. Should an infection happen anyway, these recommendations will at least limit the scope of the damage to the local user.