Background
On January 19, 2018, Juniper Threat Labs detected a Gootkit banking trojan at one of our customers sites. The file was hosted on a compromised golfing site, namely “carolinalakesgc[.]com”.
The specific urls where this malware where hosted are:
- https://carolinalakesgc[.]com/scripts/get.php
- https://carolinalakesgc[.]com/setup.exe
The threat actor was also able to upload several variations of the malware (different packers) on this compromised host for several days. This then allowed them to modify characteristics of the malware in order to avoid detection.
We observed that the threat actors were also active during this time, as they compromised another site to host this banking trojan.
- https://modamixfashion[.]com/wp-includes/pomo/get.php
- https://modamixfashion[.]com/wp-admin/flash/get.php
This malware uses some unique anti-analysis and anti-sandboxing tricks. It also employs a new persistence method taking advantage of the Pending GPO feature. The malware spawns a suspended mstsc.exe (Remote Desktop Process) and injects itself into it. Before installing itself into the system, it performs several checks related to sandboxes and tools associated with malware analysis.
Anti-Sandbox, Anti-Analysis and More
Decrypt Strings at Runtime
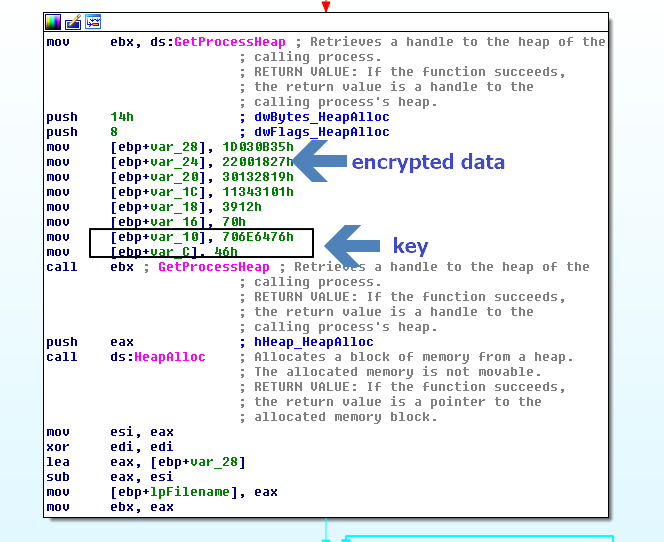
After the sample is unpacked, strings of the sample are not visible to the analyst. Strings are still encrypted during runtime, which means even after dumping the process from the memory, strings are still encrypted. The analyst would have to debug or have a comprehensive API log or manually decrypt the strings. This would prevent some tools such as “memory dumpers” from identifying interesting strings.
Aside from this, the decryption routine uses “dummy APIs,” which don’t do anything. This technique could affect the output of sandboxes with API logging tools either by performance or analysis of the API logs. Below is a sample of how it decrypts the runtime.
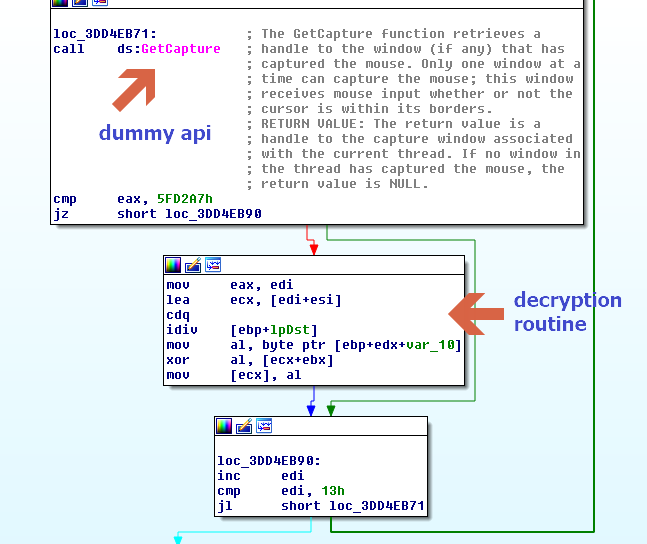
Below are the list of dummy APIs that this variant used, many of which are in the USER32.dll library.
- CreatePopupMenu
- ExitWindowsEx
- GetCapture
- ReleaseCapture
- GetClipboardOwner
- GetActiveWindow
- CountClipboardFormats
- GetProcessWindowStation
- GetMessagePos
- GetMessageTime
- GetDesktopWindow
GetClipboardViewer - GetInputState
- GetShellWindow
- CreateMenu
- GetCaretBlinkTime
- GetClipboardSequenceNumber
- DestroyCaret
- GetTickCount
- GetCurrentProcessId
- IsSystemResumeAutomatic
Process Hash Checking
To make it even harder for the analyst to figure out which processes it needs to check before installing, it uses CRC32 to hash the process name and compare it with the following hardcoded CRC32 hashes. If there is a match on any of the hashes, the malware will not install.
- 0x278CDF58
- 0x2D386ECE
- 0x0ABA416E3
- 0x0BFFDE1F0
- 0x6FADB57B
- 0x581419AC
- 0x0A93A5DA5
- 0x9FE09B81
- 0x62B621C4
- 0x0E2F42D3
- 0x1CB3F267
- 0x7DEED7DB
- 0x487C3558
- 0x0BC541011
- 0x70F400CF
- 0x7E11E4CF
- 0x52FEB192
- 0x1E24D477
- 0x4A6B6EBC
- 0x6DE558E4
- 0x6E4851F8
- 0x9F5462ED
- 0x896773D7
- 0x68B0F30D
- 0x7B8B2670
- 0x1E84D9C6
- 0x0F9B64044
- 0x11E91917
- 0x7EC953AB
- 0x0AFB3480
- 0x5D5421CF
- 0x4055C0A5
- 0x0B4C2ED2
- 0x6751A7A7
- 0x0F0FC4F7
- 0x0BF550EED
- 0x1B54824
- 0x72C7BD89
- 0x0B15AFA72
- 0x0D35C5E5C
- 0x86BD8B3A
- 0x334B7FA5
- 0x47E5605F
- 0x0E1E54873
- 0x0D8367B99
Anti-Sandbox
It checks if the data is in the registry key “HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor\0\ProcessorNameString” has word “Xeon”
It checks if the following sandbox or debugging dlls are loaded:
- dbghelp.dll
- Sbiedll.dll
It checks if the username is as follows:
- CurrentUser
- Sandbox
It checks if the computer name is:
- SANDBOX
- 7SILVIA
It checks if the registry entry “HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System” contains any of the following strings:
- “AMI“
- “BOCHS”
- QEMU
- SMCI
- “INTEL – 6040000”
- “FTNT-1”
- VBOX
- SONI
It checks if the registry key
“HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\VideoBiosVersion” has the word “VirtualBox” in the data.
It also checks if the data in the registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\SystemBiosVersion has any of the following values:
- “55274-640-2673064-23950” – associated with JoeBox
- “76487-644-3177037-23510” – associated with CWSandbox
- “76487-337-8429955-22614” – associated with CWSandbox
Environment Variables
One noticeable characteristic of Gootkit is its use of environment variables, which act as a mini-config for the malware. The malware sets the following environment variables with these corresponding values:
standalonemtm = true
vendor_id = exe_scheduler_1235
Mainprocessoverride = svchost.exe
RandomListenPortBase = 6000
Interestingly, if it is found that the environment variable “crackmeololo” is set, it will skip all of the anti-sandbox and anti-analysis checks.
New Persistence Method
This Gootkit loader uses a unique persistence method that we haven’t seen on any other malware in the past. It takes advantage of using Pending GPO (Group Policy Object) to start on the next reboot.
First, it drops a copy of itself as %APPDATA%\Microsoft\Internet Explorer\mounper.exe. It also creates a file %APPDATA%\Microsoft\Internet Explorer\mounper.inf, which contains the following:
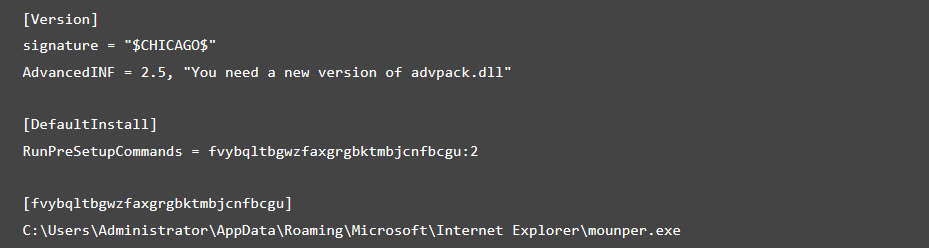
The .INF controls the execution of mounper.exe, similar to the autorun.inf seen on USB worms.
After dropping the necessary files, it creates the following registry. This, in effect, will trigger mounper.inf, which will execute mounper.exe on the next reboot.
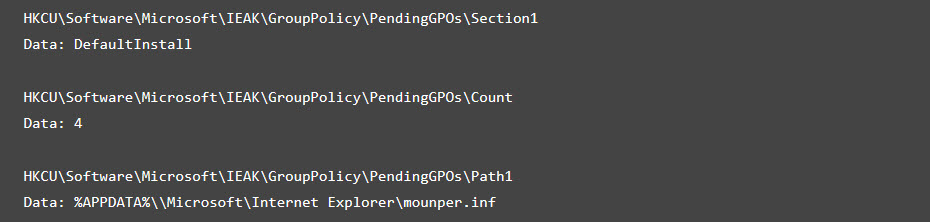
Final Payload
After it passes all of the anti-sandbox checks, it communicates to the hardcoded CnC servers below via TCP port 80.
- Zalipon.wollega.com
- Trussardi.qunamti.com
- Luga5lindalupina.com
Communication to its CnC server is encrypted. Below is a snippet of the communication between the malware and the server.
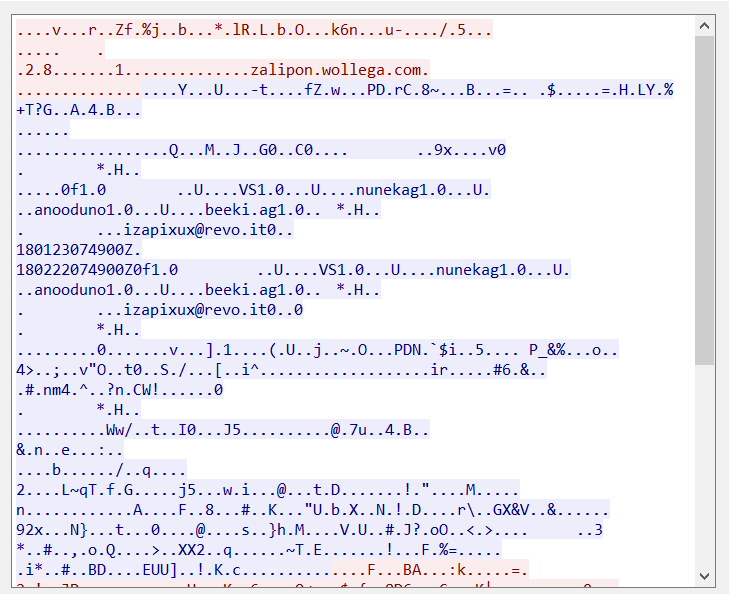
The final payload is downloaded from the same CnC server and directly injected into a spawned svchost.exe. It also did a little fileless trick as it saves the final payload as an encrypted binary blob in the registry. The Gootkit main module is a dll injected to svchost.exe. It is a pretty large malware with lots of features.
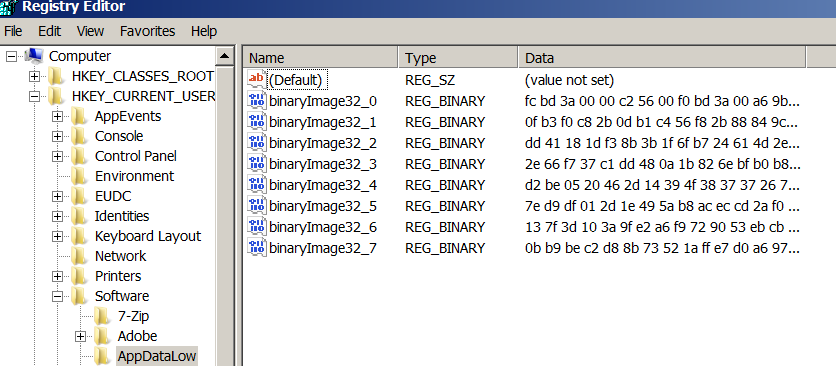
It sets up a proxy that listens on port 6000 and redirects HTTP (port 80) and HTTPS (port 433) on the infected system. This allows the malware to have a man-in-the-browser capability that can steal your usernames and/or passwords on websites that you visit.
Unlike the loader which is heavily obfuscated, the payload strings are visible. We can easily spot some of its modules, such as Spyware module, “src_iedriver\\SpywareJSWrappers.cc”. This module has the following functions, which are indication of its capabilities such as injecting to the browser, taking screenshots, keylogging, downloading and executing other files.
- DownloadFileRight
- SpIsPortIntercepted
- SpAddPortRedirection
- SpHookHttp
- SpUnhookHttp
- SpGetForegroundWindow
- SpInsertInjection
- SpInsertBlockedUrl
- SpResetConfigs
- SpHookRecv
- SpHookSend
- SpHookSockets
- SpAddFilterRule
- SpTakeScreenshot
- SpGetProcessList
- GCreateSharedString
- GGetSharedString
- GSetSharedString
- SpGetLocalNetworkNeighborhood
- SpGetLocalUsersAndGroups
- DbgGetLoadedModulesList
- DbgGetModuleDebugInformation
- SpHookKeyboard
- SpHookLsa
- SpSetFileWatermark
- SpGetFileWatermark
- SpGetVendor
- ExLoadVncDllSpecifyBuffers
- ModExecuteDll32
Below are some of the other modules/functions you can find inside this malware. Among these are spyware, VM detection, browser injection, stealing credentials from FTP and MAIL clients/programs.
- malware
- util
- line_reader
- spyware
- tunnel
- clienthttp
- keep_alive_agent
- windows
- FastBufferList
- utils
- gootkit_crypt
- inconvlite
- meta_fs
- vmx_detection
- client_proto_cmdterm
- client_proto_ping
- client_proto_fs
- client_proto_registration
- client_proto_socks
- client_proto_spyware
- generate_object_property
- generate_function
- protobuf_encodings
- protobuf_schema
- protobuf_compile
- protobuf_schema_parse
- protobuf_schema_stringify
- protobuf_schema_tokenize
- protocol_buffers
- tar_stream
- internalapi
- mail_spyware
- encoding
- chardet
- addressparser
- mimelib
- streams
- zeusmask
- mailparser
- mime
- sqlite3
- saved_creds
- pop3_client
- certgen
- config_processor
- luhn10
- FormatStackTrace
- hookit
- cookies
- dnscache
- http_injection_stream
- uploader
- sni_reader
- local_vars
- secure_device
- video_recorder
- imap_client
Indicators of Compromise
Sha256:
4b2cf725efb221506d89662bea5f428f1607f5e4142c8dad025dcc1bf6c33768
2740519b9fd4b962a118e5fca495fc2a587e513ca5c4d50628c769a9deee8f1d
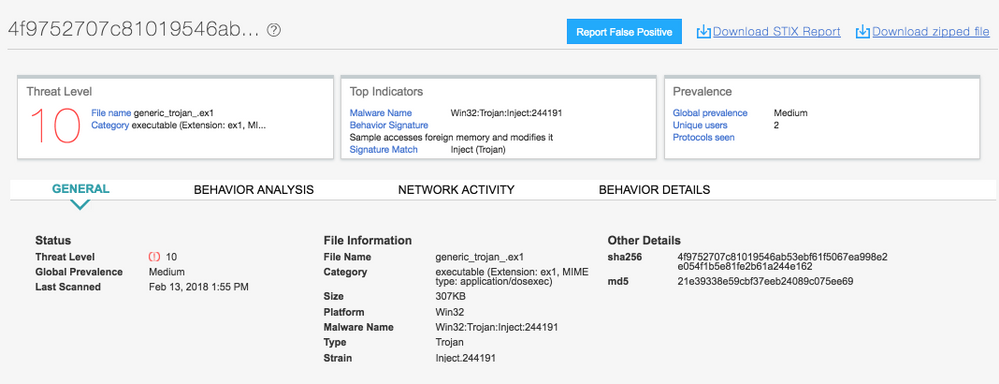
4f9752707c81019546ab53ebf61f5067ea998e2e054f1b5e81fe2b61a244e162
5f7bd3068e6ad4548da10266891224b3251a36f0d10fba2b0569a547b9f9a29a
CnC
Zalipon.wollega.com
Trussardi.qunamti.com
Luga5lindalupina.com
Download URLS:
https://carolinalakesgc[.]com/scripts/get.php
https://carolinalakesgc[.]com/setup.exe
https://modamixfashion[.]com/wp-includes/pomo/get.php
https://modamixfashion[.]com/wp-admin/flash/get.php
Juniper products detected this malware as follows:
JATP
SkyATP