What is your phone up to?
Your average enterprise security team requires access to all traffic in order to provide the secure environment that companies need to safely perform their work. In this environment, traffic information is collected and logged through various devices; a secure web gateway has a log of all the web requests that we make, while a next-generation firewall has app ID logs of all of the apps we use along with the domains and IPs that we connect to.
But end-users don’t typically get to see the information these security devices see. Most only notice security measures when their browser fails to open a website or download software from some questionable source. Without this visibility, it leaves people wanting to know, “what are the apps on my phone up to?”
Next week at RSA, we are putting this visibility back into the hands of everyone. Stop by the Juniper Networks booth (#3615) and find out what your mobile device is up to under the radar. Our team of threat researchers can show you in less than 30 seconds.
What is the demo all about?
Most of us download dozens of apps on our phones on a regular basis. Android device users might sometimes pause and ponder the screen showing all of the access permissions the new app is asking for, and from there decide to proceed or not. But, once installed, do we really know what websites the app is communicating with? Are we confident the app isn’t tracking our activity or stealing our data and sending it somewhere unauthorized? Is it normal that our ride-hailing apps are connecting to our social media sites?
Network security teams have access to these answers, but as end-users we are left in the dark. In this RSA demo, we will put that visibility in your hands by showing you on your own phone the sites (and IP addresses) that your device is connecting to and how reputable those sites are.
How is the demo performed?
We will have a WiFi hotspot set up at the Juniper Networks booth, similar to what you would find in a public place like a coffee shop. To participate, booth visitors can connect to this hotspot, allowing the Juniper Threat Labs team to collect and monitor the traffic coming out of your phone. The team will then display the list of sites your phone is connecting to, their geolocation and their reputation, all on your phone’s browser. Any known malicious site will be highlighted for full visibility.
Here is a sample screenshot from this demo:
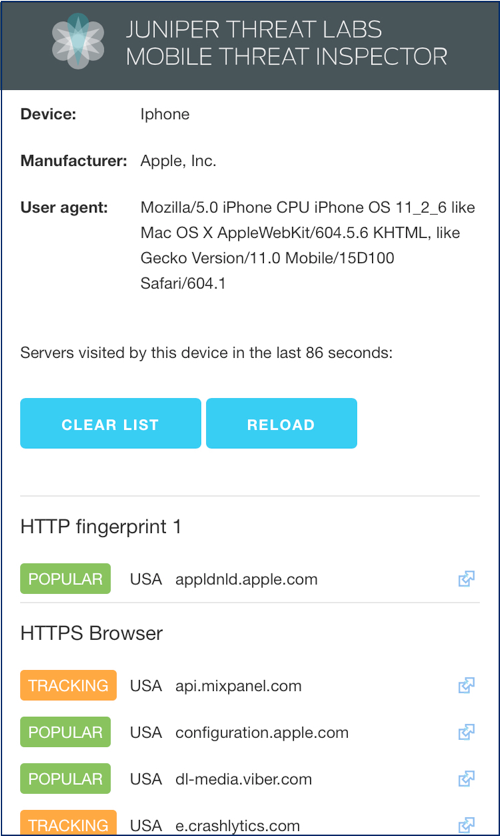
What should you try during this demo?
Most applications on our phones do not run in the background. They need to be in the foreground to perform anything, including network communication. So, here’s a fun thing to try. Remember that fancy fitness tracking app you downloaded? Open the app, then come back to your browser screen to see what sites it has connected to while running. If you see a site that you don’t recognize, you can use the Google search link we’ve included so you can do your own investigation into whether or not it’s legitimate.
Spoiler alert: we heard a lot of gasps when we rolled out the demo for our own employees in Juniper’s cafeteria. In just 30 seconds, we can put the knowledge of your data back into your own hands, so you will finally know what’s going on with your apps. Stop by the booth to see for yourself!