Threat name: BitPaymer Ransomware
IOC Hash: Sha256: 8943356b0288b9463e96d6d0f4f24db068ea47617299071e6124028a8160db9c
IOC Files:
- Files encrypted changed to extension .locked
- Files ending with Readme_txt are created containing the Ransom Notes
BitPaymer ransomware was first seen in mid 2017 and was known to infect hospitals and ask for a huge Ransom. Earlier versions of BitPaymer allegedly demanded a whopping amount of 20 to 50 bitcoins, which would approximately amount to a hundred thousand dollars. This means that the ransomware was targeting organizations rather than individuals . Recently, we came across a variant of this ransomware.
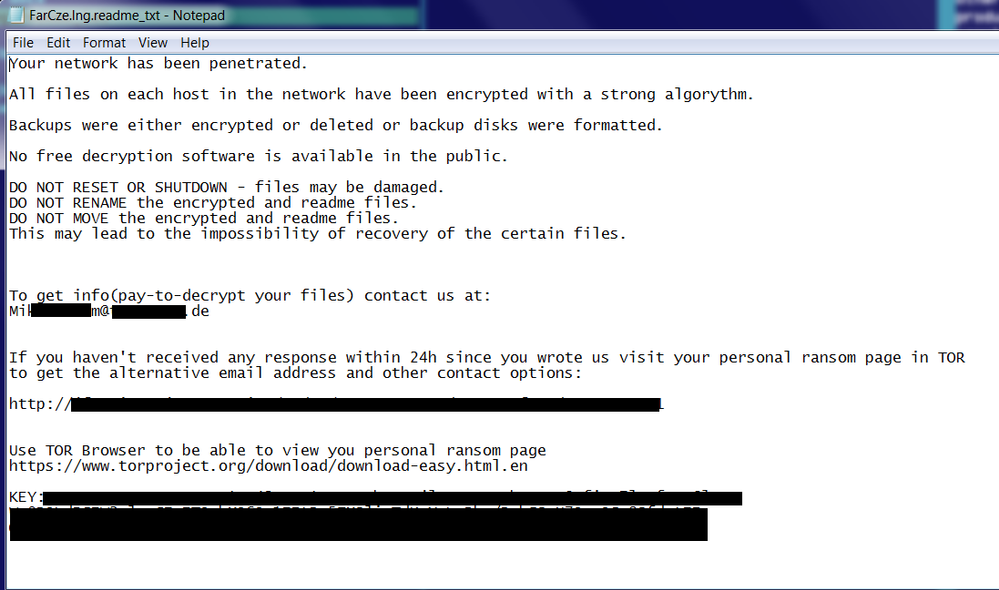
Fig: BitPaymer ransom note
BitPaymer uses a unique hiding mechanism that exploits alternate data streams (ADS), a feature of a NTFS file system that allows it to hide itself from plain sight.
Earlier versions of BitPaymer hid their own files by adding themselves to blank files as an ADS. The latest version copies a clean Windows system executable to application data folder and then adds a copy of itself as an ADS stream to that copy of clean executable file . This can evade security tools that are not able to look into ADS. The file name of the copy of the clean executable is usually 8 character with “~1” at the end ie .”SOWI3D~1”. In this version of BitPaymer, , the name of the ADS is “:bin”, while versions of the malware is “:exe” .So, the file name in this case is ”SOWI3D~1:bin”, where bin is the copy of the malware hidden as an ADS . You can only see “SOWI3D~1” as the file name when using Windows Explorer or file browsing tools like Far Manager.
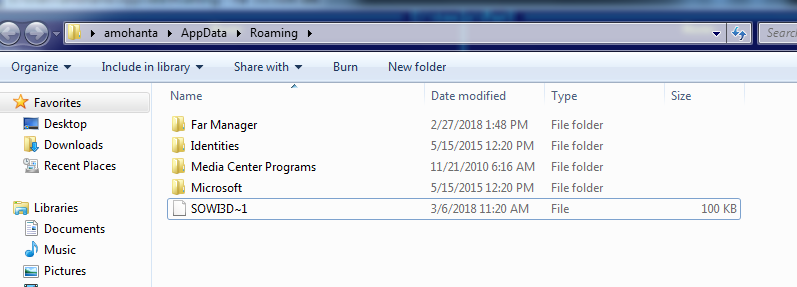
Fig: stream not visible in Windows Explorer
Tools like AlternateStreamView can be used to view the ADS.
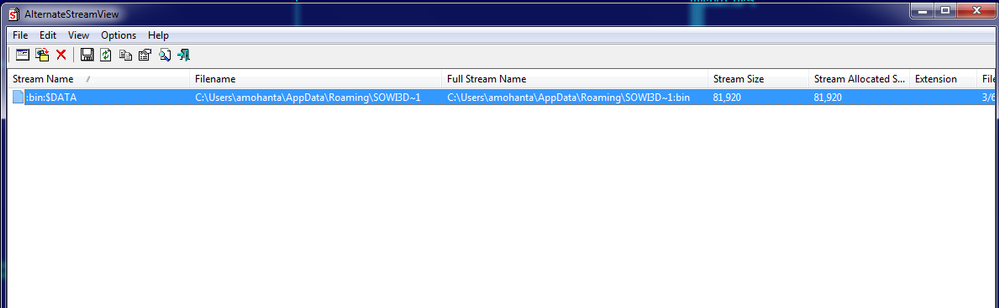
Fig: alternateStreamView tool
After adding itself as an ADS to the copy of the clean Windows system executable, the malware launches the copied executable.
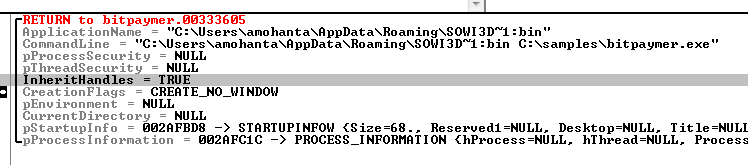
Fig: process created from ADS
The ransomware also tries to delete backup files like other ransomware. Most ransomware is known to use only VSSAdmin to delete the shadow copies but this one also seems to use “diskshadow.exe”.(note: shadow copies are used for the purpose of backup). The malware then executes the following commands to delete backups.
“C:\WINDOWS\system32\vssadmin.exe C:\WINDOWS\system32\vssadmin.exe Delete Shadows /All /Quiet”
“C:\WINDOWS\system32\diskshadow.exe C:\WINDOWS\system32\diskshadow.exe /s C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\yP34.tmp”.
The ransomware has also embedded a public key that is used for encryption purposes.
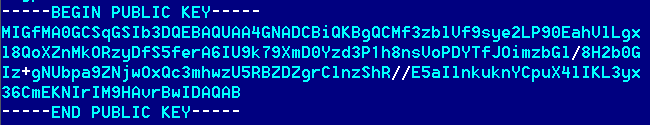
Fig: public key embedded in the ransomware
After encrypting the files, the malwares drops a ransom note file for the victim.
The ransom note is slightly different in this version of BitPaymer. This version demands the ransom to be paid within 24 hours, while the earlier gave a period of 72 hours.
The malware encrypts the files and leaves a ransom note in the directory. The encrypted files usually end with “.ini.locked” . The ransom note file name usually has the same file name with extension “ini.readme_txt”.
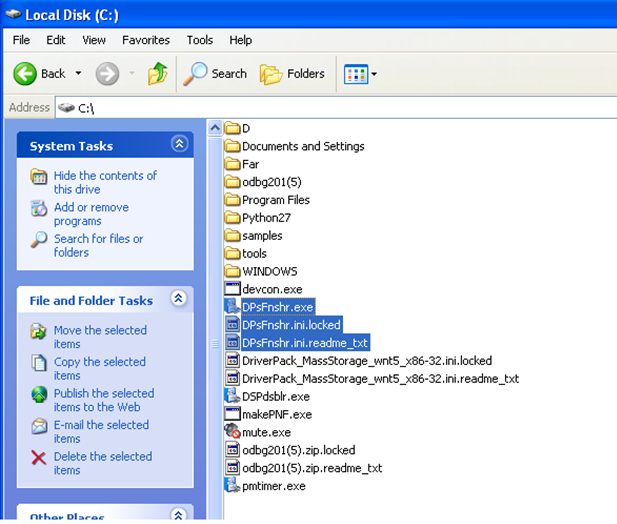
Fig: Files encrypted by BitPaymer
BitPaymer is meant to spread by Brute force Remote Desktop Protocols (RDP).
Detection
Both Juniper Sky ATP and JATP on-prem solutions detect this threat as seen in the screenshots below .
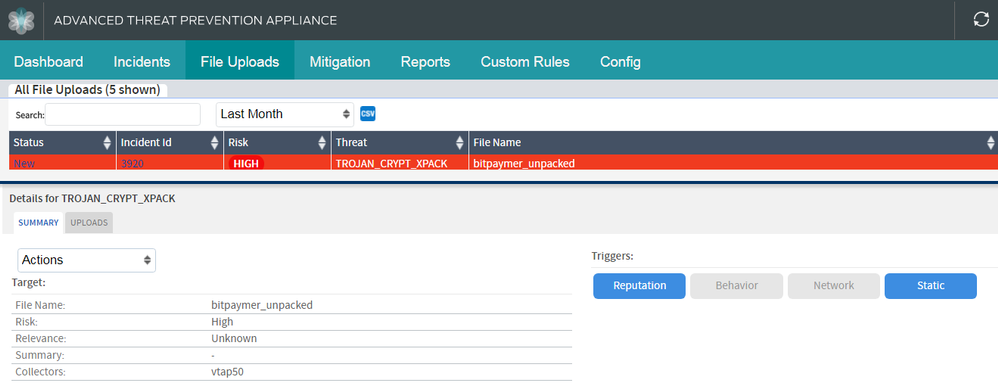
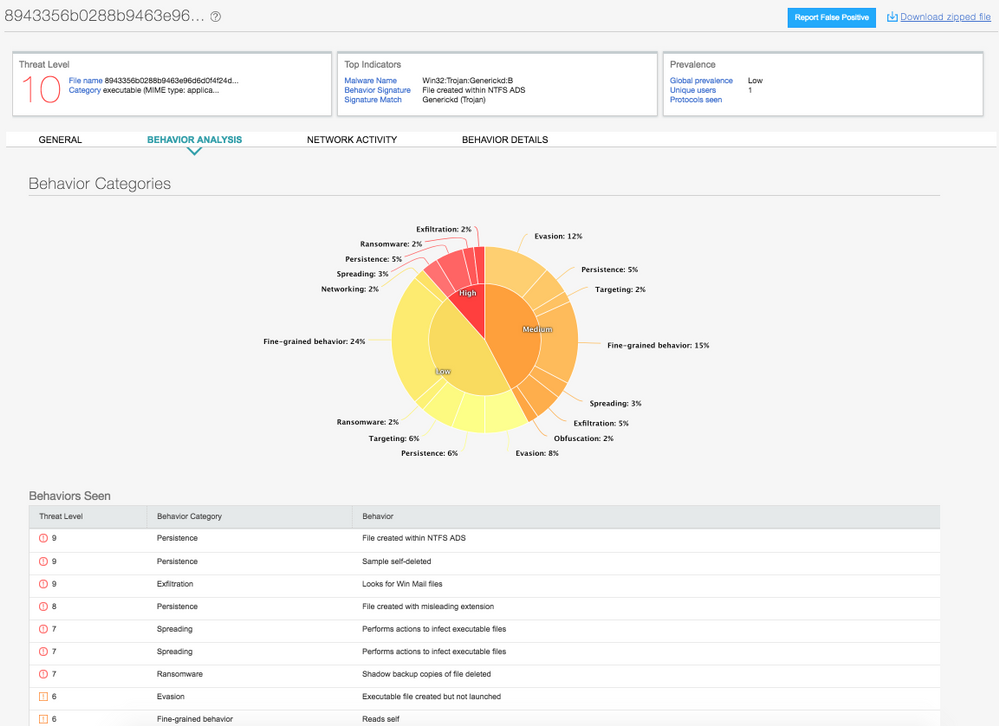
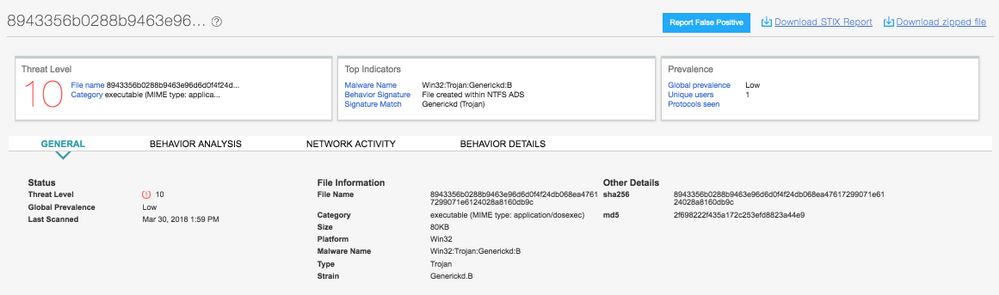
Fig: Juniper Sky ATP and JATP Detection
Customers using Juniper Sky ATP and JATP solutions are protected from the threat.

























