In our previous blog, we briefly discussed the five 5G security challenges that service providers need to tackle. In this blog, we’ll look deeper into the first challenge – what does the coexistence of 4G and 5G mean from a security standpoint?
4G and 5G will coexist for a long time.
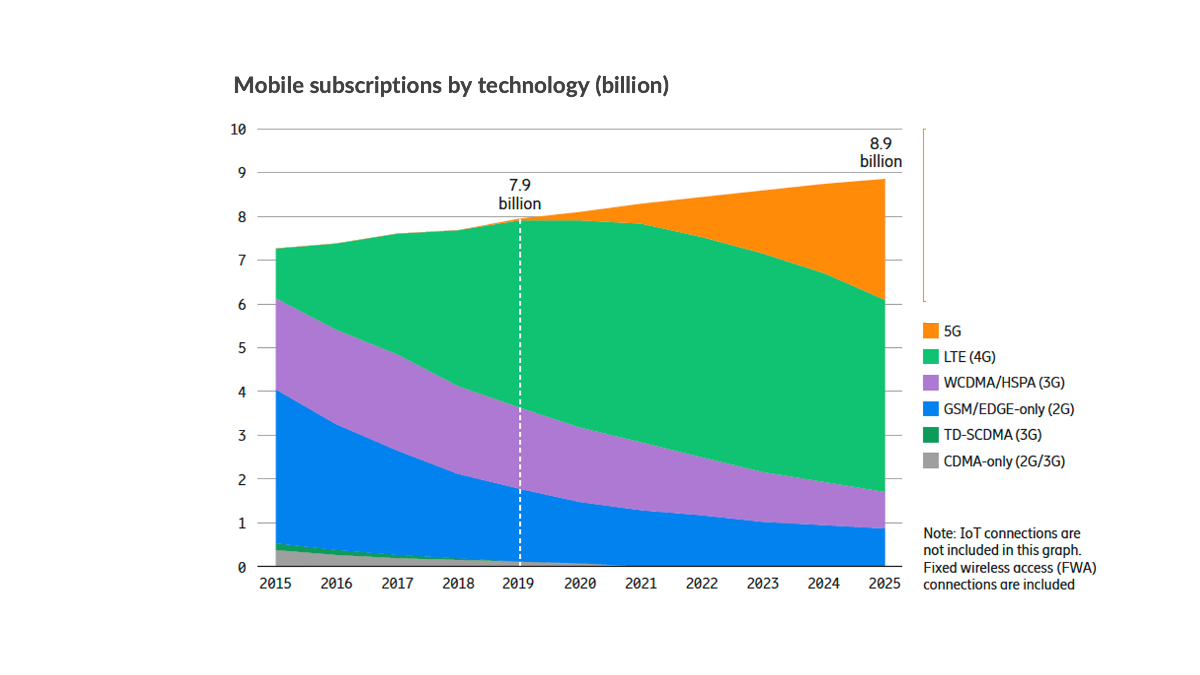
Like 4G, 5G is not going to happen at the flip of a switch. Instead, 5G will evolve side by side with 4G, with logical evolution phases taking place over the next decade. In other words, 4G and 5G will coexist for a long time. As a proof point, GSMA forecasts that 4G will still account for 59% of global connections by 2025.[1] Ericsson[2] also predicts that LTE (4G) will still account for the largest number of mobile subscriptions from now throughout 2025 while 5G subscriptions rapidly pick up.
Existing 4G security infrastructure needs performance upgrades to address 5G NSA requirements.
5G is targeting superior performance, including 1 millisecond latency and 10 Gigabit per second (Gbps) peak data rates, both of which represent an order of magnitude growth from 4G networks. Most 5G deployments will start with the 5G non-standalone (NSA) architecture, which pairs the 5G RAN with the existing 4G core for faster launch of 5G services.
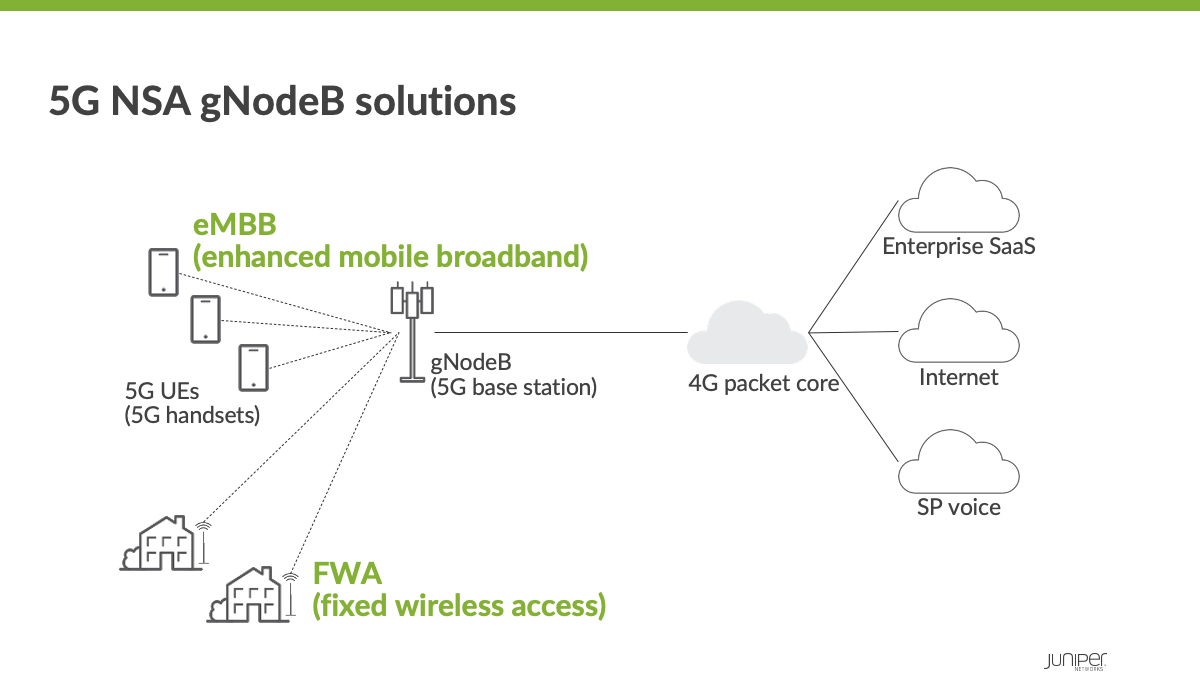
In the transition from 4G LTE to 5G NSA, there will be an increase in network traffic driven by the introduction of new 5G radio base stations (gNodeBs). These gNodeBs will support up to 25Gbps bandwidth, which is a significant increase compared to the 1-2 Gbps from the typical 4G radio base stations (eNodeBs) that exist today.
The increase in network traffic from 4G eNodeBs to 5G gNodeBs while sharing the same 4G core network will require upgrades to most of today’s 4G security infrastructure to prevent bottlenecks in performance which could impact users’ overall 5G experience.
Specifically, for the following use cases:
- SGi/N6 Firewall and CGNAT: The first security performance upgrade requirement would be for the throughput at the SGi interface of the 4G core network. Juniper Networks estimates that 500Gbps+ CGNAT and stateful firewall on the SGi/N6 interface will be required with the introduction of 5G radios in 5G NSA simply due to the increased throughput possible in total from the higher bandwidth rates enabled by the 5G NSA gNodeBs. Depending on the customers’ implementation preference, the Juniper Networks MX Series routers with MX-SPC3 Security Services cards and SRX5000 Series Services Gateways are both top choices.
- DDoS Protection: The increase in SGi/N6 interface bandwidth and scale leads to the potential for much larger scale volumetric DDoS attacks, which could be originating from within the SP network or from the outside networks that are specifically targeted against the SP’s network. With the rising number of DDoS attacks combined with the increased bandwidth of 5G, it means that the traditional “detect and redirect” DDoS mitigation approach will be inadequate because of capacity overload. The need for a highly secure and cost-efficient volumetric DDoS protection solution such as the one developed by Juniper and Corero will certainly increase as 5G NSA is rolled out around the world.
- Threat Intelligence: With a larger threat surface on the SGi/N6 interface, we will see an increase in the volume of potential malware entering the network and an increased interest in weaponizing malware from within the network. Therefore, having access to an always up-to-date threat feed (malicious IPs, Command and Control (C&C), infected hosts, etc.) and leveraging them automatically for policy enforcement will be essential. Juniper SecIntel allows you to do just that. Juniper SecIntel provides threat intelligence to all points of connection across the network to block malicious traffic, creating a threat-aware network.
- Security Gateway (SecGW/SEG): Another security performance upgrade requirement would be for the IPsec tunnel bandwidth required to secure the mobile backhaul, from the gNodeB back to the 4G core network. This bandwidth will typically exceed what most 4G/LTE security gateways (SecGW/SEG) can support for single tunnel bandwidth, thus requiring support up to 25Gbps throughput for combined encryption and decryption on a single IPsec tunnel, connecting the gNodeB to the security gateway and terminating that IPsec tunnel in front of the 4G core network. The Juniper Networks SRX5000 series services gateways and the vSRX Virtual Firewall are top choices for the world’s most demanding service providers given the advantage of high-performance security and physical-virtual feature parity. Additionally, our partnership with Ericsson allows us to offer intelligent mobile transport with comprehensive security that guarantees superior 5G performance.
Bottom Line
Service providers’ 5G security strategies must first assess existing 4G network security to ensure implementation consistency among both 4G and 5G. The logical starting point to commence this assessment is determining if their 4G network security performance is ready for the increase in network capacity from 5G NSA.
Without investment in upgrades, security will become a bottleneck to overall network performance. On a product level, security performance such as throughput, connection scale and session establishment rate should be evaluated for current mobile security use cases such as Security Gateway (SEG), SGi/N6 firewall, CGNAT, DDoS protection and threat intelligence. In our next blog, we’ll discuss how distributed edge clouds open up new attack surfaces and what you can do to secure them.
[1] GSM Association, The Mobile Economy 2019
[2] Ericsson, Ericsson Mobility Report 2020