5G promises to bring tremendous new revenue opportunities for service providers. However, the increase in performance, changes in network architecture and new technology adoption that come with it also present major security implications. What are the top security challenges that service providers need to tackle to make 5G services a successful business and mitigate the associated risks?
In this blog, we will discuss the five 5G security challenges. The next five blogs in this 6-part series will focus on each of these challenges and offer tips and strategies to help service providers tackle them effectively.
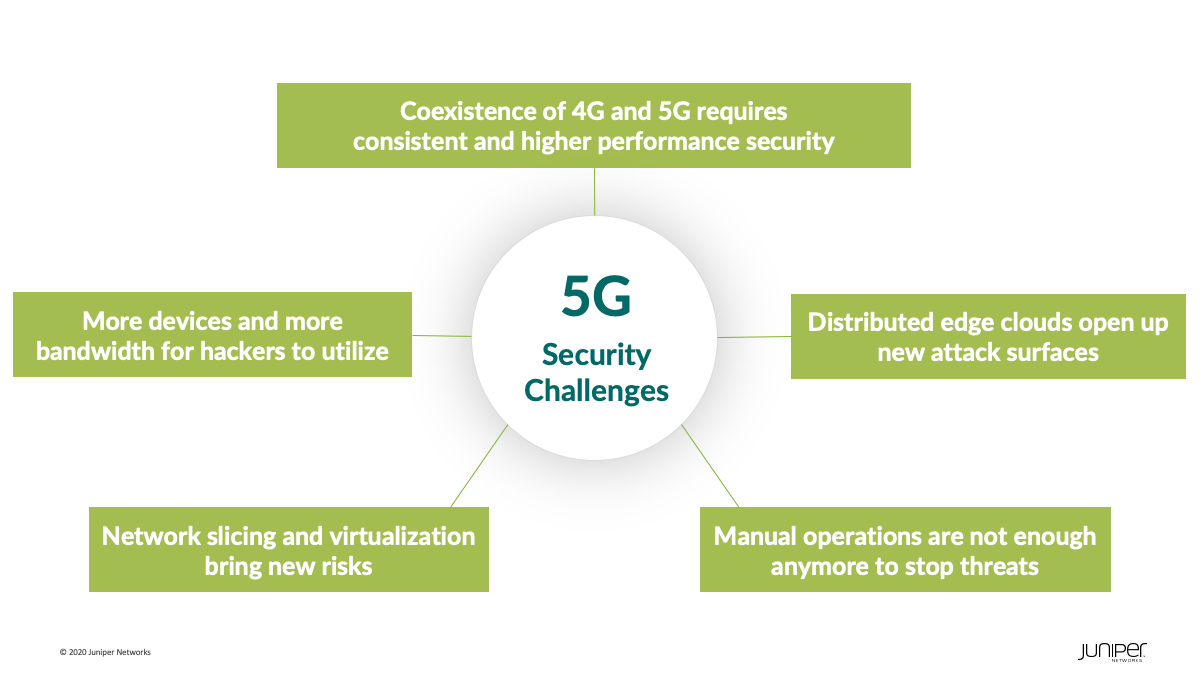 Coexistence of 4G and 5G requires consistent and higher performance security.
Coexistence of 4G and 5G requires consistent and higher performance security.
Like 4G, 5G is not going to happen at the flip of a switch. Instead, 5G will evolve side by side with 4G, with logical evolution phases taking place over the next decade. In other words, 4G and 5G will coexist for a long time. In the transition from 4G LTE to 5G NSA (Non-Stand Alone), there will be an increase in bandwidth driven by the introduction of new 5G radio base stations, or gNodeBs. The increase in bandwidth from 4G eNodeB to 5G gNodeB will cause significant increases in performance and scale requirements that the current security infrastructure may not be able to handle. This also means that as 4G and 5G networks coexist, the security policy for threat detection and mitigation must be consistent and holistic.
More devices and more bandwidth for hackers to utilize.
5G will result in a 10 to 100 times increase of connected devices as well as faster speeds and higher bandwidth. While this is great news for consumers and businesses, hackers will also take advantage of these new capabilities. Many IoT devices are fundamentally insecure and will rapidly become preferred targets for hackers to leverage in cyberattacks. And with more available bandwidth to utilize, hackers can generate more powerful DDoS attacks that can overwhelm any organizations’ network and services.
Distributed edge clouds open up new attack surfaces.
Distributed edge cloud is an architecture evolution of cloud computing that enables application hosting and data processing to move from centralized data centers to the network edge, closer to where data is generated. In this new architecture, IP connectivity will terminate at the edge of the operator if proper security mechanisms such as encryption and firewalls are not in place. As a result, the edge cloud nodes are susceptible to spoofing, eavesdropping and other attacks from the public Internet. It’s also likely that some 3rd party applications will run on the same physical platforms together with the virtual network functions (VNFs), increasing the risk of exhausting the application resources needed by the network functions or worse – offering hackers an attack vector to infiltrate the platform.
Network slicing and virtualization bring new risks.
Network slicing is a specific form of virtualization that allows multiple logical networks to run on top of shared physical network infrastructure. With network slicing, mobile service providers can partition their network resources to address a diverse set of use cases. Service providers need to consider how well the virtualization layers and network slices are isolated from each other. If someone can attack the “lower security slice”, can they then also impact the “higher security slice”? If one tenant or one slice is compromised by malware, will other tenants or slices get infected as well?
Manual operations are not enough anymore to stop threats.
5G infrastructure heterogeneity and complexity will require security to be applied at multiple levels (e.g., associated with a slice, a service or a resource) across multiple domains, with a combination of centralized and distributed, physical and virtual deployments. For previous generations, manual interventions for mitigating threats may be fine. But with 5G now and the fact that the threat landscape continues to grow in volume, velocity and sophistication, manual operations are not enough. Security absolutely must be automated – automated threat detection and mitigation, with holistic visibility.
Bottom Line
5G promises to be a game changer and security is fundamental to the successful delivery of services in the ‘Cloud + 5G + AI’ era. Service providers must carefully plan their security strategies as an integral part of the 5G evolution roadmap. The five security challenges outlined here offer a good starting point to evaluate.