In our previous blog, we briefly discussed the five 5G security challenges that service providers need to tackle. In this blog, we’ll look deeper into how the distributed edge cloud increases attack surfaces and what you can do about it.
A key enabling technology for latency-sensitive & bandwidth-intensive 5G applications
Edge cloud is an evolution of cloud computing, which enables application hosting and data processing to move from centralized data centers to the network edge. Cloud capabilities are distributed across the network, which is particularly helpful for applications that need low-latency and/or high-bandwidth.
ETSI has defined a set of technical standards for Multi-Access Edge Computing (MEC) with the objective of enabling an open ecosystem for service providers and third parties to flexibly and rapidly deploy applications with real-time access to radio network information for optimization. It is generally agreed that MEC is one of the key enabling technologies for 5G, particularly for its ability to flexibly offload traffic through the user plane function (UPF) and open environment for enabling diverse vertical apps and services.
From our analysis, there are three major attack surfaces related to MEC and edge cloud that service providers should consider having security measures to protect from:
- Insecure mobile backhaul
- Attacks from the public Internet
- Shared infrastructure with third party applications
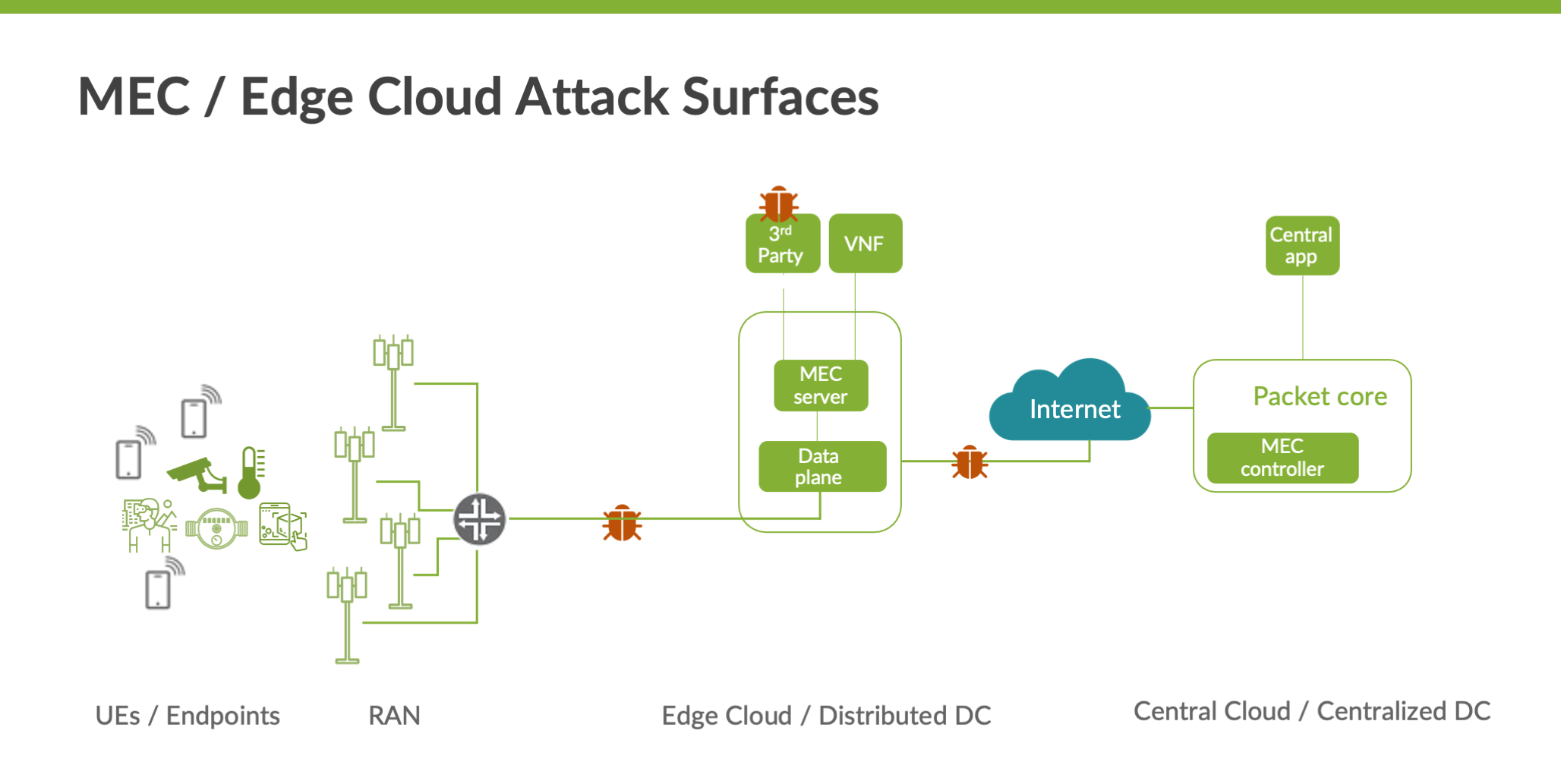
Data transiting via insecure mobile backhaul are susceptible to eavesdropping and interception
With 5G adoption, more radio base stations will need to be deployed to increase network capacity. Many of these new radio base stations will be deployed in locations that are insecure and/or use shared backhaul. Data traversing these insecure backhauls to edge cloud nodes are vulnerable to MIM (Man in the Middle) attacks, eavesdropping and interception.
To address these security challenges for the mobile transport network, the 3GPP standards body has introduced the concept of a security gateway via the 3GPP 33.210 and 3GPP 33.310 specifications. The security gateway (SecGW) provides mutual authentications between base stations and core networks for access control. Additionally, its IPsec functionality provides confidentiality and integrity protection. The Juniper vSRX can be used as the virtual security gateway and deployed as a VNF on any of the edge cloud nodes, protecting .
Susceptible to attacks from the public internet
With this new architecture, IP connectivity can be terminated at the edge cloud location, which means these nodes are susceptible to spoofing, eavesdropping and other attacks from the public Internet at the SGi/N6 interfaces.
Conventional and well-known security measures used in protecting EPC are applicable here, such as CGNAT, stateful firewall and DDoS protection. The main difference lies within the terms of the performance requirements and form factor since the MEC edge clouds are essentially distributed core networks, each of which has much smaller traffic profile compared to the centralized core. In addition, the facilities hosting the MEC edge cloud are usually significantly smaller than the typical data centers, which means space is limited. Thus, adding large-sized physical appliances may not be an option.
In this case, solutions like the use of virtualized firewalls with the Juniper vSRX would be a good fit. Another alternative could be leveraging the MX series routers at these network edge locations since many facilities might already be using them them for the routing functions. By simply adding the MX-SPC3 services card into the MX chassis, service providers can now instantly have an integrated routing and security platform at these edge cloud nodes, plus power and space efficiency.
Sharing infrastructure with third party applications increases risks.
MEC provides a new ecosystem and value chain. Operators can open their Radio Access Network (RAN) edge to authorized third parties, allowing them to flexibly and rapidly deploy applications and services to mobile subscribers, enterprises and vertical segments.
A likely deployment model runs third party MEC applications on the same physical platforms as some VNFs. These applications are not controlled by the mobile service provider, which raises the concern that these applications may exhaust resources needed by the network functions. There are also risks that some poorly designed applications could offer hackers an attack vector to infiltrate the distributed data center and affect the network functions running on the platform.
One way to mitigate such risks is to implement microsegmentation within the MEC edge cloud. Microsegmentation ensures isolation between different applications and services, thus mitigating the “noisy neighbor” problem. And it also establishes the boundary to contain malware should they arise from certain apps without impacting the rest of the tenants or VNFs.
Bottom Line
As 5G becomes more readily available, the adoption of MEC and edge cloud will be accelerated. In this blog, we’ve discussed several security aspects for the MEC and edge cloud. Before rolling out large-scale deployments, service providers should do a thorough analysis to ensure security is integrated with the infrastructure from day one.