This blog was originally published to the 128 Technology website – in 2020, Juniper Networks acquired 128 Technology. Learn more about the acquisition here.

SD-WAN is may be the hottest topic in networking right now. You’ve probably heard that SD-WAN optimizes networks, simplifies operations, and reduces expenditures leading to a more powerful, cost-effective network. You may also hear buzz about potential security concerns with deploying software-defined networks. In order to effectively mitigate any new risks that may be posed, enterprises must come to understand “two truths” about SD-WAN security.
- If a network doesn’t know what’s right, it can never know what’s wrong.
- If network activity can happen without any record of it, then malicious behaviors will be among the network activity
Tom Nolle, President of CIMI Corporation and member of 128 Technology’s technical advisory board, along with Prashant Kumar, Co-founder and Vice President of Product Management at 128 Technology, recently engaged in an in-depth discussion (click here to watch the full webinar) to shed light on the two truths, as well as share some best practices for implementing SD-WAN. We’ve put together a summary of their webinar to give you the highlights until you can listen to it in its entirety.
“We believe in these truths, and we believe our implementation of SD-WAN sets us apart in terms of security. It is these truths that you should be thinking about if you are planning to implement SD-WAN.”
– Prashant Kumar, Co-Founder and VP of Product Management, 128 Technology
THE FIRST TRUTH
If a network doesn’t know what’s right, it can never know what’s wrong.
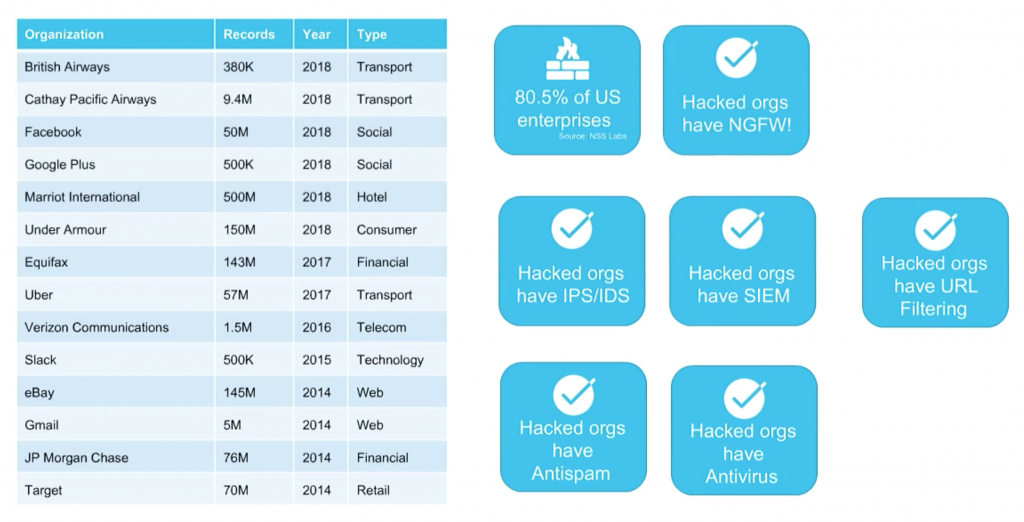
If you look at any of the most recent high-profile hacks outlined in the figure below, you will see they were large-scale attacks with millions of users compromised. In each case, several preventative measures were in place including firewalls, next generation firewalls (NGFW), anti-SPAM and SEIM solutions.
So, the question is: why are these attacks happening if networks are secured? The answer? Because you can’t understand what you don’t see. Unless you know precisely what services and applications are running on your network, it’s almost impossible to differentiate legitimate traffic from malicious requests.
Recent Hacks:
To best protect your network, you’ll not only need to know who the specific users are that have permission to access to it, but it’s critical to understand the correct destinations for traffic requests. That way you can ensure that the right resources are being accessed by the right users. Additionally, an intelligent session-based router can differentiate whether traffic is encrypted or not by leveraging adaptive encryption. It only encrypts the traffic in question so you won’t have to spend valuable time or budget on unnecessary encryption, while still being confident that your data is secure.
The question often arises if the first truth only applies to North-South traffic, which comprises requests that travel from the LAN to the WAN. The answer is No. East-West traffic refers to that which comes from within your network; for example, accessing data within an internal database. Since 60% -80% of attacks originate from inside the network, it is essential to monitor both North-South and East-West traffic as part of your overall SD-WAN security strategy.
THE SECOND TRUTH
If network activity can happen without any record of it, then malicious behaviors will be among the network activity.
Now that we know why it’s critical to take proactive measures to successfully distinguish between good and bad traffic, let’s explore why it’s just as important to have a record of everything so you can recognize threats before they attack. Intelligent journaling, or recording the behavior of your network traffic, is the key to supporting the two truths. If you define the rules for traffic flow, you’ll know precisely what is allowed and what isn’t allowed on your network. Journaling is the mechanism to seeing what’s happening behind the scenes.
A typical security breach usually involves many repetitive attacks, so it’s rare that a cyber criminal haphazardly gains entrance to a secure network. By documenting network activity through intelligent journaling efforts, you can easily identify repeated attempts to execute something nefarious on the network. With that information, you can determine if a malicious user is responsible, or if an insider unknowingly downloaded malware. Then you can respond accordingly. However, not all IT managers keep detailed logs of network traffic.
Years ago, the common thinking was that if you treated IP connectivity simply as random, individual packets floating around, it was nearly impossible to manage. Our philosophy is that applications are best understood in terms of sessions, or a persistent relationship between two entities in a network, usually between a user and an application. If you focus journaling efforts on session attempts instead of individual packets, you can quickly reduce the overhead needed to record every single packet behavior. And when you pair journaling with a session-aware capability, you’ll know exactly what is happening on the network at any time.
One best practice that complements journaling, is to segment, or divide the network into zones based on the services and applications. Security zones help to reduce the attack surface by limiting the lateral movement of traffic across the network. Segmenting networks in such a way ensures that if there is an attack in one segment, it’s contained and doesn’t spread to other areas of the network.
Real-world Example
One of Tom Nolle’s enterprise clients performed a comprehensive security audit of its network, focusing on available access to the entire suite of applications. Of the permitted access to applications:
-
- Only 3% were accessed by appropriate users
- About 9% were only occasionally used for business
The remainder of the permitted applications (88%) were unknown and should not have been on the network in the first place.
CONCLUSION
A software-defined solution may be your next step toward greater efficiency and agility. However, to conduct business securely, especially in highly regulated industries like healthcare and financial services, the practice of permissive activity is not enough in today’s environment. A more proactive, session-based approach to security – that supports the two truths – is the best way to keep a watchful eye on everything that happens on the network.
Making the right SD-WAN security choice depends on your business objectives. But one thing is certain. You’ll need innovative capabilities that will meet your security needs both today and tomorrow. Our SD-WAN solution is based on the 128T Session Smart™ Router that’s helping to close the gap between what your customers need and what your network can deliver, so you can continue to move at the speed of business.
To learn more about the value-added benefits of the 128T Session Smart Router and how it supports the tenants of the two truths, please visit 128technology.com/product-overview.
To listen to the full webinar, “The Truth About SD-WAN Security,” see here.
























