Email is an essential service for companies and individuals. Billions of emails are exchanged daily, and within a portion of those emails lurk malware aimed at compromising your organization’s network security, stealing your company’s sensitive data and creating operational disruption. This blog dives into the dark side of email traffic, uncovering some of the latest malware threats, tactics and trends that can potentially undermine your systems.
We at Juniper Threat Labs will walk you through the threat detection process. Then we will present the overall statistics from a random sampling of one million files seen in email traffic that passed through Juniper systems throughout 2022 and provide specific examples of malware threats. We will close by highlighting features in the Juniper SRX device configuration that customers can use to protect their networks.
Why Focus on Files in Email Traffic?
First off, Juniper Threat Labs observes file samples from a myriad of types of network traffic. In this blog post, we will focus only on files observed in email traffic. After all, email is widely used as a primary communication method in enterprises and it has long been one of the primary threat vectors by which organizations are attacked and compromised.
Attackers can get creative with the type of attacks using email. For example, phishing is one of the most popular attack vectors. Attackers use deceptive attachments or links in phishing emails that are designed to trick recipients and compromise their systems. When successful, some phishing attacks go to the extent of installing spy software, like keyloggers, to steal credentials to one or more sensitive systems on the network. To highlight some attacks targeting our customers, we will present a specific case of a malicious file found in email that the Juniper Advanced Threat Prevention (ATP) platform detected and stopped.
For background, Juniper Advanced Threat Prevention (ATP) is a security solution that combines machine learning, behavioral analysis and threat intelligence to detect and prevent advanced malicious threats across all threat vectors – including email. When integrated with Juniper SRX series firewall devices, Juniper ATP helps stop malicious files seen on the network before they get into your network by performing file analysis, behavior analysis, threat intelligence correlation and blocking. By working in conjunction with the Juniper SRX firewall, Juniper ATP provides a more comprehensive and practical approach to threat prevention and detection as it uses a layered approach. For example, machine learning algorithms help detect unknown threats, while threat intelligence helps identify potential matches from widespread threats.
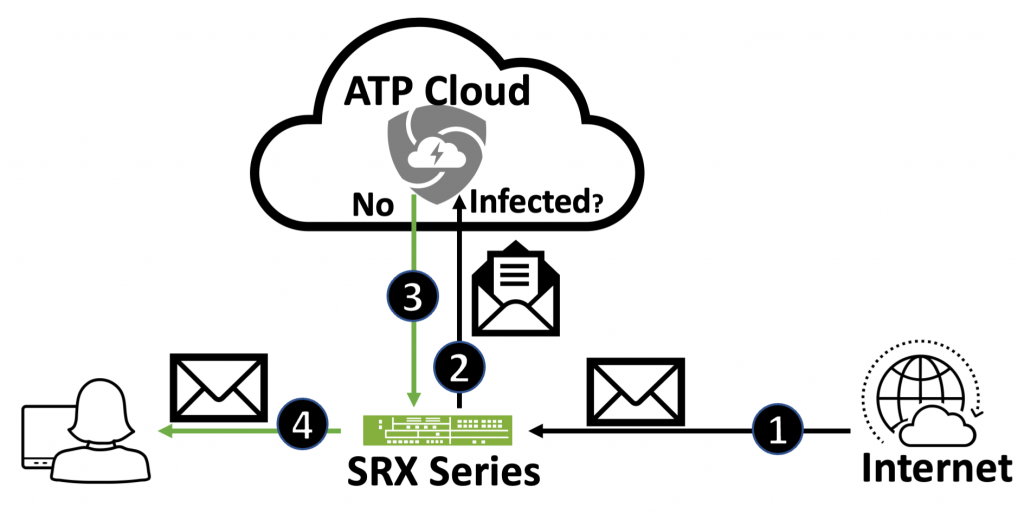 Figure 1: An overview of the SRX and ATP platform file scanning process.
Figure 1: An overview of the SRX and ATP platform file scanning process.
Figure 1 presents an overview of how Juniper ATP observes files in network traffic and analyzes them inline in real time. As emails travel through the Internet and onto customer’s network (step 1), the SRX device observes the email traffic and inspects all attachments. The Juniper SRX device sends all interesting files attached to emails to the Juniper ATP in the cloud for analysis (step 2). The Juniper ATP platform provides the Juniper SRX series device with a detection response (step 3) to block, quarantine or deliver the email with a warning header (step 4).
Though detection and prevention are very challenging, the combined protection afforded by Juniper ATP and the Juniper SRX devices are able to meet this challenge as they work together to analyze, detect, and block inline malicious threats. In order to balance performance, volume, and priority of traffic – all of which conspire to constrain analysis and response, Juniper ATP applies a tiered approach. The response is quick if the Juniper ATP platform has prior knowledge of a malicious file, otherwise the file is passed through sandbox analysis for those never-seen-before advanced malicious threats.
Analyzed Data Set
We randomly sampled one million files observed in email traffic from January 2022 to December 2022. The following statistics are based on these one million samples and do not include all scanned files. Most of the files in the random sample set were documents. PDFs make up 82.66%, and Office Documents make up 16%. However, other file types include compressed files (zip) and executables. We grouped various other file types into one category that we called “Others”. These files make up less than 0.23% of files in the random sample set. These files include text, HTML, JavaScript and encrypted files. We summarize the composition in Table 1.
Table 1: Statistics of files observed by types in email traffic.
| File Type | Percent Share |
| 82.66% | |
| Office Documents | 16.00% |
| Compressed Archives | 1.07% |
| Executables | 0.04% |
| Others | 0.23% |
Of the one million files, 14.61% were flagged suspicious and required further analysis. The Juniper ATP platform identified 3.87% of the files as malicious and signaled the Juniper SRX devices to block them. Of the nearly 4% that were malicious, almost 86% of the files were confirmed malicious using Juniper’s sandbox technology that is part of Juniper ATP. The machine learning module detected 8.26% of the malicious files missed by traditional detection techniques such as heuristics, AV signatures and blocklists. Interestingly, most of the malicious files were never seen before attacks and only 0.01% were known attacks. This analysis shows that Juniper ATP provides protection against zeroday threats and protects customers from novel attacks.
Table 2: Statistics of malicious files observed in email traffic by file type.
| File Type | Percent Known Bad |
| 5.10% | |
| Office Documents | 0.84% |
| Compressed Archives | 5.17% |
| Executables | 77.84% |
| Others | 2.97% |
Not surprisingly, the most likely malicious file types found in emails are executables like Windows and Linux binaries. Table 2 summarizes the percentage of confirmed malicious files by type. On the other hand, office documents had the least percentage of malicious files. Nevertheless, attackers still utilize office documents and PDF files to infect users. For example, in Office Documents detected as malicious, attackers mostly use Microsoft Excel files to embed malicious macros that trick users into running them. Juniper Threat Labs observed 55% of the macros were first-stage downloaders that fetched malicious code with the aim of infecting the user. We also found 43% of the infected documents utilize exploits that target older versions of Microsoft Office (e.g., 2016 & 2013) including vulnerabilities described in CVE-2017-11882 and CVE-2018-0798.
Attackers craft luring documents and embed an exploit in them to infect the user when he/she opens the document. Attackers will modify their malicious files to evade traditional techniques like reputation lists and static signatures. Supporting this point, only 16.2% of malicious files in email traffic were observed by two or more customers. Most repurposed attacks destined for multiple customers were executable files (82.6%), followed by PDF files (8.7%). This indicates that it is less probable that an attacker will repurpose the same attack when using document-based files like PDFs and Microsoft Office documents.
Example of Email Threats Identified: Remcos Remote Access Trojan
The impact of an attack depends on the type of malware that ends up on the user’s device. We observed different malware payloads, including remote access tools like Remcos and stealers like AgentTesla.
To understand the potential impact of these attacks on customers, the following is a case study from a recent attempted attack in email traffic from 2022 that was thwarted by Juniper ATP. Remcos is a remote access tool (RAT) that can be freely downloaded and used to manage computers in remote locations. However, attackers repurpose Remcos to infect users and get access to their networks.
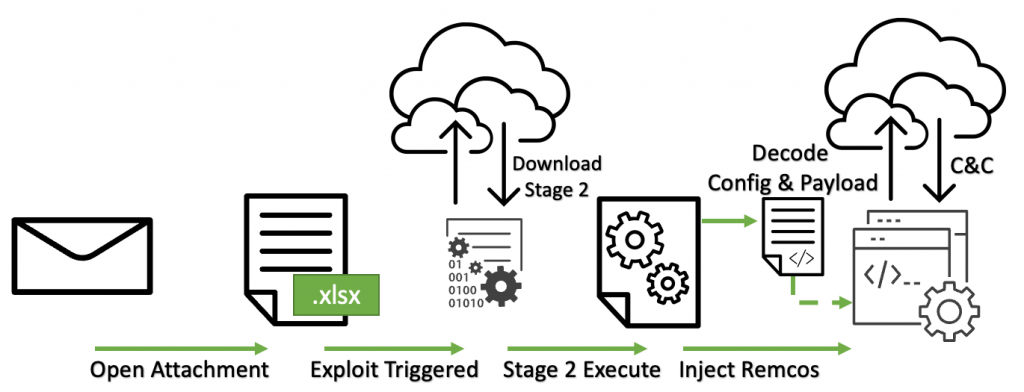 Figure 2: Infection stages for Remcos
Figure 2: Infection stages for Remcos
Attached to the email was a Microsoft Excel document with an embedded exploit for CVE-2017-11882. Figure 2 summarizes the infection stages of the Remcos attachment. Users opening this document will trigger the exploit, which will reach out to a remote server and download an instance of Remcos to infect the user’s system. Once infected, the attacker will have complete control over the victim’s computer and can monitor the user’s activities, run commands remotely, and steal sensitive information. The malicious Excel file properties are shown in Table 3.
Table 3: File properties of malicious Excel attachment.
| Malicious Excel File Properties | |
| MD5 | 0ec406570be4baa94ba2c70356819014 |
| SHA-1 | 9f14a7b8ae8eaf4dc2f2df9efa15ebe261b3c0c4 |
| SHA-256 | ef7cfc7d88ef776f589c3d6cf0c0c38bf258a70d77e601cea39c8dbc5c5d3552 |
| SSDEEP | 12288:JSsQGwMyrPM9ueF6HWDpM2fS0Qxqov/IXInJf5bbvcFio9TJ8/balhv9t+S2F:ktlMyz2DVf5QxqooXInJfZGi+01F |
| File Type | Office Open XML Spreadsheet |
| File Size | 633.44 KB (648641 bytes) |
The exploit downloads a Remcos instance from the following IP address by issuing a direct HTTP request:
- 208.136[.]4:80
The Remcos file has the following properties in Table 4:
Table 4: File properties of Remcos malware downloaded by exploit.
| Remcos Instance File Properties | |
| MD5 | d4737ba9edce7dae4e80d9c6b8dd7931 |
| SHA-1 | 6733b801c76003b32fa5f3548515148ec17b99db |
| SHA-256 | abdbc9b2fc56b9dd451fffae65630dc6ef64a6d30b73e4a46c4e4efb0180c92d |
| Imphash | f34d5f2d4577ed6d9ceec516c1f5a744 |
| SSDEEP | 24576:fq1e+17pi+O/ZscsxJKofEK+cHTWgPHrkLiq40ptjH80:yY+17vcs3hflvk+/Gt |
| File Type | Win32 EXE |
| File Size | 1.27 MB (1327104 bytes) |
This instance is packed with a .NET-based packer that implements several defense evasion tactics. For example, the sample invokes the sleep system call with a large time value enabling the malware to evade some automated malware sandbox analysis systems (though not Juniper’s!). Once the sleep system call returns, the second stage payload decrypts the configuration file and the malware payload. Then, the second stage injects the malware payload into Windows Explorer and executes its primary functionality as illustrated in Figure 2. The malware then creates an autostart registry key to ensure the sample persists after reboots. The configuration file tells the Remcos instance about the command-and-control (C2) domain, campaign name, unique host ID, and what type of information to log and exfiltrate. Table 5 shows the decoded configuration file.
Table 5: The decoded Recoms configuration file.
|
{ “Host:Port:Password”: “gdyhjjdhbvxgsfe.gotdns.ch:2718:1”, “Assigned name”: “Awele-Host”, “Copy file”: “qos.exe”, “Startup value”: “Jm”, “Mutex”: “Rmc-VC3F2C”, “Keylog file”: “logs.dat”, “Screenshot file”: “Screenshots”, “Audio folder”: “MicRecords” } |
Then the malware creates keyboard hooks to capture user keystrokes and store them in logs.dat. Also, the malware takes screenshots and records audio, which will be sent to the malicious threat actor’s C2. This instance had the following C2 information:
- gdyhjjdhbvxgsfe[.]gotdns[.]ch
The attacker uses a dynamic DNS provider called gotdns for the C2 that resolves to 37.139.129[.]71. This IP address belongs to the autonomous system AS211252, which, according to URLHaus, has hosted over 90 malware sites in the past 30 days. Thankfully, Juniper’s SecIntel feed has coverage for those indicators; so even if a customer had been infected, the outbound malware communication would have been blocked. Nevertheless, this example demonstrates how the Juniper ATP and Juniper SRX devices detect and stop malicious attachments before they reach customer devices.
Email File Scanning with ATP
Customers with an active Juniper ATP subscription can take advantage of email file scanning. Figure 3 shows the detection of the malicious attachment in the user interface of the Juniper ATP platform. To enable email attachment protection, customers should log on to their Juniper ATP portal, click the “Configure” menu item on the left, select “Email Management,” and then select the email server type (SMTP or IMAP). After selecting the email protocol, customers can configure which servers to allow the Juniper SRX to inspect and the follow-up action once a malicious threat is detected. These follow-up actions include “Quarantine malicious messages,” “Deliver with warning headers,” and “Permit messages.”
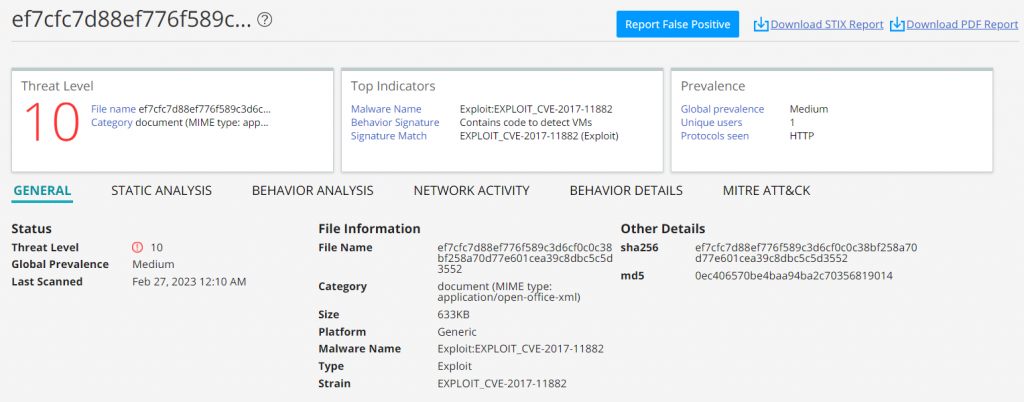 Figure 3: Remcos email attachment detection in ATP.
Figure 3: Remcos email attachment detection in ATP.
Additionally, customers can customize the type of files to scan or use only reputation-based analysis. The reputation-based analysis creates a hash of the file and queries the ATP platform. However, as we have seen in the email traffic statistics, attackers will most likely modify their malicious files to evade reputation-based analysis. A more effective approach is to enable file inspection by accepting the default scanning configuration.

























