The days when perimeter security was sufficient are long past. That’s not to say that perimeter security is unimportant, but as east-west traffic has dominated north-south traffic, practices like microsegmentation have become a critical part of any robust security posture.
But security is undergoing yet another transition as the bounds of the network expand beyond a single domain. Where an application might have ran in a data center before, the rise of cloud and multicloud stretch the conventional definitions for workload environments. As applications change, the supporting infrastructure must also change.
Distributed workloads
The promise of multicloud is that workloads and users can reside anywhere. This means that an application historically housed in a data center might have instances or components that exist well beyond the data center. During times of heavy load, for instance, enterprises might burst into one or more public clouds for additional capacity. For critical applications, perhaps the workloads run on an edge compute node, as with IoT making use of multi-access edge computing (MEC).
Even within a public cloud, enterprises that take architectural control are likely distributing their workload across different availability zones to avoid the catastrophic impacts of a public cloud outage. In this case, while an enterprise’s application might be in the cloud, it is likely deployed across multiple domains within that cloud – the cloud equivalent of managing multiple data centers.
The point is that the application is no longer bound to a single data center. And this means that microsegmentation is no longer a data-center-only proposition. Further, the rise of distributed cloud (things like Amazon’s Greengrass and Microsoft’s AzureStack) will simply amplify this effect.
What does security look like in this new world?
Diverse workloads, unified policy
Today, enterprises already know how to manage each of these environments. The challenge is not the baseline security policies needed to make any one of these instances work. Rather, the challenge is operational.
Given the diversity of deployment options, how can enterprises guarantee uniform policy? If each domain is managed with its own tools, using their own syntax and demanding their own teams, providing a uniform security umbrella becomes difficult. Enterprises either have to pay for this complexity with a degree of cross-team coordination that is expensive and fraught with peril, or they have to accept an uneven application of security across the balance of the business.
In a static environment, this is painful. In one where applications are dynamic—instantiated as, when and where they are needed—this is unpalatably limiting.
ONUG weighs in
This year, the Open Networking User Group (ONUG) Software-Defined Security Services (SDSS) Working Group challenged solution providers to showcase and prove how they solve complex workload security issues. This challenge and all solutions demonstrated were moderated and judged by Stephen Collins of ACG Research, Eric Hanselmann of 451 Research and Tom Hollingsworth with Tech Field Day.
One of the key judging criteria of the challenges was a solution’s ability to assign security policies to workloads. This is important because these policies must be enforced at the workload level, regardless of the compute environment, to protect assets at a granular level. The tradeoff for granularity is operational cost, which adds the requirement that these policies be orchestrated centrally across a diverse set of application environments.
Additionally, the nature of threats is that they are ever-changing. This means that security must be continuously deployed, from application instantiation through teardown. There can’t be any delays between workload lifecycle management activities and the application of appropriate security policies. Whether it is access control, authentication and encryption, IDS/IPS or other security services, they must be always-on.
Finally, if the effective administration of security is operationally complex, the efficacy of that security will be questionable. Enterprises cannot rely on burdensome workflows executed flawlessly by operators over any extended period of time. Solutions need to be simple, multi-domain and dynamically managed if they are to offer adequate protection for the enterprise.
Proving Juniper’s strength with Contrail Security
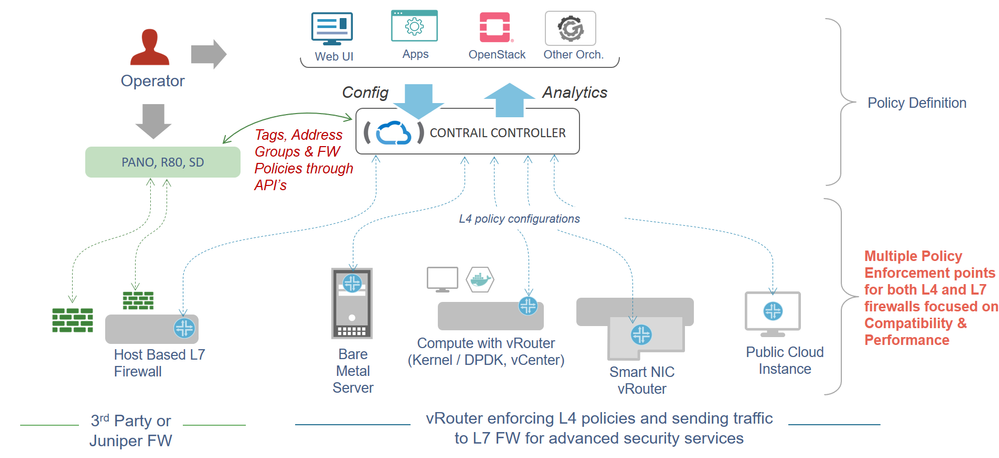
Juniper Networks has demonstrated how Contrail Security, a major component of Contrail Enterprise Multicloud, enables enterprises to define end-to-end security policies once and apply them across any cloud, any workload and any deployment.
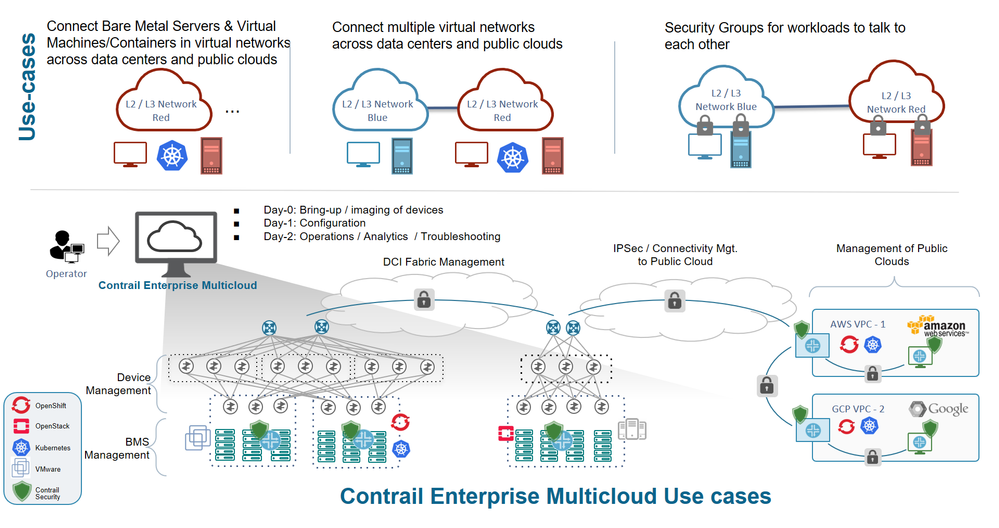
The benefits of Contrail Security include:
- Policy construct – flexible tag-based policy creation, securing workloads running on VMs, Containers and bare metal servers
- Public cloud extension – integration with public cloud providers, such as AWS, where users’ end-to-end security policies can be scaled out elastically and be portable across clouds
- Multicloud encryption between Contrail vRouters deployed on-premises and on AWS to provide secure communication between workloads deployed across clouds.
- Comprehensive Juniper security solution integration with Juniper’s Software-Defined Secure Network (SDSN) for IDS/IPS and L4-L7 security capabilities, protecting users from any number of security threats
Looking ahead
The industry is certain that workloads are evolving to become more elastic and portable. And the continued rise of scale-out applications will only speed up the shift to multi-tiered application architectures built around micro services frameworks. This will drive changes in security that require enforcement not just at the application, but at the component level.
Of course, this will all happen in the context of the simultaneous migration to cloud and multicloud, which means that security policies will need to be executed across diverse environments. Intent-based approaches that abstract the policy from the underlying infrastructure will be table stakes as enterprises look to simplify administration while improving their security posture.
Contrail Enterprise Multicloud is built with this future in mind. Hardened in the most complex environments on the planet—including carriers like AT&T, SaaS providers like Workday and enterprises like eBay—Contrail brings the best practices from the cloud into enterprises of all shapes and sizes. It is no surprise that it has taken home back-to-back ONUG SDSS awards.
By unifying policy end-to-end across single-domain, multi-domain and multicloud environments, Contrail provides the abstraction and orchestration capabilities required to truly secure and simplify enterprise operations.