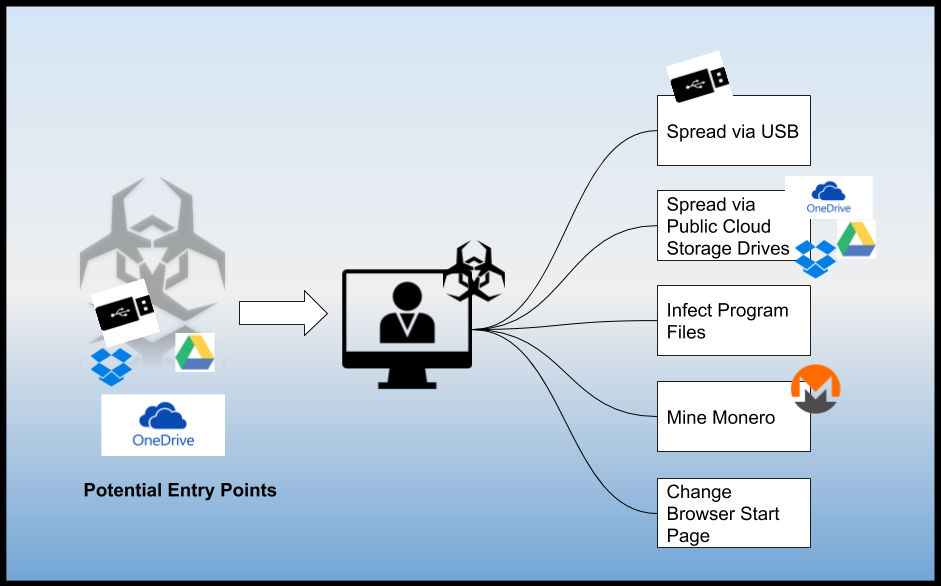
Juniper Threat Labs discovered a family of Monero Miners that spreads through cloud storage providers such as OneDrive, Google Drive and Dropbox. It also has the ability to mutate or change itself to try to avoid detection.
The volume of unique samples is relatively large, as more than 160,000 unique samples were submitted to VirusTotal over a period of 90 days. This malware can also spread via removable drives.
Monero Miner
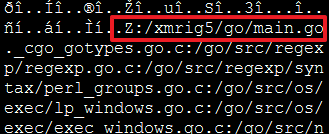
This malware’s main objective is to mine Monero. It includes in its body a version of XMRig miner. The system infected with this malware will be noticeably slow, as the cryptominer will consume most of the CPU.
We were able to extract the XMRig configuration files from the binaries we analyzed and identified at least four mining pools that this miner joins. This indicates that there could be more than one threat actor operating this network of miners. Below are examples of configurations which comprise the mining pools this miner joins, including usernames and passwords it uses.
|
“pools”: [ { “algo”: “cn/r”, “url”: “35.156.248.16:443“, “user”: “1111”, “pass”: “x”, “rig-id”: null, “nicehash”: false, } |
Sample: ad5c6dbc06422bc19682080fc2eb40e24ad7913836f7947ffc3d791ddf488d07
|
“pools”: [ { “algo”: null, “coin”: null, “url”: “n73fu7.wayout.pictures:3333“, “user”: “44VFWAnouZiSaEJMASVtZWc4dvtZgP3snVJQ6mtPHBgCgRQ93wA6N8tDiLauJru1cp2mfaWsvrthuX4hGVPizRSQGDYMD9c”, “pass”: “x”, “rig-id”: null, ], |
Sample: 271cb5b032376c6531f4f57fe17b4f9255ac2577b59320ad49f59e1f60cb4689
|
“pools”: [ { “algo”: “cn/r”, “url”: “abrakadabra.host:443“, “user”: “1111”, “pass”: “x”, “rig-id”: null, “nicehash”: false, “keepalive”: false, “enabled”: true, “tls”: true, “tls-fingerprint”: “e7658755a5a527a4db783b032bbbc91501c8605e72947213ffc7aae7d52502f4”, “daemon”: false } ], |
Sample: ec3ffdfd40d9bef3c7ffe3dfd4838f42cddbd1981135d87e193dc18419f964a0
|
“pools”: [ { “algo”: null, “coin”: null, “url”: “fh724.pikatchuworld.club:3333“, “user”: “1111”, “pass”: “x”, “rig-id”: null, “nicehash”: false, } ], |
Sample: 1a455a3291e996ef9f7e964695eb48646d223e588ccb1f355c06fc21b1052456
Public Cloud Storage Infection
One unique characteristic of this GoMiner is that it can spread itself via public cloud storage by dropping several copies of itself in “Public” folders.
It looks for the availability of the following files before dropping itself in those directories:
- %USERPROFILE%\Dropbox\Public
- %USERPROFILE%\OneDrive\Public
- %USERPROFILE%\Google Drive
When the above folders exist, it will drop a copy of itself with the following filenames:
- USBDriver.exe
- Installer.exe
- Install.exe
- Setup.exe
Fortunately, the current versions of DropBox, OneDrive and Google Drive do not have the “Public” folder by default. However, you can still get infected, if you have synced someone’s public folder who is already infected.
USB Drive Infection
This GoMiner worm spreads by scanning available removable drives. If found, it will drop a copy of itself using any of the following files:
- USBDriver.exe
- Installer.exe
- Install.exe
- Setup.exe
It also drops an autorun.inf file to trigger automatic execution of the malware when removable drives are attached to a PC.
Code that drops to USB drives
“Program Files” Infection</strong?
Each time this malware is executed, it looks for any executable file in the “Program Files” folder and replaces it with a mutated copy of itself. This means, whatever application it replaced will now become the GoMiner.
Mutation
Another unique characteristic of this malware is its ability to mutate itself. Mutating malware is not new but malware doing this is rare these days. We believe that this is an attempt by malware authors to avoid detection.
It has a function named “change_self_b”, which generates a 4-byte key and uses this key to XOR most of the bytes in its body as we will describe below. The generated keys are random and saved at a specific offset in the binary.
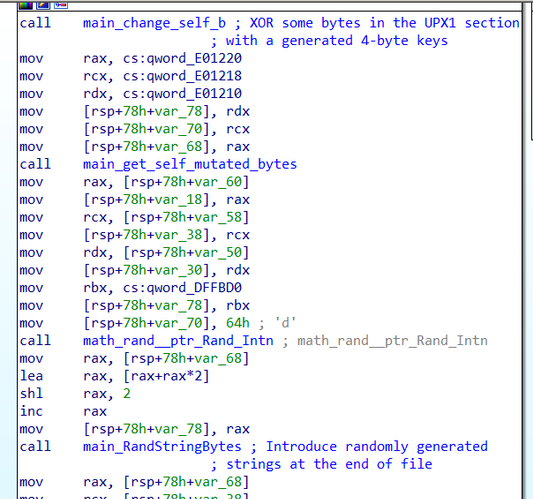
When the malware executes, the first thing it will do is return the original values of the encrypted bytes in the file. It accesses the 4-byte key at the specific address and then decrypts it’s code. This is before the UPX unpacking stub, which is the reason why the UPX tool cannot unpack.
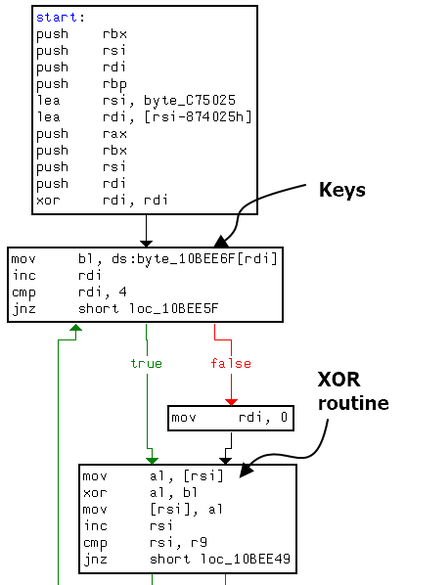
Additionally, it has another function that generates random strings and appends them at the end of the file. This simple technique changes the hash of the sample that could evade hash-based detection tools such as blacklisting.
Footprint
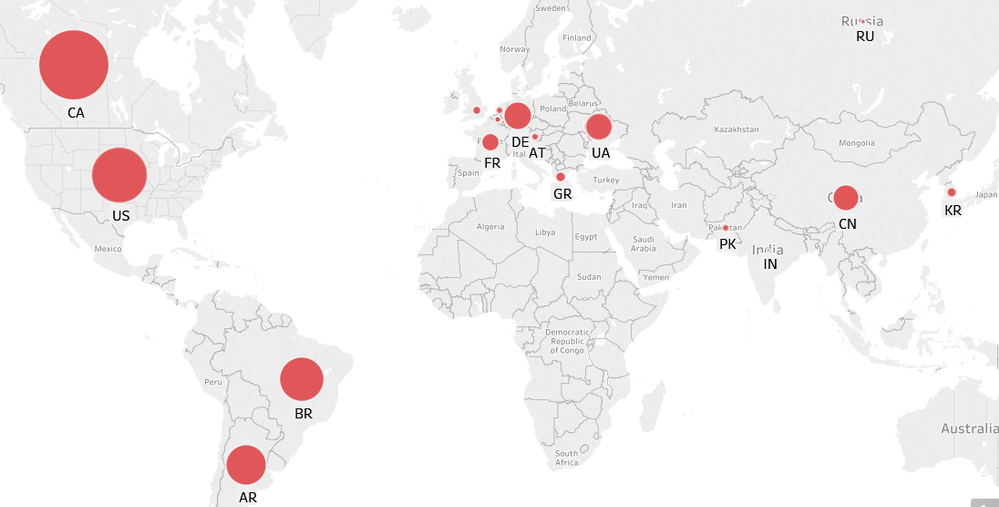
Over a period of 90 days, 165,000 samples of this malware have been submitted to Virustotal. We used the submission data in VT to identify the footprint of this malware around the world. Most of the samples were submitted from Canada, the U.S., Brazil and Argentina.
Other Details
All the samples we have seen are 64bit and compiled with Go, with sizes ranging from 2MB to 7MB for packed samples and up to 15MB for unpacked samples.
This miner uses UPX as a packer but a simple XOR decryption routine is added before the actual UPX unpacking stub. This causes the UPX tool to be unable to unpack the initial file. This can be a way for the malware to avoid detection by tools relying on the UPX tool to unpack.
It is usually a challenge to reverse such samples compiled with Go because of its different structure and the additional functions it introduces, compared to a typical C-compiled binary. To aid us in our analysis, we used an IDA helper script to rename functions that are introduced by the Go compiler. After using the script, it became easier for us to reverse since the main functions were already visible.
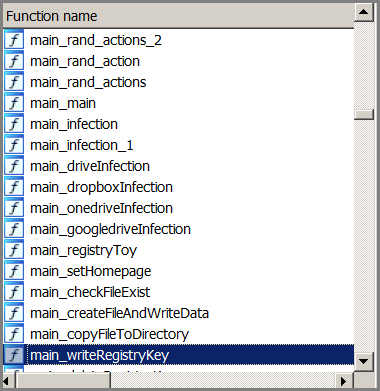
The routines of this malware can be divided into four sections.
- RegistryToy
- It disables Windows Task Manager, Registry and CMD through the registry. This is usually done to make system administration harder.
- XMRig Miner
- Run the XMRig miner.
- Random Action 1
- It chooses from the following sets of functions randomly in a loop:
- Main_Walk – Replace applications.
- MainHTTPHit1 – Connects to randomly generated readme.io subdomains e.g., {random}.{random}.readme.io and drops a mutated copy of itself in the current directory.
- MainHttpHit2 – Connects to randomly generated readme.io subdomains e.g., {random}.{random}.bitbucket.com and drops a mutated copy of itself in the current directory.
- MainPlantStartup – Creates an autostart entry in the registry and drops itself in %system32%\{random}.exe.
- Random Action 2
- It chooses from the following sets of functions randomly in a loop:
- Worm Infection
- Spread Via Removable Drive
- dropboxInfection
- oneDriveInfection
- googleDriveInfection
- SetHomepage — Sets the browser start page to randomly generated domain
- Drops a mutated version of itself in the current directory
Conclusion
This malicious miner caught our interest because of the volume of samples we are seeing and its ability to spread itself and mutate. Its capabilities are an effective way for the malware to try to avoid detection while increasing its footprint. On one hand, the malware has gone to greater lengths than other miners to avoid detection. However, once on a system — and because of the changes it makes to random executables and to the browser’s start page — it doesn’t take long before the user recognizes something has gone horribly wrong.
Juniper Advanced Threat Protection products detect the samples and block the malicious mining pools.
IOC
Sha256
1a455a3291e996ef9f7e964695eb48646d223e588ccb1f355c06fc21b1052456
271cb5b032376c6531f4f57fe17b4f9255ac2577b59320ad49f59e1f60cb4689
ec3ffdfd40d9bef3c7ffe3dfd4838f42cddbd1981135d87e193dc18419f964a0
Ad5c6dbc06422bc19682080fc2eb40e24ad7913836f7947ffc3d791ddf488d07
685223dda5556cda659cb4f5e89cde24b81c910a78b1bdeed008380dc1d62417
68a6f1e34ab571772f8aa4699b2904b9eb05de5bd2224edee138e17f87898cd4
18a2213384ec97c2b51cda378688f34b143b83a0f005977b748cca18dae2f5cd
1f36c63d182c6348e233ff8601185b585aee77eaadaab10bc226ac9df47e5ee4
ecdcc6273bd8ccbf2740a3e43caba81647d9abec14386d7df3a3e9f725b2493a
69e48b7fac8d4e318dc79adb67bb2b56c27b020fa92c86ac1b01b2c0fb50a62e
3fc3a8c9ed96021927bcd2ec69a487d51b66d7e5d03d252cf6a0bae9074e0327
fb7fd2710279a64056cbf7b55fef5dbbaf598f0b5958c71f045749685edaa1c4
77f59a8bc999e3c368894332e37ae88b986ed67d3a16a1557373ba076527db44
706f7bd0508a91905196fcfafedba742e9ec920e9e8dc4ba1e4d90cc279f6350
2e3c8c7eb64bb881fcb82f14a20a788221a17bc048ad58ca7702363986b9dfc7
5d4de43d56f18c0a69c126eff8a792c47192a4197a6ec5e1fa0333436fe4687b
98e1b71ff1980c7e1484dedde2cc6f6e6eea842729405d925dd6855795a54197
66c77ed578dbdb6c5076a66098e330b1682a69ee361bc9746f33a12f53e3e29b
51dccbe2d84e52a4b5e0cb13379d0c79fa3a03f01ea0119e7b19c174d5b0ead4
96e2bb8d289f25c3f0c61d08ea96bfc897ee95793121e5c5eafb41c4cc0aebf2
9c4d85811fd1347a155dca7b5ad4be2a08b3adf932849d4e8b1320bd339a772e
25496ec3b287c215e7a802ee4b7aad20e9eac550a4e044fe68a937baff04a077
cb8f3a0b35b985204d4f371b2f41510d503eeb1da1f51a5aee533f5ecc1b078b
a50e043fb25d68bb38deb38b8d31728c1ba2df3d68ac5cd0eed633f341485048
68a6f1e34ab571772f8aa4699b2904b9eb05de5bd2224edee138e17f87898cd4
1f36c63d182c6348e233ff8601185b585aee77eaadaab10bc226ac9df47e5ee4
ecdcc6273bd8ccbf2740a3e43caba81647d9abec14386d7df3a3e9f725b2493a
69e48b7fac8d4e318dc79adb67bb2b56c27b020fa92c86ac1b01b2c0fb50a62e
aa2c806c3ff473185e2df94e265bb0886c030daefa6f378866282fba37942820
5d4de43d56f18c0a69c126eff8a792c47192a4197a6ec5e1fa0333436fe4687b
66c77ed578dbdb6c5076a66098e330b1682a69ee361bc9746f33a12f53e3e29b
51dccbe2d84e52a4b5e0cb13379d0c79fa3a03f01ea0119e7b19c174d5b0ead4
25496ec3b287c215e7a802ee4b7aad20e9eac550a4e044fe68a937baff04a077
cb8f3a0b35b985204d4f371b2f41510d503eeb1da1f51a5aee533f5ecc1b078b
18623498d214284064336b5c49b6205de2b0724952d2cf45d819b4d034a3260b
6a42e610c1adf2d347488ec2fd42127dd1e3ca667519f7ac0a0728118f9fc607
ad01b428e35bf4b70b86d050dae8e4036791018608d70564ebfa5fec04027051
ab3790c79cc449d865e2568f2a4f854883fe0792d37c17f0a5c082581bd5fd7b
fd2b55482f3db95e0a0b4d8d563ce45d08a43b5692ac4eee5c61b6084678eb38
f46b3e8885d75baff9ec81192feeef61f1f05826d900fb05518797aae9db7b79
712939c0a69c74ba85ebab9a48c3fd2934b9cb5a3ff0a506f3a1944386a15755
9c76815aa2612c6777ce9addbcc38601d2d44e0b0de8787cdb922b0218a765f4
504a44632664652d9fe9a27519194d2296f85905fc68341b30eb9f97b8c9cf01
db3ce6b9ad58923db5e2a3137c40a59ab186f223483f696869d56a641b233062
Mining Pools
35.156.248.16:443
N73fu7.wayout.pictures:3333
Abrakadabra.host:443
fh724.pikatchuworld.club:3333