In October 2016, a major domain name system (DNS) service in the United States was hit by a very sophisticated and complex distributed denial of service (DDoS) attack that clogged its servers with malicious requests from tens of millions of IP addresses. The attack caused major disruptions and outages for internet heavyweights such as Twitter, Netflix, Spotify and Reddit.
Of course, there had been many DDoS attacks before and organizations had long put in place defenses against them. But the October 2016 attack was different. It was caused by malware called Mirai which took advantage of the vulnerable security of devices connected to the internet – the so-called Internet of Things (IoT). In the case of the October 2016 attack, the majority of the devices used were reported to be CCTV cameras.
The Internet of Things is growing rapidly. Estimates vary, but it’s certain that a vast range of IoT devices that deliver applications for home management, environmental sensing, driverless cars, remote healthcare, virtual reality, industrial automation and frictionless logistics will significantly outnumber mobile phones by 2020.
Ripe for the Picking
There are many reasons why those with malicious intent would want to hack into IoT devices – they not only provide a gateway to accessing the valuable private data of individuals, corporations and governments – they can also be used to hold companies ransom and bring networks down.
The problem is how to secure IoT devices. Unlike smart phones which have increasingly been designed with sophisticated security measures to their products – finger print recognition and pattern swiping, for example – to not only ensure that the device is authenticated correctly on the network, but that the person using the phone is who they say they are. IoT devices don’t necessarily have this level of security. In many cases, the most advanced devices only use SIM authentication.
The Mirai malware worked by scanning the internet for these vulnerable devices and exploited those with factory-default or static username and password combinations. The fact that these devices lacked encrypted authentication and simple credentials compounded the risk.
Strengthening Security
Of course, IoT device manufacturers have a part to play in improving the situation. As awareness of the problem grows, device security will become a key purchasing requirement. Vendors who cannot demonstrate the highest levels of security will lose competitive advantage.
Governments are reacting, too. Already, California has brought in a cyber security law outlining the requirements for devices that connect directly or indirectly to the internet. And in the UK, the government has produced a code of practice for manufacturers of IoT devices.
But will this be enough? A 2018 survey of organizations that have implemented IoT projects conducted by the IoT Institute titled, “Securing IoT at Scale Requires A Holistic Approach,” indicates otherwise.
A majority of the respondents (72%) believe that the role of the network is very important or critical for their IT security. Securing the IoT endpoint is the highest priority, but it is closely followed by edge, network and cloud-based security, as the graph below shows.
Prioritized Investment Areas to Strengthen IoT Security
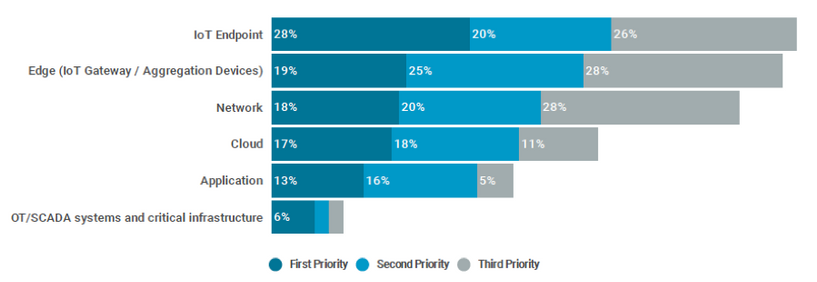
Source: “Securing IoT at Scale Requires a holistic approach”, IoT Institute and Juniper Networks.
Edge Cloud Security
In addition to organizations that have implemented IoT projects, service providers also have a vested interest in ensuring that the network is secure. With customers increasingly connecting IoT devices to their networks, service providers cannot afford damaging privacy violations or successful DDoS attacks.
Deploying security at the edge of the network can help service providers deliver the protection customers need. Edge security forms a hard line between the device and the infrastructure, putting control, execution and enforcement of policies and analysis close to devices so action can be taken more quickly.
With advanced threat prevention that includes artificial intelligence and machine learning capabilities, edge security can rapidly detect abnormal patterns and stop or quarantine the traffic before it reaches the core network.
In modern service provider architectures, edge cloud is envisioned to improve latency and enhance the quality of experience. But the edge also provides a great location to move security directly to the most vulnerable parts of the network. In addition, edge security offloads the security burden from the end points to save battery life, which is often a key consideration with IoT devices.
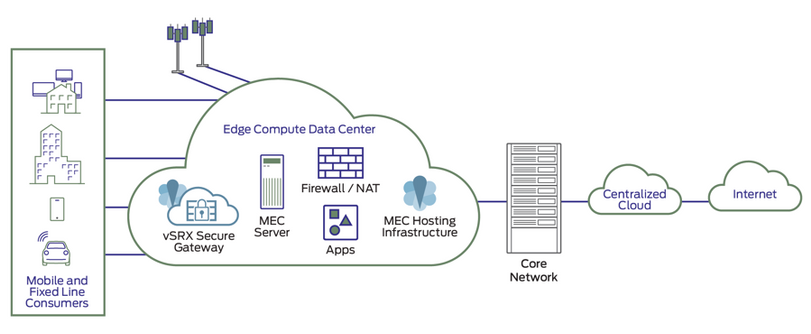
As with any other security solution, effective IoT security requires a holistic approach. Edge security solutions, such as Juniper Networks’ vSRX Virtual Firewalls and cSRX Container Firewalls, have been integrated with Contrail Edge Cloud so customers can deploy them at the edge with built-in security (Distributed Virtual Security Gateway).
Learn how Juniper can help you build a 5G network powered by Contrail Edge Cloud at https://www.juniper.net/us/en/solutions/iot/.