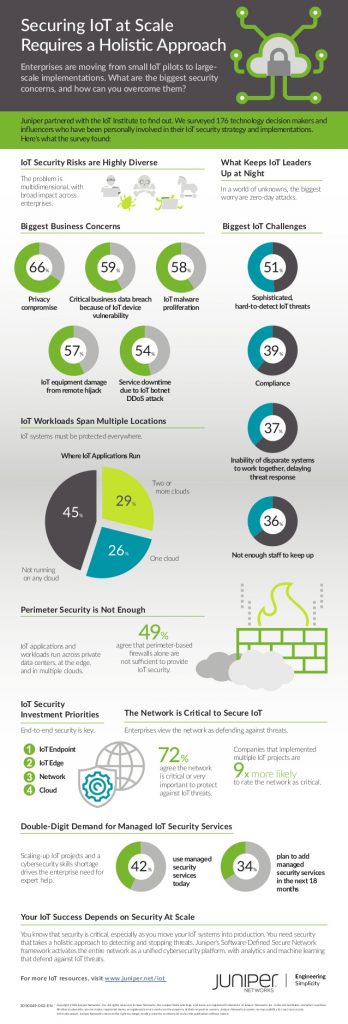
According to Gartner, “by 2020, 75% of organizations will have deployed a multicloud or hybrid cloud model for their IT needs.”1 While we’ve known for some time that the future is multicloud, ensuring cybersecurity across diverse and non-traditional environments has mostly been an afterthought. Despite organizations weaving cloud-based ecosystems and Internet of Things (IoT) devices and applications into the fabric of their networks, they have not emphasized security at the same level. To learn more about what organizations are – and are not – doing to prepare and fortify their security postures, Juniper Networks partnered with the Internet of Things Institute to survey organizations implementing IoT projects.
This study from Juniper Networks reveals that many IoT application workloads are already running in a multicloud environment, with 29 percent of respondents implementing IoT application workloads in two or more clouds. Running IoT applications in public, private and on-premises environments is an intuitive step for this technology. However, such a high level of connectivity and flexibility exposes organizations to several security vulnerabilities including compliance, lack of integration between disparate security systems and a shortage of qualified cybersecurity workers. But what is the top challenge organizations face in IoT security? Hard-to-detect sophisticated IoT threats.
For organizations preparing to move from IoT deployment pilots to at-scale production, it is critical for operators to think about security holistically – and that means starting with the network.
Out with the old, in with the new
In today’s era of sophisticated zero-day attacks, the traditional perimeter-based approach to security is no longer sufficient. Safeguarding business assets, data and IoT ecosystems must start with the network. This means visibility and protection must be embedded into the network fabric to enable real-time monitoring, detection and remediation and prevent cybercriminals from compromising valuable business information.
51 percent of survey respondents reported that they run their IoT application workloads in their private data or control centers, while 36 percent maintained deployments at the network edge and the remainder run their workloads in a public cloud. Moreover, 26 percent reported that they use a combination of the above. This expands and distorts any notion of perimeter-based security. Since IoT application workloads are being deployed in an increasingly diverse number of external places, the perimeter cannot be the only line of defense.
To address this need, security and policy enforcement must be widespread with a zero-trust model that does not rely solely on human abilities to prioritize and correlate vast amounts of threat intelligence. Juniper’s unified cybersecurity platform, powered by the Software-Defined Secure Network (SDSN), transforms the entire network into a cyber-defense system with analytics and machine learning incorporated to defend against IoT threats across environments. In other words, if one application on the network is compromised, it can be quickly isolated to stop the spread of the infection.
While shifting to a zero-trust model can help protect your organization against its most looming threats, you may need to dig deep to find the right team to implement it.
The automation skills gap
Few will argue against widespread security automation throughout the network, but there is a serious skills gap when it comes to implementing this critical technology.
It’s well-known that the cybersecurity industry is facing a skills shortage, but more specifically, we are seeing a large automation skills deficit. A recent Juniper Networks and Ponemon Institute study found that the ability to integrate disparate security technologies is the primary challenge network architects face in achieving an effective security automation architecture. This sentiment is echoed by Juniper’s Internet of Things Institute study, which found that a lack of qualified staff to keep up with IoT security is a major roadblock for 36 percent of respondents.
In the long term, education in automation will be critical to solving this problem and ultimately enhancing how IoT applications run in a multicloud environment.
Until the gap can be closed, network equipment and security solutions with built-in automation and seamless integration are key to avoid the hassle of implementing a separate automation layer. Juniper’s advanced unified cybersecurity platform helps streamline security operations and automate policy management for a more efficient and effective cyber-defense system.
A holistic approach to security
When planning to strengthen an organization’s security posture, a holistic approach must be top of mind. Focusing solely on endpoint security is anything but a foolproof solution. The good news is that the majority of respondents (72 percent) believe the role of the network is very important for securing IoT applications and devices.
As enterprise leaders prepare to scale their IoT deployments, they should consider how to address multicloud complexity, especially in terms of connectivity, security and operations. As it seems like a new security breach hits the news cycle each week, IT leaders must rely on total end-to-end visibility to avoid being another statistic.
IoT operators must think beyond endpoint security and ensure detection across the network in order to achieve a truly secure deployment.
To learn more about how Juniper can help your organization secure IoT at scale, visit www.juniper.net/iot.
1 Gartner, Market Insight: How Tech CEOs Can Position and Promote Services in the New World of Hybrid Cloud and Multicloud, 13 September 2018
Securing IoT at Scale Requires a Holistic Approach from Juniper Networks

























