The use of containers as a low-footprint infrastructure upon which to run microservices introduces another layer of infrastructure that needs to be secured. With Juniper Connected Security, organizations can provide industry-leading security for their containerized workloads, extending visibility and enforcement all the way down to the communication between individual microservices within an application.
Like all aspects of IT, containers need to be secured and administrators need visibility into data flows moving in and out of these containers. Monolithic applications are difficult to scale and incredibly inefficient when scaling is achieved. As a result, this has driven the sharding of applications into microservices for the past two decades and microservices are driving the adoption of containers.
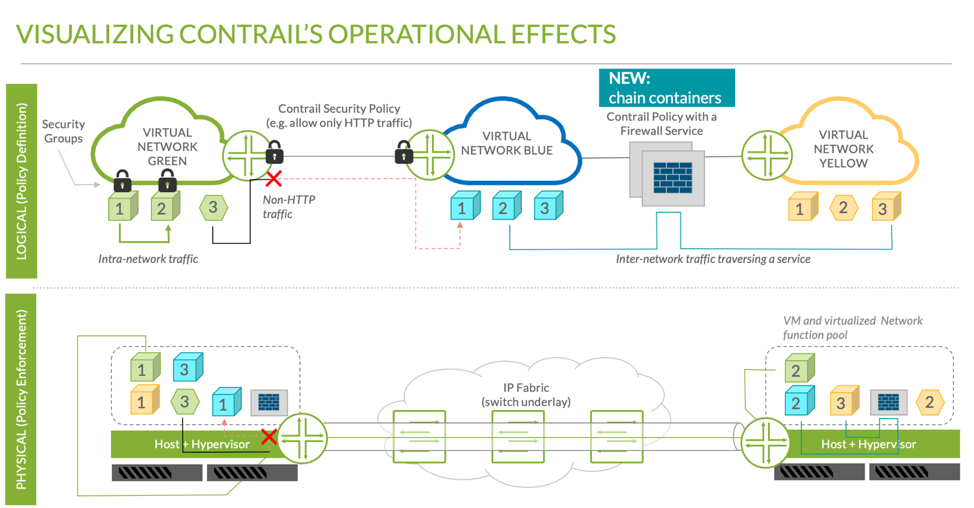
With the release of software-defined networking (SDN) controllers such as Contrail, the ability to participate in network function service chains was introduced to Juniper’s Containerized SRX (cSRX). Acting as a “bump in the wire” between two data flows and a target container, the cSRX adds security enforcement points where none existed before and offers the most comprehensive network security for Docker Containers that is available today. With Contrail, the addition of security is now transparent to application developers.
The cSRX also offers further network visibility, allowing organizations to respond more quickly to emerging threats. Individual containerized applications or microservices can be provided with their own next-generation firewall, or even an entire chain of network security services, depending on the need.
Advantages of the cSRX Container Firewall
- Purpose-built to secure containers: cSRX is the industry’s first containerized firewall. The cSRX deliberately leaves out dynamic routing or networking capabilities of the vSRX or hardware SRX firewalls in order to stay nimble. Containerized environments allow workloads to be created and destroyed quickly, in order to respond to demand. Seconds matter and the short instantiation time of the cSRX is a significant benefit to customers.
- Small footprint, highly agile: cSRX firewall instances can be instantiated in seconds and have the small footprint expected of containerized applications. This is accomplished by taking a microservices approach to the provisioning of containerized security.
- Defends against increasingly sophisticated threat landscape: The cSRX integrates features such as advanced threat prevention, as well as IP and URL blocking based on threat feeds. This makes it more than the bare-bones firewall that has become typical of containerization deployments, and instead a core piece of containerization infrastructure.
- Supports emerging technologies: The small footprint and rapid instantiation time of the cSRX makes it flexible to serve emerging technologies, such as the micro data centers at the base of 5G cell towers.
- Small enough to be built into IoT devices: Packing unified threat management and an industry leading firewall into a containerization-friendly footprint with seconds of instantiation time allows the cSRX to provide protection to resource-constrained devices and to operate at scales where the savings of even a few megabytes of RAM per instance really do add up.
- Uses implicit zones: The cSRX supports segmenting traffic into zones, allowing a single cSRX container to protect multiple containerized applications or microservices, each with their own custom security configuration, further reducing the footprint of cSRX usage.
- Participates in network function service chains: By participating in network function service chains, the cSRX can offer high availability, as well as containerized security that scales individual network functions as needed.
Juniper Connected Security
What better place to inspect traffic for signs of compromise and to enforce security than at the connection point?
Juniper Connected Security integrates networking and information security products, allowing the detection of threats and the enforcement of policy at multiple points within the network. Juniper Connected Security provides perimeter defenses, cloud defenses, network segmentation, as well as virtualized and containerized security, and even defenses for edge computing.
Making Microsegmentation a Reality
Contrail has offered advanced microsegmentation capabilities for some time. However, microsegmentation can be an expensive proposition. Microsegments are virtual network segments or rule-based containment groups that are ideally used to encapsulate all of the microservices that make up a single application, or which occupy a single tier. Each microsegment is effectively its own small network, and to communicate beyond that segment, data flows would have to traverse a router. With Contrail, that router is the vRouter and it’s distributed to every compute host.
The need for data entering or exiting a microsegment to traverse a router offers a natural choke point wherein network functions could be implemented. Traditionally, these network functions required expensive hardware and each data flow would have to be sent outside of the containerization host through the various pieces of hardware and then on to their destination.
The Contrail service chains for containers and cSRX change all of that. Network functions that can be applied to a service chain include:
-
-
- Application Firewall (AppFW)
- Application ID (AppID)
- Intrusion Prevention Systems (IPS)
- Network Address Translation (NAT)
- Unified Threat Management (UTM)
- Enhanced Web Filtering (EFW)
- Screens
-
With the cSRX, Contrail can create extremely small microsegments with extremely strong perimeters, rapidly instantiating network function service chains to defend each microsegment. Entire service chains can be stood up in seconds, allowing a microsegment and all necessary network functions to be brought into service faster than the containers or virtual machines that make up the application they defend.
Paired with Contrail Enterprise Multicloud, the cSRX represents the first production-grade solution that extends a full suite of orchestration, automation, security and analytics to deploy dynamic consumer and enterprise services in a cost and resource efficient manner into the container space. For containerized application platforms like OpenShift or Kubernetes, Contrail Enterprise Multicloud consists of Contrail Networking and Contrail Security controller, Contrail vRouter with L4 Security, cSRX and/or vSRX with L7 security, AppFormix Analytics Agent and the Kubernetes CNI plugin.
 Juniper Connected Security extends security to where cloud-native applications reside to provide consistent policy across private cloud, public cloud and IoT infrastructure. Juniper’s cSRX container firewall delivers a powerful and virtualization-specific set of advanced security services to secure containerized applications and microservices and is small enough to even be deployed by manufacturers on IoT devices.
Juniper Connected Security extends security to where cloud-native applications reside to provide consistent policy across private cloud, public cloud and IoT infrastructure. Juniper’s cSRX container firewall delivers a powerful and virtualization-specific set of advanced security services to secure containerized applications and microservices and is small enough to even be deployed by manufacturers on IoT devices.
The cSRX is feature-rich, offering administrators capabilities and a management interface that they will be familiar with because they use our vSRX and hardware SRX firewalls. The cSRX plays a vital role in Juniper Connected Security, protecting individual devices and workloads in resource constrained environments.
Securing today’s networks requires multiple points of security enforcement throughout the network and the visibility to act on threats wherever they may appear. See, automate, and protect with Juniper Connected Security.
Join us at Black Hat in Las Vegas on August 7-8, 2019 in booth #238 to experience a demo of the cSRX and to learn more about Juniper Connected Security.

























