Since its emergence in 2022, the BianLian ransomware group has rapidly evolved, showcasing sophisticated techniques and adapting to the shifting landscape of cyber threats. It’s among the top three most active ransomware groups in terms of victim postings after LockBit3 and AlphV. These posts are coming from the ransomware’s leak sites and typically contain victim identification. In this blog, we analyze key findings in terms of victimology, infrastructure, and tooling to provide a comprehensive overview of BianLian’s activities.
Emergence and Initial Tactics
BianLian threat actors gain initial access by leveraging compromised Remote Desktop Protocol (RDP) credentials likely acquired from third party or via phishing. They were also observed exploiting vulnerabilities in ProxyShell and SonicWall VPN devices to gain initial access into networks. They deploy custom malware written in the Go programming language, utilizing Living off the Land (LOL) techniques to move laterally and evade detection. Their initial operations focus on encrypting data and demanding ransoms, leveraging a custom backdoor for persistence and further exploitation. The group employed a double-extorsion approach of encrypting and stealing data, thus exerting maximum pressure on victims to pay the ransom.
Shift to Extortion-Only Operations
In early 2023, Avast released a decryptor for BianLian’s encryptor, leading the group to largely abandon encryption activities. BianLian then shifted focus to a steal-and-extort model, leveraging their Go backdoor for data theft and extortion.
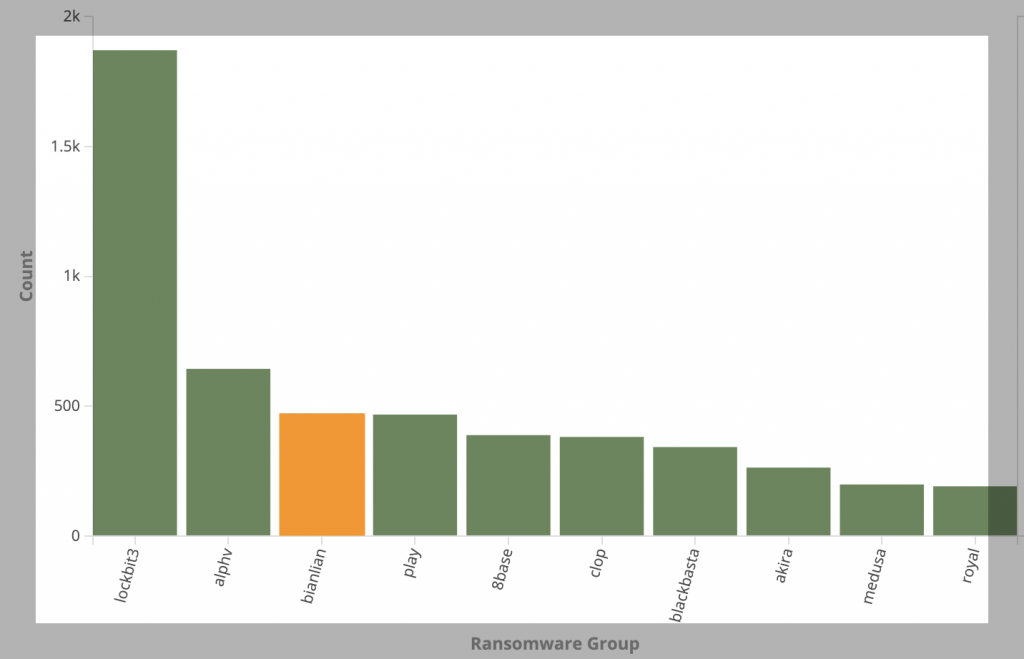
2024 Victimology
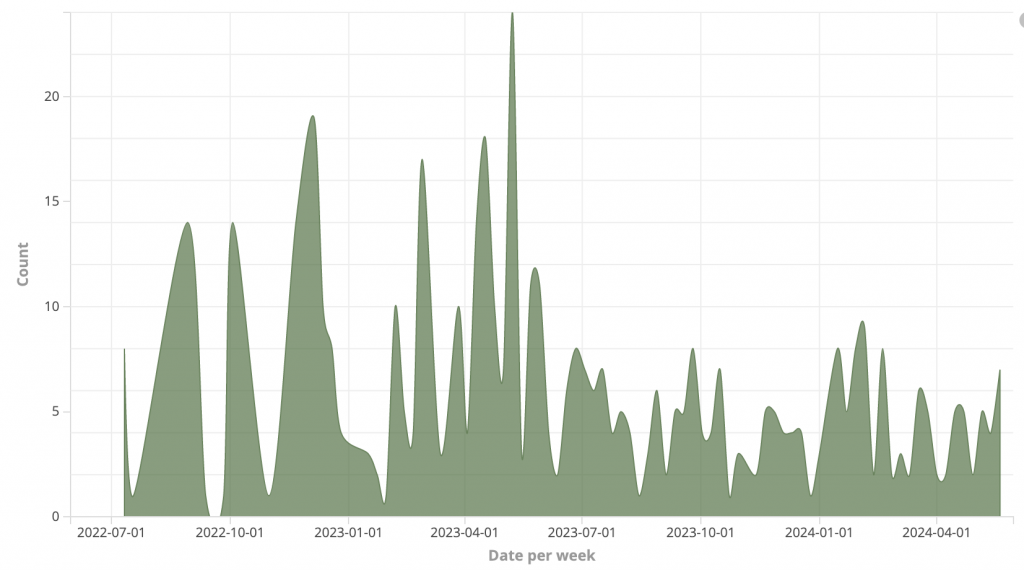
The provided graph depicts the number of victims posted on the BianLian ransomware gang’s leak site over time, from mid-2022 to mid-2024. The vertical axis represents the count of victim postings per week, while the horizontal axis shows the timeline. The highest peak occurs around May 2023. After the peak, there is a noticeable decline in the number of postings. This period shows more moderate and consistent activity. This can be attributed to the release of the Ransomware decryptor which led to the shift of strategy by the group. This can also be attributed to improved defensive measures by organizations as they are made aware of the TTP’s of the group and increased law enforcement attention on BianLian. At the start of 2024, there is a slight resurgence in activity, particularly in February.
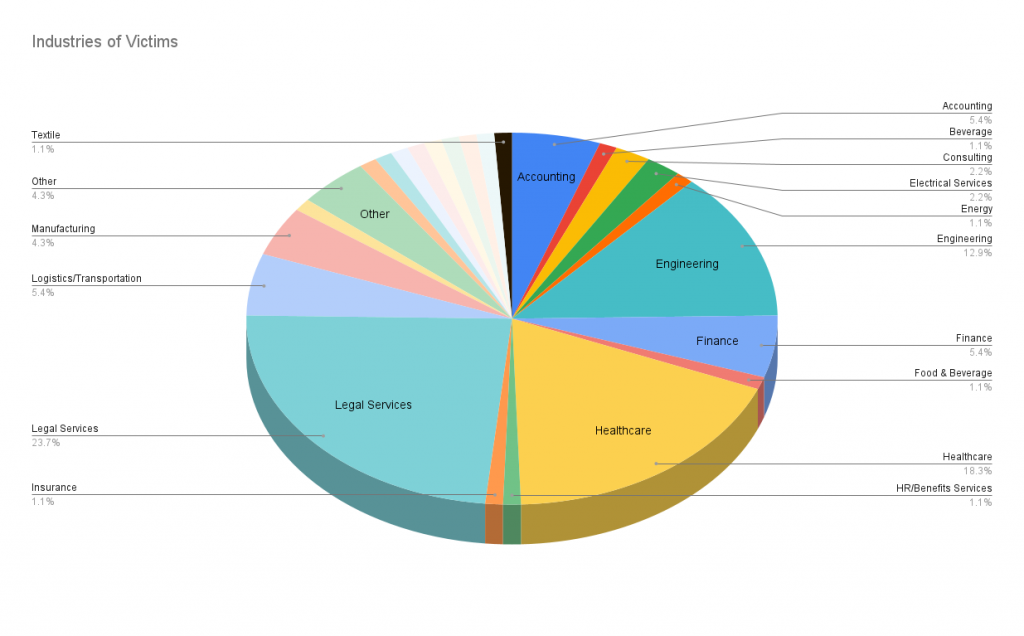
Since the start of 2024, BianLian has disclosed over 90 new victims on their leak site. The analysis of BianLian’s victim distribution in 2024 reveals a strategic focus on high-value sectors where the extorsion method can exert significant pressure to pay ransoms. Legal Services and Healthcare sectors are the most targeted, accounting for 23.7% and 18.3% of the victims, respectively. These industries handle sensitive and critical data, making them prime targets for ransomware due to the severe consequences of operational disruption and data breaches. Engineering, with 12.9% of victims, is also heavily targeted, likely due to the valuable intellectual property and critical infrastructure projects it involves.
The diverse spread of victims across other sectors such as Finance, Accounting, Logistics/Transportation, Manufacturing, and various smaller industries indicates BianLian’s opportunistic approach in targeting industries across the board.
Infrastructure
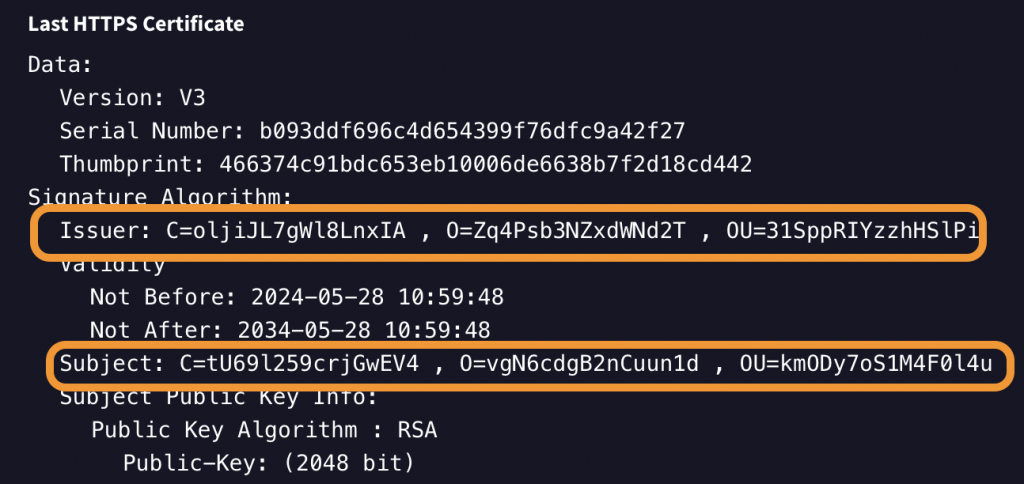
BianLian’s command and control (C2) communications use TLS. The server certificates, featuring randomly generated names, can be identified through specific patterns. For example, both the subject and issuer fields contain only the “C”, “O”, and “OU” attributes, unlike typical certificates that also include “ST” and “L” fields. Additionally, each value in these fields is exactly 16 characters long, without any spaces or special characters.
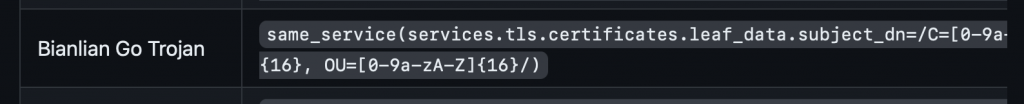
Censys provides a method to identify these certificates using regular expressions on the certificate details.
C2Intelfeeds offers a similar identification method for these C2 servers.
The following chart illustrates the number of BianLian ransomware command and control (C2) servers discovered daily in 2024. A noticeable peak occurs around mid-January, where the count of C2 servers surpasses 15 on a single day. This significant spike indicates a period of heightened activity, suggesting that BianLian ramped up its operations significantly during this time. The establishment of numerous C2 servers likely facilitated a large-scale campaign, enabling the group to manage and execute attacks more effectively.
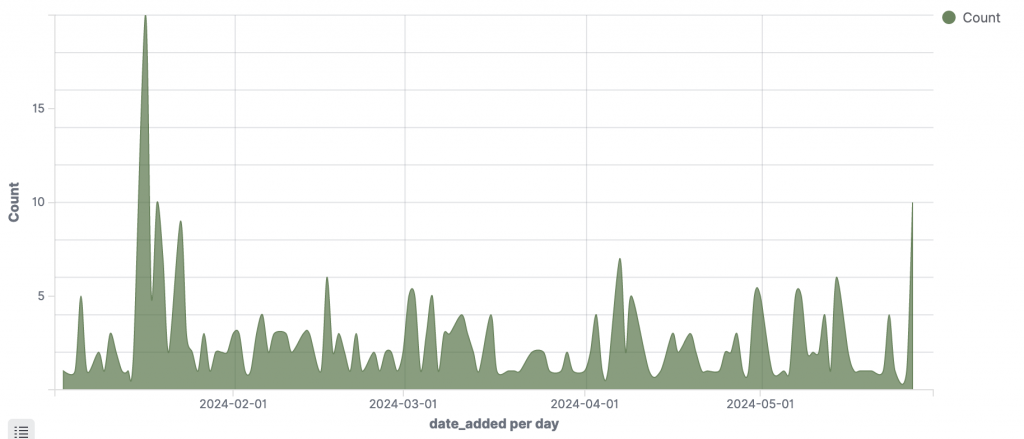
This surge in C2 servers around mid-January correlates with an observed increase in the number of victims shortly after this period, as depicted in the 2024 victimology data. The timing suggests a direct relationship between the deployment of additional C2 infrastructure and the subsequent rise in victim postings on BianLian’s leak site. It was also around this time that the group was found exploiting TeamCity server and deployed a PowerShell version of their backdoor.
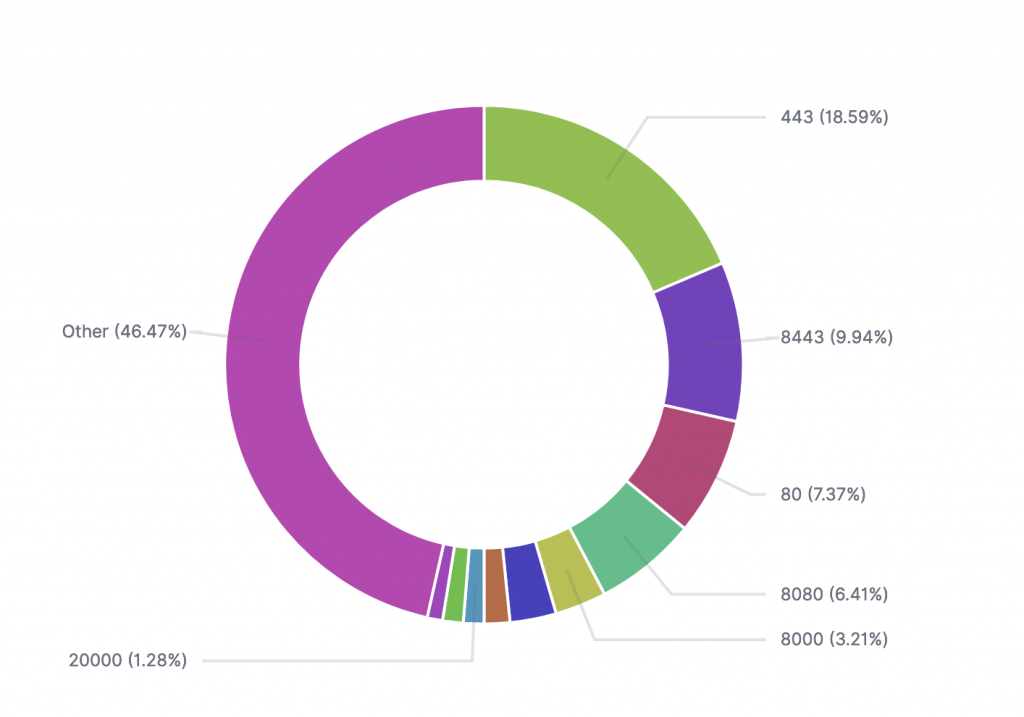
The pie chart above illustrates the distribution of ports used by BianLian’s command and control (C2) servers in 2023. The top five ports are 443, 8443, 80, 8080, and 8000, which are commonly used for web traffic and secure communications. Port 443 is the most frequently used, accounting for 18.59% of the traffic, indicating the group’s preference for blending in with legitimate HTTPS traffic. Port 8443, another HTTPS port, follows with 9.94%, further emphasizing their reliance on encrypted channels.
The chart also shows a significant portion of traffic, 46.47%, classified under “Other” ports, highlighting the group’s use of a wide range of ports to diversify their C2 communication channels and evade detection. The use of multiple ports, including non-standard ones, underscores the importance of comprehensive network monitoring to detect and respond to such threats effectively.
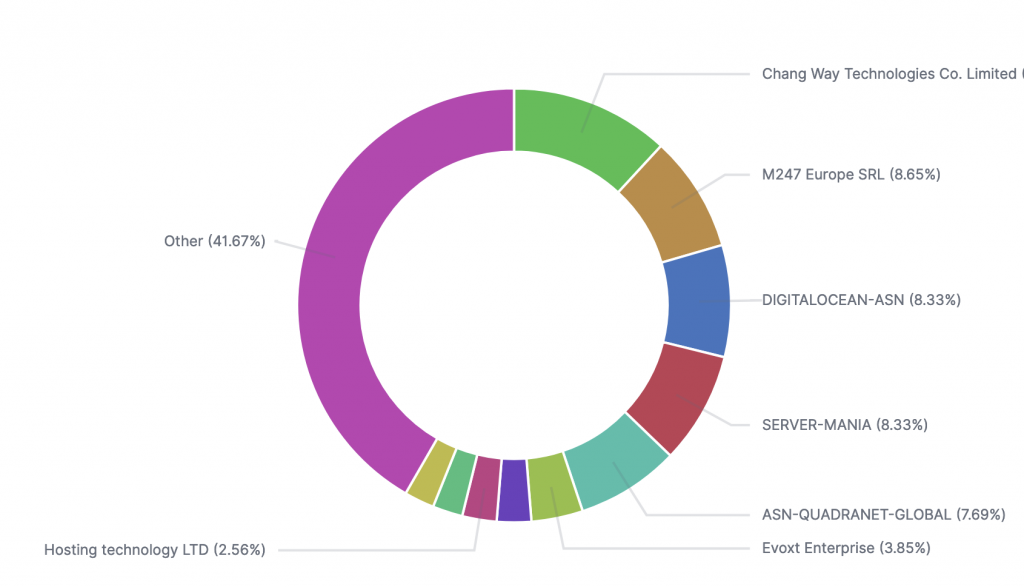
The chart above illustrates the Autonomous System Number (ASN) distribution of BianLian’s command and control (C2) servers for 2024, highlighting a strategic use of diverse hosting providers. The top ASNs include Chang Way Technologies Co. Limited, M247 Europe SRL, DIGITALOCEAN-ASN, SERVER-MANIA, and ASN-QUADRANET-GLOBAL, each accounting for significant portions of the C2 infrastructure. Notably, 41.67% of the servers are distributed across various other ASNs, indicating BianLian’s deliberate effort to diversify and avoid detection by spreading their infrastructure across multiple networks.
Backdoor
BianLian’s backdoor, similar to their encryptor, is developed using the Go programming language. Its main purpose is to function as a loader, with a primary focus on downloading and executing additional malicious payloads. The backdoor is designed with a hard-coded command and control (C2) server address and port, which it uses to communicate and receive further instructions from the attackers. This design choice ensures that the backdoor maintains a persistent connection with the C2 infrastructure, enabling BianLian to manage their malicious activities effectively.
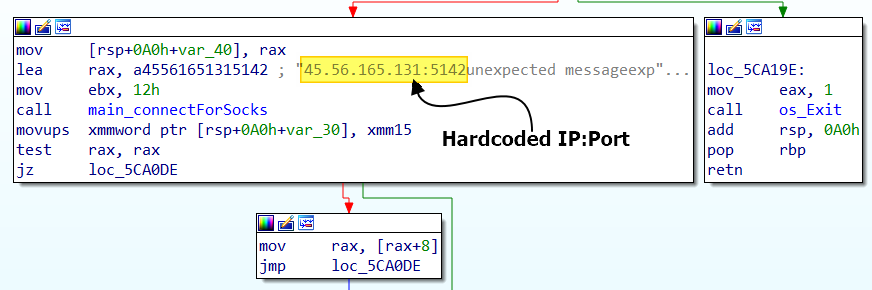
In all of the samples we have analyzed, the backdoor uses two additional Go modules named mimux and soso. While we couldn’t locate these exact module names in existing libraries, we identified similarities for mimux with a GitHub project named Yamux (Yet another Multiplexer) and for soso, a GitHub project named go-socks5.
Threat hunting for the backdoor can be approached in various ways. One method is to use the malware configuration search query in VirusTotal (VT) for the “topcorner” family.
The latest versions of the backdoor, observed in 2024, show a slight modification in their logging function compared to the 2023 version. Previously, the backdoor used the log.Print function in Go for logging activities. However, the newer versions have switched to using a Logger function. This change likely provides more structured and flexible logging capabilities, allowing for better management of log outputs and potentially more detailed logging information.
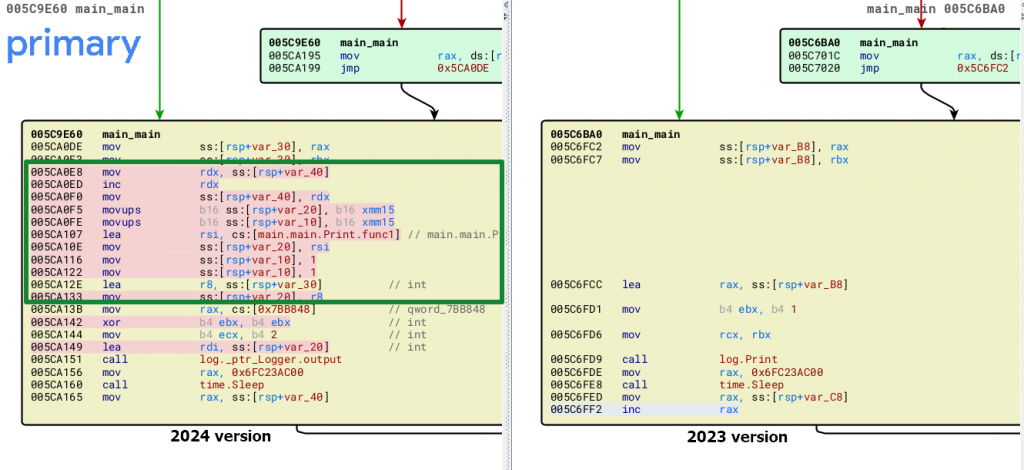
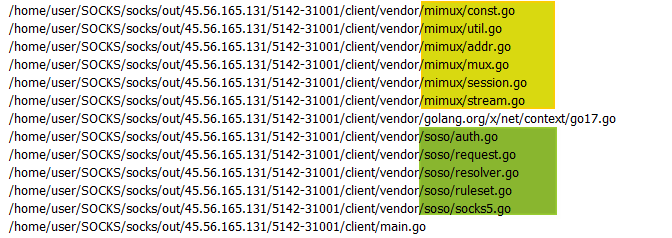
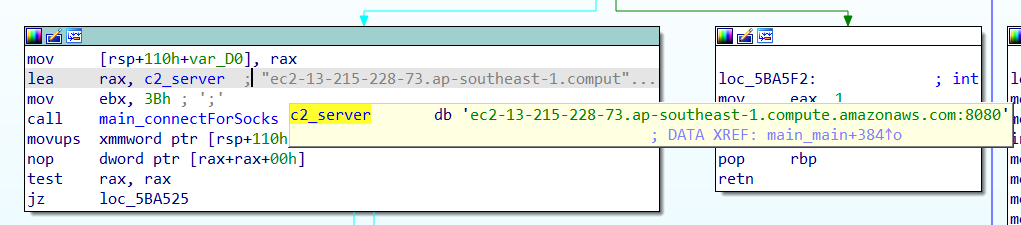
The backdoor can also be hunted by performing string searches for unique Go libraries and modules, such as soso/resolver.go. This approach led us to discover a Linux version of the backdoor (sha256: b12be86af46b0267d86fcacef0a58bad0d157a7a044f89a453082b32503bd3c0), which was first submitted to Virustotal in January 2024.
BianLian primarily uses Go as the programming language for their tools, providing the flexibility to support multiple platforms, including macOS and Linux. The Linux version we discovered contains a hardcoded Amazon EC2 instance domain on port 8080. Functionally, it is the same as the 2024 version of the Windows binaries.
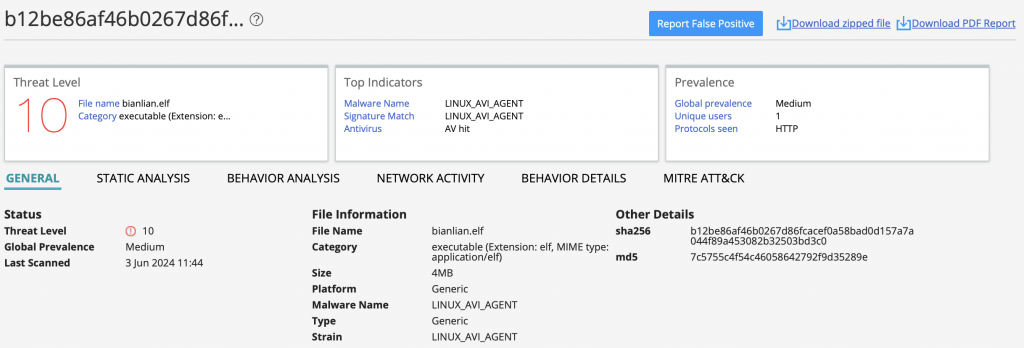
Juniper ATP Cloud detects this malware with threat level 10.
Conclusion
The BianLian ransomware group has demonstrated continuous evolution and adaptability, placing it among the top three most active ransomware groups alongside Lockbit3 and Alphv. BianLian has significantly impacted various sectors, with a particular focus on legal services, healthcare, engineering/construction, accounting services, and logistics and transportation. BianLian’s rise as a prominent ransomware group underscores the ever-evolving threat landscape. Their ability to adapt tactics, develop new tools, and exploit emerging vulnerabilities highlights the need for constant vigilance and proactive defense measures. The use of Golang has enabled BianLian to create versatile tools that operate across different operating systems. By understanding their techniques and implementing robust defenses, organizations can better prepare for and mitigate the impact of ransomware attacks.
Indicators of Compromise
3b309c076c26f27f42dbab8c89f05df51c414e87529251dc2d9946e7bc694f29 72d91293ff1a91587af3997081f65eac819d2ff73655837dc68a447d371ca2f1 f9421165e4a62c7a1941b7b3fa73ac6f2149e7ffab3a6a622406baabf1933a2e 834ab96263cca7b01b3ae6549a9811b56204e714402215ce37fb602732b981d1 B12be86af46b0267d86fcacef0a58bad0d157a7a044f89a453082b32503bd3c0 ec2-13-215-228-73[.]ap-southeast-1[.]compute[.]amazonaws[.]com 104[.]238[.]61[.]20 45[.]56[.]165[.]131 146[.]59[.]102[.]74 45[.]56[.]165[.]131 |
YARA
rule mal_bianlian_go_backdoor {
meta:
description = "Detects BianLian Go backdoor"
author = "Juniper Threat Labs"
date = "2024-05-01"
hashes = "b12be86af46b0267d86fcacef0a58bad0d157a7a044f89a453082b32503bd3c0,834ab96263cca7b01b3ae6549a9811b56204e714402215ce37fb602732b981"
strings:
$s1 = "soso/resolver.go" fullword ascii
$s2 = "mimux/mux.go" fullword ascii
condition:
(uint16(0) == 0x457f or uint16(0) == 0x5a4d) and filesize > 3MB and
filesize < 12MB and all of ($s*)
}
|
References
- https://ransomwatch.telemetry.ltd/#/recentposts
- https://www.guidepointsecurity.com/blog/bianlian-gos-for-powershell-after-teamcity-exploitation/
- https://redacted.com/blog/bianlian-ransomware-gang-gives-it-a-go/
- https://github.com/drb-ra/C2IntelFeeds
- https://threatfox.abuse.ch/browse/tag/BianLian/


