 With the rise in remote work, employee devices often share networks with personal and new devices are regularly added to networks – and often, unbeknownst to IT. Incomplete network visibility is a common factor in many high-profile data breaches. Even organizations that actively hunt for threats internally can and do miss breaches because there is just too much activity occurring on today’s networks for administrators to handle on their own.
With the rise in remote work, employee devices often share networks with personal and new devices are regularly added to networks – and often, unbeknownst to IT. Incomplete network visibility is a common factor in many high-profile data breaches. Even organizations that actively hunt for threats internally can and do miss breaches because there is just too much activity occurring on today’s networks for administrators to handle on their own.
In addition to the lack of visibility is the challenge of effectively enforcing policy. The lifecycle of networked devices is no longer entirely controlled by IT. Many devices – such as Internet of Things (IoT) devices – simply can’t be centrally managed by IT and even if they could, there’s no guarantee that the manufacturers of these devices are regularly releasing security updates.
IT teams face conflicting needs. They have to protect their networks, but they can’t see or control everything on their network. If you can’t control what’s on your network, then compromise is only a matter of time and you cannot adequately respond to a breach if you don’t know what’s happening on your network. All things considered, these are big problems that organizations simply cannot afford to ignore.
It’s all about response time
The “network perimeter” is an increasingly meaningless term; the perimeter is everywhere and the network is constantly interacting with employees, workloads and even the networks of both suppliers and customers. Integration enables success, but it also means that prevention of information security compromise events
IT needs to be able to focus on detecting compromise events when they occur and must be able to rapidly mitigate those breaches. Ultimately, this brings us back to the original problem: there is too much happening on a modern network to easily keep track of it all.
That’s where Risk Profiling driven by Mist AI can help.
Risk Profiling driven by Mist AI
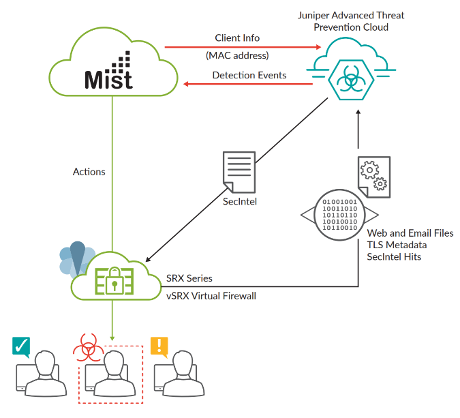 Risk Profiling driven by Mist AI brings Juniper Connected Security to the AI-Driven Enterprise by combining real-time actionable threat intelligence with AIOps powered by Mist AI. With this solution, your Juniper wired, wireless and WAN infrastructure will be secured by Juniper Advanced Threat Prevention.
Risk Profiling driven by Mist AI brings Juniper Connected Security to the AI-Driven Enterprise by combining real-time actionable threat intelligence with AIOps powered by Mist AI. With this solution, your Juniper wired, wireless and WAN infrastructure will be secured by Juniper Advanced Threat Prevention.
Risk Profiling driven by Mist AI extends security beyond the internet perimeter but doesn’t require network administrators to learn a new tool. The existing Juniper Mist Wi-Fi management interface shows any infected wireless client that is observable by Mist AI. These clients will have a threat score associated with them determined by ATP Cloud.
Juniper Mist solutions can also help administrators to physically locate compromised wireless devices. This allows Wi-Fi administrators to quickly identify and react to compromised devices without having to engage other teams.
The end of strict control over endpoints is not the end of IT security. The best way to secure a network is to build security into the network itself and this is the only realistic option for most organizations going forward. Risk Profiling driven by Mist AI provides a critical layer of visibility and policy enforcement for the Threat-Aware Networks of the next decade. Integration with Juniper Mist AI speeds resolution of user experience and information security events alike, lowering operational costs.
Risk Profiling driven by Mist AI brings network security to the distributed access network edge. Campus and branch networks, along with managed work-from-home and pop-up network sites, are now active components of their own defense as part of the Threat-Aware Network.
Download the Solution Brief to learn more and read the Transform IT with Real AI blog for more information.


