Do you know who and what is on your network?
Throughout my career, whenever I’ve asked this question to IT security leaders, it has almost always been met with an incomplete answer.
Before you run and fetch the quantity from your endpoint software purchase orders, take a minute to think about all of the devices that use your network to communicate — not just servers, laptops and mobile phones, but printers, conference rooms and security cameras, and even vending machines that “talk” with other devices inside and outside your network.
Network visibility is an important issue that security teams have struggled with. With each new connection, risk increases – especially when it comes to IoT devices. Not all connected devices can run secure operating systems, be patched or run endpoint agents.
With a huge percentage of the workforce suddenly working at home and services that once ran on dedicated secure networks now having to operate outdoors and in remote locations, there’s much more opportunity to introduce risk. This is primarily due to increased network traffic, which attracts attackers who are ready to take advantage of the chaos.
So, how do you know who and what is on your network, right now or at any given time? Use the network.
Extending visibility and enforcement to every point of connection on the network is essential. You don’t have to own the device or the application to secure it. Let the network do that. This is the premise of Juniper Connected Security: security starts with the network.
To this end, we are excited to announce the latest additions to the Juniper Connected Security portfolio: Adaptive Threat Profiling for ATP Cloud, risk-based access control through a new integration with WootCloud HyperContext® and Juniper Secure Connect.
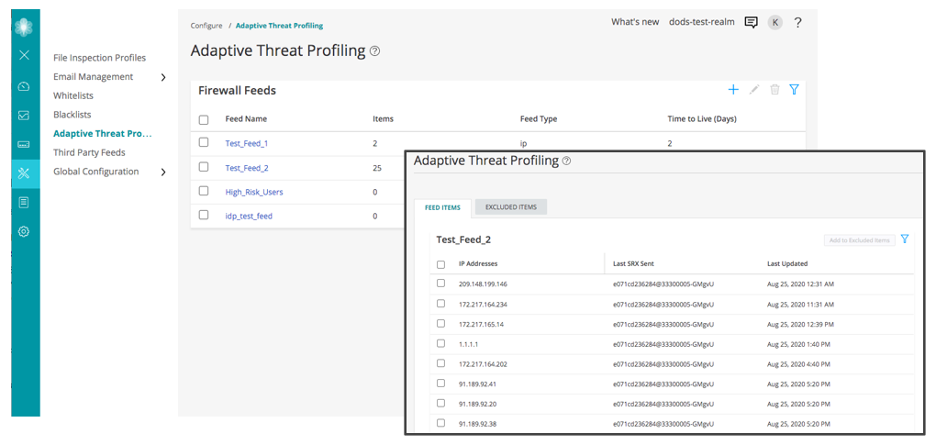
Adaptive Threat Profiling for ATP Cloud
Juniper® Advanced Threat Prevention (ATP) Cloud is the threat intelligence hub for Juniper customers, identifying indicators of compromise for users and devices across our networking and security portfolios. Through Adaptive Threat Profiling, ATP Cloud adds traffic intelligence as another piece of context to recognize, identify and defend against threats as they emerge.
To better combat the continuous onslaught of new threats, Adaptive Threat Profiling for ATP Cloud automatically creates security intelligence threat feeds based on who is currently attacking the network. Adaptive Threat Profiling leverages Juniper Security Services enabled on SRX Series firewalls to classify traffic targeting certain endpoint OSs and build custom threat intelligence feeds. These feeds can then be used for further inspection or blocking at multiple enforcement points, giving organizations the power to respond to attacks in real time. These custom feeds dynamically adapt to changing threats and extend mitigation capabilities to the rest of the network.
Risk-Based Access Control through Juniper & WootCloud HyperContext
Some amount of risk is introduced to the network with the addition of each new device connecting to it. Knowing when that happens and what those devices are is the first step to reducing that risk. The second step is taking action.
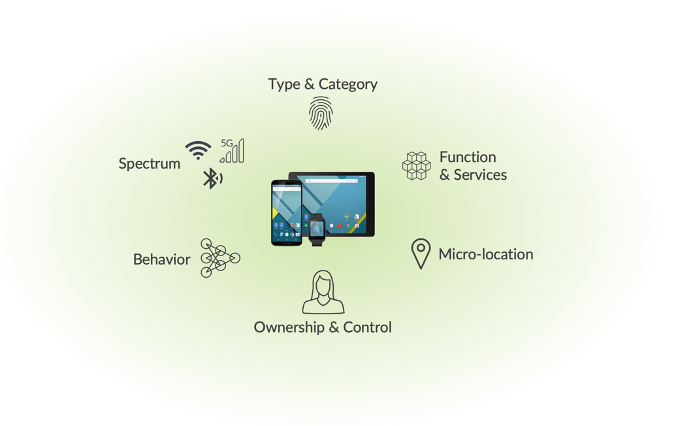
WootCloud HyperContext has integrated with SRX Series firewalls, ATP Cloud and Juniper Mist Cloud to identify devices connecting to the network, including IoT devices, and automatically segment them, apply additional threat prevention policies, enforce additional authentication or block them outright according to their type and risk level.
WootCloud’s engine uses artificial intelligence (AI) and machine learning (ML) to detect devices on the network and radio frequency spectrum. It compiles device context from physical, logical, operational and locational touch points to generate HyperContext®, providing valuable insights and accurate risk and threat assessments serving as the source of truth for access control and security policies.
The integration of WootCloud with Juniper Mist Cloud, both for wireless and wired assurance and Juniper SRX Firewall and ATP Cloud, lead to effective automated risk mitigation through visibility, intelligence, micro-segmentation and access control. This becomes a context-driven solution that can automate device management at IoT scale with enforcement happening seamlessly across the network at the switch, access point and firewall.
Juniper Secure Connect
Adaptive Threat Profiling, along with the rest of Juniper’s advanced security services, can now be extended to the home with our new VPN application, Juniper Secure Connect. Users can securely connect to the network wherever they are: at home, in the office or on the road.
Juniper Secure Connect helps organizations quickly achieve dynamic, flexible and adaptable connectivity to any device, anywhere, reducing risk by extending visibility and enforcement from client to cloud. Juniper Secure Connect includes a simple configuration process using built-in automation and ensures optimal performance and connectivity.
Now, organizations can provide security and protection for confidential data while also building a WAN access fabric that adapts as needs change.
Juniper Secure Connect, Adaptive Threat Profiling and WootCloud’s integration with our networking and security portfolios come together to show organizations exactly who and what is on their networks. More importantly, organizations can then do something about risky devices, even when they are remote or aren’t equipped with endpoint agents.
With this announcement, we are delivering on Juniper’s Connected Security strategy to safeguard users, applications and infrastructure by using the network to extend visibility and enforcement to every point of connection. Security starts with the network and today, we’re making it easier than ever for our customers to do just that.
Come see for yourself and learn more about our newest additions to the Juniper Connected Security portfolio.


